TLS/SSL Rules Best Practices
This chapter provides an example SSL policy with TLS/SSL rules that illustrates our best practices and recommendations. First we'll discuss settings for the SSL and access control policies and then walk through all the rules and why we recommend they be ordered in a particular way.
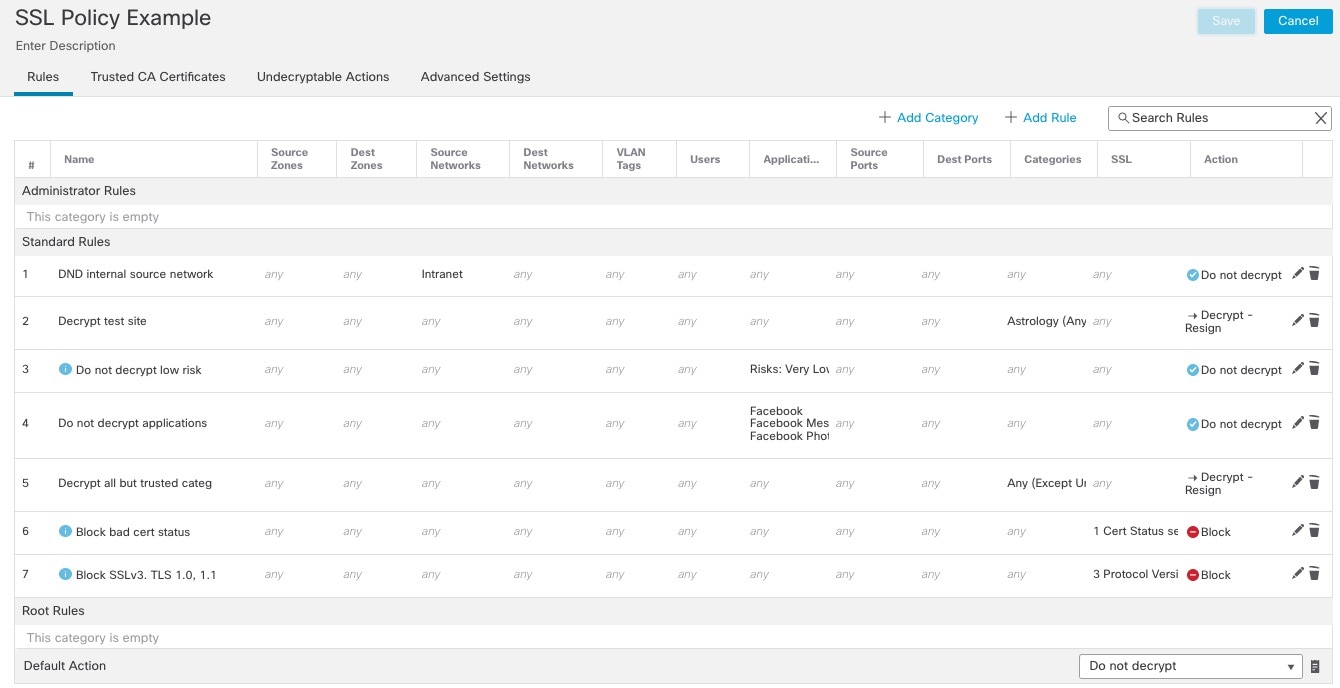
Following is the SSL policy we'll discuss in this chapter.

 Feedback
Feedback