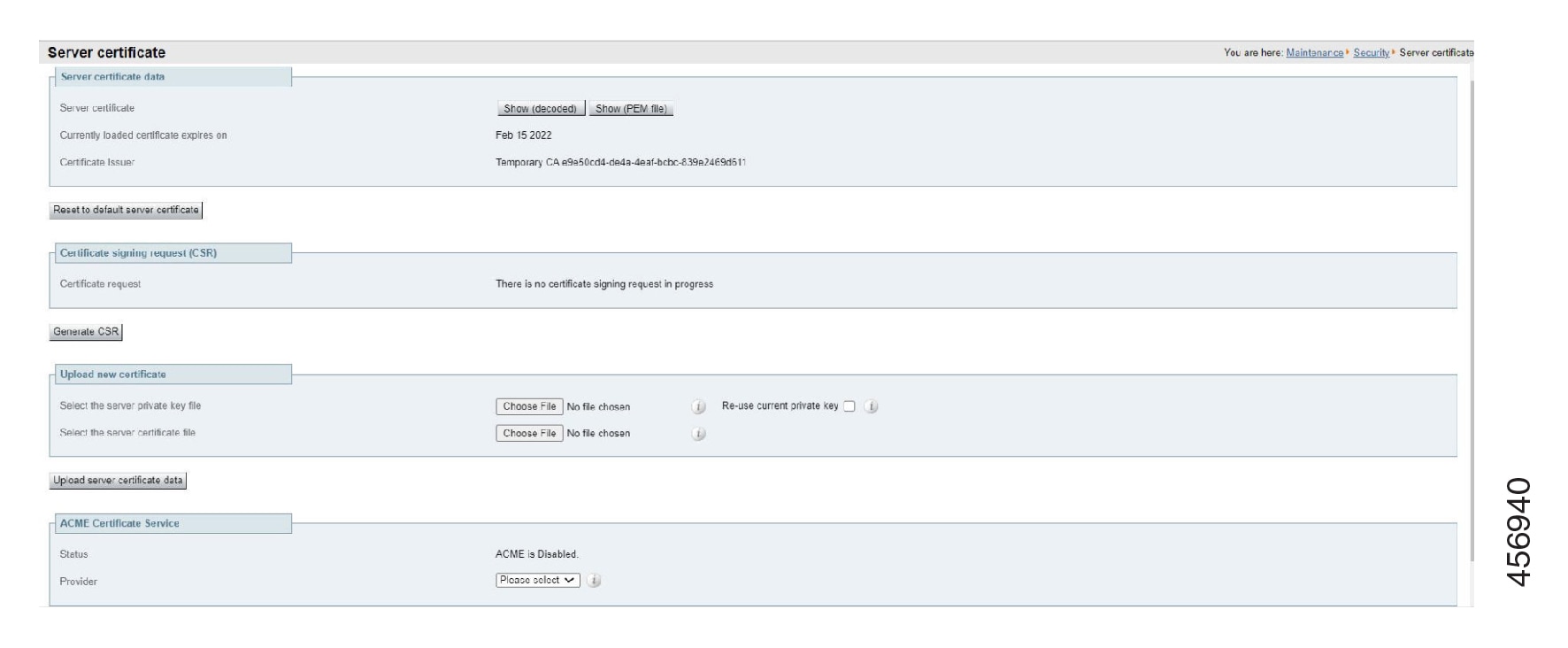
Loading Certificates and Keys Onto Expressway
The Expressway uses standard X.509 certificates. The certificate information must be supplied to the Expressway in PEM format. Typically three elements are loaded:
-
The server certificate (which is generated by the certificate authority, identifying the ID of the certificate holder, and should be able to act as both a client and server certificate).
-
The private key (used to sign data sent to the client, and decrypt data sent from the client, encrypted with the public key in the server certificate). This must only be kept on the Expressway and backed up in a safe place – security of the TLS communications relies upon this being kept secret.
-
A list of certificates of trusted certificate authorities.
 Note |
New installations of Expressway software (from X8.1 onwards) ship with a temporary trusted CA, and a server certificate issued by that temporary CA. We strongly recommend that you replace the server certificate with one generated by a trusted certificate authority, and that you install CA certificates for the authorities that you trust. |
 Note |
On Expressway-C and Expressway-E, we recommend that you do not upload multiple CA certificates with the same common name. This is because the endpoints may fail to log in if Expressway is configured to authenticate endpoints using an external IdP. |
 Warning |
Warning messages that may be displayed |
From X8.10, the upload mechanism for server certificates () displays a warning if the certificate fails to meet certain criteria. Cases when the warning is displayed include:
-
Certificate does not have an acceptable level of security.
-
Certificate is missing a common name (CN) attribute. An alarm is also raised in this case. Because some Expressway services don't work without the common name (MRA, Jabber Guest, and the Web Proxy for Cisco Meeting Server).
-
The certification authority (CA) or certificate revocation list (CRL) is not recognized.
The certificate upload is not prevented.

 Feedback
Feedback