Components Involved
All possible components involved in an implementation of Smart Licensing Using Policy are listed here, along with a brief description of the component’s role in the implementation.
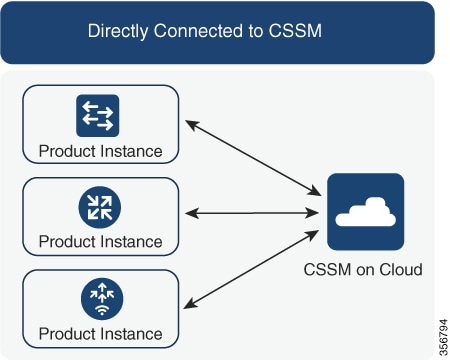
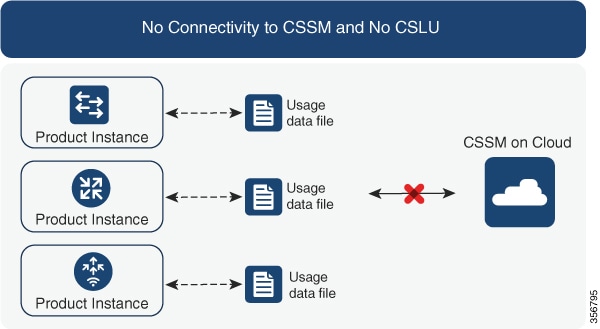
Out of all these components, two are necessarily part of any implementation: the product instance and Cisco SSM. The product instance, because it consumes the license and Cisco SSM because it is the central portal for information about Cisco software licenses.
Product Instance
A product instance is a single instance of a Cisco product, identified by a Unique Device Identifier (UDI). A product instance records and reports license usage (RUM reports), and provides alerts and system messages about overdue reports, communication failures, etc. RUM reports and usage data are securely stored in the product instance.
Throughout this document, the term product instance refers to all supported physical and virtual product instances - unless noted otherwise. For information about the product instances that are within the scope of this document, see Supported Products.
Cisco Smart Software Manager (Cisco SSM)
Cisco SSM is a portal that enables you to manage all your Cisco software licenses from a centralized location. Cisco SSM helps you manage current requirements and review usage trends to plan for future license requirements.
You can access the Cisco SSM Web UI at https://software.cisco.com. Under Smart Software Manager, click the Manage Licenses link.
The Connecting to Cisco SSM section in this document explains the different ways in which you can connect to Cisco SSM.
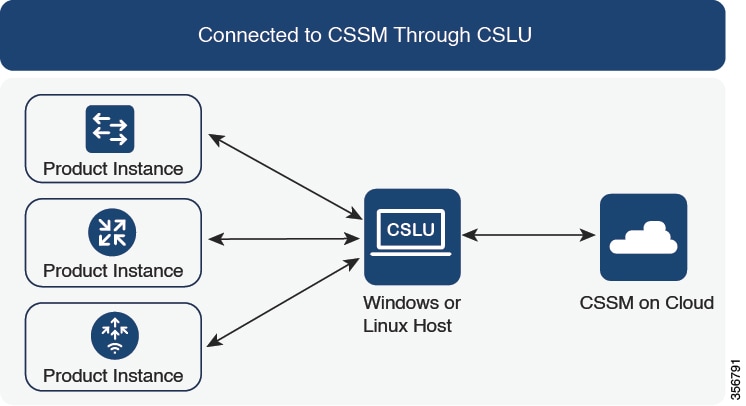
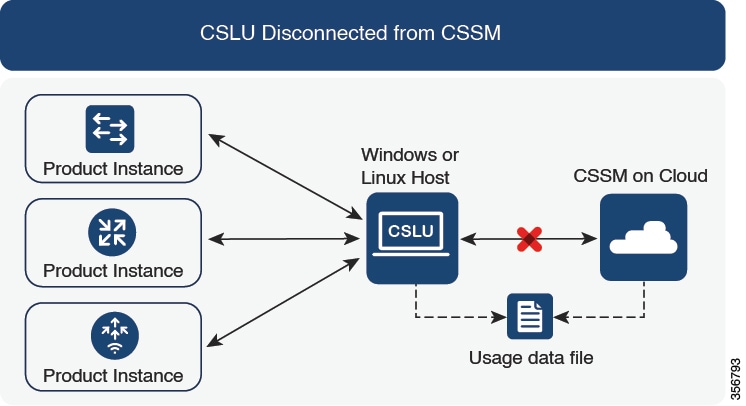
Cisco Smart License Utility (CSLU)
CSLU is a Windows-based reporting utility that provides aggregate licensing workflows. This utility performs these key functions:
-
Provides options relating to how workflows are triggered. The workflows can be triggered by CSLU or by the product instance.
-
Collects usage reports from the product instance and uploads these usage reports to the corresponding Smart Account or Virtual Account – online, or offline, using files. Similarly, the RUM report ACK is collected online, or offline, and sent back to the product instance.
-
Sends authorization code requests to Cisco SSM and receives authorization codes from Cisco SSM, if applicable.
CSLU can be integrated into the Smart Licensing Using Policy implementation in several ways. As a Windows application that is a standalone tool connected to or disconnected from Cisco SSM. Alternatively, it can be deployed on a machine (laptop or desktop) running Linux. It can also be embedded by Cisco in a controller such as Cisco Catalyst Center.
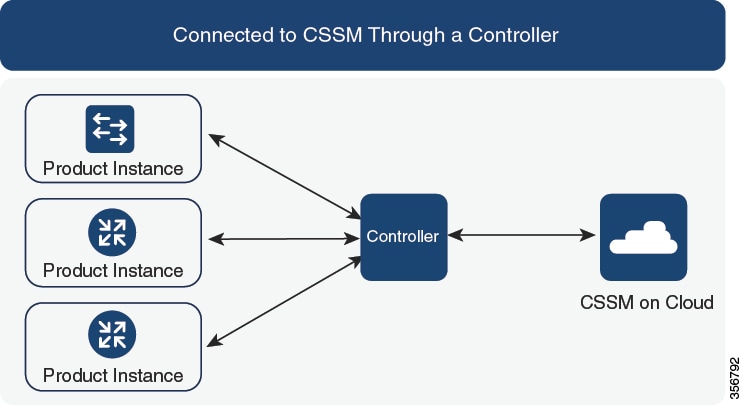
Controller
A management application or service that manages multiple product instances. On Cisco Catalyst 9000 Series Switches, Cisco Catalyst Center is the supported controller.
This table provides information about the supported controller, product instances that support the controller, and minimum required software versions on the controller and on the product instance.
|
Component |
Minimum Required Release |
|---|---|
|
Cisco Catalyst Center This is the minimum required Cisco Catalyst Center version that supports Smart Licensing Using Policy. Support continues on all subsequent releases - unless noted otherwise. |
Cisco DNA Center Release 2.2.2 |
|
Cisco Catalyst 9200 Series Switches Cisco Catalyst 9300 Series Switches Cisco Catalyst 9400 Series Switches Cisco Catalyst 9500 Series Switches Cisco Catalyst 9600 Series Switches |
Cisco IOS XE Amsterdam 17.3.2a This is the minimum required software version on the product instance. This means support continues on all subsequent releases - unless noted otherwise. |
For more information about Cisco DNA Center, see the support page at: https://www.cisco.com/c/en/us/support/cloud-systems-management/dna-center/series.html.
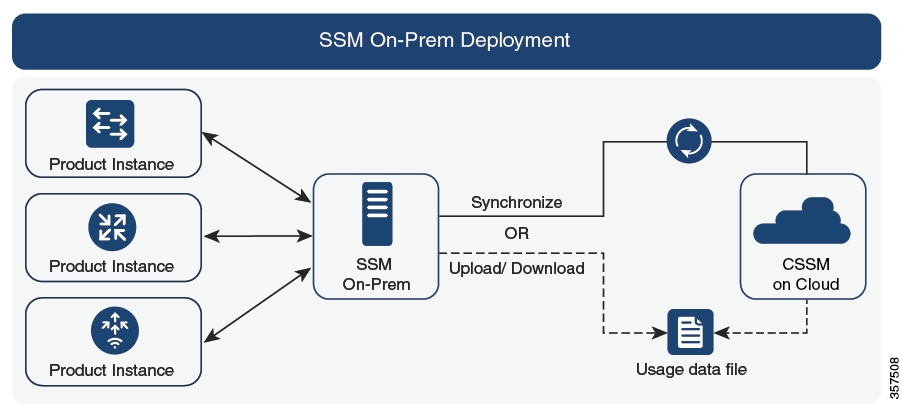
Cisco Smart Software Manager On-Prem (SSM On-Prem)
SSM On-Prem is a license server that enables license administration from a server inside an organization’s premises, instead of having to connect directly to Cisco SSM.
SSM On-Prem is locally connected and acts as a local license authority. It involves setting up an SSM on-prem license server, which synchronizes its license database with Cisco SSM periodically and functions similarly to Cisco SSM.
This table provides information about the minimum required version of SSM On-Prem and the minimum required software version on the supported product instances.
|
Component |
Minimum Required Release |
|---|---|
|
SSM On-Prem This is the minimum required SSM On-Prem version that supports Smart Licensing Using Policy. Support continues on all subsequent releases - unless noted otherwise. |
Version 8, Release 202102 |
|
Cisco Catalyst 9200 Series Switches Cisco Catalyst 9300 Series Switches Cisco Catalyst 9400 Series Switches Cisco Catalyst 9500 Series Switches Cisco Catalyst 9600 Series Switches |
Cisco IOS XE Amsterdam 17.3.3 This is the minimum required software version on the product instance. This means support continues on all subsequent releases - unless noted otherwise. |
For more information, see Cisco Smart Software Manager On-Prem Data Sheet.

 Feedback
Feedback