About Users
You can add custom user accounts on managed devices, either as internal users or as external users on a LDAP or RADIUS server. Each managed device maintains separate user accounts. For example, when you add a user to the management center, that user only has access to the management center; you cannot then use that username to log directly into a managed device. You must separately add a user on the managed device.
Internal and External Users
Managed devices support two types of users:
-
Internal user—The device checks a local database for user authentication.
-
External user—If the user is not present in the local database, the system queries an external LDAP or RADIUS authentication server.
Web Interface and CLI Access
The management center has a web interface, CLI (accessible from the console (either the serial port or the keyboard and monitor) or using SSH to the management interface), and Linux shell. For detailed information about the management UIs, see System User Interfaces.
See the following information about management center user types, and which UI they can access:
-
admin user—The management center supports two different internal admin users: one for the web interface, and another with CLI access. The system initialization process synchronizes the passwords for these two admin accounts so they start out the same, but they are tracked by different internal mechanisms and may diverge after initial configuration. See the Getting Started Guide for your model for more information on system initialization. (To change the password for the web interface admin, use System (
 ) > Users. To change
the password for the CLI admin, use the
management center CLI command configure
password .)
) > Users. To change
the password for the CLI admin, use the
management center CLI command configure
password .)
-
Internal users—Internal users added in the web interface have web interface access only.
-
External users—External users have web interface access, and you can optionally configure CLI access.
-
SSO users—SSO users have web interface access only.
 Caution |
CLI users can access the Linux shell using the
expert command. We
strongly recommend that you do not use the Linux
shell unless directed by Cisco TAC or explicit
instructions in the management center documentation. CLI users can obtain
|
User Roles
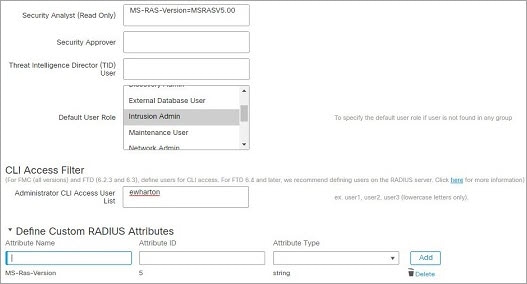
CLI User Role
CLI external users on the management center do not have a user role; they can use all available commands.
Web Interface User Roles
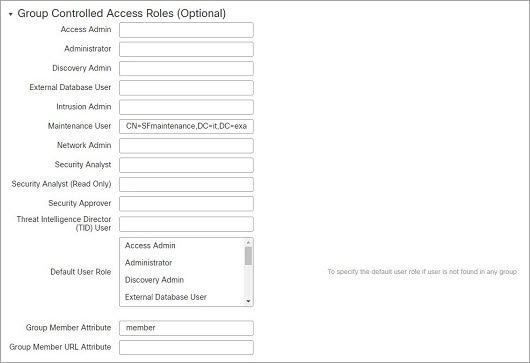
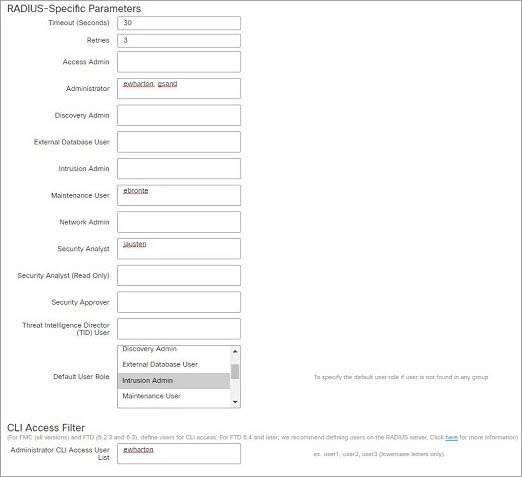
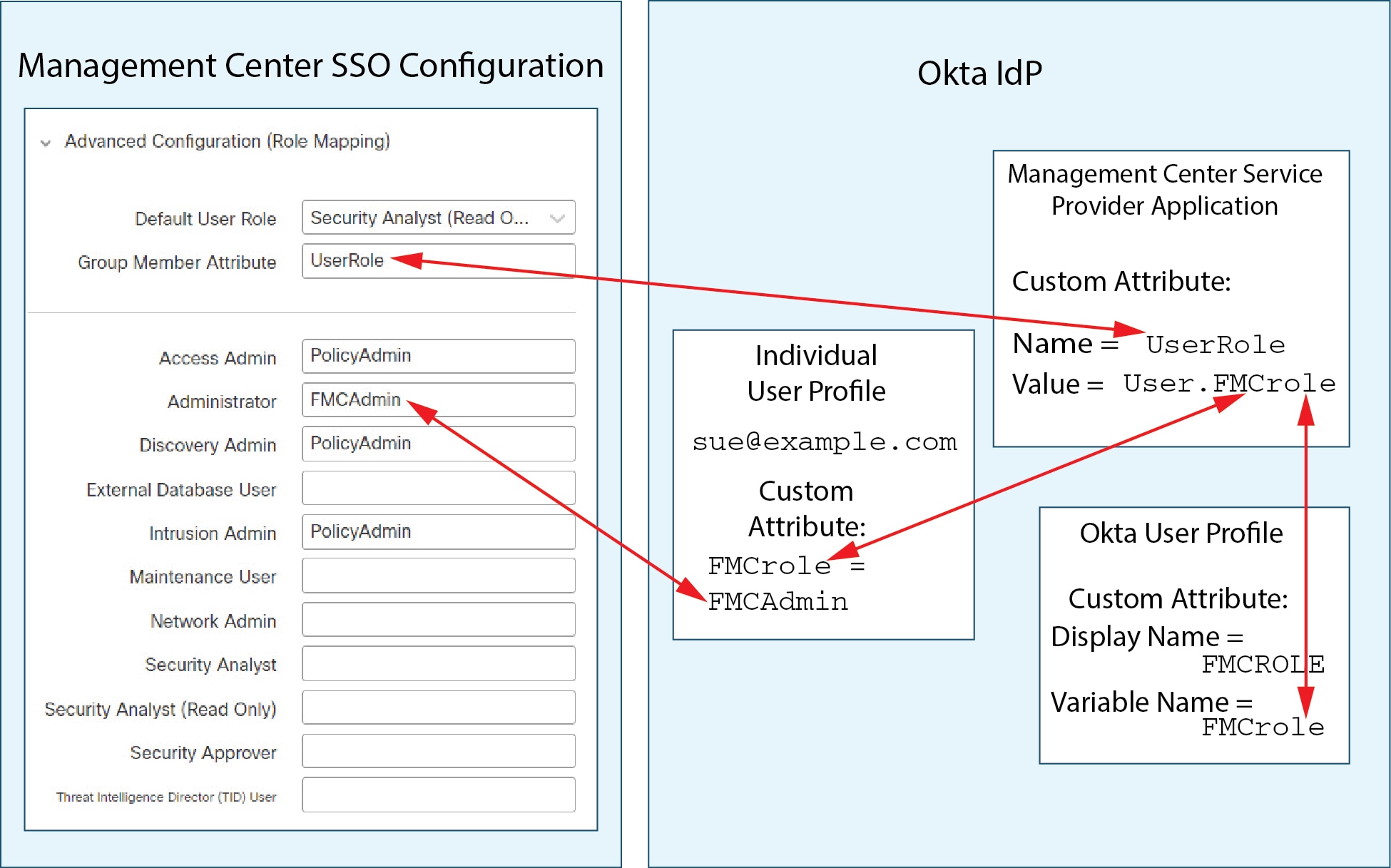
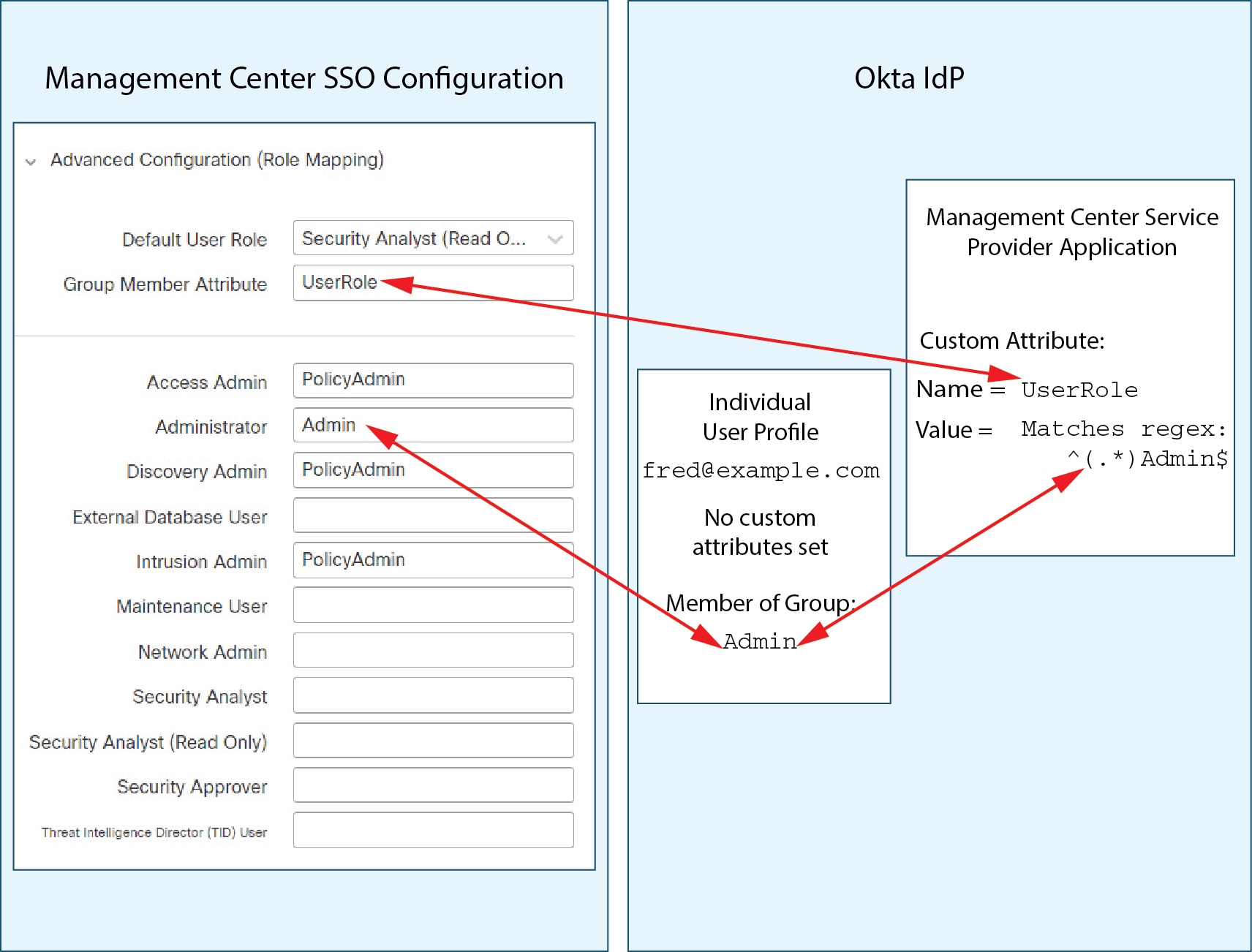
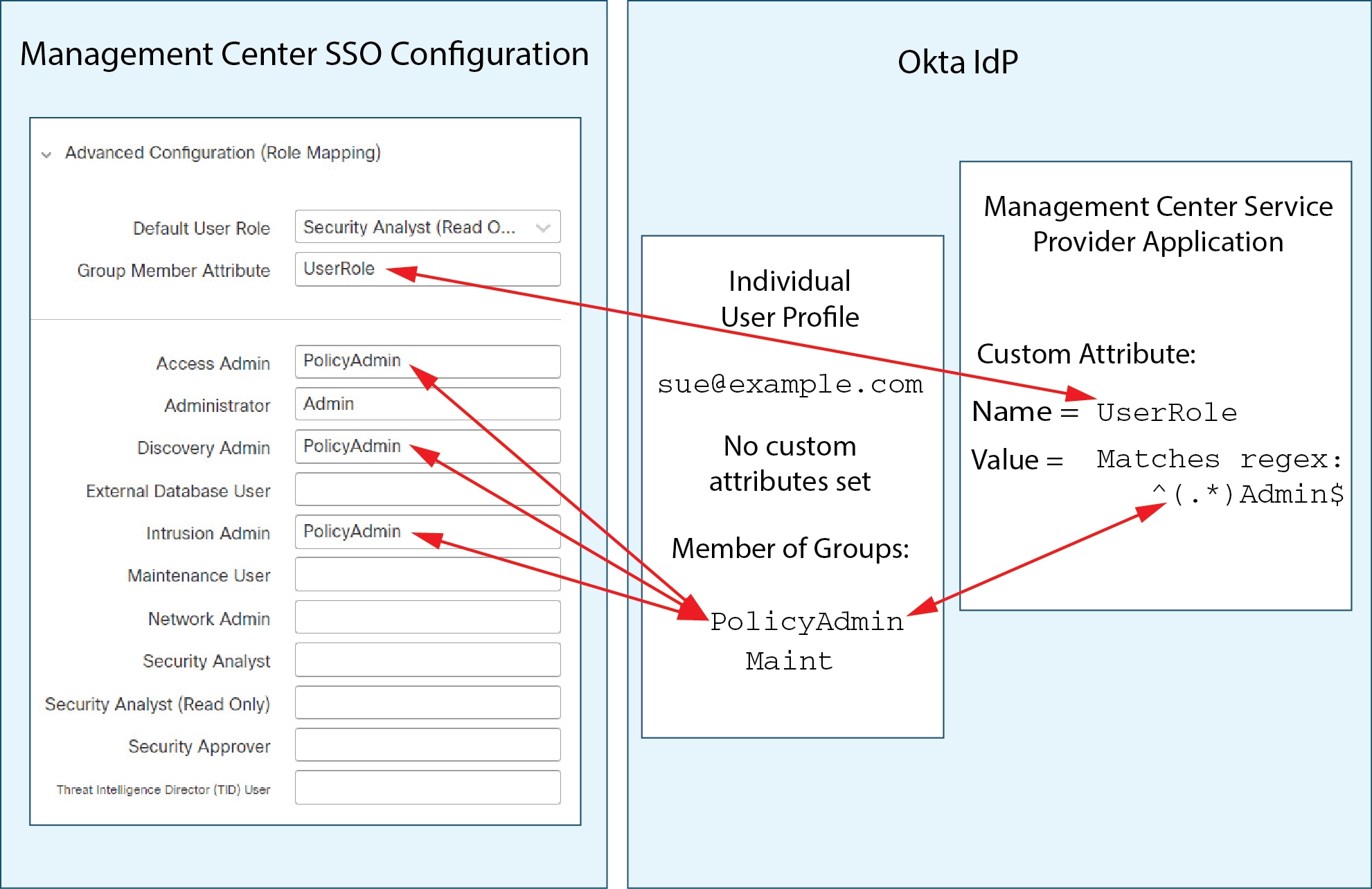
User privileges are based on the assigned user role. For example, you can grant analysts predefined roles such as Security Analyst and Discovery Admin and reserve the Administrator role for the security administrator managing the device. You can also create custom user roles with access privileges tailored to your organization’s needs.
To view the privileges assigned to predefined user roles, click Copy ( ) for a role as though you are going to make a custom role based on the predefined role. You can then see all of the privileges
assigned.
) for a role as though you are going to make a custom role based on the predefined role. You can then see all of the privileges
assigned.
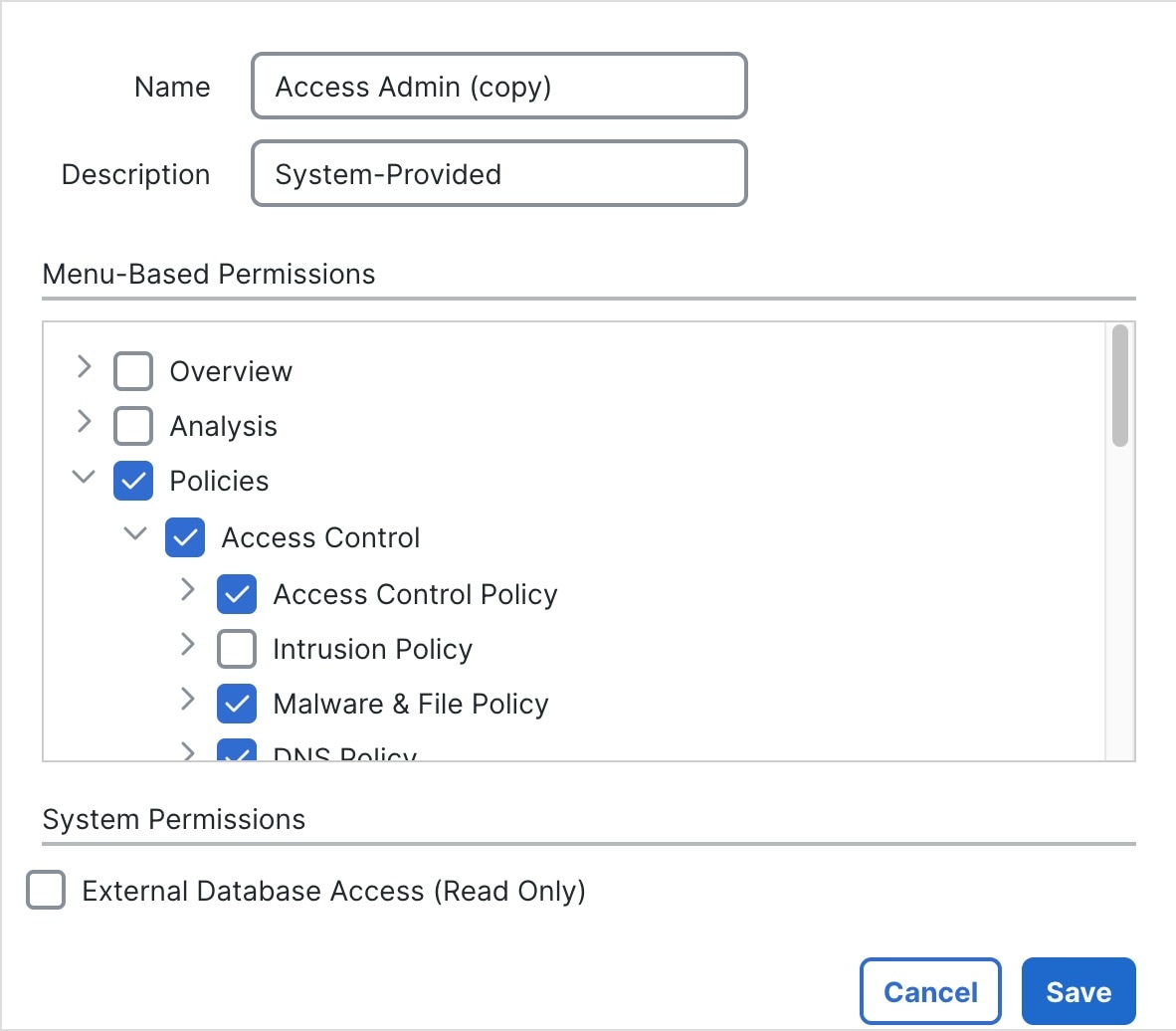
The management center includes the following predefined user roles:
- Access Admin
-
Provides access to access control policy and associated features in the Policies menu. Access Admins cannot deploy policies.
- Administrator
-
Administrators have access to everything in the product; their sessions present a higher security risk if compromised, so you cannot make them exempt from login session timeouts.
You should limit use of the Administrator role for security reasons.
- Discovery Admin
-
Provides access to network discovery, application detection, and correlation features in the Policies menu. Discovery Admins cannot deploy policies.
- External Database User (Read Only)
-
Provides read-only access to the database using an application that supports JDBC SSL connections. For the third-party application to authenticate to the appliance, you must enable database access in the system settings. On the web interface, External Database Users have access only to online help-related options in the Help menu. Because this role’s function does not involve the web interface, access is provided only for ease of support and password changes.
- Intrusion Admin
-
Provides access to all intrusion policy, intrusion rule, and network analysis policy features in the Policies and Objects menus. Intrusion Admins cannot deploy policies.
- Maintenance User
-
Provides access to monitoring and maintenance features. Maintenance Users have access to maintenance-related options in the Health and System menus.
- Network Admin
-
Provides access to access control, SSL inspection, DNS policy, and identity policy features in the Policies menu, as well as device configuration features in the Devices menus. Network Admins can deploy configuration changes to devices.
- Security Analyst
-
Provides access to security event analysis features, and read-only access to health events, in the Overview, Analysis, Health, and System menus.
- Security Analyst (Read Only)
-
Provides read-only access to security event analysis features and health event features in the Overview, Analysis, Health, and System menus.
User with this role can also:
-
From the health monitor pages for specific devices, generate and download troubleshooting files.
-
Under user preferences, set file download preferences.
-
Under user preferences, set the default time window for event views (with the exception of the Audit Log Time Window).
-
- Security Approver
-
Provides limited access to access control and associated policies and network discovery policies in the Policies menu. Security Approvers can view and deploy these policies, but cannot make policy changes.
- Threat Intelligence Director (TID) User
-
Provides access to Threat Intelligence Director configurations in the Intelligence menu. Threat Intelligence Director (TID) Users can view and configure TID.
User Passwords
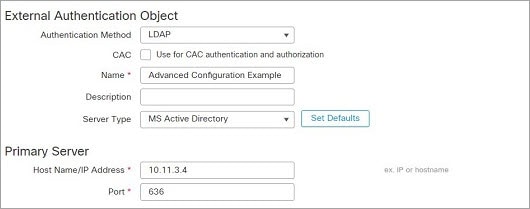
The following rules apply to passwords for internal user accounts on the management center, with Lights-Out Management (LOM) enabled or disabled. Different password requirements apply for externally authenticated accounts or in systems with security certifications compliance enabled. See Configure External Authentication for the Management Center and Security Certifications Compliance for more information.
During management center initial configuration, the system requires the admin user to set the account password to comply with strong password requirements described in the table below. For physical management centers, the strong password requirements with LOM enabled are used, and for virtual management centers, the strong password requirements with LOM not enabled are used. At this time the system synchronizes the passwords for the web interface admin and the CLI access admin. After initial configuration, the web interface admin can remove the strong password requirement, but the CLI access admin must always comply with strong password requirements with LOM not enabled.
|
LOM Not Enabled |
LOM Enabled |
|
|---|---|---|
|
Password Strength Checking On |
Passwords must include:
The system checks passwords against a special dictionary containing not only many English dictionary words, but also other character strings that could be easily cracked with common password hacking techniques. |
Passwords must include:
The rules for special characters vary between different series of physical management centers. We recommend restricting your choice of special characters to those listed in the final bullet above. Do not include the user name in the password. The system checks passwords against a special dictionary containing not only many English dictionary words, but also other character strings that could be easily cracked with common password hacking techniques. |
|
Password Strength Checking Off |
Passwords must include the minimum number of characters configured for the user by the administrator. (See Add or Edit an Internal User for more information.) |
Passwords must include:
The rules for special characters vary between different series of physical management centers. We recommend restricting your choice of special characters to those listed in the final bullet above. Do not include the user name in the password. |
Users and Domains
In a multidomain deployment, you can create user accounts in any domain in which you have been assigned Administrator access.
User Roles in Domains
Users can have different privileges in each domain. You can assign user roles in both ancestor and descendant domains. For example, you can assign read-only privileges to a user in the Global domain, but Administrator privileges in a descendant domain:

User Management
Users are only visible in the domain in which they are created.
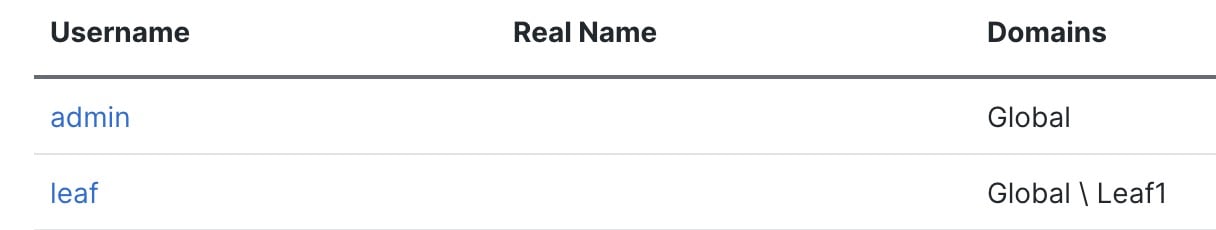
If you add a user in the current domain but assign a user role in a subdomain, then that user will only show on the current domain's Users page, even though the user has a role in a subdomain. For example, from the Global domain, you add user leaf and assign a role for Leaf1, but because you were in the Global domain when you added the user, you can see it from the Global domain:
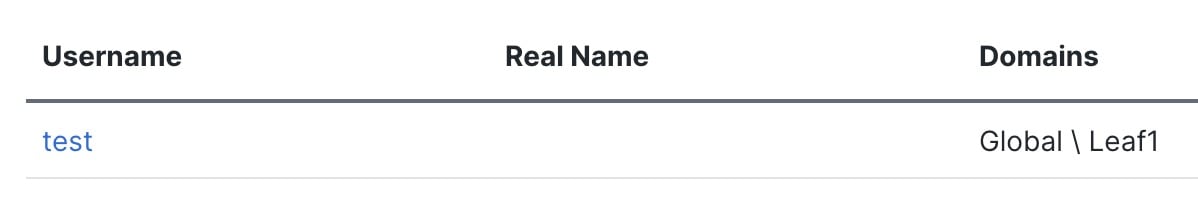
If you change domains to Leaf1, you cannot see the user leaf, but you can see the user test, which was added directly from the Leaf1 subdomain:
Logging In
Users added from the Global domain will log in with just their username, even if their roles are only in a subdomain. In this case, leaf only has a user role in the Leaf1 subdomain, but because it was added from Global, do not include the subdomain in the login:

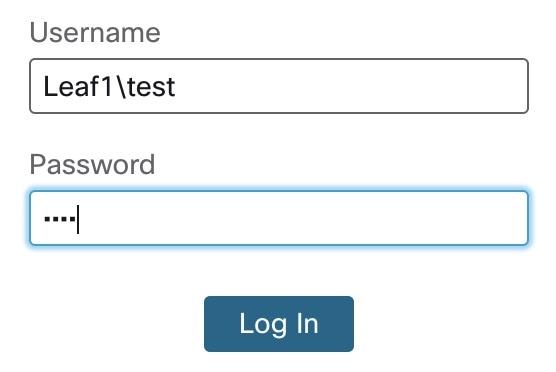
Users added directly in a subdomain need to log into the management center with the subdomain(s) as part of the login name, depending on which domain their user was added from: subdomain1\subdomain2\username. You do not need to enter the Global parent domain. For example, test was added from the Leaf1 subdomain, so you need to include Leaf1 in the login name:
When you log in, you are placed in the domain where your username was added. For example, the admin user defaults to the Global domain:
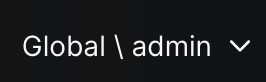
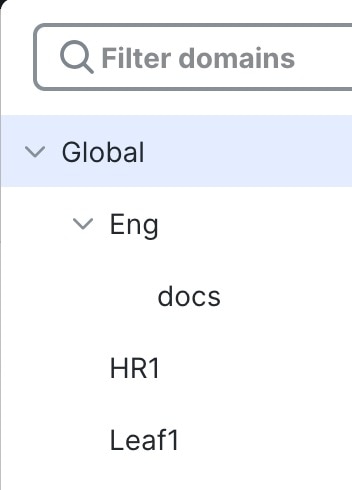
However, after login, you can change to a subdomain by clicking the down arrow:







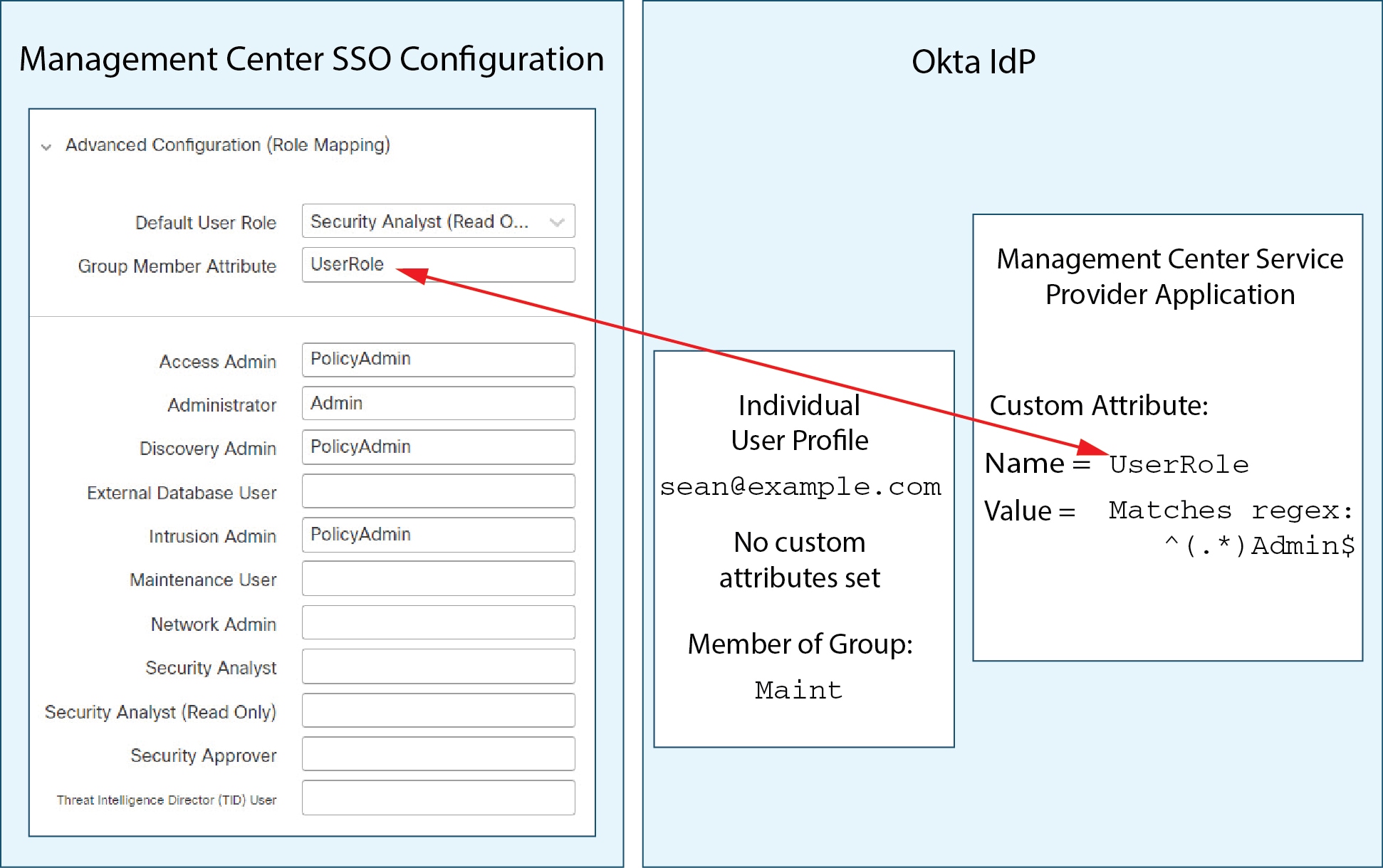

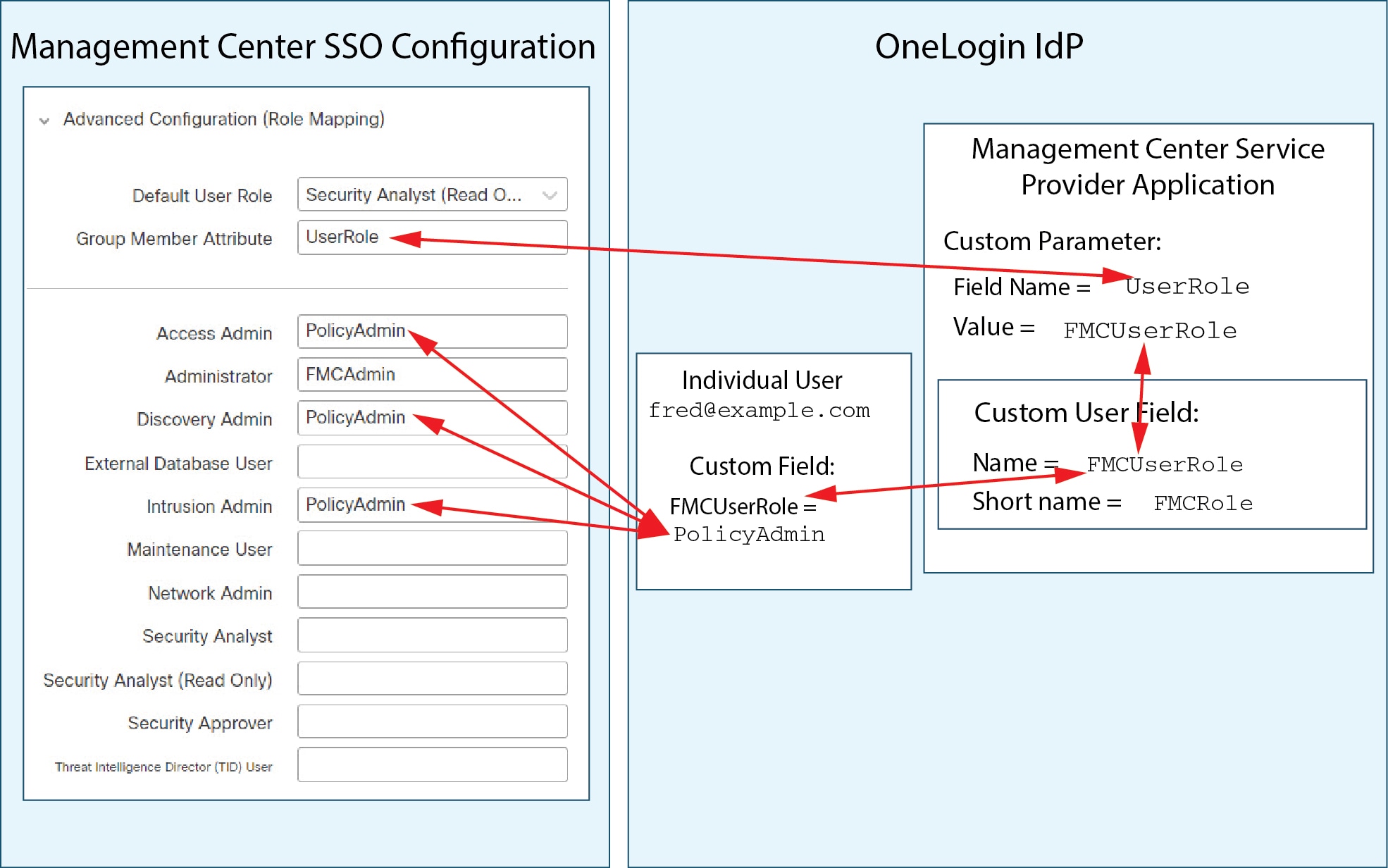
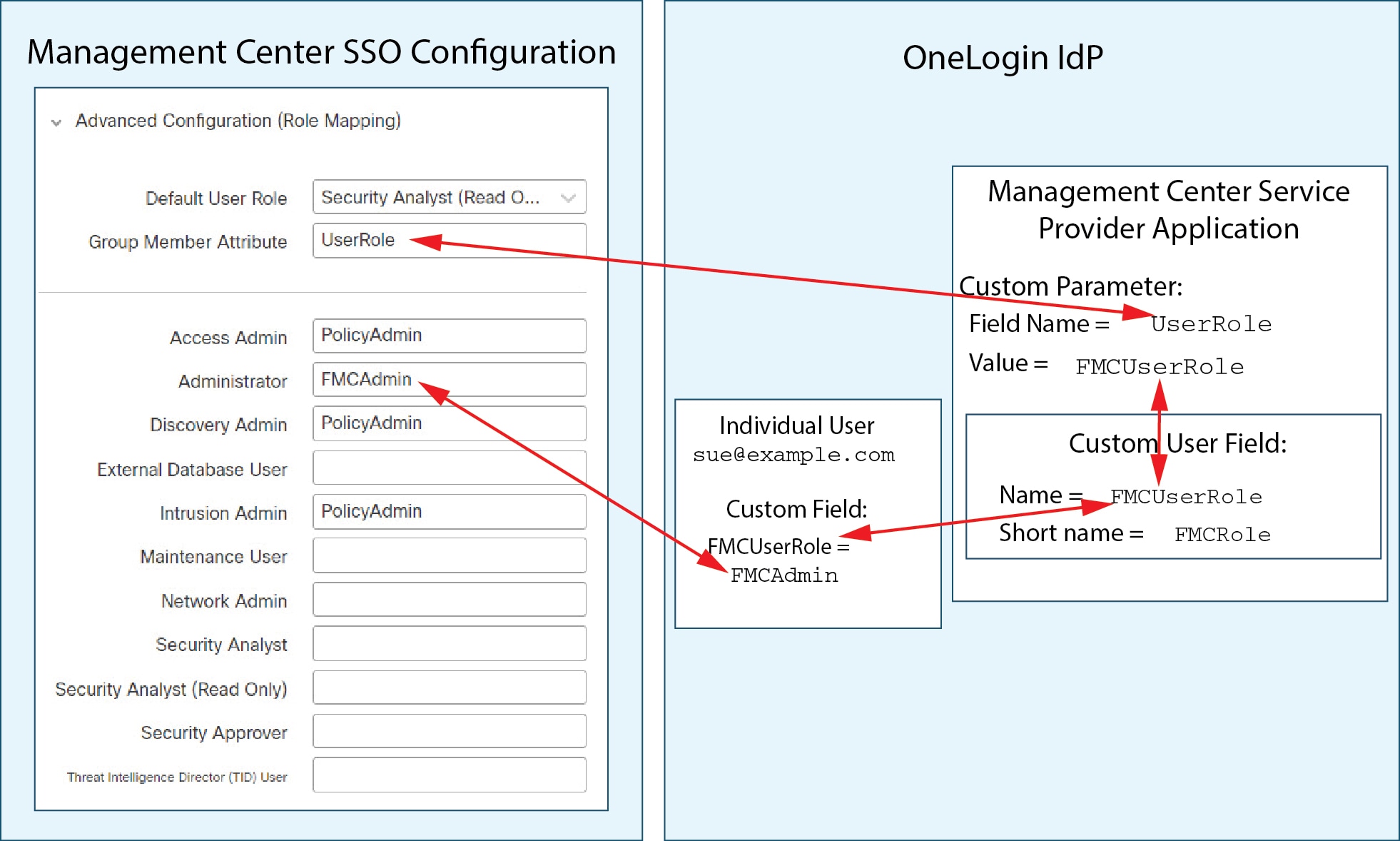


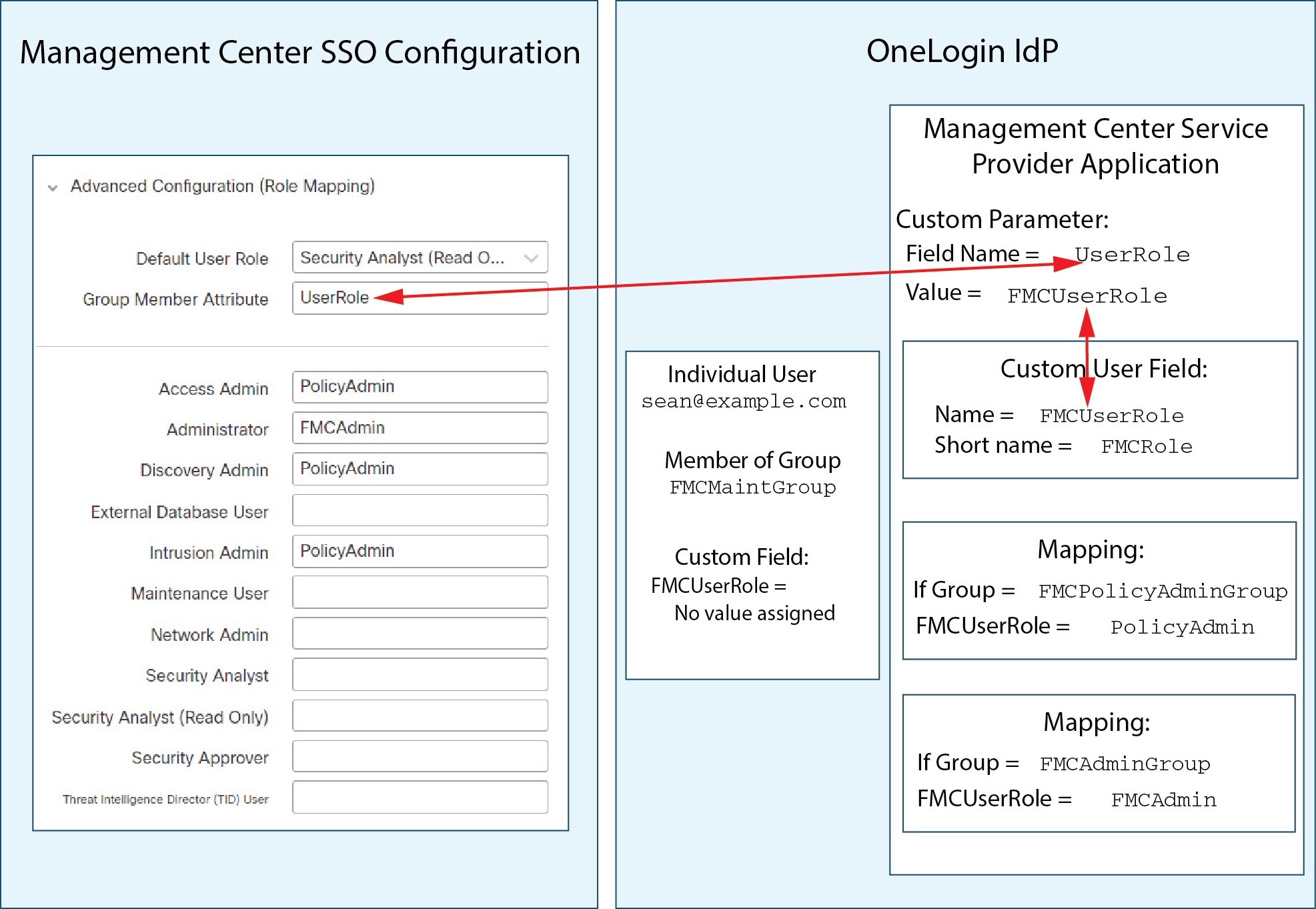







 Feedback
Feedback