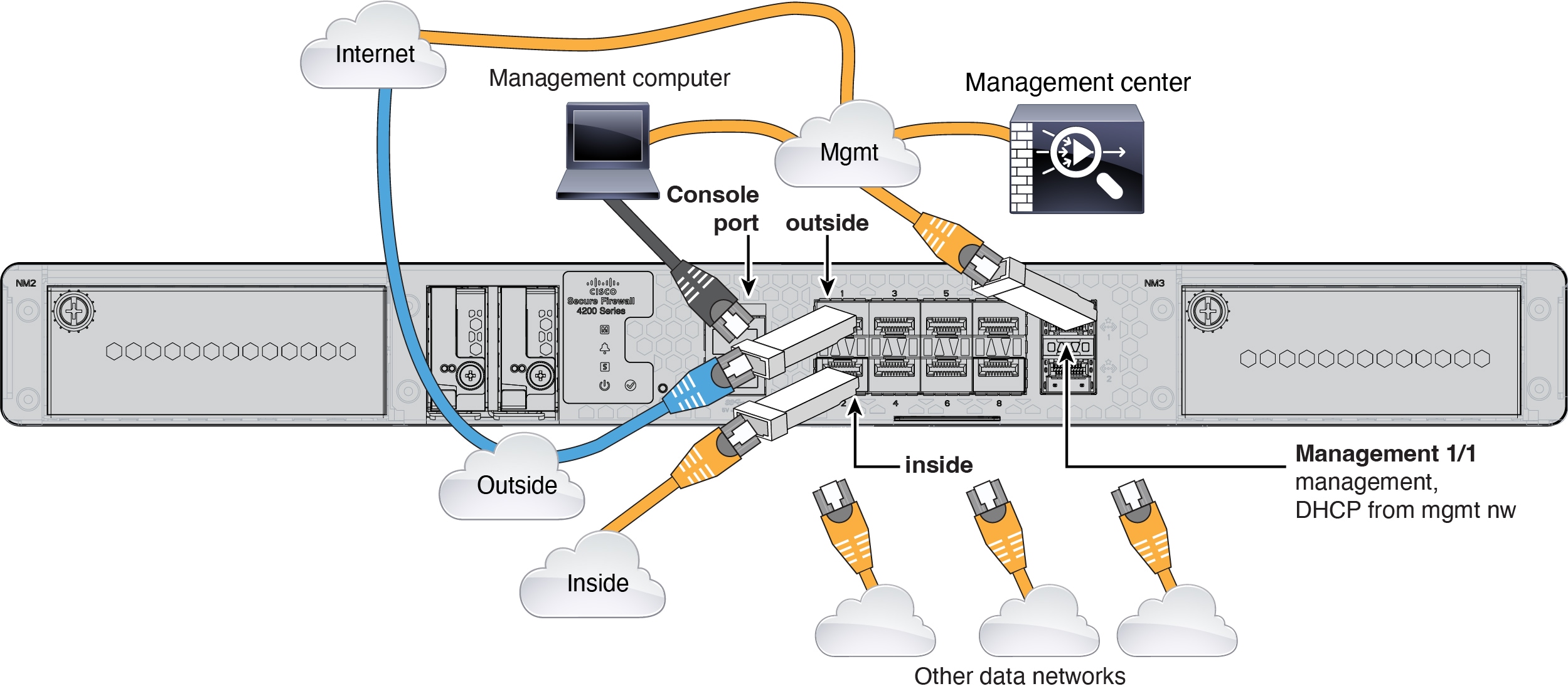
Cable the Firewall
Connect the management center to the dedicated Management 1/1 interface. The management network needs access to the internet for updates. For example, you can connect the management network to the internet through the firewall itself (for example, by connecting to the inside network).
-
Obtain a console cable—The firewall does not ship with a console cable by default, so you will need to buy a third-party USB-to-RJ-45 serial cable, for example.
-
Install SFPs into the data interface ports—The built-in ports are 1/10/25-Gb SFP28 ports that require SFP/SFP+/SFP28 modules.
-
See the hardware installation guide for more information.
 Feedback
Feedback