About the Cisco Secure Dynamic Attributes Connector
The Cisco Secure Dynamic Attributes Connector enables you to use service tags and categories from various cloud service platforms in Firepower Management Center (FMC) access control rules.
Supported connectors
We currently support:
|
CSDAC version/platform |
AWS |
GitHub |
Google Cloud |
Azure |
Azure Service Tags |
Microsoft Office 365 |
vCenter |
Webex |
Zoom |
|---|---|---|---|---|---|---|---|---|---|
|
Version 1.1 (on-premises) |
Yes |
No |
No |
Yes |
Yes |
Yes |
Yes |
No |
No |
|
Version 2.0 (on-premises) |
Yes |
No |
Yes |
Yes |
Yes |
Yes |
Yes |
No |
No |
More information about connectors:
-
Amazon Web Services (AWS)
For more information, see a resource like Tagging AWS resources on the Amazon documentation site.
-
Microsoft Azure
For more information, see this page on the Azure documentation site.
-
Microsoft Azure service tags
For more information, see a resource like Virtual network service tags on Microsoft TechNet.
-
Office 365 IP addresses
For more information, see Office 365 URLs and IP address ranges on docs.microsoft.com.
-
VMware categories and tags managed by vCenter and NSX-T
For more information, see a resource like vSphere Tags and Attributes in the VMware documentation site.
How It Works
Network constructs such as IP address are not reliable in virtual, cloud and container environments due to the dynamic nature of the workloads and the inevitability of IP address overlap. Customers require policy rules to be defined based on non-network constructs such as VM name or security group, so that firewall policy is persistent even when the IP address or VLAN changes.
You can collect these tags and attributes using Docker containers running on an Ubuntu virtual machine. Install the Cisco Secure Dynamic Attributes Connector on the Ubuntu host using an Ansible collection.
The following figure shows how the system functions at a high level.
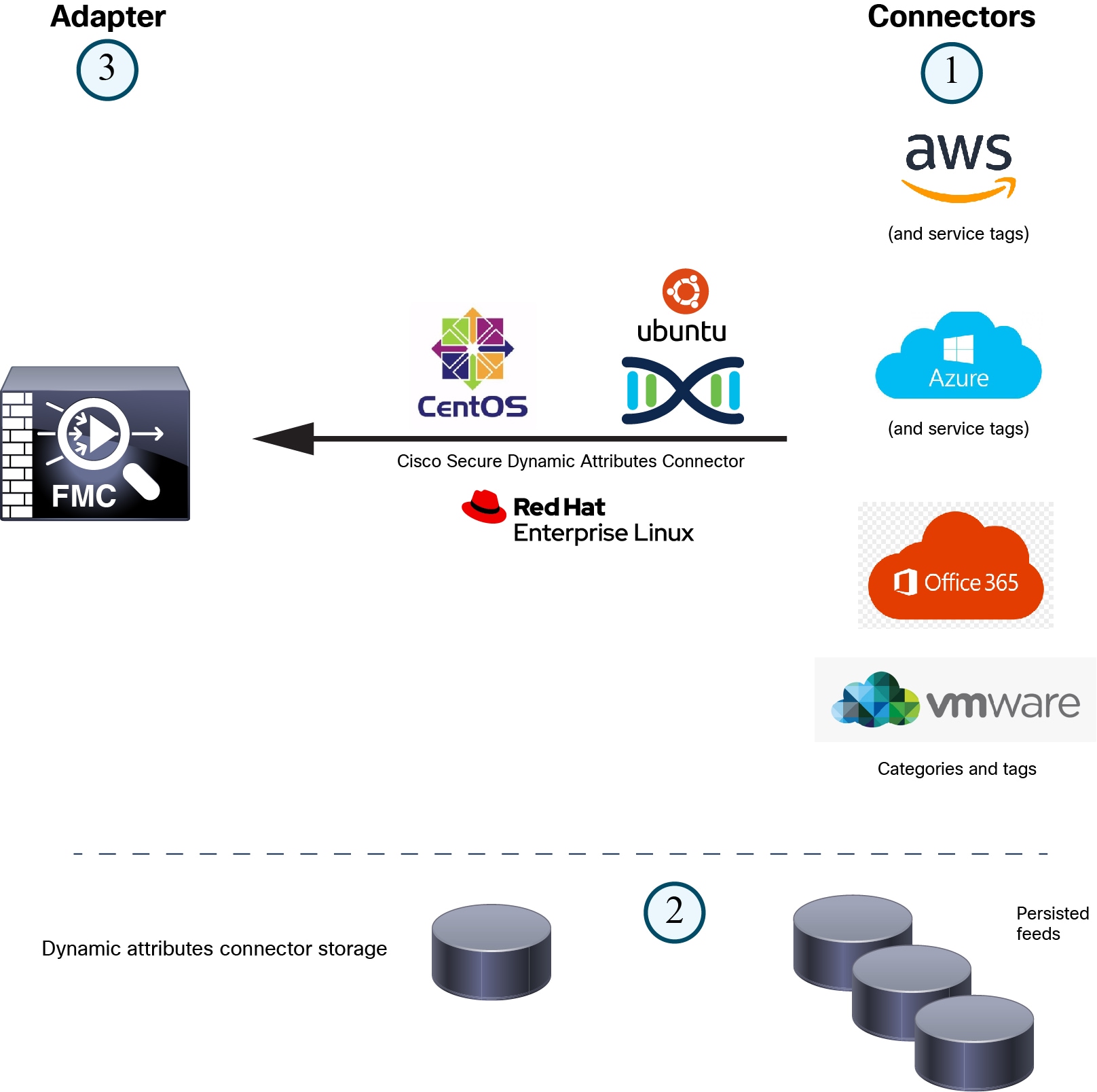
-
Install the dynamic attributes connector on a supported Linux virtual machine.
For more information, see Supported Operating Systems and Third-Party Software.
-
The system supports certain public cloud providers.
This topic discusses supported connectors (which are the connections to those providers).
-
The adapter defined by the dynamic attributes connector receives those dynamic attributes filters as dynamic objects and enables you to use them in access control rules.
You can create the following types of adapters:
-
FMC for an on-premises FMC device.
This type of FMC device might be managed by Cisco Defense Orchestrator (CDO) or it might be a standalone.
-
Cloud-delivered Firewall Management Center for devices managed by CDO.
-
-
Connectors contain the tags and containers to query.
For example, typically these tags define dynamically allocated network and IP addresses for which you cannot create access control rules. Persisted feeds from the connectors are stored on the dynamic attributes connector for fast access.
-
Tag information is persisted on the dynamic attributes connector where you create dynamic attribute filters that define which information is important to use in access control rules.
For example, if AWS defines networks for the Accounting and Finance Departments virtual machines, you can create a dynamic attributes filter that specifies only the Finance network.
-
The adapter defined by the dynamic attributes connector receives those dynamic attributes filters as dynamic objects and enables you to use them in access control rules.
You can create the following types of adapters:
 Feedback
Feedback