You can enable Layer 2 protocol tunneling (by protocol) on the ports that are connected to the customer in the edge devices
of the service-provider network. The service-provider edge devices connected to the customer device perform the tunneling
process. Edge device tunnel ports are connected to customer IEEE 802.1Q trunk ports. Edge device access ports are connected
to customer access ports. The edge devices connected to the customer device perform the tunneling process.
You can enable Layer 2 protocol tunneling on ports that are configured as access ports or tunnel ports or trunk ports. You
cannot enable Layer 2 protocol tunneling on ports that are configured in either switchport mode dynamic auto mode (the default mode) or switchport mode dynamic desirable mode.
The device supports Layer 2 protocol tunneling for CDP, STP, and VTP. For emulated point-to-point network topologies, it also
supports PAgP, LACP, LLDP, and UDLD protocols.

Note
|
PAgP, LACP, and UDLD protocol tunneling are only intended to emulate a point-to-point topology. An erroneous configuration
that sends tunneled packets to many ports could lead to a network failure.
|
When the Layer 2 PDUs that entered the service-provider inbound edge device through a Layer 2 protocol-enabled port exit through
the trunk port into the service-provider network, the device overwrites the customer PDU-destination MAC address with a well-known
Cisco proprietary multicast address (01-00-0c-cd-cd-d0). If IEEE 802.1Q tunneling is enabled, packets are also double-tagged;
the outer tag is the customer metro tag, and the inner tag is the customer’s VLAN tag. The core devices ignore the inner tags
and forward the packet to all trunk ports in the same metro VLAN. The edge devices on the outbound side restore the proper
Layer 2 protocol and MAC address information and forward the packets to all tunnel or access ports in the same metro VLAN.
Therefore, the Layer 2 PDUs remain intact and are delivered across the service-provider infrastructure to the other side of
the customer network.
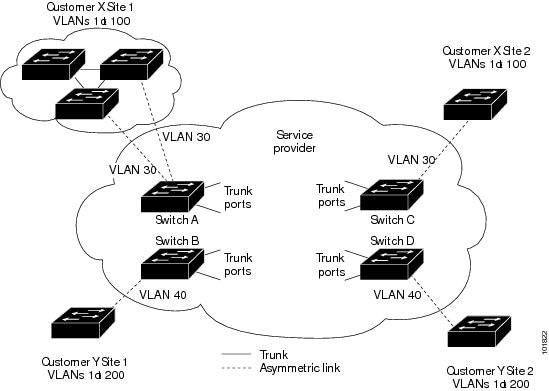
See the Layer 2 Protocol Tunneling figure in Layer 2 Protocol Tunneling Overview, with Customer X and Customer Y in access VLANs 30 and 40, respectively. Asymmetric links connect the customers in Site 1
to edge switches in the service-provider network. The Layer 2 PDUs (for example, BPDUs) coming into Switch B from Customer
Y in Site 1 are forwarded to the infrastructure as double-tagged packets with the well-known MAC address as the destination
MAC address. These double-tagged packets have the metro VLAN tag of 40, as well as an inner VLAN tag (for example, VLAN 100).
When the double-tagged packets enter Switch D, the outer VLAN tag 40 is removed, the well-known MAC address is replaced with
the respective Layer 2 protocol MAC address, and the packet is sent to Customer Y on Site 2 as a single-tagged frame in VLAN
100.
You can also enable Layer 2 protocol tunneling on access ports on the edge switch that is connected to access or trunk ports
on the customer switch. In this case, the encapsulation and decapsulation process are the same as described in the previous
paragraph, except that the packets are not double-tagged in the service-provider network. The single tag is the customer-specific
access VLAN tag.
In switch stacks, Layer 2 protocol tunneling configuration is distributed among all member switches. Each member switch that
receives an ingress packet on a local port encapsulates or decapsulates the packet and forwards it to the appropriate destination
port. On a single switch, ingress Layer 2 protocol-tunneled traffic is sent across all local ports in the same VLAN on which
Layer 2 protocol tunneling is enabled. In a stack, packets received by a Layer 2 protocol-tunneled port are distributed to
all ports in the stack that are configured for Layer 2 protocol tunneling and are in the same VLAN. All Layer 2 protocol tunneling
configuration is handled by the active switch and distributed to all member switches in the stack.

 Feedback
Feedback