Log Into the Device Manager
Log into the device manager to configure your threat defense.
Procedure
|
Step 1 |
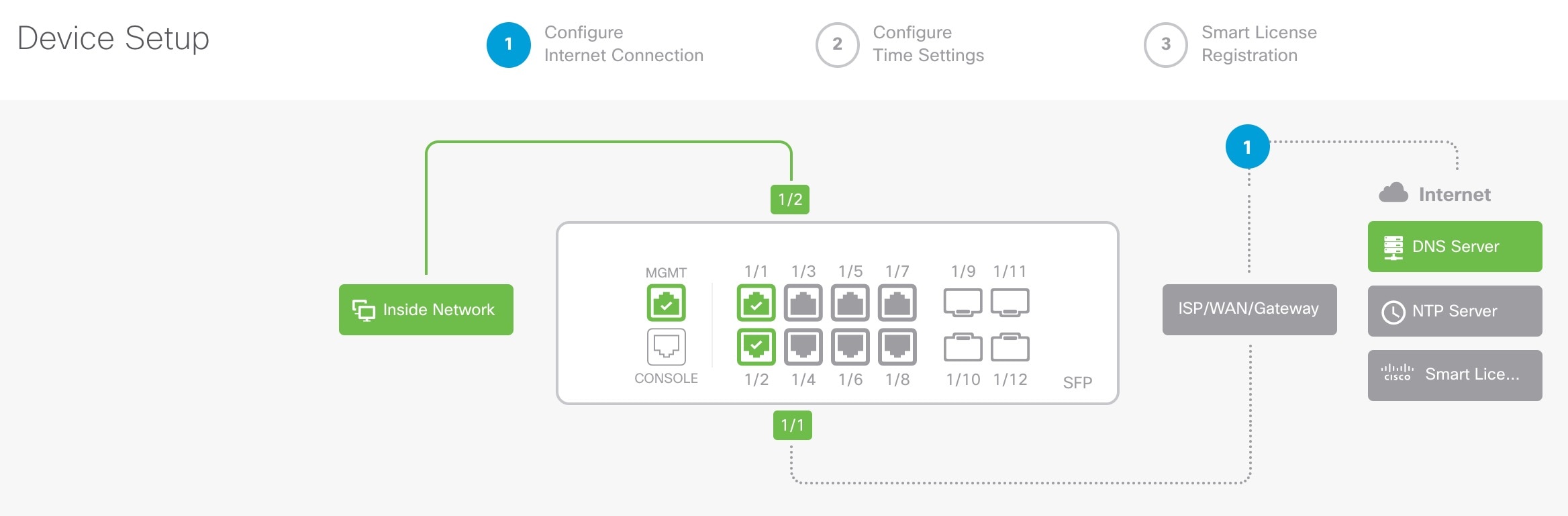
Enter the following URL in your browser, depending on which interface your computer is connected to.
|
|
Step 2 |
Log in with the username admin, and the default password Admin123. |
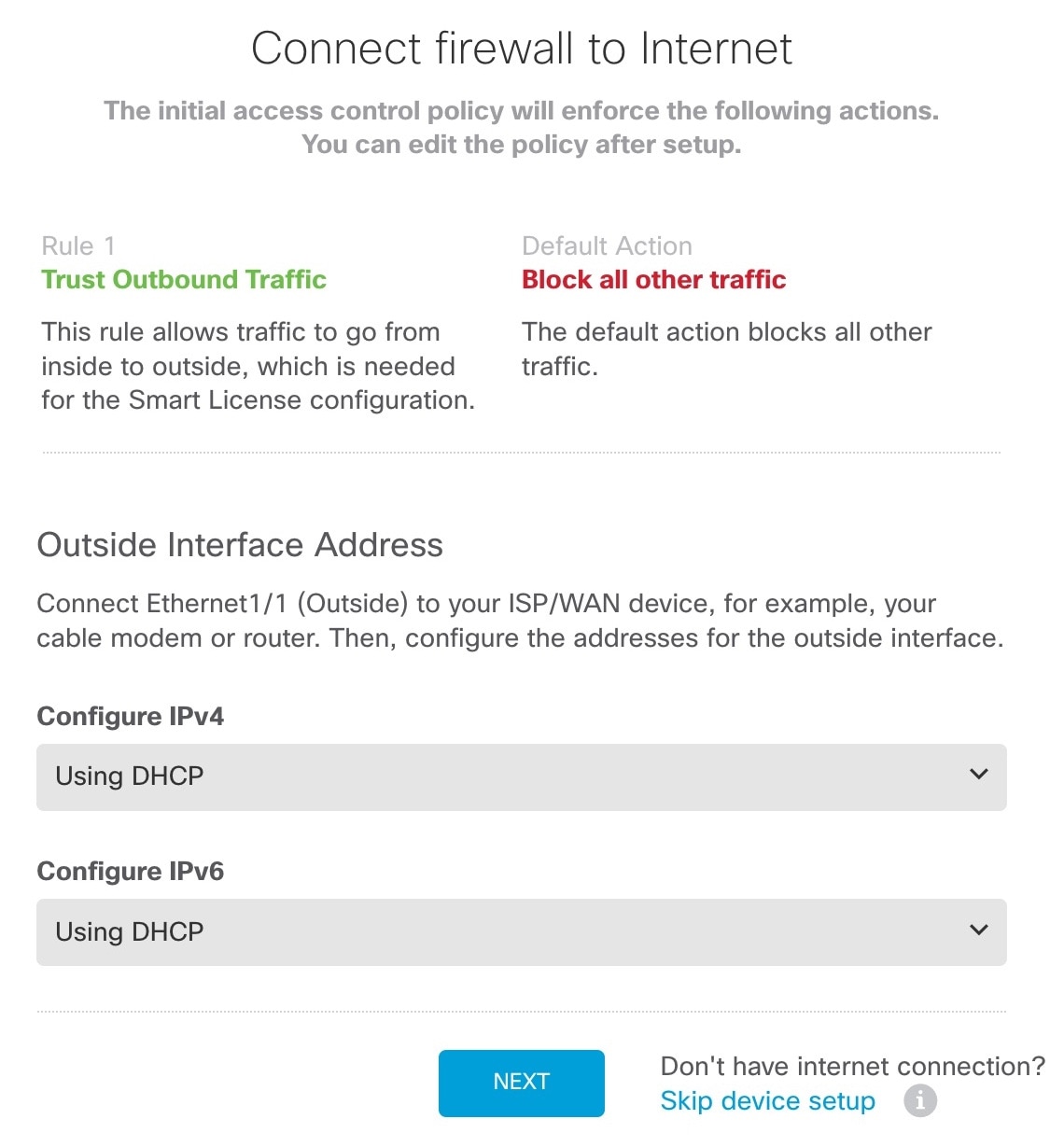
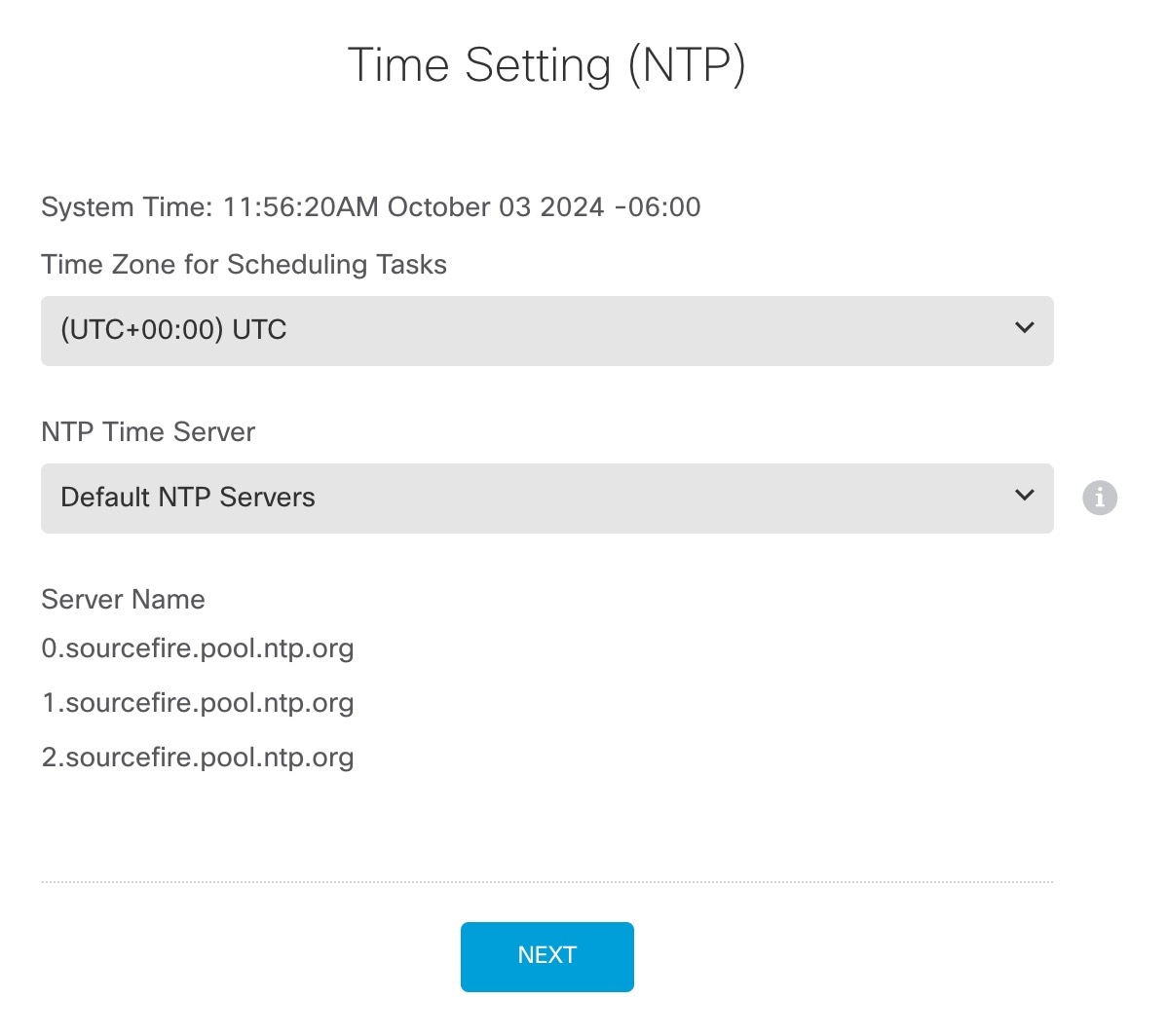
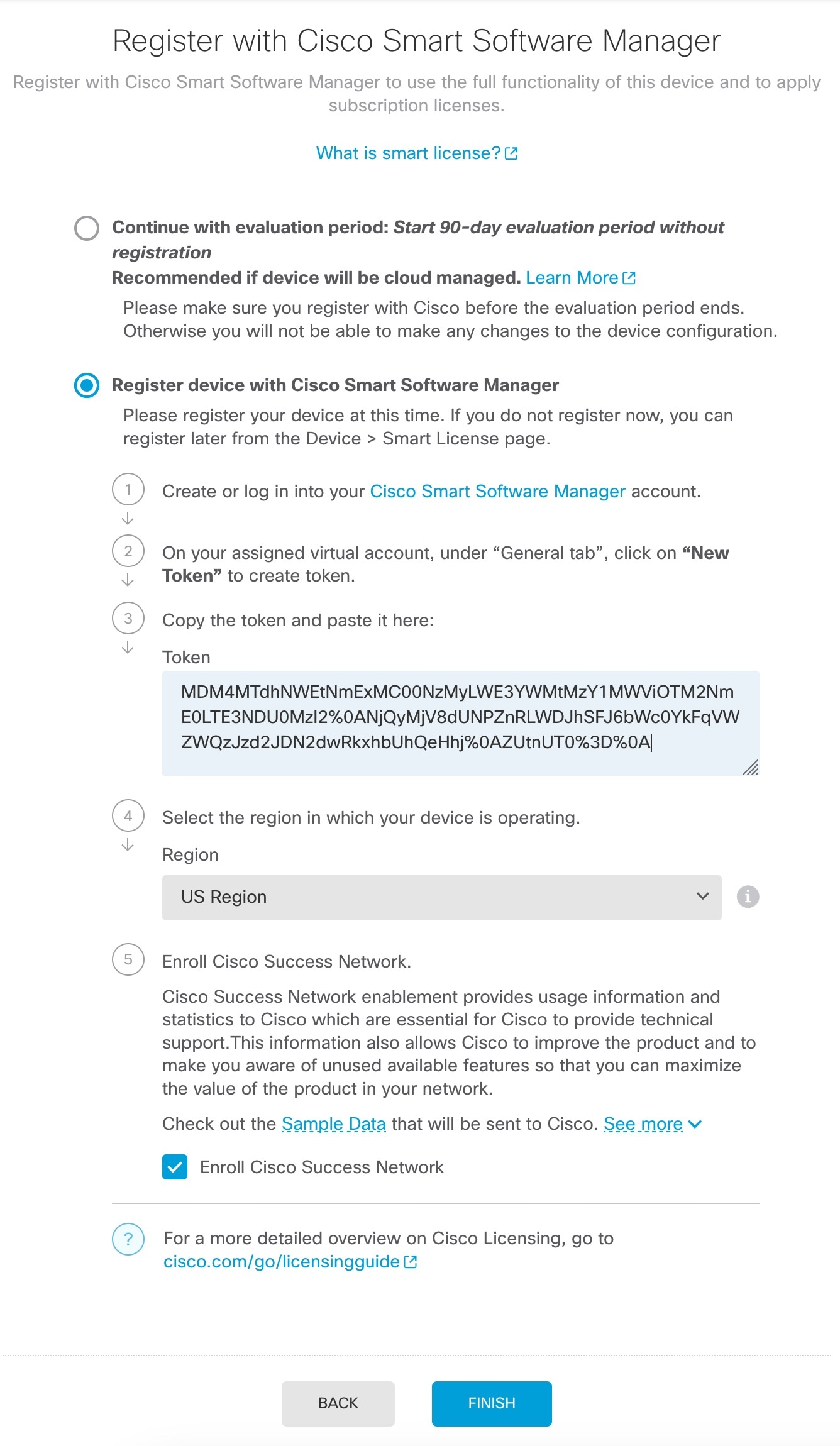
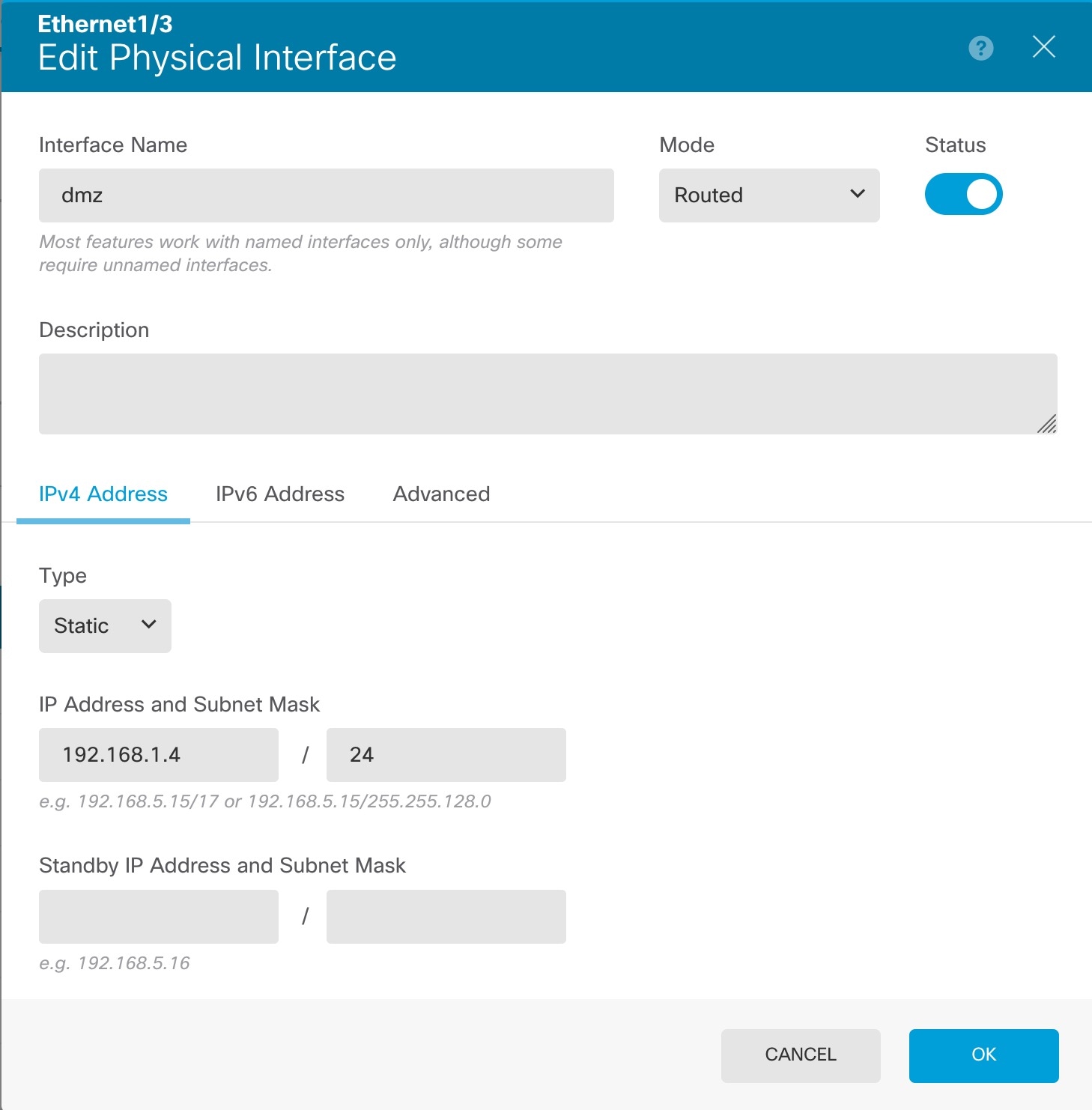
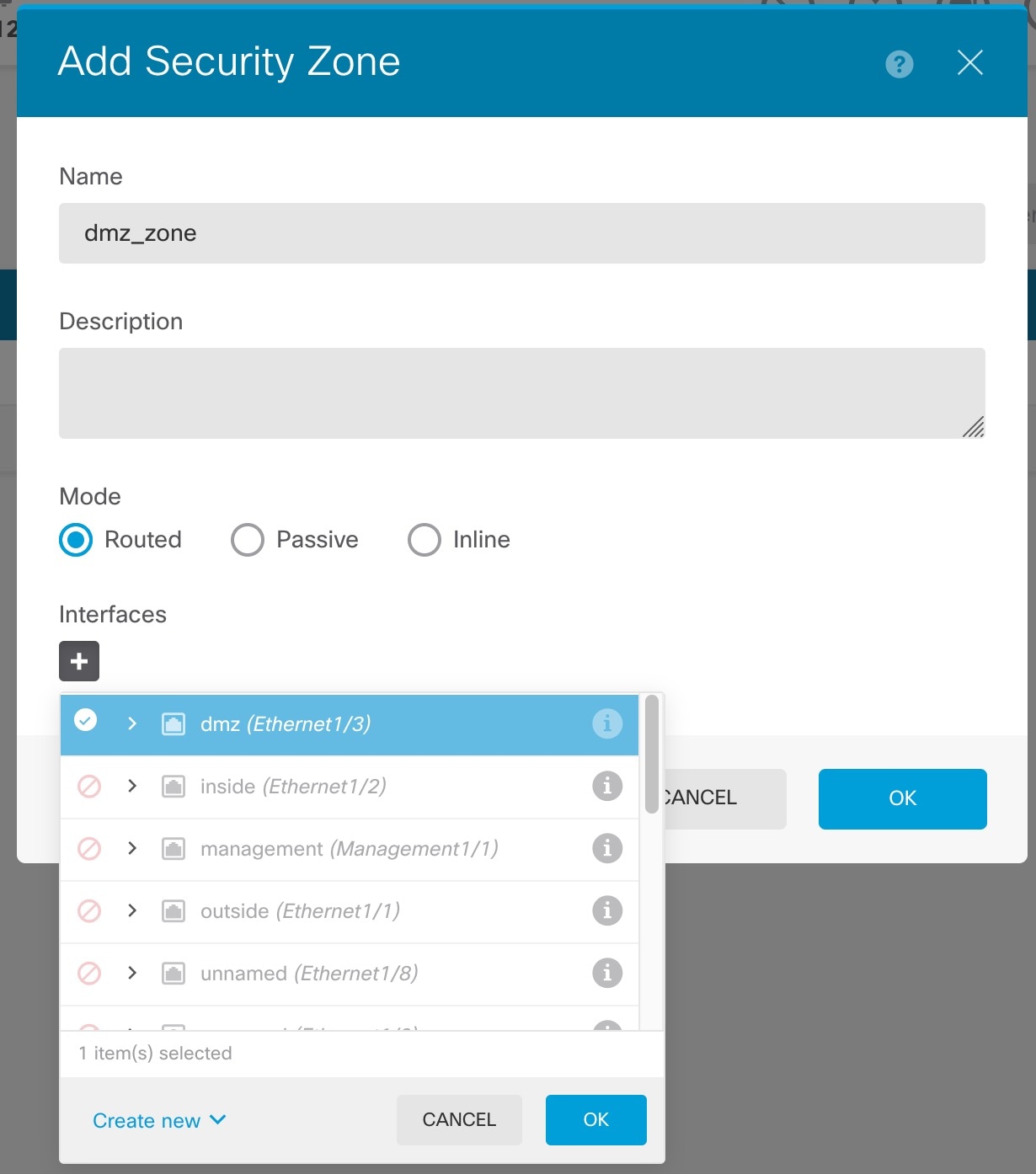
 ) for each interface to define the name, IP address, and other settings.
) for each interface to define the name, IP address, and other settings.

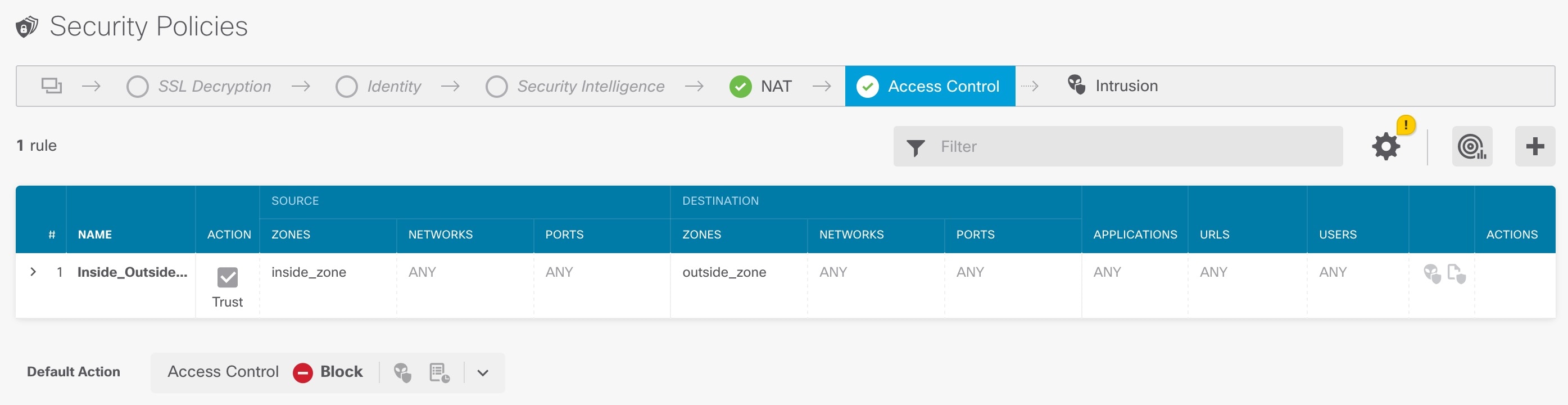
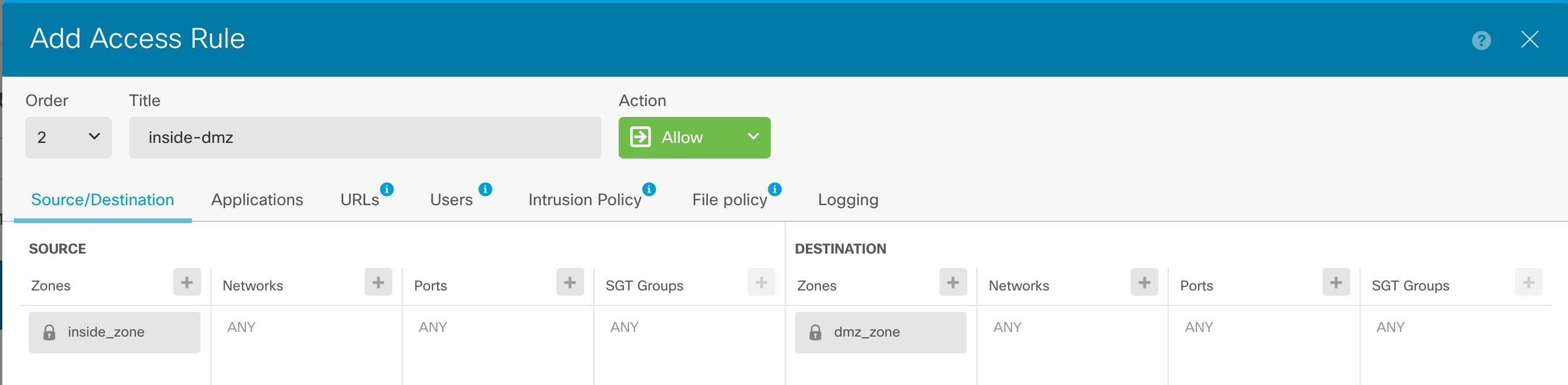
 ) to deploy your changes to the device.
) to deploy your changes to the device.
 Feedback
Feedback