What is LISP VXLAN Fabric
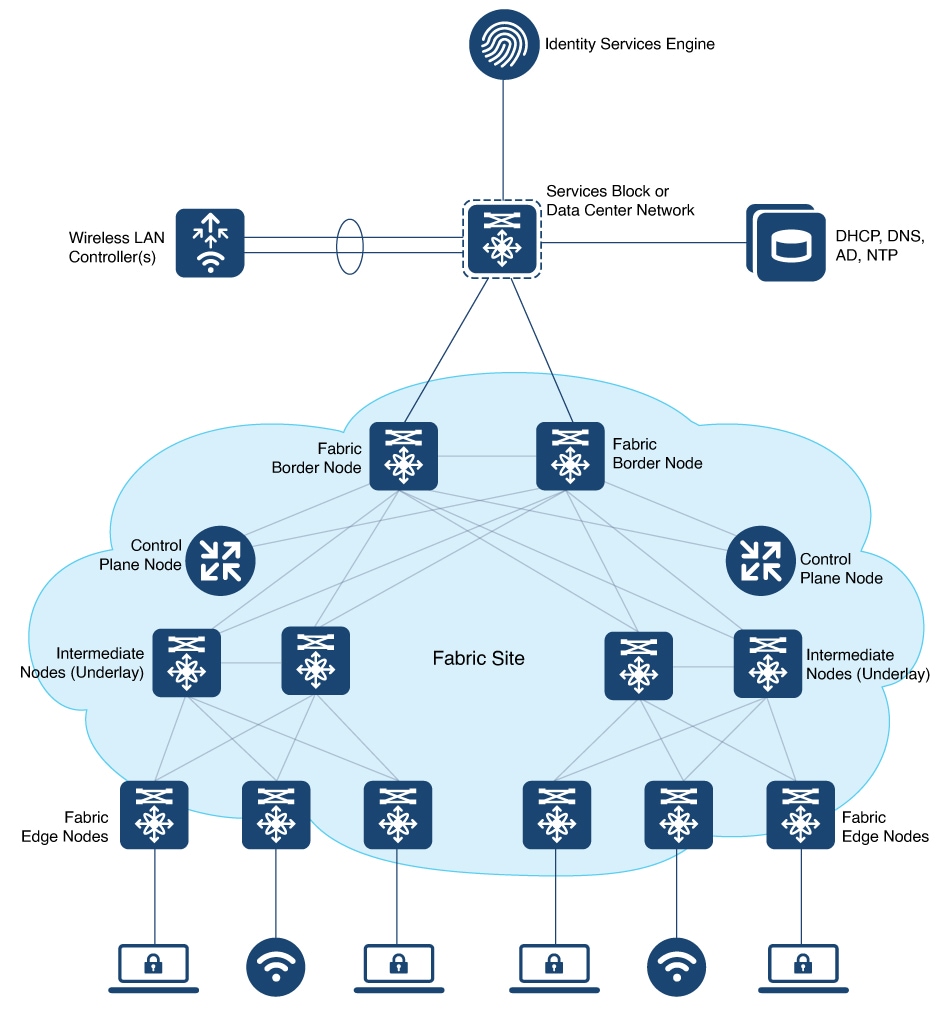
A network fabric is made of network devices such as wireless access points, switches, and routers that are interconnected, to transport data to its destination. These physical devices form the underlay network that forwards the traffic. A virtual network is built over the underlay network using tunneling technologies such as VXLAN, and is called an overlay. Endpoints or users are logically connected to the overlay network, which transports the user data.
While there are several routing protocols that enable the transport of data in a fabric, this particular fabric uses a combination of Locator/ID Separation Protocol (LISP) and VXLAN.
The Locator/ID Separation Protocol (LISP) is an overlay routing technology that provides improved routing scalability and dynamic host mobility. LISP works with two separate IP address spaces: one to indicate routing locators (RLOCs) for routing traffic to the external network and a second address called endpoint identifier (EID), which is used to identify the endpoints.
VXLAN, a Layer 2 tunneling mechanism, forms the data plane in the overlay network and uses a MAC-in-IP encapsulation method to carry the data packets through the tunnel.
A LISP VXLAN fabric solution uses virtual networks (overlay networks) that run on a physical network (underlay network). The overlay network creates a logical topology to virtually connect the physical devices that are part of the underlay network. In the underlay network, IP connectivity is established among the physical devices through a routing protocol.
Three fundamental components work together to provision a LISP VXLAN fabric. These enable flexible attachment of devices, data transmission and enhanced security through segmentation and group-based policies:
-
Control Plane: Uses LISP for mapping endpoint identity (IP addresses or MAC addresses) to their location within the fabric.
-
Data Plane: Uses Virtual Extensible LAN (VXLAN) encapsulation method to transmit data packets.
-
Policy Plane: (Optional) Uses Cisco Security Group Tags (SGTs) and Group-Based Policy for microsegmentation.

 Feedback
Feedback