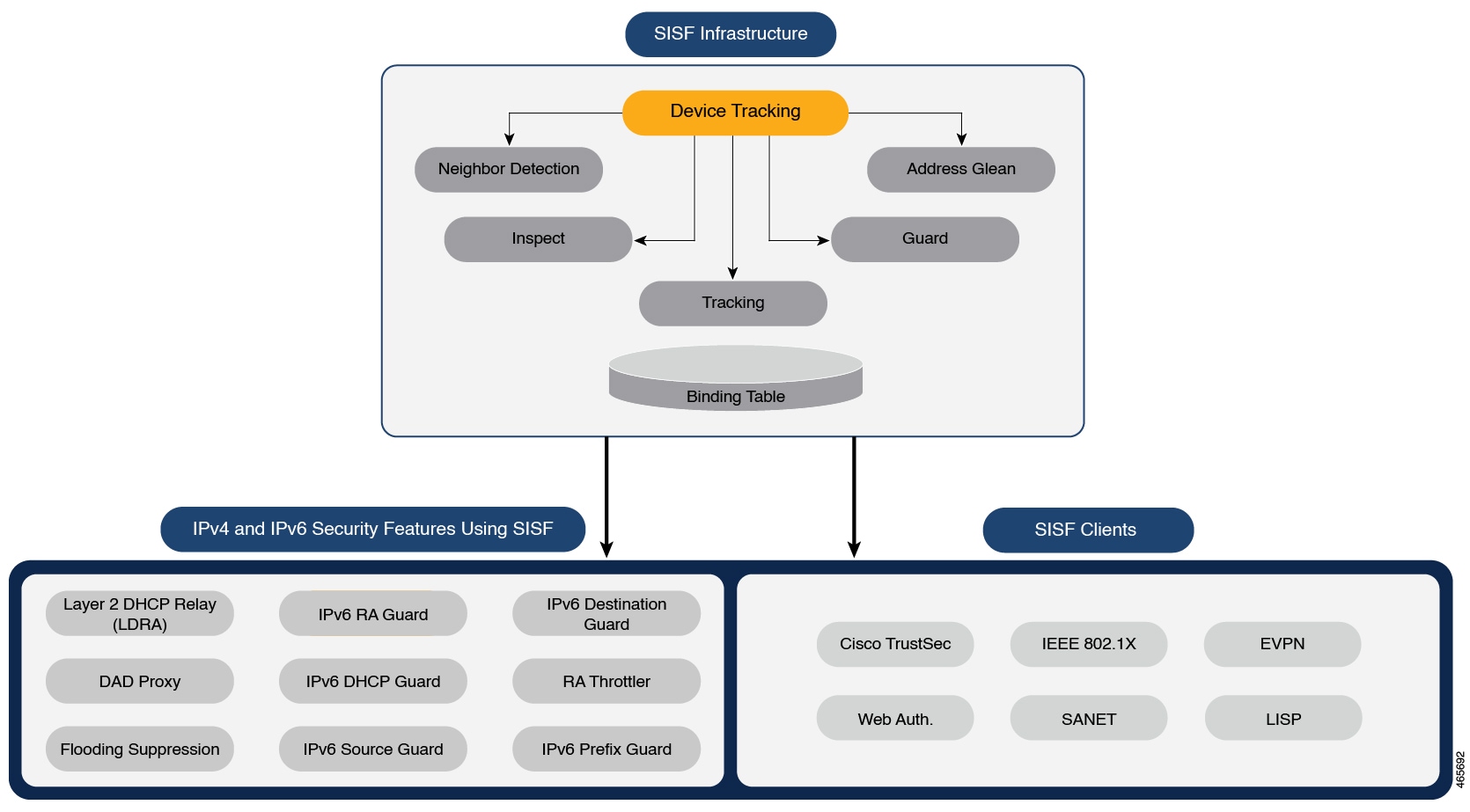
Information About SISF
Overview
Switch Integrated Security Features (SISF) is a framework developed to optimize security in Layer 2 domains. It merges the IP Device Tracking (IPDT) and certain IPv6 first-hop security (FHS) functionality1, to simplify the migration from IPv4 to IPv6 stack or a dual-stack.
The SISF infrastructure provides a unified database that is used by:
-
IPv6 FHS features: IPv6 Router Advertisement (RA) Guard, IPv6 DHCP Guard, Layer 2 DHCP Relay, IPv6 Duplicate Address Detection (DAD) Proxy, Flooding Suppression, IPv6 Source Guard, IPv6 Destination Guard, RA Throttler, and IPv6 Prefix Guard.
-
Features like Cisco TrustSec, IEEE 802.1X, Locator ID Separation Protocol (LISP), Ethernet VPN (EVPN), and Web Authentication, which act as clients for SISF.
 Note |
The terms “SISF” “device-tracking” and “SISF-based device-tracking” are used interchangeably in this document and refer to the same feature. Neither term is used to mean or should be confused with the legacy IPDT or IPv6 Snooping features. |
Understanding the SISF Infrastructure
This section explains the various elements of the SISF infrastructure as shown in the SISF Framework.
The Binding Table
The SISF infrastructure is built around the binding table. The binding table contains information about the hosts that are connected to the ports of a switch and the IP and MAC address of these hosts. This helps to create a physical map of all the hosts that are connected to a switch.
Each entry in a binding table provides the following information about a connected host:
-
IPv4 or IPv6 address of the host.
-
MAC address of the host. The same MAC address may be linked to an IPv4 and IPv6 address.
-
The interface or port on the switch that the host is connected to, and the associated VLAN.
-
The state of the entry, which indicates the reachability of the entry.
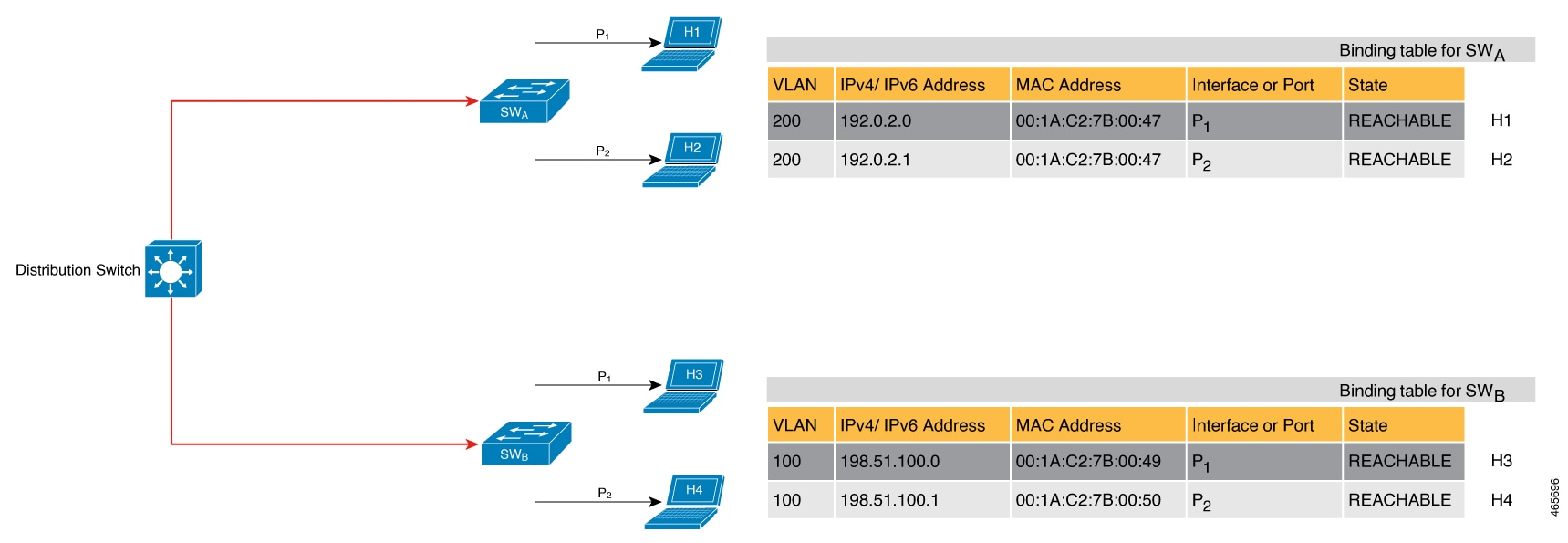
The following figure shows a simple network topology and a representative binding table for each access switch in the network. SWA and SWB are the two access switches in the network. The two access switches are connected to the same distribution switch. H1, H2, H3, H4 are the hosts.
This is an example of a distributed binding table, that is, each access switch in the network has its own table. An alternative set-up could be one centralised binding table on the distribution switch with the entries of SWA and SWB.
Having a distributed or a centralised binding table is a key design choice in the process of implementing SISF in your network and is covered in greater detail in the Understanding Policy Parameters section in this chapter.
States and Lifetime of a Binding Table Entry
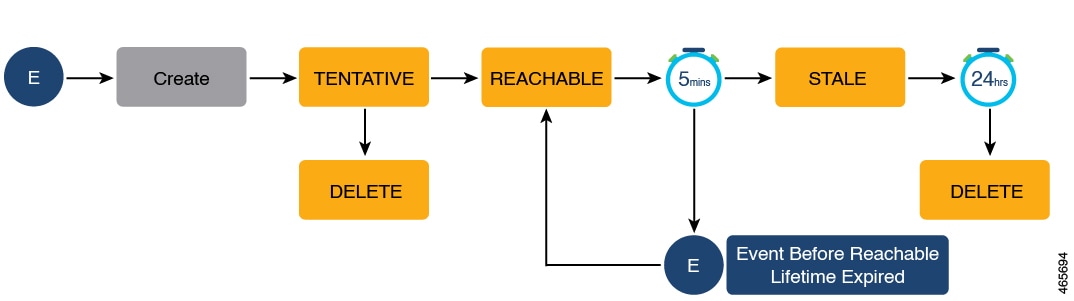
The state of an entry indicates if the host is reachable or not. The stable states of a binding table entry are: REACHABLE, DOWN, and STALE. When changing from one state to another, an entry may have other temporary or transitional states such as: VERIFY, INCOMPLETE, and TENTATIVE.
How long an entry remains in a given state is determined by its lifetime and by whether or not the entry is validated successfully. The lifetime of an entry can be policy-driven or configured globally.
device-tracking binding { reachable-lifetime { seconds | infinite } | stale-lifetime { seconds | infinite } | down-lifetime { seconds | infinite } }
State: Reachable
If an entry has this state, it means the host (IP and MAC address) from which a control packet was received, is a verified and valid host. A reachable entry has a default lifetime of 5 minutes. You can also configure a duration. By configuring a reachable-lifetime, you specify how long a host can remain in a REACHABLE state, after the last incoming control packet from that host.
If an event is detected before the entry’s reachable lifetime expires, then the reachable lifetime is reset.
To qualify for the REACHABLE state, a new entry goes through the process illustrated in the figure below. The switch detects an event (E), such as an incoming control packet from a connected host and creates an entry. Various events cause the creation of an entry, and these are described in the Binding Table Sources section. The creation of an entry is followed by different transient states, such as TENTATIVE or INCOMPLETE. While in a transitional state, the switch validates and confirms the integrity of the binding entry. If the entry is found to be valid, then the state changes to REACHABLE.
But if an address theft or similar event is detected, then the entry is regarded as invalid and is deleted. For example, if an attacker sends unsolicited neighbor advertisement messages with the same IP as the target IP and its (attacker's) own MAC address to redirect traffic.

State: Stale
If an entry is in this state it means that the entry’s reachable lifetime has expired and the corresponding host is still silent (no incoming packets from the host). A stale entry has a default lifetime of 24 hours. You can also configure a duration. An entry that remains in the STALE state beyond the stale lifetime, is deleted.
This is illustrated in the figure below which depicts the lifecycle of an entry.
State: Down
If an entry is in this state, it means that the host’s connecting interface is down. A down entry has a default lifetime of 24 hours. You can also configure a duration. An entry that remains in the DOWN state beyond the down lifetime, is deleted.
Polling a Host and Updating the Binding Table Entry
Polling is a periodic and conditional checking of the host to see the state it is in, whether it is still connected, and whether it is communicating. In addition to determining an entry’s state, you can use polling to reconfirm an entry's state.
You can enable polling with the device-tracking tracking command in global configuration mode. After you do, you still have the flexibility to turn polling on or off for a particular interface or VLAN. For this, configure the tracking enable or tracking disable keywords in the policy (the device-tracking configuration mode). When polling is enabled, the switch polls the host at the specified interval, thus reconfirming its reachability for the duration of its reachable lifetime.
When polling is enabled, the switch sends up to three polling requests, after the reachable lifetime expires, at system-determined intervals. You can also configure this interval with the device-tracking tracking retry-interval seconds command in global configuration mode.
The figure below depicts the lifecycle of an entry where the host is polled. Default reachable and stale lifetimes, and retry intervals are used in figure:
An event (E) is detected and a REACHABLE entry is created.
If an event is detected during the reachable lifetime, the reachable lifetime timer is reset.
The switch sends a polling request after the reachable lifetime expires. The switch polls the host up to three times at fixed, system-determined intervals. The polling request may be in the form of a unicast Address Resolution Protocol (ARP) probe or a Neighbor Solicitation message. During this time the state of the entry changes to VERIFY. If a polling response is received (thus confirming reachability of the host), the state of the entry changes back to REACHABLE.
If the switch does not receive a polling response after three attempts, the entry changes to the STALE state. It remains in this state for 24 hours. If an event is detected during the stale lifetime, the state of the entry is changed back to REACHABLE. At expiry of the stale lifetime, the device sends one final polling to ascertain reachability. If this final polling attempt receives a reply, the state of the entry is changed back to REACHABLE. If the final polling attempt does not receive a response, the entry is deleted.

Binding Table Sources
This section describes the sources of information and events that cause the creation and update of a binding table entry.
-
Learning events that dynamically populate the binding table:
-
Dynamic Host Configuration Protocol (DHCP) negotiation (DHCP REQUEST, and DHCP REPLY). This includes DHCPv4 and DHCPv6.
-
Address Resolution Protocol (ARP) packets.
Starting with Cisco IOS XE Amsterdam 17.3.1, ARP packets are throttled to mitigate high CPU utilization scenarios. In a five second window, a maximum of 50 ARP broadcast packets per binding entry are processed by SISF. When the limit is reached, incoming ARP packets are dropped. Note that the limit of 50 in five seconds is for each binding entry, that is, for each source IP.
-
Neighbor Discovery Protocol (NDP) packets.
-
Multiple Identity Association-Nontemporary Address (IA_NA) and Identity Association-Prefix Delegation (IA_PD).
In some cases, a network device can request and receive more than one IPv6 address from the DHCP server. This may be done to provide addresses to multiple clients of the device, such as when a residential gateway requests addresses to distribute to its LAN clients. When the device sends out a DHCPv6 packet, the packet includes all of the addresses that have been assigned to the device.
When SISF analyzes a DHCPv6 packet, it examines the IA_NA (Identity Association-Nontemporary Address) and IA_PD (Identity Association-Prefix Delegation) components of the packet and extracts each IPv6 address contained in the packet. SISF adds each extracted address to the binding table.
-
-
Configuration of static binding entries.
If there are silent but reachable hosts in the Layer 2 domain, you can create static binding entries to retain binding information even if the host becomes silent.
For this, you configure the following command in global configuration mode: device-tracking binding vlan vlan-id {ipv4_address ipv6_address ipv6_prefix} {interface interface-type_no } .
 Note |
In addition to the primary or key events listed above, there is a specific scenario in which a ping can result in a device-tracking entry. If a sender’s ARP cache or IPv6 neighbor table doesn’t have the target’s IP address yet, then a ping triggers an ARP packet for IPv4, or ND packet for IPv6. This can result in a device-tracking entry. But if the target IP is already in the ARP cache or IPv6 neighbour table, no ARP or ND packet is generated when you ping - in which case SISF cannot learn the IP address. |
Device-Tracking
SISF-based device-tracking is disabled by default. You can enable the feature on an interface or VLAN.
When you enable the feature, the binding table is created, followed by subsequent maintenance of the binding table.
The events listed in the Binding Table Sources section act as triggers for SISF-based device-tracking, to track the presence, location, and movement of hosts in the network, to populate and maintain the binding table. For example, if information about a host is learnt by means of an ARP or ND packet, every subsequent ARP or ND packet from the same host acts as an alert for SISF-based device-tracking, to refresh the entry in the binding table, thus indicating if the host is still present in the same location or has moved.
The continuous process of snooping of packets that the switch receives, extraction of device identity (MAC and IP address), and storage of information in the binding table of the switch, ensures binding integrity and maintains the reachability status of the hosts in the binding table.
For information how to enable SISF-based device-tracking, see How to Configure SISF.
Device-Tracking Policy
A device-tracking policy is a set of rules that SISF-based device-tracking follows. The policy dictates which events will be listened to, whether a host will be probed, the wait time before the host is probed, and so on. These rules are referred to as policy parameters.
 Note |
The policy must be attached to an interface or VLAN. Only then is the binding table for that interface or VLAN populated - in accordance with policy parameters. For information about the various ways in which you can create a policy, see How to Configure SISF. To display a policy's settings, use the show device-tracking policy policy_name command in privileged EXEC mode. |
Understanding Policy Parameters
Policy parameters are the keywords available for configuration in the device-tracking configuration mode. Each policy parameter addresses one or more aspects of network security.
This section explains the purpose of some of the important policy parameters so you can configure your policy to better suit your requirements.
Device(config)# device-tracking policy example_policy
Device(config-device-tracking)# ?
device-tracking policy configuration mode:
device-role Sets the role of the device attached to the port
limit Specifies a limit
security-level setup security level
tracking Override default tracking behavior
trusted-port setup trusted port
For information about all the paramters displayed in the device-tracking configuration mode, see the command reference document of the corresponding release.
Glean versus Guard versus Inspect
When a packet enters the network, SISF extracts the IP and MAC address (the source of the packet) and subsequent action, is dictated by the security-level that is configured in the policy.
Glean, guard, and inspect are the options available under the security-level parameter. Glean is the least secure option, inspect, is moderately secure, and guard, is the most secure.
To configure this parameter in a policy, enter the security-level keyword in the device-tracking configuration mode.
Glean
When the security-level is set to glean, SISF extracts the IP and MAC address and enters them into the binding table, without any verification. This option therefore does not ensure binding integrity. It may for example, be suited to a set-up where client applications such as IEEE 802.1X or SANET want to only learn about the host and not rely on SISF for authentication.
The only factor that affects the addition of the binding entry for this security-level, is the address count limit. There are separate limits for the maximum number of IPs per port, IPv4 per MAC, and IPv6 per MAC. Entries are rejected once a limit is reached. For more information about this parameter, see Address-Count Limits.
Guard
This is the default value for the security-level parameter.
When the security-level is set to guard, SISF extracts and verifies the IP and MAC address of packets entering the network. The outcome of the verification determines if a binding entry is added, or updated, or if the packet is dropped and the client is rejected.
The process of verification starts with the search for a matching entry in the database. The database may be centralised or distributed. If a matching entry is not found, a new entry is added.
If a matching entry is found and the points of attachment (MAC, VLAN, or interface) are found to be the same, only the timestamp is updated. If not, the scope of verification is extended to include validation of address ownership. This may include host polling to determine if the change in the point of attachment (a different MAC, or VLAN) is valid. If the change is valid the entry is updated, or if it is a case of theft, the entry is not added to the binding table.
If a binding entry is added or updated, the corresponding client is granted access to the network. If an entry does not pass verification, the corresponding client is rejected.
 Note |
The verification process affects not only the binding entry, but also the corresponding incoming packet. |
SISF uses only a copy of the packet when its IPv4. When its an IPv6 packet, SISF stops the orginal packet for the duration of the verification. A rejected entry means the following for the corresponding packet:
-
If the incoming packet is IPv4, the packet is allowed to go through even if the entry is rejected.
-
If the incoming packet is IPv6, a rejected entry means that the packet is also dropped.
Inspect
Even though security-level inspect is available on the CLI, we recommend not using it. The glean and guard options described above address most use cases and network requirements.
Trusted-Port and Device-Role Switch
The device-role switch and trusted-port options help you design an efficient and scalable “secure zone”. When used together, these two parameters help you achieve an efficient distribution of the creation of entries in the binding table. This keeps the binding tables size under control.
The trusted-port option: Disables the guard function on configured targets. Bindings learned through a trusted-port have preference over bindings learned through any other port. A trusted port is also given preference in case of a collision while making an entry in the table.
The device-role option: Indicates the type of device that is facing the port and this can be a node or a switch. To allow the creation of binding entries for a port, you configure the device as a node. To stop the creation of binding entries, you configure the device as switch.
Configuring the device as a switch is suited to multi-switch set-ups, where the possibility of large device tracking tables is very high. Here, a port facing a device (an uplink trunk port) can be configured to stop creating binding entries, and the traffic arriving at such a port can be trusted, because the switch on the other side of the trunk port will have device-tracking enabled and that will have checked the validity of the binding entry.
 Note |
While there are scenarios where configuring only either one of these options may be suitable, the more common use case is for both the trusted-port and device-role switch options to be configured on the port - the examples below explain this in detail. Possible scenarios where only either one of these options is suited or required have also been described, at the end of this section. |
To configure these parameters in a policy, enter the trusted-port and device-role keywords in the device-tracking configuration mode.
Example: Using Trusted-Port and Device-Role Switch Options in a Multi-Switch Set-Up
The following example explains how the device-role switch and trusted-port options help to design an efficient and scalable “secure zone”.
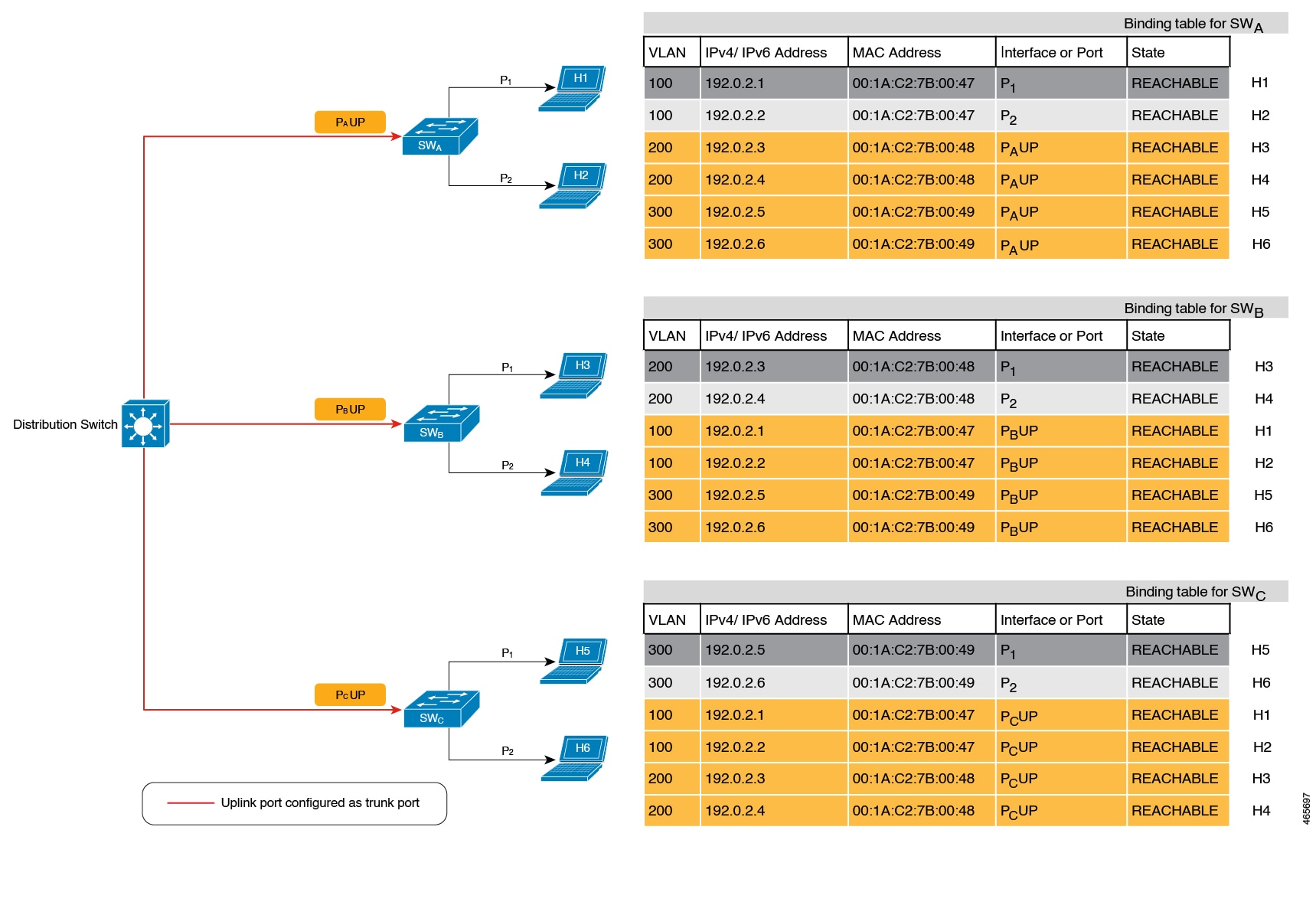
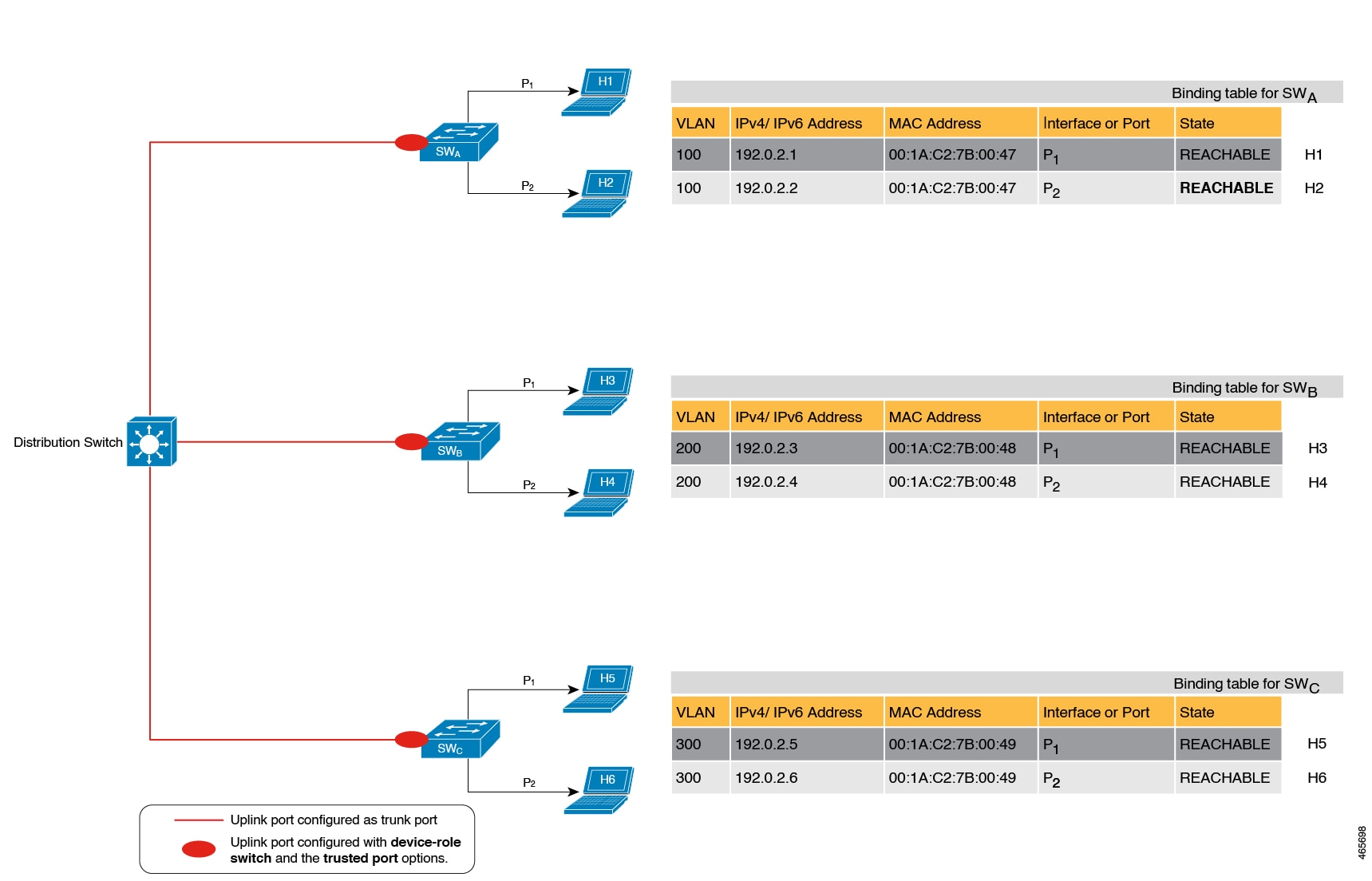
In figure Multi-Switch Set-Ups Without Trusted-Port and Device-Role Switch Options below, SWA, SWB, and SWC are three access switches. They are all connected to a common distribution switch. The only required configuration on the distribution switch in this scenario is to ensure that traffic of any kind is not blocked.
H1, H2, …H6 are the hosts. Each switch has two directly connected hosts. All hosts are communicating with each other, that is, control packets are being transmitted. All hosts are also within the same VLAN boundary. Each switch is receiving control packets from hosts that are directly connected to it, and also from hosts that are connected to other switches. This means SWA is receiving control packets from H1, H2, …H6 similarly with SWB and SWC.
For each switch, the entries of directly connected hosts have interface or port P1 and P2 in the binding table. Entries originating from hosts that are connected to other switches have interface or port name PxUP, to show that they have been learned through the uplink port (x represents the corresponding uplink port for each switch. For example, the entries that SWA has learnt through its uplink port have interface or port name PAUP and for SWB it is PBUP, and so forth.
The end result is that each switch learns and creates binding entries for all hosts in the set-up.
This scenario displays an inefficient use of the binding table, because each host is being validated multiple times, which does not make it more secure than if just one switch validates host. Secondly, entries for the same host in multiple binding tables could mean that the address count limit is reached sooner. After the limit is reached, any further entries are rejected and required entries may be missed this way.
By contrast see figure Multi-Switch Set-Ups With Trusted-Port and Device-Role Switch Options below. Here when SWA intercepts the packet of a host that is not attached to it (say H3 which is directly attached to SWB), it does not create an entry because it detects that H3 is attached to a device that is configured as a switch (device-role switch option) and the uplink port of the switch (where the packet came from) is a trusted port (trusted-port option).
By creating binding entries only on switches where the host appears on an access port (port P1 and P2 of each switch), and not creating entries for a host that appears over an uplink port or trusted port (Px UP), each switch in the set-up validates and makes only the required entries, thus achieving an efficient distribution of the creation of binding table entries.
A second advantage of configuring device-role switch and trusted-port options in a multi-switch scenario is that it prevents duplicate entries when a host, say H1 moves from one switch to another. H1’s IP and MAC binding in the earlier location (let’s say SWA) continues to remain there until it reaches the STALE state. But if H1 moves and connects to a second switch, say SWC, then SWA receives a duplicate binding entry through the uplink port. In such a situation, if the uplink port of the second switch (SWC) is configured as a trusted port, SWA deletes its stale entry. Further, it doesn’t create another new binding entry because the SWC will already have the latest entry and this entry is trusted.
Example: When Not to Use Trusted-Port and Device-Role Switch Options
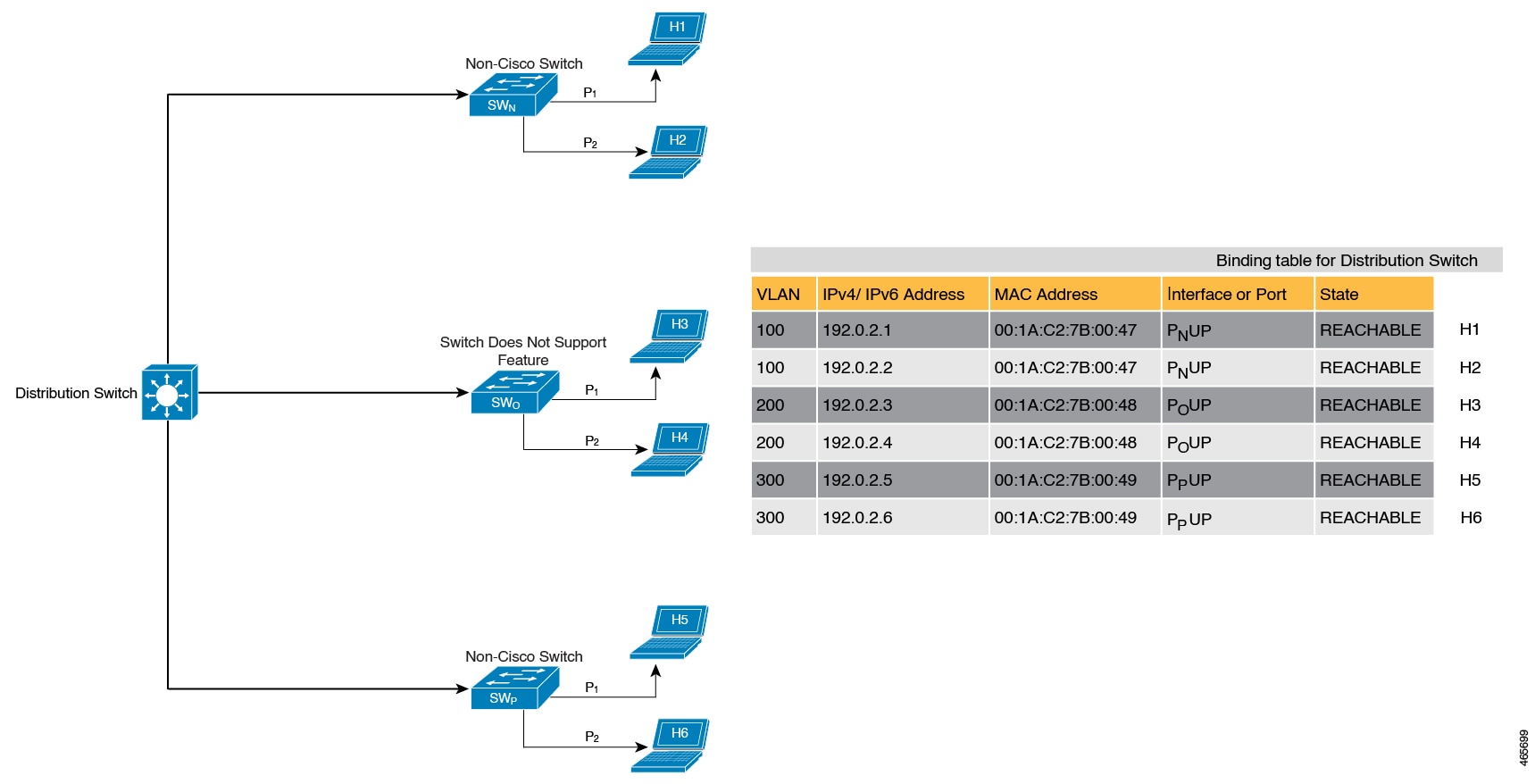
While the previous example clarifies how a multi-switch set-up with distributed binding tables stands to benefit from the device-role switch and trusted-port options, it may not suit networks of the following kinds:
-
Networks where non-Cisco switches are being used
-
Networks where the switch does not support the SISF-based device-tracking feature.
In both cases, we recommended that you not configure the device-role switch and trusted-port options. Further, we recommended that you maintain a centralised binding table - on the distribution switch. When you do, all the binding entries for all the hosts connected to non-Cisco switches and switches that do not support the feature, are validated by the distribution switch and still secure your network. The figure below illustrates the same.
Creating an Efficient and Scalable Secure Zone
By using the trusted-port and device-role switch options in suitable networks and leaving them out in others, you can achieve an efficient and scalable secure zone.
Secure Zones 1, 2 and 3, display three different set-ups and the secure zone that is established in each case.
| Secure Zone: |
Secure Zone 1 - Inefficient and Unscalable Secure Zone |
Secure Zone 2 - Efficient and Scalable Secure Zone When Binding Tables are Decentralized |
Secure Zone 3: Efficient Secure Zone When Binding Table is Centralized |
|---|---|---|---|
| Scalability: | Unscalable; each switch has entries of all the hosts in the network | Scalable; each switch as entries of only directly connected hosts | Unscalable; the distribution switch has entries of all hosts in the network |
|
Polling and its effect on the network: n = number of hosts m = number of switches total number of polling requests: = n X m |
18 polling requests are being sent (6 hosts x 3 switches). Each host is polled by all the switches in the network (in the absence of the trusted-port and device-role switch options). Network load is very high. |
6 polling requests are being sent (2 hosts x 1 switch for each switch). Minimal network load. (Polling requests are sent by the local access switches to directly connected hosts, each polling request passes through fewer points in the network.) |
6 polling requests are being sent (6 hosts x 1 switch) Network load is higher than secure zone 2, but not as high as secure zone 1. (Polling requests come from the distribution switch and go through the access switch before reaching the host.) |
| Efficiency: |
Inefficient binding table, because the binding table is duplicated on each switch. |
Efficient binding table, because each host’s binding information is entered only once, and in one binding table and this the binding table of the directly connected switch. | Efficient binding table, because the binding information for each host is entered only once, and this is in the central binding table, which is on the distribution switch. |
| Recommended Action: | Reapply suitable policies to make the secure zone like secure zone 2 | None; this is an efficient and scalable secure zone. | None; this is the best possible secure zone given the type of set-up (where the other switches in the network are either non-Cisco or do not support the feature) |



When to Use Only Trusted-Port or Only Device-Role Switch
Configuring only device-role switch is suited to situations when you want to listen but not learn entries. For example, for Duplicate Address Detection (DAD), or when you want to send IPv6 or Neighbor Solicitation (NS) message on a switch-facing port.
When you configure this option on a switch port (or interface), SISF-based device-tracking treats the port as a trunk port, implying that the port is connected to other switches. It does not matter whether the port is actually a trunk port or not. Therefore, when NS packets or queries are sent to switches in the network for new entry validation, only the secure ports (ports where the device-role switch is configured) receive the packet or query. This safeguards the network. If the command is not configured on any port, a general broadcast of the query is sent.
Configuring only trusted-port is suited to situations where an access port should be configured as a trusted port. If an access port is connected to a DHCP server or a similar service that the switch is consuming, configuring an access port as a trusted port ensures that the service is not disrupted because traffic from such a port is trusted. This also widens the secure zone, to include the access port.
Address Count Limits
The address count limit parameter specifies limits for the number of IP and MAC addresses that can be entered in a binding table. The purpose of these limits is to contain the size of the binding table based on the number of known and expected hosts, thus enabling you to take pre-emptive action against rogue hosts or IPs in the network.
At a policy level there are separate limits for the number of IP addresses per port, the number of IPv4 addresses per MAC, and IPv6 addresses per MAC. You can configure or change only the number of IP addresses per port.
IP per Port
The IP per port option is the total number of IP addresses allowed for a port. The address can be IPv4 or IPv6. When the limit is reached, no further IP addresses (i.e., entries) are added to the binding table.
To configure this parameter in a policy, enter the limit address-count ip-per-port keyword in the device-tracking configuration mode. If you configure a limit that is lower than the currently configured one, then the new (lower) limit is applicable only to new entries. An existing entry remains in the binding table and goes through its binding entry lifecycle.
IPv4 per MAC and IPv6 per MAC
The number of IPv4 addresses that can be mapped to one MAC address and the number of IPv6 addresses that can be mapped to one MAC address. When the limit is reached, no further entries can be added to the binding table, and traffic from new hosts will be dropped.
 Note |
The IPv4 per MAC limit and the IPv6 per MAC limit that is effective on an interface or VLAN is as defined in the policy that is applied. If the policy does not specify a limit, this means that a limit does not exist. You cannot change or configure a limit for IPv4 per MAC or IPv6 per MAC for any kind of policy (programmatic, or custom policy, or default policy). |
Device# show device-tracking policy LISP-DT-GUARD-VLAN
Policy LISP-DT-GUARD-VLAN configuration:
security-level guard (*)
<output truncated>
limit address-count for IPv4 per mac 4 (*)
limit address-count for IPv6 per mac 12 (*)
tracking enable
<output truncated>Overall Address Count Limit Considerations
-
The limits do not have a hierarchy, but the threshold that is set for each limit affects the others.
For example, if the IP per port limit is 100, and the IPv4 per MAC limit is one. The limit is reached with a single host’s IPv4-MAC binding entry. No further entries are allowed even though the port has a provision for 99 more IP addresses.
-
Address count limits and the security-level parameter.
For information about how the address count limits interact with the security-level parameter glean, see Glean.
When the security-level parameter is guard, reaching an address count limit results in a rejection of the entry. This has the following effect on the incoming packet:
-
If the incoming packet is IPv4, the packet is allowed to go through even though the entry is rejected.
-
If the incoming packet is IPv6, a rejected entry means that the packet is also dropped.
-
-
Global and policy-level limits
The limits configured with the device-tracking binding max-entries command are at the global level, the limits configured with the limit address-count command in the device-tracking configuration mode are for a policy, which is at the interface or VLAN level.
If a policy-level value and a globally configured value exists, the creation of binding entries is stopped when a limit is reached - this can be any one of the global values or the policy-level value.
If only globally configured values exist, the creation of binding entries is stopped when a limit is reached.
If only a policy-level value exists, the creation of binding entries is stopped when the policy-level limit is reached.
Tracking
The tracking parameter involves tracking of hosts in the network. In section Polling a Host and Updating the Binding Table Entry above, this is referred to as "polling". It also describes polling behaviour in detail.
To configure polling parameters at the global level, enter the device-tracking tracking command in global configuration mode. After you configure this command you still have the flexibility to turn polling on or off, for individual interfaces and VLANs. For this you must enable or disable polling in the policy.
To enable polling in a policy, enter the tracking enable keywords in the device-tracking configuration mode. By default, polling is disabled in a policy.
Guidelines for Policy Creation
-
If multiple policies are available on a given target, a system-internal policy priority determines which policy takes precedence.
A manually created policy has the highest priority. When you want to override the settings of a programmatically created policy, you can create a custom policy, so it has higher priority.
-
The parameters of a programmatically created policy cannot be changed. You can configure certain attributes of a custom policy.
Guidelines for Applying a Policy
-
Multiple policies can be attached to the same VLAN.
-
If a programmatic policy is attached to a VLAN and you want to change policy settings, create a custom device-tracking policy and attach it to the VLAN.
-
When multiple policies with different priorities are attached to the same VLAN, the settings of the policy with the highest priority are effective. The exceptions here are the limit address-count for IPv4 per mac and limit address-count for IPv6 per mac settings - the settings of the policy with the lowest priorty are effective.
-
When a device-tracking policy is attached to an interface under a VLAN, the policy settings on the interface take precedence over those on its VLAN; exceptions here are the values for limit address-count for IPv4 per mac and limit address-count for IPv6 per mac, which are aggregated from the policy on both the interface and VLAN.
-
A policy cannot be removed unless the device tracking client feature configuration is removed.
 Feedback
Feedback