CTI Server
CTI Server, the basic server component of Cisco CTI, enables the Unified ICM software to deliver agent, call, and customer data in real-time to a server and/or workstation application as events occur throughout the life of a call. The CTI Server is a software process that runs on a Peripheral Gateway (PG). It is the CTI gateway into the Unified ICM software's data and services.
The following figure shows a sample CTI Server system. CTI Servers may be running at one or several call centers in the enterprise.
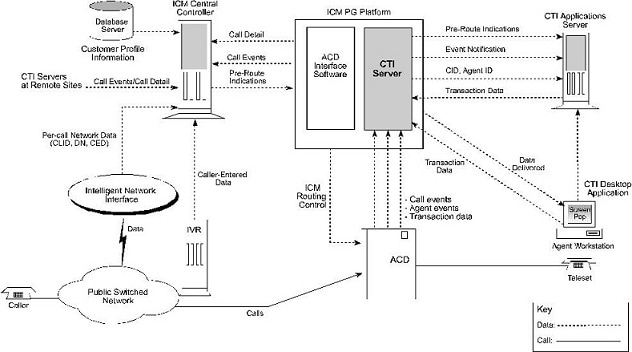
One function of the CTI Server is to forward pre-route indications to CTI application servers. Pre-route indications identify the caller and provide CTI applications with other call attributes while the call is still in the public or private network (that is, before the call is connected to an agent or IVR resource).
CTI Server also reports call events and agent work state changes as they occur through each stage of the call flow—from the moment a call arrives at an answering resource (ACD, PBX, IVR), until the caller hangs up. In a desktop application environment, call event information is delivered to the targeted agent desktop at the same time the call is delivered.
CTI Server Communications
The CTI Server uses TCP/IP Ethernet for communication with clients. You can use multi-protocol IP routers to provide connectivity to clients on other types of LANs. You can use the same LAN for the Peripheral Gateway's visible network interface and for CTI client-to-server communications.
CTI Server Platform Options
The CTI Server runs on a machine that is also running a Cisco ACD (or VRU) PG process. The shared platform option is shown in the following figure.

CTI Server Fault Tolerance
You can implement the CTI Server in a duplexed, fully fault-tolerant configuration. In a duplexed configuration, the CTI Server is installed on a pair of server platforms. In the event of a failed CTI client connection, the client process can automatically reestablish a connection to either side of the duplexed CTI Servers. The call's CTI client history list and any updates to call variables remain in effect when the connection is reestablished. The following figure shows a duplexed CTI Server configuration.

Cisco CTI Object Server (CTI OS)
CTI Object Server (CTI OS) is a high-performance, scalable, fault-tolerant server-based solution for deploying CTI applications. CTI OS serves as a single point of integration for third-party applications, including Customer Relationship Management (CRM) systems, data mining, and workflow solutions.
Configuration data is managed at the server, which helps simplify customization, updates, and maintenance of CTI applications. You can access and manage servers remotely. Thin-client and browser-based applications that do not require Cisco software on the desktop can be developed and deployed with CTI OS.
CTI OS incorporates the following major components:
-
CTI OS Toolkit
-
Client Interface Library
-
CTI OS Combo Desktop for Agents and Supervisors
CTI OS is a client of CTI Server. It has a single all-events connection to Cisco CTI Server. In turn, CTI OS accepts client connections using session, agent, and call interfaces. These interfaces are implemented in .NET, COM, Java, C++, and C, allowing for a wide range of application development uses. The interfaces are used for call control, to access data values, and to receive event notifications.
For complete and current information about the number of agents supported for CTI OS and other configurations, see the Solution Design Guide for Cisco Unified Contact Center Enterprise at http://www.cisco.com/c/en/us/support/customer-collaboration/unified-contact-center-enterprise/products-implementation-design-guides-list.html. See Virtualization for Unified Contact Center Enterprise at http://www.cisco.com/c/dam/en/us/td/docs/voice_ip_comm/uc_system/virtualization/virtualization-unified-contact-center-enterprise.html for hardware requirements for Unified CCE virtualized systems.
For all installations, the CTI OS Server must be co-resident with the PG.
For more information on CTI OS, refer to the CTI OS document set.




 Feedback
Feedback