To assist you with advanced troubleshooting and working with Cisco TAC, we provide the following troubleshooting tools. To
use these tools, log in as any user to the Ubuntu host on which the dynamic
attributes connector is running.
Check container status
To check the status of the dynamic
attributes connector Docker containers, enter the following commands:
cd ~/csdac/app
sudo ./muster-cli status
Sample output follows:
============================== CORE SERVICES =============================
Name Command State Ports
----------------------------------------------------------------------------------------------------------
muster-bee ./docker-entrypoint.sh run ... Up 50049/tcp, 50050/tcp
muster-etcd etcd Up 2379/tcp, 2380/tcp
muster-ui /docker-entrypoint.sh runs ... Up (healthy) 0.0.0.0:443->8443/tcp,:::443->8443/tcp
muster-ui-backend ./docker-entrypoint.sh run ... Up 50031/tcp
=========================== CONNECTORS AND ADAPTERS ===========================
Name Command State Ports
-------------------------------------------------------------------------------
muster-adapter-fmc.1 ./docker-entrypoint.sh run ... Up 50070/tcp
muster-connector-vcenter.1 ./docker-entrypoint.sh run ... Up 50070/tcp
Stop, start, or restart the Dynamic Attributes Connector Docker containers
If the ./muster-cli status indicates containers are down or to restart containers in the event of issues, you can enter the following commands:
Stop and restart:
cd ~/csdac/app
sudo ./muster-cli stop
sudo ./muster-cli start
Start only:
cd ~/csdac/app
sudo ./muster-cli start
Enable debug logging and generate troubleshoot files
If advised to do so by Cisco TAC, enable debug logging and generate troubleshoot files as follows:
cd ~/csdac/app
sudo ./muster-cli debug-on
sudo ./muster-cli ts-gen
The troubleshoot file name is ts-bundle-timestamp.tar and is created in the same directory.
The following table shows the location of troubleshoot files and logs in the troubleshoot file.
|
Location
|
What it contains
|
|
/csdac/app/ts-bundle-timestamp/info
|
etcd database contents
|
|
/csdac/app/ts-bundle-timestamp/logs
|
Container log files
|
|
/csdac/app/ts-bundle-timestamp/status.log
|
Container status, versions, and image status
|
Verify dynamic objects on the
To verify your connectors and adapters are creating objects on the FMC, you can use the following command on the FMC as an administrator:
sudo tail f /var/opt/CSCOpx/MDC/log/operation/usmsharedsvcs.log
Example: Successful object creation
26-Aug-2021 12:41:35.912,[INFO],(DefenseCenterServiceImpl.java:1442)
com.cisco.nm.vms.api.dc.DefenseCenterServiceImpl, ajp-nio-127.0.0.1-9009-exec-10
** REST Request [ CSM ]
** ID : 18b25356-fd6b-4cc4-8d27-bbccb52a6275
** URL: POST /audit
{
"version": "7.1.0",
"requestId": "18b25356-fd6b-4cc4-8d27-bbccb52a6275",
"data": {
"userName": "csdac-centos7",
"subsystem": "API",
"message": "POST https://myfmc.example.com/api/fmc_config/v1/domain/e276abec-e0f2-11e3-8169-6d9ed49b625f
/object/dynamicobjects Created (201) - The request has been fulfilled and resulted in a new resource being created",
"sourceIP": "192.0.2.103",
"domainUuid": "e276abec-e0f2-11e3-8169-6d9ed49b625f",
"time": "1629981695431"
},
"deleteList": []
}
Example: Unsuccessful object creation (in this case because the adapter user has insufficient privileges):
26-Aug-2021 12:47:50.440,[INFO],(DefenseCenterServiceImpl.java:1442)
com.cisco.nm.vms.api.dc.DefenseCenterServiceImpl, ajp-nio-127.0.0.1-9009-exec-2
** REST Request [ CSM ]
** ID : 58566831-7532-4d61-a579-2bbc3c325b2f
** URL: POST /audit
{
"version": "7.1.0",
"requestId": "58566831-7532-4d61-a579-2bbc3c325b2f",
"data": {
"userName": "csdac-centos7",
"subsystem": "API",
"message": "GET https://myfmc.example.com/api/fmc_config/v1/domain/e276abec-e0f2-11e3-8169-6d9ed49b625f/
object/dynamicobjects/vCenter___CentOS_7__4 Forbidden (403) - The server understood the request, but is refusing to fulfill it",
"sourceIP": "192.0.2.103",
"domainUuid": "e276abec-e0f2-11e3-8169-6d9ed49b625f",
"time": "1629982070404"
},
"deleteList": []
}
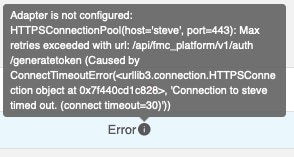


 Feedback
Feedback