Overview
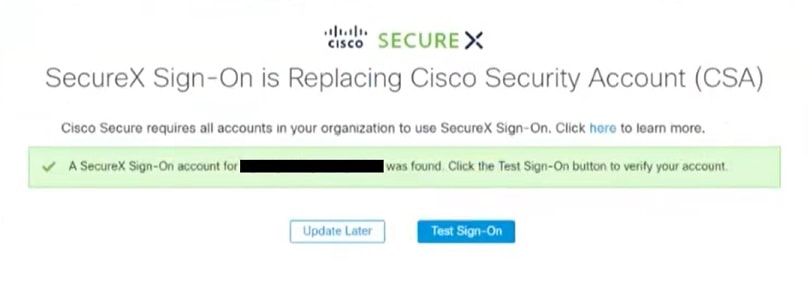
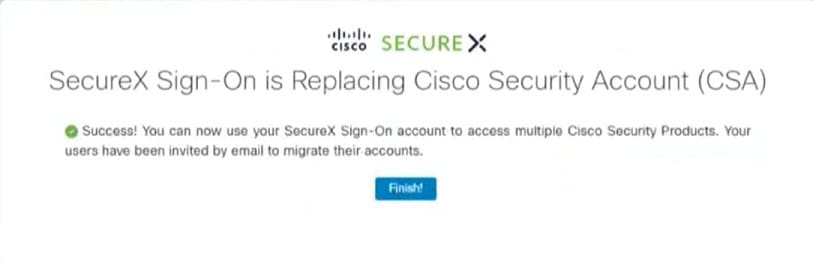
Starting in August 2021, all users with a Cisco Security Accounts (CSA) account must be updated to use a SecureX sign-on account instead. This affects all users that sign in with CSA to access Cisco Security products such as:
-
Cisco Secure Endpoint (formerly Advanced Malware Protection for Endpoints)
-
Global Threat Alerts (formerly Cognitive Intelligence and Cognitive Threat Analytics)
-
Orbital
-
SecureX
CSA will be retired, so going forward, you'll use SecureX sign-on to access SecureX and other Cisco Security products. How you'll update your account depends on your account role in your organization and whether you already have a SecureX sign-on account delegated as your single sign-on for CSA. To proceed, choose one of the following options:







 Feedback
Feedback