- Preface
- Product Overview
- Command-Line Interfaces
- Configuring the Switch for the First Time
- Administering the Switch
- Configuring the Cisco IOS In Service Software Upgrade Process
- Configuring Interfaces
- Checking Port Status and Connectivity
- Configuring Supervisor Engine Redundancy Using RPR and SSO
- Configuring Cisco NSF with SSO Supervisor Engine Redundancy
- Environmental Monitoring and Power Management
- Configuring Power over Ethernet
- Configuring the Catalyst 4500 Series Switch with Cisco Network Assistant
- Configuring VLANs, VTP, and VMPS
- Configuring IP Unnumbered Interface
- Configuring Layer 2 Ethernet Interfaces
- Configuring SmartPort Macros
- Configuring STP and MST
- Configuring Flex Links and Flex Links+
- Configuring Resilient Ethernet Protocol
- Configuring Optional STP Features
- Configuring EtherChannel
- Configuring IGMP Snooping and Filtering
- Configuring IPv6 MLD Snooping
- Configuring 802.1Q and Layer 2 Protocol Tunneling
- Configuring CDP
- Configuring LLDP
- Configuring UDLD
- Configuring Unidirectional Ethernet
- Configuring Layer 3 Interfaces
- Configuring Cisco Express Forwarding
- Configuring Unicast Reverse Path Forwarding
- Configuring IP Multicast
- Configuring Policy-Based Routing
- Configuring VRF-lite
- Configuring Quality of Service
- Configuring Voice Interfaces
- Configuring Private VLANs
- Configuring 802.1X Port-Based Authentication
- Configuring Port Security
- Configuring Control Plane Policing
- Configuring DHCP Snooping, IP Source Guard, and IPSG for Static Hosts
- Configuring Dynamic ARP Inspection
- Configuring Network Security with ACLs
- Port Unicast and Multicast Flood Blocking
- Configuring Storm Control
- Configuring SPAN and RSPAN
- Configuring System Message Logging
- Configuring SNMP
- Configuring NetFlow
- Configuring Cisco IP SLA
- Configuring RMON
- Performing Diagnostics
- Configuring WCCP Version 2 Services
- ROM Monitor
- Configuring MIB Support
- Configuring CFM and OAM
- Configuring Y.1731
- Acronym
- Index
- EtherChannel Overview
- EtherChannel Configuration Guidelines and Restrictions
- Configuring EtherChannel
- Displaying EtherChannel to a Virtual Switch System
Configuring EtherChannel
This chapter describes how to use the command-line interface (CLI) to configure EtherChannel on the Catalyst 4500 series switch Layer 2 or Layer 3 interfaces. It also provides guidelines, procedures, and configuration examples.
This chapter includes the following major sections:
•![]() EtherChannel Configuration Guidelines and Restrictions
EtherChannel Configuration Guidelines and Restrictions
•![]() Displaying EtherChannel to a Virtual Switch System
Displaying EtherChannel to a Virtual Switch System

Note ![]() The commands in the following sections can be used on all Ethernet interfaces on a Catalyst 4500 series switch, including the uplink ports on the supervisor engine.
The commands in the following sections can be used on all Ethernet interfaces on a Catalyst 4500 series switch, including the uplink ports on the supervisor engine.

Note ![]() For complete syntax and usage information for the switch commands used in this chapter, first look at the Cisco Catalyst 4500 Series Switch Command Reference and related publications at this location:
For complete syntax and usage information for the switch commands used in this chapter, first look at the Cisco Catalyst 4500 Series Switch Command Reference and related publications at this location:
http://www.cisco.com/en/US/products//hw/switches/ps4324/index.html
If the command is not found inthe Catalyst 4500 Command Reference, it will be found in the larger Cisco IOS library. Refer to the Cisco IOS Command Reference and related publications at this location:
http://www.cisco.com/en/US/products/ps6350/index.html
EtherChannel Overview
EtherChannel bundles individual Ethernet links into a single logical link that provides bandwidth up to 1600 Mbps (Fast EtherChannel full duplex),16 Gbps (Gigabit EtherChannel), or 40 Gbps (10 Gigabit Etherchannel) between a Catalyst 4500 series switch and another switch or host.
A Catalyst 4500 series switch supports a maximum of 64 EtherChannels. You can form an EtherChannel with up to eight compatibly configured Ethernet interfaces across modules in a Catalyst 4500 series switch. All interfaces in each EtherChannel must be the same speed and must be configured as either Layer 2 or Layer 3 interfaces.

Note ![]() The network device to which a Catalyst 4500 series switch is connected may impose its own limits on the number of interfaces in an EtherChannel.
The network device to which a Catalyst 4500 series switch is connected may impose its own limits on the number of interfaces in an EtherChannel.
If a segment within an EtherChannel fails, traffic previously carried over the failed link switches to the remaining segments within the EtherChannel. When the segment fails, an SNMP trap is sent, identifying the switch, the EtherChannel, and the failed link. Inbound broadcast and multicast packets on one segment in an EtherChannel are blocked from returning on any other segment of the EtherChannel.

Note ![]() The port channel link failure switchover for the Catalyst 4500 series switch was measured at 50 ms, giving you SONET-like link failure switchover time.
The port channel link failure switchover for the Catalyst 4500 series switch was measured at 50 ms, giving you SONET-like link failure switchover time.
These subsections describe how EtherChannel works:
•![]() How EtherChannels Are Configured
How EtherChannels Are Configured
Port-Channel Interfaces
Each EtherChannel has a numbered port-channel interface. A configuration applied to the port-channel interface affects all physical interfaces assigned to that interface.

Note ![]() QoS does not propagate to members. The defaults, QoS cos = 0 and QoS dscp = 0, apply on the portchannel. Input or output policies applied on individual interfaces are ignored.
QoS does not propagate to members. The defaults, QoS cos = 0 and QoS dscp = 0, apply on the portchannel. Input or output policies applied on individual interfaces are ignored.
After you configure an EtherChannel, the configuration that you apply to the port-channel interface affects the EtherChannel; the configuration that you apply to the physical interfaces affects only the interface where you apply the configuration. To change the parameters of all ports in an EtherChannel, apply configuration commands to the port-channel interface (such commands can be STP commands or commands to configure a Layer 2 EtherChannel as a trunk).
How EtherChannels Are Configured
These subsections describe how EtherChannels are configured:
•![]() EtherChannel Configuration Overview
EtherChannel Configuration Overview
•![]() Manual EtherChannel Configuration
Manual EtherChannel Configuration
•![]() PAgP EtherChannel Configuration
PAgP EtherChannel Configuration
•![]() IEEE 802.3ad LACP EtherChannel Configuration
IEEE 802.3ad LACP EtherChannel Configuration
EtherChannel Configuration Overview
You can configure EtherChannels manually or you can use the Port Aggregation Control Protocol (PAgP) or, with Cisco IOS Release 12.2(25)EWA and later, the Link Aggregation Control Protocol (LACP) to form EtherChannels. The EtherChannel protocols allow ports with similar characteristics to form an EtherChannel through dynamic negotiation with connected network devices. PAgP is a Cisco-proprietary protocol and LACP is defined in IEEE 802.3ad.
PAgP and LACP do not interoperate. Ports configured to use PAgP cannot form EtherChannels with ports configured to use LACP and vice versa.
Table 21-1 lists the user-configurable EtherChannel modes.
Manual EtherChannel Configuration
Manually configured EtherChannel ports do not exchange EtherChannel protocol packets. A manually configured EtherChannel forms only when you configure all ports in the EtherChannel compatibly.
PAgP EtherChannel Configuration
PAgP supports the automatic creation of EtherChannels by exchanging PAgP packets between LAN ports. PAgP packets are exchanged only between ports in auto and desirable modes.
The protocol learns the capabilities of LAN port groups dynamically and informs the other LAN ports. Once PAgP identifies correctly matched Ethernet links, it facilitates grouping the links into an EtherChannel. The EtherChannel is then added to the spanning tree as a single bridge port.
Both the auto and desirable modes allow PAgP to negotiate between LAN ports to determine if they can form an EtherChannel, based on criteria such as port speed and trunking state. Layer 2 EtherChannels also use VLAN numbers.
LAN ports can form an EtherChannel when they are in different PAgP modes if the modes are compatible. For example:
•![]() A LAN port in desirable mode can form an EtherChannel successfully with another LAN port that is in desirable mode.
A LAN port in desirable mode can form an EtherChannel successfully with another LAN port that is in desirable mode.
•![]() A LAN port in desirable mode can form an EtherChannel with another LAN port in auto mode.
A LAN port in desirable mode can form an EtherChannel with another LAN port in auto mode.
•![]() A LAN port in auto mode cannot form an EtherChannel with another LAN port that is also in auto mode because neither port initiates negotiation.
A LAN port in auto mode cannot form an EtherChannel with another LAN port that is also in auto mode because neither port initiates negotiation.
IEEE 802.3ad LACP EtherChannel Configuration
Cisco IOS Release 12.2(25)EWA and later releases support IEEE 802.3ad LACP EtherChannels. LACP supports the automatic creation of EtherChannels by exchanging LACP packets between LAN ports. LACP packets are exchanged only between ports in passive and active modes.
The protocol learns the capabilities of LAN port groups dynamically and informs the other LAN ports. Once LACP identifies correctly matched Ethernet links, it facilitates grouping the links into an EtherChannel. The EtherChannel is then added to the spanning tree as a single bridge port.
Both the passive and active modes allow LACP to negotiate between LAN ports to determine if they can form an EtherChannel, based on criteria such as port speed and trunking state. Layer 2 EtherChannels also use VLAN numbers.
LAN ports can form an EtherChannel when they are in different LACP modes as long as the modes are compatible. For example:
•![]() A LAN port in active mode can form an EtherChannel successfully with another LAN port that is in active mode.
A LAN port in active mode can form an EtherChannel successfully with another LAN port that is in active mode.
•![]() A LAN port in active mode can form an EtherChannel with another LAN port in passive mode.
A LAN port in active mode can form an EtherChannel with another LAN port in passive mode.
•![]() A LAN port in passive mode cannot form an EtherChannel with another LAN port that is also in passive mode, because neither port initiates negotiation.
A LAN port in passive mode cannot form an EtherChannel with another LAN port that is also in passive mode, because neither port initiates negotiation.
LACP uses the following parameters:
•![]() LACP system priority—You may configure an LACP system priority on each switch running LACP. The system priority can be configured automatically or through the CLI. See the "Configuring the LACP System Priority and System ID" section. LACP uses the system priority with the switch MAC address to form the system ID and also during negotiation with other systems.
LACP system priority—You may configure an LACP system priority on each switch running LACP. The system priority can be configured automatically or through the CLI. See the "Configuring the LACP System Priority and System ID" section. LACP uses the system priority with the switch MAC address to form the system ID and also during negotiation with other systems.

Note ![]() The LACP system ID is the combination of the LACP system priority value and the MAC address of the switch.
The LACP system ID is the combination of the LACP system priority value and the MAC address of the switch.
•![]() LACP port priority—You must configure an LACP port priority on each port configured to use LACP. The port priority can be configured automatically or through the CLI. See the "Configuring Layer 2 EtherChannels" section. LACP uses the port priority with the port number to form the port identifier.
LACP port priority—You must configure an LACP port priority on each port configured to use LACP. The port priority can be configured automatically or through the CLI. See the "Configuring Layer 2 EtherChannels" section. LACP uses the port priority with the port number to form the port identifier.
•![]() LACP administrative key—LACP automatically configures an administrative key value equal to the channel group identification number on each port configured to use LACP. The administrative key defines the ability of a port to aggregate with other ports. A port's ability to aggregate with other ports is determined by these factors:
LACP administrative key—LACP automatically configures an administrative key value equal to the channel group identification number on each port configured to use LACP. The administrative key defines the ability of a port to aggregate with other ports. A port's ability to aggregate with other ports is determined by these factors:
–![]() Port physical characteristics, such as data rate, duplex capability, and point-to-point or shared medium
Port physical characteristics, such as data rate, duplex capability, and point-to-point or shared medium
–![]() Configuration restrictions that you establish
Configuration restrictions that you establish
LACP tries to configure the maximum number of compatible ports in an EtherChannel up to the maximum allowed by the hardware (eight ports). If a port cannot be actively included in a channel, it is not included automatically if a channelled port fails.

Note ![]() Standby and "sub-channeling" are not supported in LACP and PAgP.
Standby and "sub-channeling" are not supported in LACP and PAgP.
Load Balancing
EtherChannel can balance the traffic load across the links in the channel by reducing part of the binary pattern formed from the addresses or ports in the frame to a numerical value that selects one of the links in the channel. To balance the load, EtherChannel uses MAC addresses, IP addresses, or Layer 4 port numbers, and either the message source or message destination, or both.
Use the option that provides the greatest variety in your configuration. For example, if the traffic on a channel is going only to a single MAC address, using the destination MAC address always chooses the same link in the channel; using source addresses or IP addresses might result in better load balancing.

Note ![]() Load balancing can only be configured globally. As a result, all channels (manually configured, PagP, or LACP) use the same load balancing method.
Load balancing can only be configured globally. As a result, all channels (manually configured, PagP, or LACP) use the same load balancing method.
For additional information on load balancing, see the "Configuring EtherChannel Load Balancing" section.
EtherChannel Configuration Guidelines and Restrictions
If improperly configured, some EtherChannel interfaces are disabled automatically to avoid network loops and other problems. Follow these guidelines and restrictions to avoid configuration problems:
•![]() All Ethernet interfaces on all modules support EtherChannel (maximum of eight interfaces) with no requirement that interfaces be physically contiguous or on the same module.
All Ethernet interfaces on all modules support EtherChannel (maximum of eight interfaces) with no requirement that interfaces be physically contiguous or on the same module.
•![]() Configure all interfaces in an EtherChannel to operate at the same speed and duplex mode.
Configure all interfaces in an EtherChannel to operate at the same speed and duplex mode.
•![]() Enable all interfaces in an EtherChannel. Putting down an interface in an Ether Channel is treated as a link failure, and its traffic is transferred to one of the remaining interfaces in the EtherChannel.
Enable all interfaces in an EtherChannel. Putting down an interface in an Ether Channel is treated as a link failure, and its traffic is transferred to one of the remaining interfaces in the EtherChannel.
•![]() An EtherChannel does not form if one of the interfaces is a Switched Port Analyzer (SPAN) destination port.
An EtherChannel does not form if one of the interfaces is a Switched Port Analyzer (SPAN) destination port.
•![]() For Layer 3 EtherChannels:
For Layer 3 EtherChannels:
–![]() Assign Layer 3 addresses to the port-channel logical interface, not to the physical interfaces in the channel.
Assign Layer 3 addresses to the port-channel logical interface, not to the physical interfaces in the channel.
•![]() For Layer 2 EtherChannels:
For Layer 2 EtherChannels:
–![]() Assign all interfaces in the EtherChannel to the same VLAN, or configure them as trunks.
Assign all interfaces in the EtherChannel to the same VLAN, or configure them as trunks.
–![]() If you configure an EtherChannel from trunk interfaces, verify that the trunking mode and the native VLAN is the same on all the trunks. Interfaces in an EtherChannel with different trunk modes or different native VLANs can have unexpected results.
If you configure an EtherChannel from trunk interfaces, verify that the trunking mode and the native VLAN is the same on all the trunks. Interfaces in an EtherChannel with different trunk modes or different native VLANs can have unexpected results.
–![]() An EtherChannel supports the same allowed range of VLANs on all the interfaces in a trunking Layer 2 EtherChannel. If the allowed ranges differ for selected interface differ, they do not form an EtherChannel.
An EtherChannel supports the same allowed range of VLANs on all the interfaces in a trunking Layer 2 EtherChannel. If the allowed ranges differ for selected interface differ, they do not form an EtherChannel.
–![]() Interfaces with different Spanning Tree Protocol (STP) port path costs can form an EtherChannel as long they are otherwise compatibly configured. Setting different STP port path costs does not, by itself, make interfaces incompatible for the formation of an EtherChannel.
Interfaces with different Spanning Tree Protocol (STP) port path costs can form an EtherChannel as long they are otherwise compatibly configured. Setting different STP port path costs does not, by itself, make interfaces incompatible for the formation of an EtherChannel.
•![]() After you configure an EtherChannel, any configuration that you apply to the port-channel interface affects the EtherChannel; any configuration that you apply to the physical interfaces affects only the interface you configure.
After you configure an EtherChannel, any configuration that you apply to the port-channel interface affects the EtherChannel; any configuration that you apply to the physical interfaces affects only the interface you configure.
Storm Control is an exception to this rule. For example, you cannot configure Storm Control on some of the members of an EtherChannel; Storm Control must be configured on all or none of the ports. If you configure Storm Control on only some of the ports, those ports will be dropped from the EtherChannel interface (put in suspended state). Therefore, you should configure Storm Control at the port-channel interface level, and not at the physical interface level.
•![]() A physical interface with port security enabled can join a Layer 2 EtherChannel only if port security is also enabled on the EtherChannel; otherwise the command is rejected by the CLI.
A physical interface with port security enabled can join a Layer 2 EtherChannel only if port security is also enabled on the EtherChannel; otherwise the command is rejected by the CLI.
•![]() You cannot configure a 802.1X port in an EtherChannel.
You cannot configure a 802.1X port in an EtherChannel.
Configuring EtherChannel
These sections describe how to configure EtherChannel:
•![]() Configuring Layer 3 EtherChannels
Configuring Layer 3 EtherChannels
•![]() Configuring Layer 2 EtherChannels
Configuring Layer 2 EtherChannels
•![]() Configuring the LACP System Priority and System ID
Configuring the LACP System Priority and System ID
•![]() Configuring EtherChannel Load Balancing
Configuring EtherChannel Load Balancing
•![]() Removing an Interface from an EtherChannel
Removing an Interface from an EtherChannel

Note ![]() Ensure that the interfaces are configured correctly. (See the "EtherChannel Configuration Guidelines and Restrictions" section.)
Ensure that the interfaces are configured correctly. (See the "EtherChannel Configuration Guidelines and Restrictions" section.)
Configuring Layer 3 EtherChannels
To configure Layer 3 EtherChannels, create the port-channel logical interface and then put the Ethernet interfaces into the portchannel.
These sections describe Layer 3 EtherChannel configuration:
•![]() Creating Port-Channel Logical Interfaces
Creating Port-Channel Logical Interfaces
•![]() Configuring Physical Interfaces as Layer 3 EtherChannels
Configuring Physical Interfaces as Layer 3 EtherChannels
Creating Port-Channel Logical Interfaces

Note ![]() To move an IP address from a physical interface to an EtherChannel, you must delete the IP address from the physical interface before configuring it on the port-channel interface.
To move an IP address from a physical interface to an EtherChannel, you must delete the IP address from the physical interface before configuring it on the port-channel interface.
To create a port-channel interface for a Layer 3 EtherChannel, perform this task:
This example shows how to create port-channel interface 1:
Switch# configure terminal
Switch(config)# interface port-channel 1
Switch(config-if)# ip address 172.32.52.10 255.255.255.0
Switch(config-if)# end
This example shows how to verify the configuration of port-channel interface 1:
Switch# show running-config interface port-channel 1
Building configuration...
Current configuration:
!
interface Port-channel1
ip address 172.32.52.10 255.255.255.0
no ip directed-broadcast
end
Switch#
Configuring Physical Interfaces as Layer 3 EtherChannels
To configure physical interfaces as Layer 3 EtherChannels, perform this task for each interface:
This example shows how to configure Fast Ethernet interfaces 5/4 and 5/5 into port-channel 1 with PAgP mode desirable:
Switch# configure terminal
Switch(config)# interface range fastethernet 5/4 - 5 (Note: Space is mandatory.)
Switch(config-if)# no switchport
Switch(config-if)# no ip address
Switch(config-if)# channel-group 1 mode desirable
Switch(config-if)# end

Note ![]() See the "Configuring a Range of Interfaces" section for information about the range keyword.
See the "Configuring a Range of Interfaces" section for information about the range keyword.
The following two examples show how to verify the configuration of Fast Ethernet interface 5/4:
Switch# show running-config interface fastethernet 5/4
Building configuration...
Current configuration:
!
interface FastEthernet5/4
no ip address
no switchport
no ip directed-broadcast
channel-group 1 mode desirable
end
Switch# show interfaces fastethernet 5/4 etherchannel
Port state = EC-Enbld Up In-Bndl Usr-Config
Channel group = 1 Mode = Desirable Gcchange = 0
Port-channel = Po1 GC = 0x00010001 Pseudo-port-channel = Po1
Port indx = 0 Load = 0x55
Flags: S - Device is sending Slow hello. C - Device is in Consistent state.
A - Device is in Auto mode. P - Device learns on physical port.
Timers: H - Hello timer is running. Q - Quit timer is running.
S - Switching timer is running. I - Interface timer is running.
Local information:
Hello Partner PAgP Learning Group
Port Flags State Timers Interval Count Priority Method Ifindex
Fa5/4 SC U6/S7 30s 1 128 Any 55
Partner's information:
Partner Partner Partner Partner Group
Port Name Device ID Port Age Flags Cap.
Fa5/4 JAB031301 0050.0f10.230c 2/45 1s SAC 2D
Age of the port in the current state: 00h:54m:52s
Switch#
This example shows how to verify the configuration of port-channel interface 1 after the interfaces have been configured:
Switch# show etherchannel 1 port-channel
Channel-group listing:
----------------------
Group: 1
------------
Port-channels in the group:
----------------------
Port-channel: Po1
------------
Age of the Port-channel = 01h:56m:20s
Logical slot/port = 10/1 Number of ports = 2
GC = 0x00010001 HotStandBy port = null
Port state = Port-channel L3-Ag Ag-Inuse
Ports in the Port-channel:
Index Load Port
-------------------
1 00 Fa5/6
0 00 Fa5/7
Time since last port bundled: 00h:23m:33s Fa5/6
Switch#
Configuring Layer 2 EtherChannels
To configure Layer 2 EtherChannels, configure the Ethernet interfaces with the channel-group command. This creates the port-channel logical interface.

Note ![]() Cisco IOS software creates port-channel interfaces for Layer 2 EtherChannels when you configure Layer 2 Ethernet interfaces with the channel-group command.
Cisco IOS software creates port-channel interfaces for Layer 2 EtherChannels when you configure Layer 2 Ethernet interfaces with the channel-group command.
To configure Layer 2 Ethernet interfaces as Layer 2 EtherChannels, perform this task for each interface:
This example shows how to configure Fast Ethernet interfaces 5/6 and 5/7 into port-channel 2 with PAgP mode desirable:
Switch# configure terminal
Switch(config)# interface range fastethernet 5/6 - 7 (Note: Space is mandatory.)
Switch(config-if-range)# channel-group 2 mode desirable
Switch(config-if-range)# end
Switch# end

Note ![]() See the "Using the Ethernet Management Port" section for information about the range keyword.
See the "Using the Ethernet Management Port" section for information about the range keyword.
This example shows how to verify the configuration of port-channel interface 2:
Switch# show running-config interface port-channel 2
Building configuration...
Current configuration:
!
interface Port-channel2
switchport access vlan 10
switchport mode access
end
Switch#
The following two examples show how to verify the configuration of Fast Ethernet interface 5/6:
Switch# show running-config interface fastethernet 5/6
Building configuration...
Current configuration:
!
interface FastEthernet5/6
switchport access vlan 10
switchport mode access
channel-group 2 mode desirable
end
Switch# show interfaces fastethernet 5/6 etherchannel
Port state = EC-Enbld Up In-Bndl Usr-Config
Channel group = 1 Mode = Desirable Gcchange = 0
Port-channel = Po1 GC = 0x00010001
Port indx = 0 Load = 0x55
Flags: S - Device is sending Slow hello. C - Device is in Consistent state.
A - Device is in Auto mode. P - Device learns on physical port.
d - PAgP is down.
Timers: H - Hello timer is running. Q - Quit timer is running.
S - Switching timer is running. I - Interface timer is running.
Local information:
Hello Partner PAgP Learning Group
Port Flags State Timers Interval Count Priority Method Ifindex
Fa5/6 SC U6/S7 30s 1 128 Any 56
Partner's information:
Partner Partner Partner Partner Group
Port Name Device ID Port Age Flags Cap.
Fa5/6 JAB031301 0050.0f10.230c 2/47 18s SAC 2F
Age of the port in the current state: 00h:10m:57s
This example shows how to verify the configuration of port-channel interface 2 after the interfaces have been configured:
Switch# show etherchannel 2 port-channel
Port-channels in the group:
----------------------
Port-channel: Po2
------------
Age of the Port-channel = 00h:23m:33s
Logical slot/port = 10/2 Number of ports in agport = 2
GC = 0x00020001 HotStandBy port = null
Port state = Port-channel Ag-Inuse
Ports in the Port-channel:
Index Load Port
-------------------
1 00 Fa5/6
0 00 Fa5/7
Time since last port bundled: 00h:23m:33s Fa5/6
Switch#
Configuring the LACP System Priority and System ID
The LACP system ID is the LACP system priority value combined with the MAC address of the switch.
To configure the LACP system priority and system ID, perform this task:
This example shows how to configure the LACP system priority:
Switch# configure terminal
Switch(config)# lacp system-priority 23456
Switch(config)# end
Switch# show module
Mod Ports Card Type Model Serial No.
----+-----+--------------------------------------+-----------------+-----------
1 2 1000BaseX (GBIC) Supervisor(active) WS-X4014 JAB063808YZ
2 48 10/100BaseTX (RJ45) WS-X4148-RJ JAB0447072W
3 48 10/100BaseTX (RJ45)V WS-X4148-RJ45V JAE061704J6
4 48 10/100BaseTX (RJ45)V WS-X4148-RJ45V JAE061704ML
M MAC addresses Hw Fw Sw Status
--+--------------------------------+---+------------+----------------+---------
1 0005.9a39.7a80 to 0005.9a39.7a81 2.1 12.1(12r)EW 12.1(13)EW(0.26) Ok
2 0002.fd80.f530 to 0002.fd80.f55f 0.1 Ok
3 0009.7c45.67c0 to 0009.7c45.67ef 1.6 Ok
4 0009.7c45.4a80 to 0009.7c45.4aaf 1.6 Ok
This example shows how to verify the configuration:
Switch# show lacp sys-id
23456,0050.3e8d.6400
Switch#
The system priority is displayed first, followed by the MAC address of the switch.
Configuring EtherChannel Load Balancing

Note ![]() Load balancing can only be configured globally. As a result, all channels (manually configured, PagP, or LACP) use the same load balancing method.
Load balancing can only be configured globally. As a result, all channels (manually configured, PagP, or LACP) use the same load balancing method.
To configure EtherChannel load balancing, perform this task:
The load-balancing keywords are:
•![]() src-mac—Source MAC addresses
src-mac—Source MAC addresses
•![]() dst-mac—Destination MAC addresses
dst-mac—Destination MAC addresses
•![]() src-dst-mac—Source and destination MAC addresses
src-dst-mac—Source and destination MAC addresses
•![]() src-ip—Source IP addresses
src-ip—Source IP addresses
•![]() dst-ip—Destination IP addresses
dst-ip—Destination IP addresses
•![]() src-dst-ip—Source and destination IP addresses (Default)
src-dst-ip—Source and destination IP addresses (Default)
•![]() src-port—Source Layer 4 port
src-port—Source Layer 4 port
•![]() dst-port—Destination Layer 4 port
dst-port—Destination Layer 4 port
•![]() src-dst-port—Source and destination Layer 4 port
src-dst-port—Source and destination Layer 4 port
This example shows how to configure EtherChannel to use source and destination IP addresses:
Switch# configure terminal
Switch(config)# port-channel load-balance src-dst-ip
Switch(config)# end
Switch#
This example shows how to verify the configuration:
Switch# show etherchannel load-balance
EtherChannel Load-Balancing Configuration:
src-dst-ip
EtherChannel Load-Balancing Addresses Used Per-Protocol:
Non-IP: Source XOR Destination MAC address
IPv4: Source XOR Destination IP address
IPv6: Source XOR Destination IP address
Switch#
Removing an Interface from an EtherChannel
To remove an Ethernet interface from an EtherChannel, perform this task:
This example shows how to remove Fast Ethernet interfaces 5/4 and 5/5 from port-channel 1:
Switch# configure terminal
Switch(config)# interface range fastethernet 5/4 - 5 (Note: Space is mandatory.)
Switch(config-if)# no channel-group 1
Switch(config-if)# end
Removing an EtherChannel
If you remove an EtherChannel, the member ports are shut down and removed from the channel group.

Note ![]() If you want to change an EtherChannel from Layer 2 to Layer 3, or Layer 3 to Layer 2, you must remove the EtherChannel and recreate it in the desired configuration.
If you want to change an EtherChannel from Layer 2 to Layer 3, or Layer 3 to Layer 2, you must remove the EtherChannel and recreate it in the desired configuration.
To remove an EtherChannel, perform this task:
This example shows how to remove port-channel 1:
Switch# configure terminal
Switch(config)# no interface port-channel 1
Switch(config)# end
Displaying EtherChannel to a Virtual Switch System
Catalyst 4500 series switches support enhanced PAgP. If a Catalyst 4500 series switch is connected to a Catalyst 6500 series Virtual Switch System (VSS) via a PAgP EtherChannel, the Catalyst 4500 series switch will automatically serve as a VSS client, using enhanced PAgP on this EtherChannel for dual-active detection. This VSS client feature has no impact on the performance of Catalyst 4500 series switches and does not require any user configuration.
Topics include:
•![]() Displaying EtherChannel Links to VSS
Displaying EtherChannel Links to VSS
Understanding VSS Client
Topics covered include:
•![]() Dual-Active Detection Using Enhance PAgP
Dual-Active Detection Using Enhance PAgP
Virtual Switch System
The Cisco Catalyst 6500 Series VSS 1440 allows for the combination of two Cisco Catalyst 6500 Series switches into a single, logical network entity from the network control-plane and management perspectives. Within the Cisco VSS, one chassis is designated as the active virtual switch, acting as the single management point of the entire system, and the other is designated as the standby virtual switch. There two chassis are bound together by a special link, called Virtual Switch Link (VSL), which carries the internal signaling and control information between them.
Dual-Active Scenarios
One of the failure scenarios in a VSS is called dual-active, which occurs when the VSL fails completely. In this case, neither virtual switch knows of the other's status. From the perspective of the active virtual switch, the standby chassis is lost. The standby virtual switch also views the active chassis as failed and transitions to active state via an SSO switchover. So, two active virtual switches will exist in the network with identical configurations, causing duplicate IP addresses and bridge identifiers. This scenario has adverse effects on the network topology and traffic if it persists.
Dual-Active Detection Using Enhance PAgP
One mechanism for detecting a dual-active scenario is based on enhanced PAgP (PAgP+). Specifically, the VSS sends regularly scheduled PAgP messages with Type-Length-Values (TLVs) containing the ID of the current active virtual switch ( Figure 21-1). When the VSL fails completely, the standby virtual switch immediately sends asynchronous PAgP messages with TLVs containing its own ID on all port channels enabled for enhanced PAgP dual-active detection (Figure 21-2). The remote switch
(the VSS client) connected to both VSS components via EtherChannel links, compares every received active ID with its stored active ID. If they match, the remote switch simply sends TLVs containing its stored active ID back to the VSS in its regularly scheduled PAgP messages. If they do not match, the remote switch stores the new active ID and immediately transmits asynchronous PAgP messages with TLVs containing the new active ID. Upon receiving the new active ID from the remote switch, the original active virtual switch detects the dual-active scenario and takes appropriate actions.
Figure 21-1 Enhanced PAgP in VSS Normal Opertaion

Figure 21-2 Enhanced PAgP in VSS Dual-active Scenario
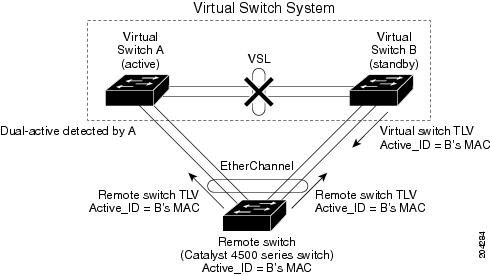
As a remote switch, the Catalyst 4500 series switch supports stateful VSS client. In particular, the ID of the current active virtual switch is synchronized from the active supervisor engine to the redundant supervisor engine of the Catalyst 4500 series switch. This ensures that dual-active detection is not disrupted even when the active supervisor engine switches over to the redundant supervisor engine.
Displaying EtherChannel Links to VSS
To display the dual-active detection capability of the configured PAgP portchannel, use the
show pagp port_channel_number dual-active command.
It indicates whether:
•![]() A switch uses enhanced PAgP for dual-active detection.
A switch uses enhanced PAgP for dual-active detection.
You should always see "Yes" after "PAgP dual-active diction enabled" on a Catalyst 4500 switch.
•![]() The configured PAgP EtherChannel is connected to a Catalyst 6500 switch VSS.
The configured PAgP EtherChannel is connected to a Catalyst 6500 switch VSS.
You will see "N/A" below "Partner Version" if this EtherChannel is not connected to a VSS. Otherwise, user will see the version of enhanced PAgP dual-active detection implemented in the VSS.
•![]() This switch is capable of detecting dual-active scenarios in the connected VSS.
This switch is capable of detecting dual-active scenarios in the connected VSS.
You will see "Yes" below "Dual-Active Detect Capable" if and only if the configured EtherChannel is connected to a Catalyst 6500 series VSS that uses the same version of enhanced PAgP dual-active detection.

Note ![]() You can also see the name of the neighboring switch (Partner Name) and the ports to which this EtherChannel is connected (Partner Port).
You can also see the name of the neighboring switch (Partner Name) and the ports to which this EtherChannel is connected (Partner Port).
If a Catalyst 4500 switch is connected to a Catalyst 6500 series VSS with the same version of enhanced PAgP dual-active detection, the switch can detect a dual-active scenario:
Switch# show pagp 1 dual-active
PAgP dual-active detection enabled: Yes
PAgP dual-active version: 1.1
Channel group 1
Dual-Active Partner Partner Partner
Port Detect Capable Name Port Version
Gi6/5 Yes VSS Gi1/8/1 1.1
Gi6/6 Yes VSS Gi2/8/1 1.1
If a Catalyst 4500 switch is not connected to a Catalyst 6500 series VSS, the switch cannot detect a dual-active scenario:
Switch# show pagp 1 dual-active
PAgP dual-active detection enabled: Yes
PAgP dual-active version: 1.1
Channel group 1
Dual-Active Partner Partner Partner
Port Detect Capable Name Port Version
Gi6/5 No Switch Fa6/5 N/A
Gi6/6 No Switch Fa6/6 N/A
 Feedback
Feedback