Integrate Management Center with the Cisco Security Cloud
Cisco Security Cloud connects your Secure Firewall deployment to the breadth of Cisco's integrated security cloud services for a consistent experience that unifies visibility, enables automation, and strengthens your security across network, endpoints, and applications. Cisco Security Cloud offers a platform approach with simpler, more integrated cloud services that reduce the complexity of managing multiple products.
Use your Cisco Defense Orchestrator (CDO) account to authorize the management center to register to the Cisco Security Cloud and bring your Secure Firewall deployment onboard to the Cisco cloud tenancy. Registering your management center to the CDO enables you to do the following:
-
Establish consistent policy across management centers using shared object management.
-
Zero-Touch Provisioning of the threat defense devices.
-
Send events to the cloud and use various Cisco Security Cloud services to enrich your threat hunts and investigations.
-
Get a centralized view of inventory across management centers.
For more information about onboarding a management center to CDO, see Onboard an On-Prem Management Center.
To integrate the Secure Firewall Management Center with Cisco XDR, see the Cisco Secure Firewall Management Center and Cisco XDR Integration Guide.
Enable Cisco Security Cloud Integration
Integrate the management center with Cisco Security Cloud to onboard both the management center and its managed devices to a CDO tenant. This integration connects the management center to a suite of Cisco cloud services. When the management center is onboarded to CDO, you can view its managed devices, view managed network objects, and cross-launch to the management center UI to manage associated devices and objects.
Before you begin
-
CDO uses Cisco Security Cloud Sign On as its identity provider and Duo for multifactor authentication. Ensure that you have your Cisco Security Cloud Sign On credentials and can sign in to the Cisco regional cloud where your account was created.
-
This task requires a CDO tenant to integrate the management center with Cisco Security Cloud. If you do not already have a CDO tenant, request for a tenant or create one during this workflow. For more information, see Request a CDO Tenant.
-
Link your CDO tenant, the one you want to use for onboarding the management center, to your Security Services Exchange (SSE) account. For more information, see Link Your Cisco Defense Orchestrator and Cisco XDR Tenant Accounts.
-
Your management center must be between version 7.0.2 and 7.0.x, or version 7.2 and later to perform this task.
Procedure
|
Step 1 |
In the management center, choose . |
||
|
Step 2 |
Choose a Cisco regional cloud from the Current Region drop-down list.
|
||
|
Step 3 |
Click Enable Cisco Security Cloud. A separate browser tab opens to log you in to your CDO account. Make sure this page is not blocked by a pop-up blocker. |
||
|
Step 4 |
Click Continue to Cisco SSO. 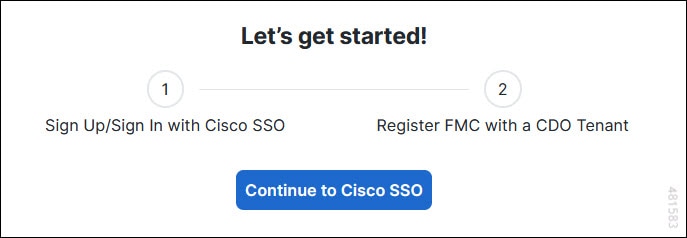
|
||
|
Step 5 |
Log in to your CDO account. 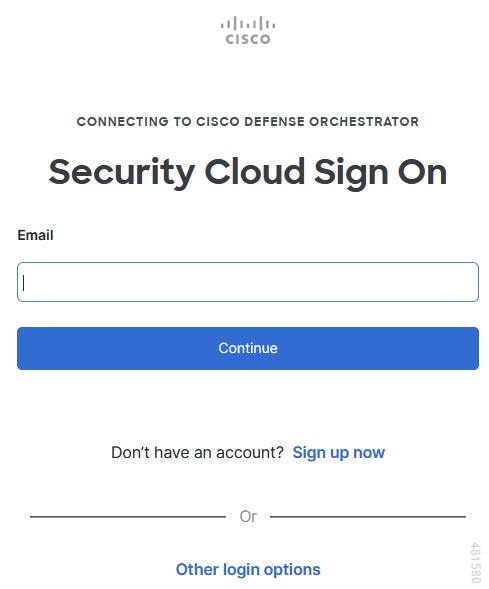
If you do not have a Security Cloud Sign On account to log in to CDO and you want to create one, click Sign up now in the Security Cloud Sign On page. See Create a New Cisco Security Cloud Sign On Account. |
||
|
Step 6 |
Choose a CDO tenant that you want to use for this integration. The management center and the managed devices get onboarded to the CDO tenant that you choose here. 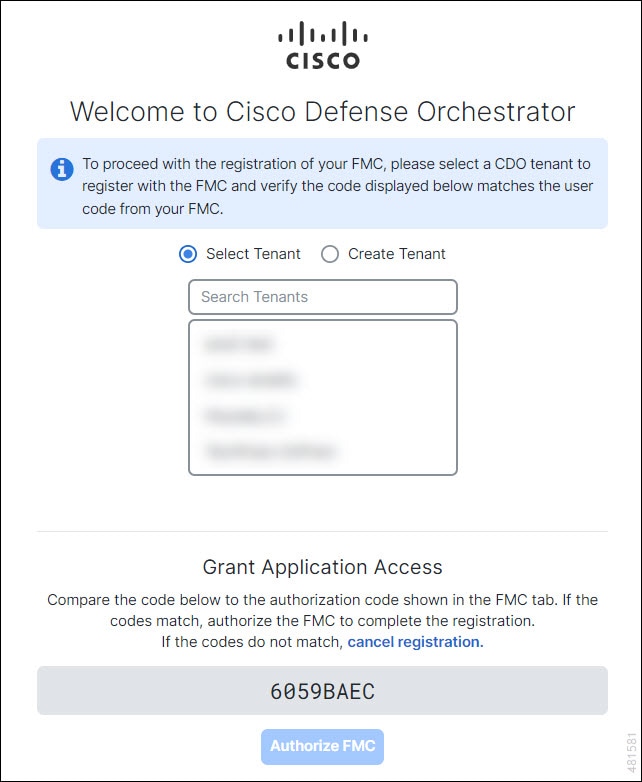
If you do not already have a CDO tenant or if you want to use a new tenant for this integration, create a new tenant. See Request a CDO Tenant for more information. |
||
|
Step 7 |
Verify that the code displayed in the CDO login page matches the code provided by the management center. 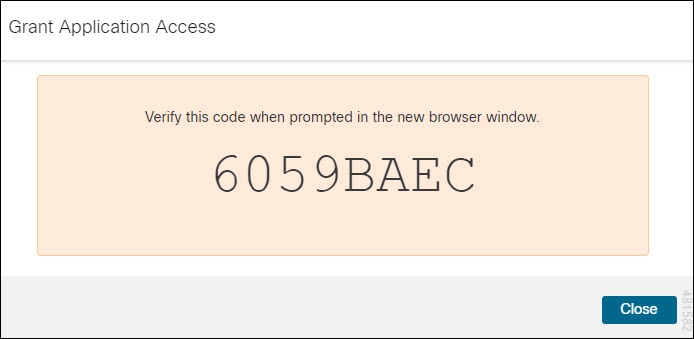
|
||
|
Step 8 |
Click Authorize FMC. |
||
|
Step 9 |
In the management center, configure the following:
|
||
|
Step 10 |
Click Save. |
View Cloud Onboarding Status of the Management Center
When you enable Cisco Security Cloud integration, the management center will be onboarded to the selected CDO tenant. On the Cisco Security Cloud Integration page, Cloud Onboarding Status displays the status of your management center onboarding to CDO. The following table describes the cloud onboarding statuses:
|
Status |
Description |
|---|---|
|
Online |
The management center is onboarded to CDO. |
|
Onboarding |
The cloud onboarding task is in progress. This could take up to 10 minutes to complete. |
|
Error on CDO |
An error has occurred on CDO while onboarding the management center to the cloud. Try enabling Cisco Security Cloud integration after some time. |
|
Not Available |
Either the management center is removed from CDO or the cloud onboarding task has not started and CDO has not discovered the management center yet. Try enabling Cisco Security Cloud again. |
|
Unreachable - Onboarded, but currently unable to communicate with management center |
The management center was successfully onboarded to CDO, but CDO cannot communicate with the management center. From CDO, try reconnecting to the management center. For more information, see Managing On-Prem Firewall Management Center with Cisco Defense Orchestrator. |
|
Failed to get status |
The management center cannot request CDO for the status due to a cloud connectivity error. Refresh the Cisco Security Cloud Integration page after sometime to check the status. If the issue persists, try enabling Cisco Security Cloud again. |
 Note |
After enabling Cisco Security Cloud integration, it could take upto 90 seconds to complete the registration of management center with the Cisco Security Cloud. If the Cloud Onboarding Status does not appear after you enable Cisco Security Cloud integration, refresh the Cisco Security Cloud Integration page. |
Use Cisco AI Assistant for Security to Manage Your Threat Defense Devices Effectively
The Cisco AI Assistant for Security in your management center is built on generative artificial intelligence and natural language processing technologies. You can use it to:
-
Seek assistance with various tasks associated with your management center.
-
Ensure that your configuration aligns with best practices and security requirements.
-
Provide descriptions of policies and identify policy components and attributes.
 Note |
|
Enable Cisco AI Assistant for Security
Before you begin
-
Ensure that you have administrator privileges in the management center.
-
Ensure that you have enabled Cisco Security Cloud () in the management center.
Procedure
|
Step 1 |
Click . |
|
Step 2 |
Under the Cisco AI Assistant for Security section, check the Enable Cisco AI Assistant for Security check box. Once you enable the AI assistant, you can find it ( 
|
Seek Assistance Using Cisco AI Assistant for Security
Before you begin
-
Ensure that you have administrator privileges in the management center.
-
Ensure that you have enabled Cisco AI Assistant for Security () in the management center.
Procedure
|
Step 1 |
From the management center menu bar, click the Cisco AI Assistant for Security ( 
If you are opening the AI assistant for the first time, a carousel window appears. |
|
Step 2 |
(One-time activity) Review the content on the carousel window and click Launch AI Assistant. |
|
Step 3 |
In the AI assistant window, select one of the available suggestions or enter your own question in the text field, and click
Send Message ( For more information, see the AI Assistant User Guide. |
Configure Management Center to Share Usage Metrics and Statistics with Cisco
Cisco Success Network is a cloud service that enables the management center to establish a secure connection to Cisco cloud and stream usage information and statistics. Streaming this telemetry provides a mechanism to select data of interest from the threat defense device and send it in a structured format to remote management stations for the following reasons:
-
To inform you of available, but unused features that can improve the effectiveness of the product in your network.
-
To inform you of additional technical support services and monitoring that are available for your product.
-
To help Cisco improve its products.
To know more about the telemetry data that Cisco collects, see Cisco Success Network Telemetry Data Collected from Cisco Secure Firewall Management Center Devices.
 Note |
|
Before you begin
Enable Cisco security cloud integration or register your management center with the Smart License to perform this task.
Procedure
|
Step 1 |
Click . |
||
|
Step 2 |
Under Cisco Security Cloud Support, check the Enable Cisco Success Network check box to enable this service.
|
||
|
Step 3 |
Click Save. |
Configure Management Center to Share Device Health Data with Cisco
Cisco Support Diagnostics is a cloud-based TAC support service that enables the management center and the managed devices to establish a secure connection with the Cisco cloud and send device health-related information to the cloud. This feature is enabled by default.
Cisco Support Diagnostics provides an enhanced user experience during troubleshooting by allowing Cisco TAC to securely collect essential data from your device during the resolution of a TAC case. Moreover, Cisco periodically collects health data, and processes this data using an automated problem-detection system to notify you of issues if any. While data collection service during the resolution of a TAC case is available for all users with support contracts, the notification service is available only to users with specific service contracts.
Cisco Support Diagnostics allows both threat defense devices and the management center to establish and maintain secure connections with the Cisco cloud. The management center sends the collected data to the regional cloud selected on the Cisco Security Cloud Integration page.
Administrators can view a sample data set collected from the management center by following the steps in Producing Troubleshooting Files for Specific System Functions.
Before you begin
Enable Cisco Security Cloud integration or register your management center with the Smart License to perform this task.
Procedure
|
Step 1 |
Click . |
||
|
Step 2 |
Under Cisco Security Cloud Support, check the Enable Cisco Support Diagnostics check box to enable this service.
|
||
|
Step 3 |
Click Save. |










 Feedback
Feedback