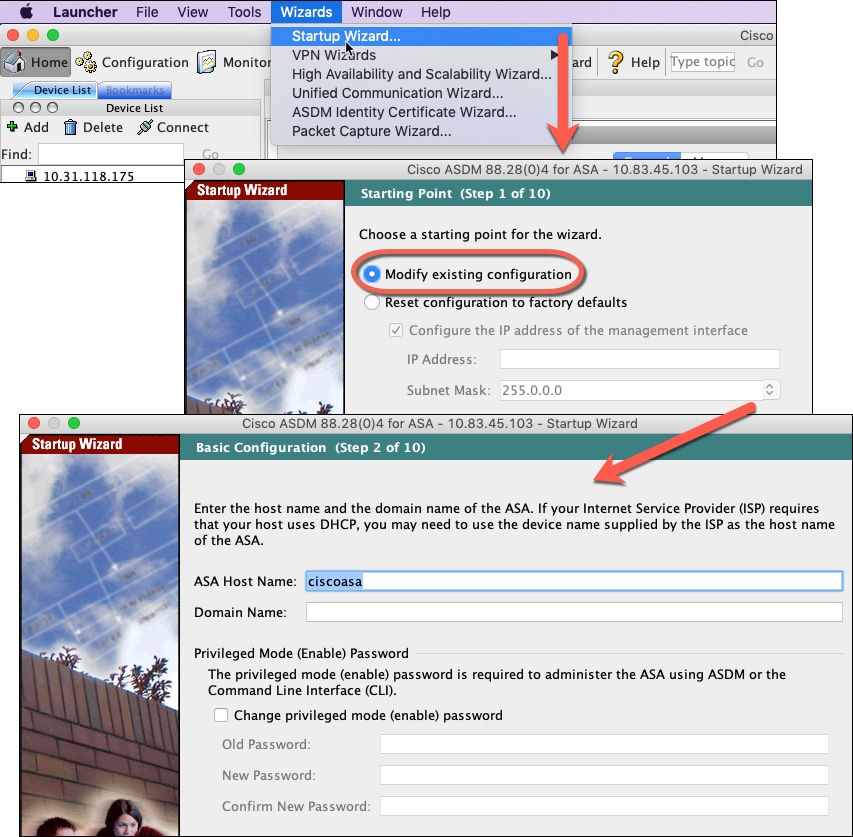
(Optional) Change the IP Address
By default, you can launch ASDM from the following interfaces:
-
Ethernet 1/2 through Ethernet 1/8 or 1/10—192.168.1.1
-
Management 1/1—192.168.45.1
If you cannot use the default IP address, you can set the IP address of the Management 1/1 interface at the ASA CLI.
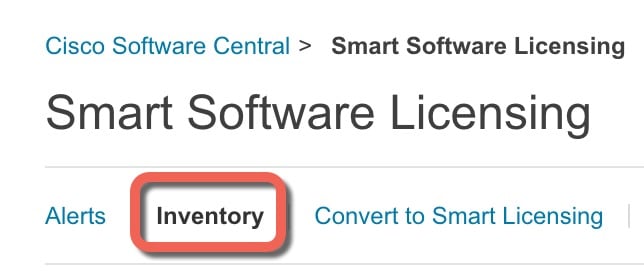
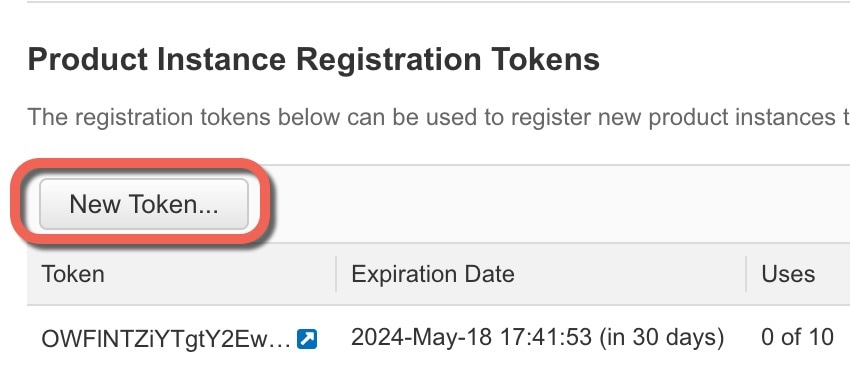
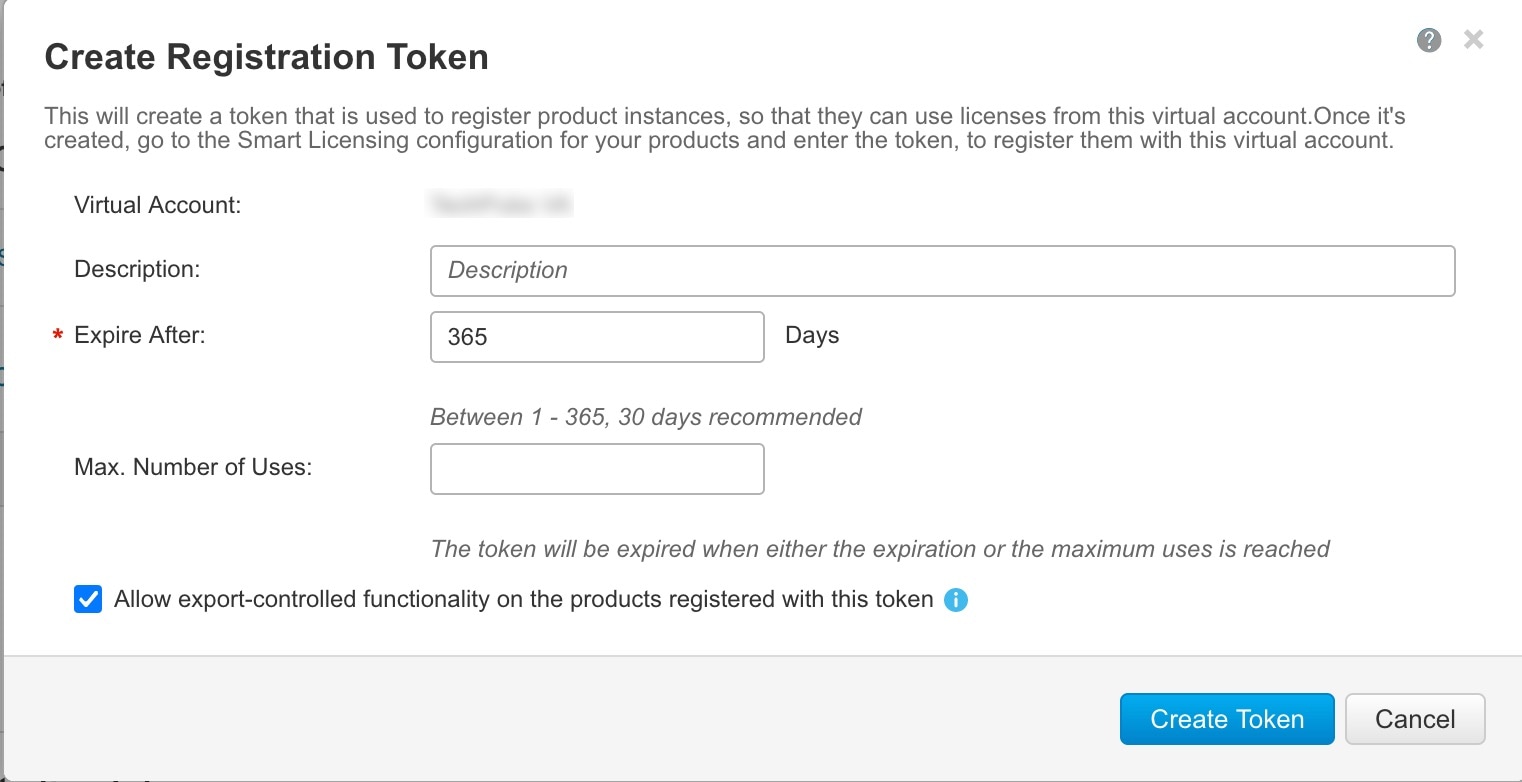
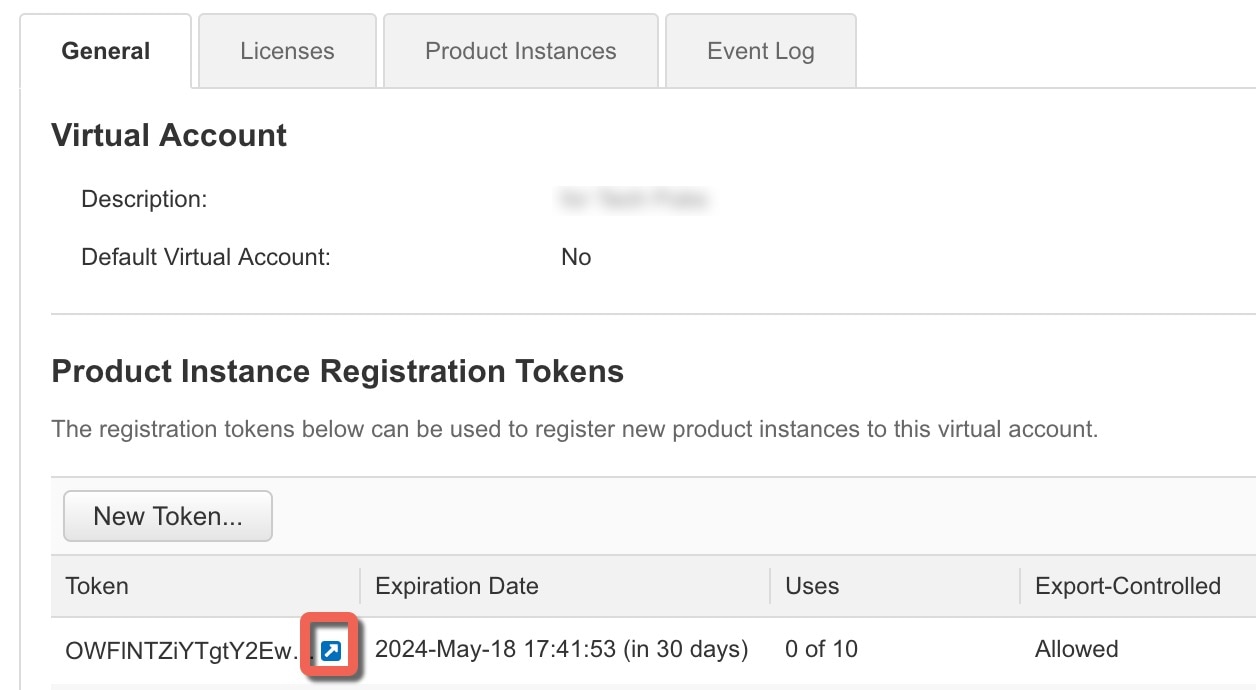
Procedure
|
Step 1 |
Connect to the console port and access global configuration mode. See Access the ASA CLI. |
|
Step 2 |
Restore the default configuration with your chosen IP address. configure factory-default [ip_address [mask]] Example: |
|
Step 3 |
Save the default configuration to flash memory. write memory |
 Feedback
Feedback