System Management Overview
ASR 5500 management capabilities reflect the requirements of the Telecommunications Management Network (TMN) model for network element (NE) and element management system (EMS) functions. The system also supports external element management applications via standards-based protocols (CORBA and SNMPv1, v2). Wireless operators can readily integrate the ASR 5500 into their overall network, service, and business management systems. All management is performed out-of-band for security and to maintain system performance.
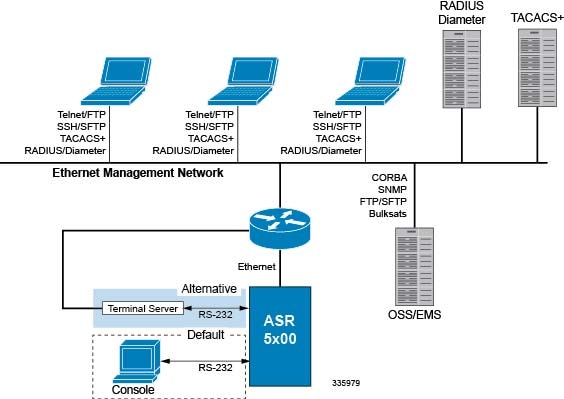
There are multiple ways to manage the system either locally or remotely using its out-of-band management interfaces.
-
Local login through the Console port on the MIO/MIO2 card using an RS-232 Console connection (RJ45) directly or indirectly via a terminal server
-
Remote login using Telnet, and Secure Shell (SSH) access to the CLI through the MIO/MIO2 card's Ethernet management interfaces:
-
Two autosensing RJ45 10/100/1000Base-T (IEEE 802.3ab) shielded twisted-pair (STP) ports

Important
In release 20.0 and higher Trusted StarOS builds, the Telnet and FTP options are not available.
-
-
The MIO2 card also supports two 10 GbE ports that accept 10GBase-SR fiber optic-to-electrical signal Small Form-Factor Pluggable (SFP+) transceivers. These ports are intended for local context only offload of data records and bulk statistics.
-
Support for Common Object Request Broker Architecture (CORBA) via an Object Request Broker Element Manager (ORBEM) interface and Simple Network Management Protocol version 1 (SNMPv1) and version 2 (SNMPv2) for fault management
-
Authentication via RADIUS/Diameter or TACACS+
The StarOS CLI provides complete Fault, Configuration, Accounting, Performance, and Security (FCAPS) capabilities as described in the remaining chapters of this guide.
 Important |
By default StarOS supports local Console access to the CLI via the RS-232 Console port for initial system configuration. |


 Feedback
Feedback