- High Availability Installation Guide for Cisco Security Manager
- Contents
- Preface
- Overview
- System Requirements
- Installing the Cisco Security Management Suite High Availability Solution
- Maintenance Activities
- VCS Resource Views for the Reference Configurations
- High Availability and Disaster Recovery Certification Test Plan
- Index
Overview
This document explains how to install Cisco Security Management Suite (Security Manager) in a high availability (HA) or disaster recovery (DR) environment. The Security Manager HA/DR solution is based on Symantec’s Veritas Storage Foundation and High Availability solutions. The Security Manager HA/DR solutions described in this guide support the following applications:

Note![]() Since devices contact the AUS server directly using the AUS server IP address, it is necessary for the device to support defining up to two AUS servers for a DR configuration, where the AUS server at each site has a different IP address. Defining more than one AUS server IP address is supported only by the ASA 5500 Series beginning with release 7.2.1.
Since devices contact the AUS server directly using the AUS server IP address, it is necessary for the device to support defining up to two AUS servers for a DR configuration, where the AUS server at each site has a different IP address. Defining more than one AUS server IP address is supported only by the ASA 5500 Series beginning with release 7.2.1.
The HA solution supports both local redundancy (HA) and geographic redundancy (DR) configurations.

Note![]() Cross-launching the Cisco Prime Security Manager (PRSM) application is supported in both HA and DR configurations; however, seamless, direct access to PRSM from Security Manager using the “single sign-on” (SSO) feature is only supported in HA mode.
Cross-launching the Cisco Prime Security Manager (PRSM) application is supported in both HA and DR configurations; however, seamless, direct access to PRSM from Security Manager using the “single sign-on” (SSO) feature is only supported in HA mode.
Local Redundancy (HA) Process Overview
The local redundancy configuration provides an automatic failover solution in the event of software or hardware failures without the need to reconfigure IP addresses or DNS entries on your switched/routed network.
Figure 1-1 illustrates the local redundancy HA configuration.

Note![]() The servers in Figure 1-1 optionally contain mirrored internal boot disks. We recommend that they be the same make, model, and storage capacity. We recommend a fault-tolerant switched/routed network for communicating with the HA servers.
The servers in Figure 1-1 optionally contain mirrored internal boot disks. We recommend that they be the same make, model, and storage capacity. We recommend a fault-tolerant switched/routed network for communicating with the HA servers.
Figure 1-1 Local Redundancy HA Configuration
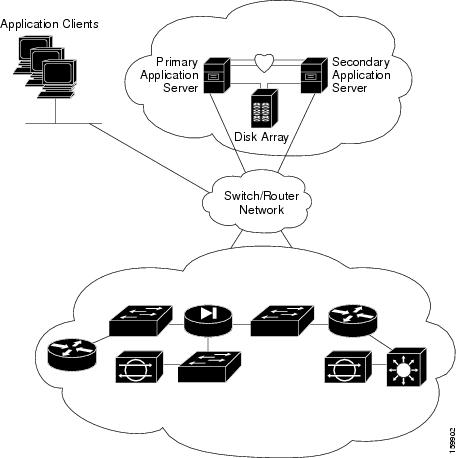
Local Redundancy (HA) Configuration Steps
The following table lists the steps required to configure a locally redundant installation of Cisco Security Manager.
Geographic Redundancy (DR) Process Overview
The geographic redundancy configuration provides disaster recovery by replicating application data between two sites. Failover between sites can be initiated manually or performed automatically.
Figure 1-2 illustrates a geographic redundancy (DR) configuration.

Note![]() The servers in Figure 1-2 optionally contain mirrored internal boot disks. We recommend that they be the same make, model, and storage capacity. We recommend a fault-tolerant switched/routed network for communicating with the servers.
The servers in Figure 1-2 optionally contain mirrored internal boot disks. We recommend that they be the same make, model, and storage capacity. We recommend a fault-tolerant switched/routed network for communicating with the servers.
Figure 1-2 Geographic Redundancy (DR) Configuration
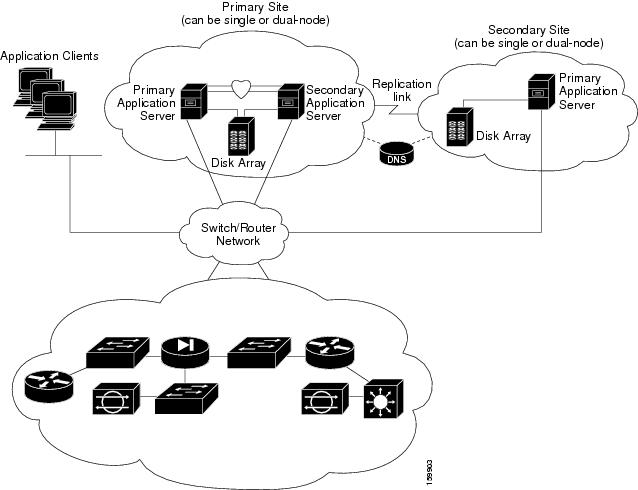
Geographic Redundancy (DR) Configuration Steps
The following table lists the steps required to configure a geographically redundant installation of Cisco Security Manager.
Symantec Veritas Products
The Security Manager HA/DR solutions described in this document are based on Symantec Veritas products. This section gives a brief summary of each specific Veritas application.
VSFW provides volume management technology, quick recovery, and fault tolerant capabilities to Windows enterprise computing environments. VSFW provides the foundation for VCS and VVR.
VCS is a clustering solution for reducing application downtime. The Global Cluster Option (GCO) for VCS supports managing multiple clusters (such as used in a DR configuration).
VVR provides a foundation for continuous data replication over IP networks, enabling rapid and reliable recovery of critical applications at remote recovery sites.
The VEA GUI console window provides a graphical way to view and manipulate all the storage objects in your system.
Cluster Manager (Java Console) offers complete administration capabilities for your cluster. Use the different views in the Java Console to monitor clusters and VCS objects, including service groups, systems, resources, and resource types:
Cluster Monitor displays general information about actual or simulated clusters. Use Cluster Monitor to log on to and off of a cluster, view summary information on various VCS objects, customize the display, use VCS Simulator, and exit Cluster Manager.
Cluster Explorer is the main window for cluster administration. From this window, you can view the status of VCS objects and perform various operations.
 Feedback
Feedback