Deploying on a Management Network
The FireSIGHT System can be deployed to accommodate the needs of each unique network architecture. The Defense Center provides a centralized management console and database repository for the FireSIGHT System. Devices are installed on network segments to collect traffic connections for analysis.
Defense Centers use a management interface to connect to a trusted management network (that is, a secure internal network not exposed external traffic). Devices then connect to a Defense Center using a management interface.

Note![]() See the ASA documentation for more information on deployment scenarios for ASA FirePOWER devices.
See the ASA documentation for more information on deployment scenarios for ASA FirePOWER devices.
To learn more about your interface options, see the following sections for more information:
Management Deployment Considerations
Your management deployment decisions are based on a variety of factors. Answering these questions can help you understand your deployment options to configure the most efficient and effective system:
- Will you use the default single management interface to connect your device to your Defense Center? Will you enable additional management interfaces to improve performance, or to isolate traffic received on the Defense Center from different networks? See Understanding Management Interfaces for more information.
- Do you want to enable traffic channels to create two connections between the Defense Center and the managed device to improve performance? Do you want to use multiple management interfaces to further increase throughput capacity between the Defense Center and the managed device? See Deploying with Traffic Channels for more information.
- Do you want to use one Defense Center to manage and isolate traffic from devices on different networks? See Deploying with Network Routes for more information.
- Are you deploying your management interfaces in a protected environment? Is appliance access restricted to specific workstation IP addresses? Security Considerations describes considerations for deploying your management interfaces securely.
Understanding Management Interfaces
Management interfaces provide the means of communication between the Defense Center and all devices it manages. Maintaining good traffic control between the appliances is essential to the success of your deployment.
On Series 3 appliances and virtual Defense Centers, you can enable the management interface on the Defense Center, device, or both, to sort traffic between the appliances into two separate traffic channels. The management traffic channel carries all internal traffic (such as inter-device traffic specific to the management of the appliance and the system), and the event traffic channel carries all event traffic (such as web events). Splitting traffic into two channels creates two connection points between the appliances which increases throughput, thus improving performance. You can also enable multiple management interfaces to provide still greater throughput between appliances, or to manage and isolate traffic between devices on different networks.
After you register the device to the Defense Center, you can change the default configuration to enable traffic channels and multiple management interfaces using the web browser on each appliance. For configuration information, see Configuring Appliance Settings in the FireSIGHT System User Guide.
To learn more about using management interfaces, see the following sections for more information:
Single Management Interface
Supported Defense Centers: Any
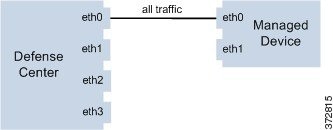
When you register your device to a Defense Center, you establish a single communication channel that carries all traffic between the management interface on the Defense Center and the management interface on the device.
The following graphic shows the default single communication channel. One interface carries one communication channel that contains both management and event traffic.
Multiple Management Interfaces
Supported Defense Centers: Series 3, Virtual
You can enable and configure multiple management interfaces, each with a unique IPv4 or IPv6 address and, optionally, a unique hostname, to provide greater traffic throughput by sending each traffic channel to a different management interface. Configure a smaller interface to carry the lighter management traffic load, and a larger interface to carry the heavier event traffic load. You can register devices to separate management interfaces and configure both traffic channels for the same interface, or use a dedicated management interface to carry the event traffic channels for all devices managed by the Defense Center.
You can also create a route from a specific management interface on your Defense Center to a different network, allowing your Defense Center to manage traffic from devices on one network separately from traffic from devices on another network.
Additional management interfaces function the same as the default management interface (such as using high availability between the Defense Centers) with the following exceptions:
- You can configure DHCP on the default (
eth0) management interface only. Additional (eth1and so on) interfaces require unique static IP addresses and hostnames. - You must configure both traffic channels to use the same management interface when you use a non-default management interface to connect your Defense Center and managed device and those appliances are separated by a NAT device.
- On the 70xx Family, you can separate traffic into two channels and configure those channels to send traffic to one or more management interfaces on the virtual Defense Center. However, because the 70xx Family contains only one management interface, the device receives traffic sent from the Defense Center on only one management interface.
Deployment Options
You can manage traffic flow using traffic channels to improve performance on your system using one or more management interfaces. In addition, you can create a route to a different network using a specific management interface on the Defense Center and its managed device, allowing you to isolate traffic between devices on different networks. For more information, see the following sections:
Deploying with Traffic Channels
Supported Defense Centers: Series 3, Virtual
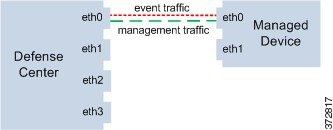
When you use two traffic channels on one management interface, you create two connections between the Defense Center and the managed device. One channel carries management traffic and one carries event traffic, separately and on the same interface.
The following example shows the communication channel with two separate traffic channels on the same interface.
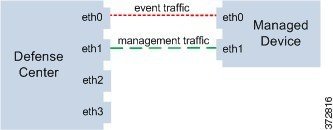
When you use multiple management interfaces, you can improve your performance by dividing the traffic channels over two management interfaces, thus increasing the traffic flow by adding the capacity of both interfaces. One interface carries the management traffic channel and the other carries the event traffic channel. If either interface fails, all traffic reroutes to the active interface and the connection is maintained.
The following graphic shows the management traffic channel and the event traffic channel over two management interfaces.
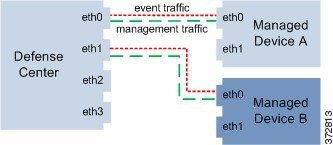
You can use a dedicated management interface to carry only event traffic from multiple devices. In this configuration, each device is registered to a different management interface to carry the management traffic channel, and one management interface on the Defense Center carries all event traffic channels from all devices. If an interface fails, traffic reroutes to the active interface and the connection is maintained. Note that because event traffic for all devices is carried on the same interface, traffic is not isolated between networks.
The following graphic shows two devices using different management channel traffic interfaces sharing the same dedicated interface for event traffic channels.

Deploying with Network Routes
Supported Defense Centers: Series 3, Virtual
You can create a route from a specific management interface on your Defense Center to a different network. When you register a device from that network to the specified management interface on the Defense Center, you provide an isolated connection between the Defense Center and the device on a different network. Configure both traffic channels to use the same management interface to ensure that traffic from that device remains isolated from device traffic on other networks. Because the routed interface is isolated from all other interfaces on the Defense Center, if the routed management interface fails, the connection is lost.

Tip![]() You must register a device to the static IP address of any management interface other than the default (
You must register a device to the static IP address of any management interface other than the default (eth0) management interface. DHCP is supported only on the default management interface.
After you install your Defense Center, you configure multiple management interfaces using the web interface. See Configuring Appliance Settings in the FireSIGHT System User Guide for more information.
The following graphic shows two devices isolating network traffic by using separate management interfaces for all traffic. You can add more management interfaces to configure separate management and event traffic channel interfaces for each device.
When you register an 8000 Series managed device to your Defense Center, you must either auto-negotiate on both sides of the connection, or set both sides to the same static speed to ensure a stable network link. 8000 Series managed devices do not support half duplex network links; they also do not support differences in speed or duplex configurations at opposite ends of a connection.
Security Considerations
To deploy your management interfaces in a secure environment, Cisco recommends that you consider the following:
- Always connect the management interface to a trusted internal management network that is protected from unauthorized access.
- Identify the specific workstation IP addresses that can be allowed to access appliances. Restrict access to the appliance to only those specific hosts using Access Lists within the appliance’s system policy. For more information, see the FireSIGHT System User Guide.
 Feedback
Feedback