Loading a Server Certificate and Private Key Onto Expressway
The Expressway’s server certificate is used to identify the Expressway when it communicates with client systems using TLS encryption, and with web browsers over HTTPS.
As well as these instructions, a video demonstration of the process provided by Cisco TAC engineers is available on the Expressway/VCS Screencast Video List page.
 Note |
We recommend you install the CA certificate first before installing the server certificate. Otherwise, the server certificate will fail to load. |
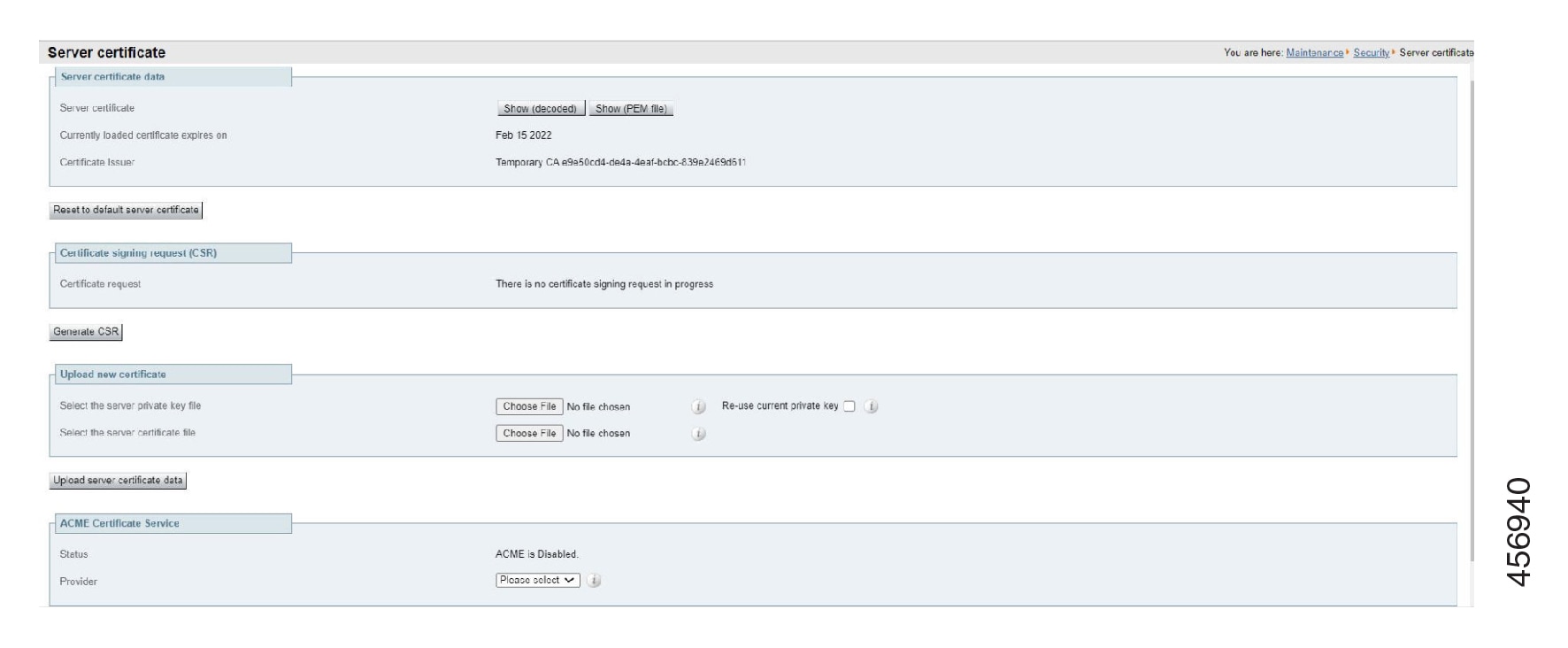
To upload a server certificate:
-
Go to .
-
Use the Browse button in the Upload new certificate section to select and upload the server certificate PEM file.

Note
Make sure to upload the Server certificate file with a valid FQDN.
-
If you upload a certificate with a hostname or IP in the SAN field, the upload fails with the error "File upload failed.: Subject alternative name must be a valid FQDN".
-
If you upload a certificate with a hostname or IP in the CN (common name) field, the upload fails with the error "File upload failed.: Common name must be a valid FQDN".
-
-
If you used an external system to generate the Certificate Signing Request (CSR) you must also upload the server private key PEM file that was used to encrypt the server certificate. (The private key file will have been automatically generated and stored earlier if the Expressway was used to produce the CSR for this server certificate.)
-
The server private key PEM file must not be password protected.
-
You cannot upload a server private key if a certificate signing request is in progress.
-
-
Click Upload server certificate data.
-
When you generate a CSR in X7, the application puts csr.pem and privkey_csr.pem into /tandberg/persistent/certs.
-
When you generate a CSR in X8, the application puts csr.pem and privkey.pem into /tandberg/persistent/certs/generated_csr.
Re-use current private key check box - According to your local security requirements, check the Re-use current private key check box if you don't want a new private key. You may want to do this if you are extending the validity of your current certificate or re-issuing a previously generated CSR.
-
-
Use the Provider drop-down list in the ACME Certificate Service section to select trusted ACME clients used for signing of CSRs.
If you want to upgrade from X7 and have an unsubmitted CSR, then we recommend you to discard the CSR before upgrade, and then regenerate the CSR after upgrade.


 Feedback
Feedback