- Preface
- Product Overview
- Command-Line Interfaces
- Configuring the Switch for the First Time
- Administering the Switch
- Configuring Virtual Switching Systems
- Programmability
- Configuring the Cisco IOS In-Service Software Upgrade Process
- Configuring the Cisco IOS XE In Service Software Upgrade Process
- Configuring Interfaces
- Checking Port Status and Connectivity
- Configuring Supervisor Engine Redundancy Using RPR and SSO on Supervisor Engine 6-E and Supervisor Engine 6L-E
- Configuring Supervisor Engine Redundancy Using RPR and SSO on Supervisor Engine 7-E, Supervisor Engine 7L-E, and Supervisor Engine 8-E
- Configuring Cisco NSF with SSO Supervisor Engine Redundancy
- Environmental Monitoring and Power Management
- Configuring Power over Ethernet
- Configuring Cisco Network Assistant
- Configuring VLANs, VTP, and VMPS
- Configuring IP Unnumbered Interface
- Configuring Layer 2 Ethernet Interfaces
- Configuring EVC-Lite
- Configuring SmartPort Macros
- Configuring Cisco IOS Auto Smartport Macros
- Configuring STP and MST
- Configuring Flex Links and MAC Address-Table Move Update
- Configuring Resilient Ethernet Protocol
- Configuring Optional STP Features
- Configuring EtherChannel and Link State Tracking
- Configuring IGMP Snooping and Filtering, and MVR
- Configuring IPv6 Multicast Listener Discovery Snooping
- Configuring 802.1Q Tunneling, VLAN Mapping, and Layer 2 Protocol Tunneling
- Configuring Cisco Discovery Protocol
- Configuring LLDP, LLDP-MED, and Location Service
- Configuring UDLD
- Configuring Unidirectional Ethernet
- Configuring Layer 3 Interfaces
- Configuring Cisco Express Forwarding
- Configuring Unicast Reverse Path Forwarding
- Configuring IP Multicast
- Configuring ANCP Client
- Configuring Bidirectional Forwarding Detection
- Configuring Campus Fabric
- Configuring Policy-Based Routing
- Configuring VRF-lite
- Configuring Quality of Service
- Configuring AVC with DNS-AS
- Configuring Voice Interfaces
- Configuring Private VLANs
- Configuring MACsec Encryption
- Configuring 802.1X Port-Based Authentication
- X.509v3 Certificates for SSH Authentication
- Configuring the PPPoE Intermediate Agent
- Configuring Web-Based Authentication
- Configuring Wired Guest Access
- Configuring Auto Identity
- Configuring Port Security
- Configuring Auto Security
- Configuring Control Plane Policing and Layer 2 Control Packet QoS
- Configuring Dynamic ARP Inspection
- Configuring the Cisco IOS DHCP Server
- Configuring DHCP Snooping, IP Source Guard, and IPSG for Static Hosts
- DHCPv6 Options Support
- Configuring Network Security with ACLs
- Support for IPv6
- Port Unicast and Multicast Flood Blocking
- Configuring Storm Control
- Configuring SPAN and RSPAN
- Configuring ERSPAN
- Configuring Wireshark
- Configuring Enhanced Object Tracking
- Configuring System Message Logging
- Onboard Failure Logging (OBFL)
- Configuring SNMP
- Configuring NetFlow-lite
- Configuring Flexible NetFlow
- Configuring Ethernet OAM and CFM
- Configuring Y.1731 (AIS and RDI)
- Configuring Call Home
- Configuring Cisco IOS IP SLA Operations
- Configuring RMON
- Performing Diagnostics
- Configuring WCCP Version 2 Services
- Configuring MIB Support
- Configuring Easy Virtual Networks
- ROM Monitor
- Acronyms and Abbreviations
- Index
Configuring ERSPAN
This module describes how to configure Encapsulated Remote Switched Port Analyzer (ERSPAN). The Cisco ERSPAN feature allows you to monitor traffic on ports or VLANs and send the monitored traffic to destination ports.

Note![]() The ERSPAN feature is not supported on Layer 2 switching interfaces.
The ERSPAN feature is not supported on Layer 2 switching interfaces.
This module describes the feature and consists of these sections:
- Information About ERSPAN
- How to Configure ERSPAN
- Configuration Examples for ERSPAN
- Verifying ERSPAN
- Additional References for Configuring ERSPAN
- Feature Information for ERSPAN

Note![]() For complete syntax and usage information for the switch commands used in this chapter, see the
For complete syntax and usage information for the switch commands used in this chapter, see the
Cisco IOS Command Reference Guides for the Catalyst 4500 Series Switch.
If a command is not in the Cisco Catalyst 4500 Series Switch Command Reference , you can locate it in the Cisco IOS Master Command List, All Releases.
Prerequisites for ERSPAN
- Only IPv4 delivery/transport header is supported.
- Access control list (ACL) filter is applied before sending the monitored traffic on to the tunnel.
- Only supports Type-II ERSPAN header.
- The extended VLAN ID that is reserved for each ERSPAN session cannot be used for any other purpose, until the ERSPAN source session is present in the configuration. Use the show vlan internal usage command to display the extended VLAN ID.
- This feature is supported on Cisco Catalyst 4500-E Supervisor Engines 7-E, 7L-E, 8-E, 8L-E, and 4500-X Series Switches.
Restrictions for ERSPAN
The following restrictions apply for this feature:
- The maximum number of available ports for each ERSPAN session is 128.
- A maximum of 8 ingress and 8 egress ERSPAN sessions (a total of 16 sessions) are supported.
- You can configure either a list of ports or a list of VLANs as a source, but cannot configure both for a given session.
- When a session is configured through the ERSPAN CLI, the session ID and the session type cannot be changed. To change them, you must use the no form of the configuration commands to remove the session and then reconfigure the session.
- ERSPAN source sessions do not copy locally-sourced Remote SPAN (RSPAN) VLAN traffic from source trunk ports that carry RSPAN VLANs.
- ERSPAN source sessions do not copy locally-sourced ERSPAN GRE-encapsulated traffic from source ports.
The Catalyst 4500 series switches do not support the following for this feature:
- ERSPAN destination type.
- Timestamp indication in the ERSPAN header.
- Bad/Short/Oversized (BSO) packet indication in the ERSPAN header.
- The original VLAN ID or Class of Service (COS) in the ERSPAN header.
- Generic routing encapsulation (GRE) header flags.
- GRE header sequence number or key.
- Maximum transmission unit (MTU) checking and fragmentation. Hence, traffic exceeding the configured MTU size (as determined by Layer 3 protocols) is dropped.
- Truncation of the original packet; because of which the T-bit in the ERSPAN header is always zero.
- Setting of the Differentiated Services Code Point (DSCP)/Time to Live (TTL) field for IP encapsulation differently for various ERSPAN source sessions. Use the erspan { ttl | tos } command to set these values. The configured values are used in all ERSPAN source sessions originating from the device.
- Simple Network Management Protocol (SNMP).
Information About ERSPAN
ERSPAN Overview
The Cisco ERSPAN feature allows you to monitor traffic on ports or VLANs, and send the monitored traffic to destination ports. ERSPAN sends traffic to a network analyzer, such as a Switch Probe device or a Remote Monitoring (RMON) probe. ERSPAN supports source ports, source VLANs, and destination ports on different devices, which helps remote monitoring of multiple devices across a network.
ERSPAN supports encapsulated packets of up to 9180 bytes. ERSPAN consists of an ERSPAN source session, routable ERSPAN GRE-encapsulated traffic, and an ERSPAN destination session.
ERSPAN consists of an ERSPAN source session, routable ERSPAN GRE-encapsulated traffic, and an ERSPAN destination session. You can configure an ERSPAN source session, an ERSPAN destination session, or both on a device. A device on which only an ERSPAN source session is configured is called an ERSPAN source device, and a device on which only an ERSPAN destination session is configured is called an ERSPAN termination device. A device can act as both; an ERSPAN source device and a termination device.

Note![]() Catalyst 4500 series switches do not support ERSAPN destination type/session.
Catalyst 4500 series switches do not support ERSAPN destination type/session.
For a source port or a source VLAN, the ERSPAN can monitor the ingress, egress, or both ingress and egress traffic. By default, ERSPAN monitors all traffic, including multicast, and Bridge Protocol Data Unit (BPDU) frames.
An ERSPAN source session is defined by the following parameters:
- A session ID
- List of source ports or source VLANs to be monitored by the session
- The destination and origin IP addresses, which are used as the destination and source IP addresses of the GRE envelope for the captured traffic, respectively
- ERSPAN flow ID
- Optional attributes, such as, IP type of service (TOS) and IP Time to Live (TTL), related to the GRE envelope

Note![]() ERSPAN source sessions do not copy ERSPAN GRE-encapsulated traffic from source ports. Each ERSPAN source session can have either ports or VLANs as sources, but not both.
ERSPAN source sessions do not copy ERSPAN GRE-encapsulated traffic from source ports. Each ERSPAN source session can have either ports or VLANs as sources, but not both.
An ERSPAN destination session is defined by the following parameters:
- Session ID
- Destination ports
- Source IP address, which is the same as the destination IP address of the corresponding source session
- ERSPAN flow ID, which is used to match the destination session with the source session
- The ERSPAN source sessions copy traffic from the source ports or source VLANs and forwards the traffic using routable GRE-encapsulated packets to the ERSPAN destination session. The ERSPAN destination session switches the traffic to the destination ports

Note![]() Because encapsulation is performed in the hardware, the CPU performance is not impacted.
Because encapsulation is performed in the hardware, the CPU performance is not impacted.
Figure 67-1 ERSPAN Configuration
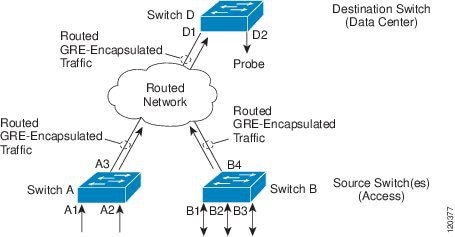
ERSAN Sources
The Cisco ERSPAN feature supports the following sources:
- Source ports—A source port that is monitored for traffic analysis. Source ports in any VLAN can be configured and trunk ports can be configured as source ports along with nontrunk source ports.
- Source VLANs—A VLAN that is monitored for traffic analysis.
The following tunnel interfaces are supported as source ports for a source session:
How to Configure ERSPAN
Configuring an ERSPAN Source Session
The ERSPAN source session defines the session configuration parameters and the ports or VLANs to be monitored.
Configuration Examples for ERSPAN
Example: Configuring an ERSAPN Source Session
Verifying ERSPAN
To verify the ERSPAN configuration, use the following commands:
The following is sample output from the show monitor session erspan-source command:
Switch# show monitor session erspan-source session
The following is sample output from the show monitor session erspan-source detail command:
Switch# show monitor session erspan-source detail
Type : ERSPAN Source Session
Status : Admin Enabled
Description : -
Source Ports :
RX Only : Gi1/4/33
TX Only : None
Both : None
Source VLANs :
RX Only : None
TX Only : None
Both : None
Source RSPAN VLAN : None
Destination Ports : None
Filter VLANs : None
Filter Addr Type :
RX Only : None
TX Only : None
Both : None
Filter Pkt Type :
RX Only : None
Dest RSPAN VLAN : None
IP Access-group : None
IPv6 Access-group : None
Destination IP Address : 20.20.163.20
Destination IPv6 Address : None
Destination IP VRF : None
Destination ERSPAN ID : 110
The following output from the show capability feature monitor erspan-source command displays information about the configured ERSPAN source sessions:
The following output from the show capability feature monitor erspan-destination command displays all the configured global built-in templates:
Additional References for Configuring ERSPAN
Related Documents
|
|
|
|---|---|
Cisco IOS Command Reference Guides for the Catalyst 4500 Series Switch |
Standards & MIBs
|
|
|
|---|---|
|
|
To locate and download MIBs for selected platforms, Cisco software releases, and feature sets, use Cisco MIB Locator found at the following URL: |
RFCs
|
|
|
|---|---|
Technical Assistance
Feature Information for ERSPAN
Use Cisco Feature Navigator to find information about platform support and software image support. Cisco Feature Navigator enables you to determine which software images support a specific software release, feature set, or platform. To access Cisco Feature Navigator, go to http://www.cisco.com/go/cfn. An account on Cisco.com is not required.

Note![]() Table 1 lists only the software release that introduced support for a given feature in a given software release train. Unless noted otherwise, subsequent releases of that software release train also support that feature.
Table 1 lists only the software release that introduced support for a given feature in a given software release train. Unless noted otherwise, subsequent releases of that software release train also support that feature.
 Feedback
Feedback