The IPv6 Neighbor Discovery Inspection, or IPv6 "snooping," feature bundles several Layer 2 IPv6 first-hop security features,
including IPv6 Address Glean and IPv6 Device Tracking. IPv6 neighbor discovery (ND) inspection operates at Layer 2, or between
Layer 2 and Layer 3, and provides IPv6 features with security and scalability. This feature mitigates some of the inherent
vulnerabilities for the neighbor discovery mechanism, such as attacks on duplicate address detection (DAD), address resolution,
device discovery, and the neighbor cache.
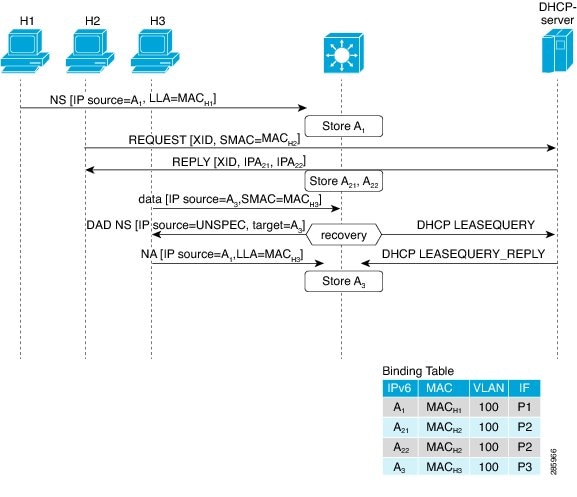
IPv6 ND inspection learns and secures bindings for stateless autoconfiguration addresses in Layer 2 neighbor tables and analyzes
ND messages in order to build a trusted binding table. IPv6 ND messages that do not have valid bindings are dropped. An ND
message is considered trustworthy if its IPv6-to-MAC mapping is verifiable.
When IPv6 ND inspection is configured on a target (which varies depending on platform target support and may include device
ports, switch ports, Layer 2 interfaces, Layer 3 interfaces, and VLANs), capture instructions are downloaded to the hardware
to redirect the ND protocol and Dynamic Host Configuration Protocol (DHCP) for IPv6 traffic up to the switch integrated security
features (SISF) infrastructure in the routing device. For ND traffic, messages such as NS, NA, RS, RA, and REDIRECT are directed
to SISF. For DHCP, UDP messages sourced from port 546 or 547 are redirected.
IPv6 ND inspection registers its "capture rules" to the classifier, which aggregates all rules from all features on a given
target and installs the corresponding ACL down into the platform-dependent modules. Upon receiving redirected traffic, the
classifier calls all entry points from any registered feature (for the target on which the traffic is being received), including
the IPv6 ND inspection entry point. This entry point is the last to be called, so any decision (such as drop) made by another
feature supersedes the IPv6 ND inspection decision.
 Feedback
Feedback