Product Description
Until recently, Wireless LAN (WLAN) security was considered poor in strength and ease-of-use compared with that of LTE networks and devices, and operators used their core networks to add security layers such as IKEv2 for UE authentication and authorization and IPSec for network security between the UEs and the core network gateways. With the deployment of 802.1x, 802.11u, 802.11i, and Hotspot 2.0, operators now consider WLAN security strength and ease-of-use to be as acceptable as LTE security.
The Cisco® S2a Mobility Over GTP (SaMOG) Gateway addresses this next step in network evolution by enabling mobile operators to provide IP access from trusted non-3GPP access networks to the 3GPP EPC (Evolved Packet Core) network via. the S2a interface, including traffic from trusted WiFi, femtocell, metrocell, and small cell access networks. The SaMOG Gateway allows operators to provide services to 3G subscribers using GGSN (GTPv1) and 4G subscribers using P-GW (GTPv2, PMIPv6) via. PMIPv6, EoGRE or L3IP access-types.
The SaMOG Gateway has the following key features:
- Provides seamless mobility between the 3GPP EPC network and WLANs for EPS (Evolved Packet System) services via. the GTPv1 based Gn interface, or GTPv2/PMIPv6-based S2a interface.
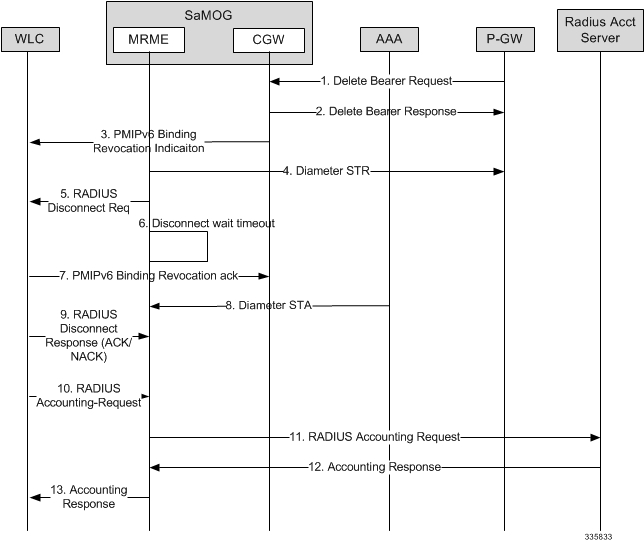
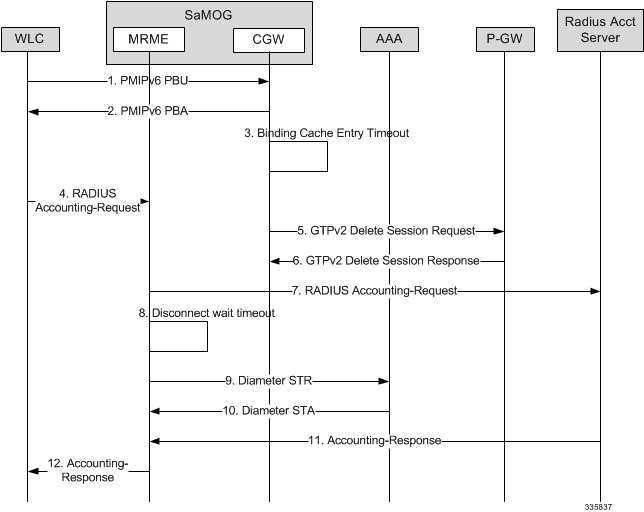
- Functions as a 3GPP Trusted WLAN Access Gateway (TWAG) as the Convergence Gateway (CGW) service. The CGW service terminates the S2a interface to the GGSN/P-GW and acts as the default router for the WLAN UEs on its access link.
- Functions as a 3GPP Trusted WLAN AAA Proxy (TWAP) as the Multi Radio Management Entity (MRME) service. The MRME service terminates the STa interface to the 3GPP AAA server and relays the AAA information between the WLAN IP access network and the AAA server, or AAA proxy in the case of roaming.
The following figure provides the network architecture of the SaMOG Gateway:

Qualified Platforms
The SaMOG Gateway is a StarOS™ application that runs on Cisco ASR 5x00 and virtualized platforms. For additional platform information, refer to the appropriate System Administration Guide and/or contact your Cisco account representative.
DPC2 on ASR 5500
The SaMOG Gateway is fully qualified to run on the second generation Data Processing Card (DPC2) on the ASR 5500.
The DPC2 offers increased performance versus the first generation DPC, while maintaining backwards compatibility with other ASR 5500 cards. The raw input/output has been increased from 80Gbps (DPC/UDPC) to 150Gbps (DPC2).
The DPC2 has three CPU subsystems. Each subsystem consists of two CPUs with 24 cores each (maximum 144 cores) that are paired with a Platform Controller Hub (PCH). Each CPU is associated with 32 GB of DDR4 memory (total of 192 GB per DPC2) and a latest generation crypto offload engine.
For more information on the DPC2 card, refer the System Administration Guide.
MIO Demux Card on ASR 5500
The SaMOG Gateway is fully qualified to run on the Management Input/Output (MIO) card for demux functions. SaMOG can leverage on the additional card for user plane processing to increase the capacity of the chassis.
For more information on the MIO Demux card, refer the System Administration Guide.
Licenses
The SaMOG Gateway is a licensed Cisco product. Two mutually exclusive SaMOG base licenses are available for operators with different network deployment models:
- SaMOG General License: This base license is available for operators with a pure 4G deployment model or a Mixed Mode (running both 3G and 4G) deployment model. Operators can configure subscribers to setup 3G or 4G sessions based on the serving PLMN and the subscription of the subscriber.
- SaMOG 3G License: This base license is available for operators with a pure 3G deployment model. Operators can setup 3G (GTPv1) sessions through the SaMOG Gateway. This license does not permit configuration of a Diameter-based authentication.
In addition to the base license for running SaMOG services, separate session and feature licenses may also be required. Contact your Cisco account representative for detailed information on specific licensing requirements. For information on installing and verifying licenses, see "Managing License Keys" in the System Administration Guide.














 Feedback
Feedback