Release Notes for Cisco 5700 Series Wireless LAN Controller, Cisco IOS XE Release 3.7.xE
Available Languages
Table of Contents
Release Notes for Cisco 5700 Series Wireless LAN Controller, Cisco IOS XE Release 3.7.xE
What’s New in Cisco IOS XE Release 3.7.5E
What’s New in Cisco IOS XE Release 3.7.4E
–B Domain Compliant Cisco APs in this Release
What’s New in Cisco IOS XE Release 3.7.3E
Configuring OPENAUTH and WEBAUTH in Parallel
WEBAUTH Command Output Examples
What’s New in Cisco IOS XE Release 3.7.2E
What’s New in Cisco IOS XE Release 3.7.1E
What’s New in Cisco IOS XE Release 3.7.0E
Cisco Wireless LAN Controller Models
Access Points and Mobility Services Engine
Wireless Web UI Software Requirements
Upgrading the Controller Software
Interoperability with Other Client Devices
Resolved Caveats in Cisco IOS XE Release 3.7.5E
Resolved Caveats in Cisco IOS XE Release 3.7.4E
Resolved Caveats in Cisco IOS XE Release 3.7.3E
Resolved Caveats in Cisco IOS XE Release 3.7.2E
Resolved Caveats in Cisco IOS XE Release 3.7.1E
Resolved Caveats in Cisco IOS XE Release 3.7.0E
Obtaining Documentation and Submitting a Service Request
Release Notes for Cisco 5700 Series Wireless LAN Controller, Cisco IOS XE Release 3.7.xE
This document gives an overview of the features for the Cisco IOS XE 3.7.xE software on the Cisco 5700 Series Wireless LAN Controller.
Introduction
The Cisco 5700 Series Wireless LAN Controller (Cisco 5700 Series WLC) is designed for 802.11ac performance with maximum services, scalability, and high resiliency for mission-critical wireless networks. With an enhanced software programmable ASIC, the controller delivers wire-speed performance with services such as Advanced QoS, Flexible NetFlow Version 9, and downloadable ACLs enabled in a wireless network. The controller works with other controllers and access points to provide network managers with a robust wireless LAN solution. The Cisco WLC 5700 provides:
- Network traffic visibility through Flexible NetFlow Version 9
- Radio frequency (RF) visibility and protection
- Support for features such as CleanAir, ClientLink 2.0, and VideoStream
The Cisco IOS XE software represents the continuing evolution of the preeminent Cisco IOS operating system. The Cisco IOS XE architecture and well-defined set of APIs extend the Cisco IOS software to improve portability across platforms and extensibility outside the Cisco IOS environment. The Cisco IOS XE software retains the same look and feel of the Cisco IOS software, while providing enhanced future-proofing and improved functionality.
For more information about the Cisco IOS XE software, see http://www.cisco.com/en/US/prod/collateral/iosswrel/ps9442/ps11192/ps11194/QA_C67-622903.html
Revision History
Added: CSCus83638
What’s New in Cisco IOS XE Release 3.7.5E
There are no features or enhancements in this release. For more information about updates in this release, see the “Caveats” section
What’s New in Cisco IOS XE Release 3.7.4E
Support for –B Domain
The FCC (USA) rule making on 5 GHz released on April 1, 2014 (FCC 14-30 Report and Order) goes into effect for products that are sold or shipped on or after June 2, 2016. Cisco APs and Cisco WLCs will comply with the new rules by supporting the new regulatory domain (–B) for the US and will create new AP SKUs that are certified under the new rules. Examples of new rules include new 5-GHz band channels permitted for outdoor use, and transmission (Tx) power level increased to 1W for indoor, outdoor, and point-to-point transmissions.

Note Cisco APs and Cisco WLCs that are in the –A domain category can continue to operate and even coexist with –B domain devices without any issues.
We recommend that you upgrade Cisco APs and Cisco WLCs to the appropriate software release that supports –B domain.
What’s New in Cisco IOS XE Release 3.7.3E
– Cisco Aironet 1850 Series Access Points
– Cisco Aironet 1830 Series Access Points
- Support for HTTP Request—You can customize the HTML pages to send credentials through an HTTP GET Request.

Note We recommend password encryption while using an HTTP GET Request.
- Different Attributes in Long URL—The webauth parameter map supports external URLs with a maximum length of 256 characters. While configuring a login URL for web authentication, ensure that complete length of the redirected URL does not exceed 550 characters. Use the following commands to configure external webauth parameter map with long URL:
- Multiple VLAN support for Wired Guest Access with both Anchor and Foreign as Cisco 5760 WLC—Wired guest anchor can now support multiple VLANs and multiple guest LANs. Separate VLANs can be assigned for each security profile like openauth, webauth and web consent. For more information about the Wired Guest Anchor feature, see “Multiple VLAN Support for Wired Guest Access with Cisco 5760 WLC as Both Anchor and Foreign Controller” section.
Multiple VLAN Support for Wired Guest Access with Cisco 5760 WLC as Both Anchor and Foreign Controller
Restrictions
- Wired guest VLAN on the access switch should not have any switch virtual interfaces (SVIs) present on any of the local switches. It should terminate directly on the foreign controller, so that the traffic is exported to the anchor.
- The anchor VLAN should not be allowed on the foreign controller’s uplink. Doing so may result in unexpected behavior.
- The foreign and anchor guest LANs should not be on the same VLAN.
- Wired guest configuration should only be performed during scheduled network downtime period.
Overview
In enterprise networks, there is typically a need for providing network access to a network’s guests on the campus. Guest access requirements include providing connectivity to the Internet or other selective enterprise resources to both wired and wireless guests in a consistent and manageable manner. The same wireless LAN controller can be used to provide access to both types of guests on the campus. For security reasons, a large number of enterprise network administrators segregate guest access to a demilitarized zone (DMZ) controller via tunneling. The guest access solution is also used as a fallback method for guest clients that fail dot1x and MAB authentication methods.
This document covers deployment of Wired Guest Access feature on Cisco 5760 WLC acting as Foreign Anchor and Cisco 5760 WLC acting as Guest Anchor in the DMZ. The feature works in a similar fashion on Cisco Catalyst 3650 switch acting as foreign controller.
A guest user connects to the designated wired port on an access layer switch for access. Optionally, it may be made to go through Web Consent or Web Authentication modes, depending upon the security requirements. After guest authentication succeeds, access is provided to the network resources and the guest controller manages the client traffic. Foreign controller is the primary switch where a client connects for network access; it also initiates tunnel requests. Guest anchor is the switch where a client gets anchored.
Before the guest access feature can be deployed, a mobility tunnel is established between the foreign anchor and guest anchor switches. The guest access feature works for both MC (Foreign Controller) to MC (Guest Anchor) and MA (Foreign Controller) to MC (Guest Anchor) models. The foreign anchor switch trunks wired guest traffic to the guest anchor controller. Multiple guest anchors can be configured for load balancing. The client is anchored to a DMZ anchor controller. It is also responsible for handling DHCP IP address assignment and authentication of a client. After the authentication is completed, the client is able to access the network.
Deployment Scenarios
The following sections describe common scenarios where the wired clients connect to access switches for network access. Two modes of access are explained with different examples. In both the methods, the wired guest access feature can act as a fallback method for authentication. This is typically a scenario where a guest user brings an end device that is unknown to the network. Since the end device is missing endpoint supplicant, it will fail the dot1x mode of authentication. Similarly, MAC authentication bypass (MAB) will also fail, as the MAC address of the end device is unknown to the authenticating server. It is worth noting that in such implementations, corporate end devices successfully get access to network as they would either have a dot1x supplicant or MAC addresses in the authenticating server for validation. This enables flexibility in deployment, because the administrator does not have to restrict and tie up ports specifically for guest access.
The figure below shows the topology used in this deployment scenario:
Figure 1-1 Wired Guest Access with Cisco 5760 WLC as Both Guest Anchor and Foreign Controller
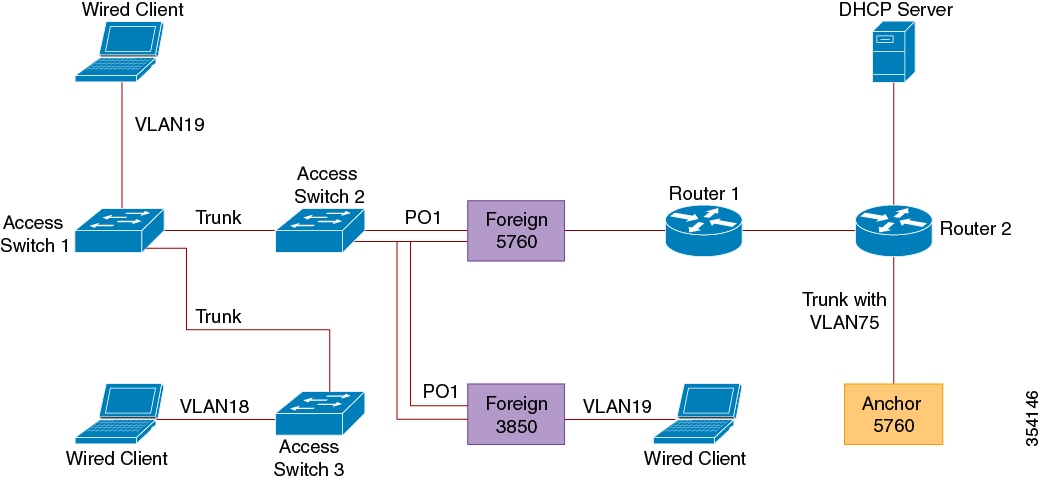
Open Authentication
Step 1 Enable IP Device Tracking (IPDT) and Dynamic Host Configuration Protocol (DHCP) snooping on client VLANs (VLAN75). The client VLAN should be created in the guest anchor:
Step 2 Create VLAN 75 and a L3 VLAN interface:
Step 3 Create a guest LAN specifying the client VLAN, with Cisco 5760 WLC acting as the mobility-anchor. (For openmode, use the no security web-auth command.)
Foreign Configuration
Step 1 Enable DHCP and create a VLAN. The client VLAN need not be on the foreign controller.
Step 2 The switch detects MAC address of the incoming client on the port channel configured with the access-session port-control auto command and applies the OPENAUTH subscriber policy. The OPENAUTH policy should be created first, as described below:

Note The policy can be applied on the port where the end device is connected while the 3850/3650 is acting as the Foreign.
Step 3 Configure MAC learning on the foreign controller for the VLAN:
Step 4 The OPENAUTH policy is referred to sequentially, which in this example points to a service template named SERV-TEMP3-OPENAUTH as defined below:
Step 5 The service template contains a reference to the tunnel type and name. The VLAN 75 client should exist only on the guest anchor because it is responsible for handling client traffic:
Step 6 A tunnel request is initiated from the foreign controller to the guest anchor for the wired client and a ‘tunneladdsuccess’ message is displayed to indicate that the tunnel build up process is completed.
On the access switch 1, a wired client connects to the Ethernet port that is set to access mode by the network administrator. It is portGigabitEthernet 1/0/11 in this example.
Guest Anchor Configuration
Step 1 Enable IPDT and DHCP snooping on a client VLAN, in this example VLAN75 is created on the guest anchor.
Step 2 Create VLAN 75 and the L3 VLAN interface:
Step 3 Configure the RADIUS server and the parameter map.
Step 4 Create a guest LAN specifying the client VLAN, with Cisco 5760 WLC acting as the mobility anchor:
Foreign Configuration
Step 1 Enable DHCP and create a VLAN. The client VLAN does not have to be set up on the foreign controller.
Step 2 The switch detects MAC address of the incoming client on the port channel configured with access-session port-control auto command and applies the WEBAUTH subscriber policy. The WEBAUTH policy should be created first, as described below:
Step 3 MAC learning should be configured on the foreign controller for the VLAN:
Step 4 The WEBAUTH policy is referred to sequentially, which in this example points to a service template named SERV-TEMP3-WEBAUTH, as defined below:
Step 5 The service template contains a reference to the tunnel type and name. The client VLAN75 should exist only on the guest anchor as it is responsible for handling client traffic:
Step 6 A tunnel request is initiated from the foreign controller to the guest anchor for the wired client. A ‘tunneladdsuccess’ message is displayed to indicate that the tunnel build-up process is completed.
On access switch 1, a wired client connects to the Ethernet port that is set to access mode by the network administrator. It is portGigabitEthernet 1/0/11 in this example.
Configuring OPENAUTH and WEBAUTH in Parallel
If you have two guest LANs and wants to assign them to different clients, base them on the VLANs on which the clients are learned.
Guest Anchor Configuration
Step 1 Enable IPDT and DHCP snooping on a client VLAN, in this case VLAN75. The client VLAN should be created on the guest anchor.
Step 2 Create VLAN 75 and the L3 VLAN interface:
Step 3 Create a guest LAN specifying the client VLAN, with Cisco 5760 WLC acting as the mobility anchor. (For openmode, use the no security web-auth command.)
Foreign Configuration
Step 1 Enable DHCP and create a VLAN. Note that the client VLAN need not have to be setup on the foreign controller.
Step 2 The switch detects MAC address of the incoming client on the port channel configured with access-session port-control auto command and applies the DOUBLEAUTH subscriber policy. The vlan18, vlan19 class maps are explained in “Step4”. Everything else is WEBAUTH. Using the second “always” class-map with “match-first” event, create the DOUBLEAUTH policy, as described below:
Step 3 Configure MAC learning on the foreign controller for VLAN 18 and VLAN 19.
Step 4 The ‘VLAN 18 and VLAN 19 class maps contain the VLAN match criteria based on which the guest LAN, under which the client falls in is differentiated.
Step 5 The OPENAUTH policy is referred to sequentially, which in this example points to a service template named SERV-TEMP3-OPENAUTH, as defined below:
Step 6 The service template contains a reference to the tunnel type and name. The VLAN 75 client should exist only on the guest anchor because it is responsible for handling client traffic:
Step 7 A tunnel request is initiated from the foreign controller to the guest anchor for the wired client. A ‘tunneladdsuccess’ message is displayed to indicate that the tunnel build-up process is complete.
On the access swicth, there are multiple wired clients connecting to either VLAN 18 or VLAN 19, which can be then be assigned guest LANs accordingly.
What’s New in Cisco IOS XE Release 3.7.2E
New parameter call-station-id added to the wireless security dot1x radius mac-authentication command. The call-station-id parameter configures Call Station ID type for MAC authentication.
There are no other features or enhancements in this release. For more information about updates in this release, see the “Caveats” section.
What’s New in Cisco IOS XE Release 3.7.1E
There are no other features or enhancements in this release. For more information about updates in this release, see the “Caveats” section.
What’s New in Cisco IOS XE Release 3.7.0E
- Wireless capability is added to Catalyst 4500E Series Switch Supervisor Engine 8-E .
- Support is added for the following access points:
– Cisco Aironet 1700 Series Access Point
– Cisco Aironet 1570 Series Access Point (supported only in Local mode)
- VLAN tagging is supported on Cisco Aironet 700W Series Access Points
- mDNS Service Discovery Gateway—The Service Discovery Gateway feature enables multicast Domain Name System (mDNS) to operate across Layer 3 (L3) boundaries. In this phase, features such as de-congestion of incoming mDNS traffic, redistribution of service withdrawal messages, a filter criterion for learning services available on a specific interface, and the periodic browsing of services on specific interfaces are introduced.
- AVC top ‘N’ users per application—This feature enables you to know network usage information on a per user basis within an application. This feature is enabled by default and is available if AVC is enabled.
- AN Infra—Autonomic networking makes network devices intelligent by introducing self-management concepts that simplify network management for the network operator.
- WebAuth sleeping client—Allows successfully authenticated devices to stay logged in for a configured period without reauthentication.
The following CLI is added under the webauth parameter map:
sleeping-client timeout timeout-in-minutes
– There is one-to-one mapping between device MAC and username/password. Once an entry is added to sleeping-client cache, the device/user gets policies for the user stored in the cache. Therefore, any other user using the device also gets the same policies as the user stored in the sleeping-client cache. The user can force normal authentication by logging out. To do that, the user must explicitly enter the following URL:
– Mobility is not supported. If the client roams from one controller to another, the client undergoes normal authentication on the foreign controller.
- Regulatory domains for India (–D), Indonesia (–F), Brazil (–Z), Honk Kong (–S) are supported.
- New Flexible NetFlow Collect parameters:
– collect wireless afd drop bytes —Collects the fields for wireless approximate fair drop (AFD) drop bytes
– collect wireless afd accept bytes —Collects the fields for AFD accept bytes
Controller# show platform qos wireless stats ssid { ssid-value | all } client all
This CLI lists client MAC address, WLAN ID, BSSID, accept byte, and drop byte details.
Supported Hardware
Catalyst 3850 Switch Models
Network Modules
Table 3 lists the three optional uplink network modules with 1-Gigabit and 10-Gigabit slots. You should only operate the switch with either a network module or a blank module installed.
Four 1-Gigabit small form-factor pleadable (SFP) module slots. Any combination of standard SFP modules are supported. SFP+ modules are not supported.
Catalyst 3650 Switch Models
Stackable 24 10/100/1000 Ethernet downlink ports, four 1-Gigabit SFP (small form-factor pluggable) uplink ports, 250-W power supply
Stackable 48 10/100/1000 Ethernet downlink ports, four 1-Gigabit SFP uplink ports, 250-W power supply
Stackable 24 10/100/1000 PoE+1 downlink ports, four 1-Gigabit SFP uplink ports, 640-W power supply
Stackable 48 10/100/1000 PoE+ downlink ports, four 1-Gigabit SFP uplink ports, 640-W power supply
Stackable 48 10/100/1000 Full PoE downlink ports, four 1-Gigabit SFP uplink ports, 1025-W power supply
Stackable 24 10/100/1000 Ethernet downlink ports, two 1-Gigabit SFP and two 10-Gigabit SFP+ uplink ports, 250-W power supply
Stackable 48 10/100/1000 Ethernet downlink ports, two 1-Gigabit SFP and two 10-Gigabit SFP+ uplink ports, 250-W power supply
Stackable 24 10/100/1000 PoE+ downlink ports, two 1-Gigabit SFP and two 10-Gigabit SFP+ uplink ports, 640-W power supply
Stackable 48 10/100/1000 PoE+ downlink ports, two 1-Gigabit SFP and two 10-Gigabit SFP+ uplink ports, 640-W power supply
Stackable 48 10/100/1000 Full PoE downlink ports, two 1-Gigabit SFP and two 10-Gigabit SFP+ uplink ports, 1025-W power supply
Stackable 48 10/100/1000 Full PoE downlink ports, four 10-Gigabit SFP+ uplink ports, 1025-W power supply
Stackable 48 10/100/1000 PoE+ downlink ports, four 10-Gigabit SFP+ uplink ports, 640-W power supply
Stackable 48 10/100/1000 Ethernet downlink ports, four 10-Gigabit SFP+ uplink ports, 250-W power supply
Stackable 24 10/100/1000 Ethernet downlink ports, four 1-Gigabit SFP uplink ports, 250-W power supply
Stackable 48 10/100/1000 Ethernet downlink ports, four 1-Gigabit SFP uplink ports, 250-W power supply
Stackable 24 10/100/1000 PoE+ downlink ports, four 1-Gigabit SFP uplink ports, 640-W power supply
Stackable 48 10/100/1000 PoE+ downlink ports, four 1-Gigabit SFP uplink ports, 640-W power supply
Stackable 48 10/100/1000 Full PoE downlink ports, four 1-Gigabit SFP uplink ports, 1025-W power supply
Stackable 24 10/100/1000 Ethernet downlink ports, two 1-Gigabit SFP and two 10-Gigabit SFP+ uplink ports, 250-W power supply
Stackable 48 10/100/1000 Ethernet downlink ports, two 1-Gigabit SFP and two 10-Gigabit SFP+ uplink ports, 250-W power supply
Stackable 24 10/100/1000 PoE+ downlink ports, two 1-Gigabit SFP and two 10-Gigabit SFP+ uplink ports, 640-W power supply
Stackable 48 10/100/1000 PoE+ downlink ports, two 1-Gigabit SFP and two 10-Gigabit SFP+ uplink ports, 640-W power supply
Stackable 48 10/100/1000 Full PoE downlink ports, two 1-Gigabit SFP and two 10-Gigabit SFP+ uplink ports, 1025-W power supply
Stackable 48 10/100/1000 Full PoE downlink ports, four 10-Gigabit SFP+ uplink ports, 1025-W power supply
Stackable 48 10/100/1000 PoE+ downlink ports, four 10-Gigabit SFP+ uplink ports, 640-W power supply
Stackable 48 10/100/1000 Ethernet downlink ports, four 10-Gigabit SFP+ uplink ports, 250-W power supply
Stackable 24 10/100/1000 Ethernet downlink ports, four 1-Gigabit SFP uplink ports, 250-W power supply
Stackable 48 10/100/1000 Ethernet downlink ports, four 1-Gigabit SFP uplink ports, 250-W power supply
Stackable 24 10/100/1000 PoE+ downlink ports, four 1-Gigabit SFP uplink ports, 640-W power supply
Stackable 48 10/100/1000 PoE+ downlink ports, four 1-Gigabit SFP uplink ports, 640-W power supply
Stackable 48 10/100/1000 Full PoE downlink ports, four 1-Gigabit SFP uplink ports, 1025-W power supply
Stackable 24 10/100/1000 Ethernet downlink ports, two 1-Gigabit SFP and two 10-Gigabit SFP+ uplink ports, 250-W power supply
Stackable 48 10/100/1000 Ethernet downlink ports, two 1-Gigabit SFP and two 10-Gigabit SFP+ uplink ports, 250-W power supply
Stackable 24 10/100/1000 PoE+ downlink ports, two 1-Gigabit SFP and two 10-Gigabit SFP+ uplink ports, 640-W power supply
Stackable 48 10/100/1000 PoE+ downlink ports, two 1-Gigabit SFP and two 10-Gigabit SFP+ uplink ports, 640-W power supply
Stackable 48 10/100/1000 Full PoE downlink ports, two 1-Gigabit SFP and two 10-Gigabit SFP+ uplink ports, 1025-W power supply
Stackable 48 10/100/1000 Full PoE downlink ports, four 10-Gigabit SFP+ uplink ports, 1025-W power supply
Stackable 48 10/100/1000 PoE+ downlink ports, four 10-Gigabit SFP+ uplink ports, 640-W power supply
Stackable 48 10/100/1000 Ethernet downlink ports, four 10-Gigabit SFP+ uplink ports, 250-W power supply
Optics Modules
Catalyst switches support a wide range of optics. Because the list of supported optics is updated on a regular basis, consult the tables at this URL for the latest (SFP) compatibility information:
http://www.cisco.com/en/US/products/hw/modules/ps5455/products_device_support_tables_list.html
Cisco Wireless LAN Controller Models
Access Points and Mobility Services Engine
Table 6 lists the supported products of the Cisco 5700 Series WLC.

Note On platforms that run Cisco IOS XE releases, the WSSI/3G modules on access points are not supported.
Table 7 lists the specific supported Cisco access points.
Compatibility Matrix
Table 8 lists the software compatibility matrix.
For more information on the compatibility of wireless software components across releases, see the Cisco Wireless Solutions Software Compatibility Matrix .
Software Version
Table 9 shows the mapping of the Cisco IOS XE version number and the Cisco IOS version number.
Upgrading the Controller Software
To upgrade the Cisco IOS XE software, use the software install privileged EXEC command to install the packages from a new software bundle file. You can install the software bundle from the local storage media or it can be installed over the network using TFTP or FTP.
The software instal l command expands the package files from the specified source bundle file and copies them to the local flash: storage device. When the source bundle is specified as a tftp: or ftp: URL, the bundle file is first downloaded into the switch's memory (RAM); the bundle file is not copied to local storage media.
After the package files are expanded and copied to flash: the running provisioning file (flash:packages.conf) is updated to reflect the newly installed packages, and the controller displays a reload prompt.
[1]: Downloading file tftp://10.10.10.2/system1/ct5760-ipservicesk9.SPA.03.03.00.SE.150-1.EZ.bin to active switch 1[1]: Finished downloading file tftp://172.19.26.230/kart/ct5760-ipservicesk9.SPA.03.03.00.SE.150-1.EZ.bin to active switch 1
Important Upgrade Note
After you upgrade to Cisco IOS XE Release 3.7E, the WebAuth success page behavior is different from the behavior seen in Cisco IOS XE Release 3.3.X SE. After a successful authentication on the WebAuth login page, the original requested URL opens in a pop-up window and not on the parent page. Therefore, we recommend that you upgrade the Web Authentication bundle so that the bundle is in the format that is used by the AireOS Wireless LAN Controllers.
To download a sample Web Authentication bundle, follow these steps:
Step 1 Browse to http://software.cisco.com/download/navigator.html .
Step 2 Navigate to Products > Wireless > Wireless LAN Controller > Standalone Controller > Cisco 5700 Series Wireless LAN Controllers > Cisco 5760 Wireless LAN Controller.
Step 3 Click Wireless Lan Controller Web Authentication Bundle .
Step 4 Choose Release 3.7.0 and click Download .
Step 5 After the download, follow the instructions provided in the Read Me file that is attached in the bundle.

Note In a High Availability scenario, if you download the Web Authentication bundle to the active controller, the bundle cannot be synchronized with the standby controller. Therefore, we recommend that you also manually download the Web Authentication bundle to the standby controller.
Features
The Cisco 5700 Series WLC is the first Cisco IOS-based controller built with smart ASIC for next generation unified wireless architectures. The Cisco 5700 Series WLC can be deployed both as a Mobility Controller (MC) in Converged Access solutions and as a Centralized Controller.
For more information about the features, see the product data sheet at this URL:
http://www.cisco.com/c/en/us/products/wireless/5700-series-wireless-lan-controllers/datasheet-listing.html
Interoperability with Other Client Devices
This section describes the interoperability of this version of the controller software release with other client devices.
Table 11 lists the client types on which the tests were conducted. The clients included laptops, handheld devices, phones, and printers.
Important Notes
- With Cisco Prime Infrastructure 2.1.1, the refresh config and inventory collection tasks from the controller might take anywhere from 20 minutes to 40 minutes. For more information, see CSCum62747 on the Bug Search Tool.
- Although visible in the CLI, the following commands are not supported:
– authorize-lsc-ap (CSCui93659)
– Mesh, FlexConnect, and OfficeExtend access point deployment
Limitations and Restrictions
- Flex Links are not supported. We recommend that you use spanning tree protocol (STP) as the alternative.
- Outdoor access points are supported only when they are in Local mode.
- Restrictions for Cisco TrustSec:
– Cisco TrustSec can be configured only on physical interfaces, not on logical interfaces.
– Cisco TrustSec for IPv6 is not supported.
– Dynamic binding of IP-SGT is not supported for hosts on Layer 3 physical routed interfaces because the IP Device Tracking feature for Layer 3 physical interfaces is not supported.
– Cisco TrustSec cannot be configured on a pure bridging domain with IPSG feature enabled. You must either enable IP routing or disable the IPSG feature in the bridging domain.
– Cisco TrustSec on the controller supports up to 255 security group destination tags for enforcing security group ACLs.
– Cisco TrustSec VLAN-to-SGT binding cannot be enabled in pure bridging domain. You have to either manually enable IP device tracking on the ports in the VLAN, or enable SVI interface for the VLAN.
– For Cisco IOS Release 3.7E and later, Cisco TrustSec VLAN-to-SGT binding cannot be enabled in pure bridging domain. You have to either manually enable IP device tracking on the ports in the VLAN, or enable SVI interface for the VLAN.
Caveats
- Cisco Bug Search Tool
- Open Caveats
- Resolved Caveats in Cisco IOS XE Release 3.7.5E
- Resolved Caveats in Cisco IOS XE Release 3.7.4E
- Resolved Caveats in Cisco IOS XE Release 3.7.3E
- Resolved Caveats in Cisco IOS XE Release 3.7.2E
- Resolved Caveats in Cisco IOS XE Release 3.7.1E
- Resolved Caveats in Cisco IOS XE Release 3.7.0E
Cisco Bug Search Tool
Caveats describe unexpected behavior in a product. The Open Caveats section lists open caveats that apply to the current release and may apply to previous releases. A caveat that is open for a prior release and is still unresolved applies to all future releases until it is resolved.
To view the details of the software bugs pertaining to your product, perform the following task:
Click the Caveat ID/Bug ID number in the table.
The corresponding Bug Search Tool page is displayed with details of the Caveat ID/Bug ID.
The Bug Search Tool (BST), which is the online successor to the Bug Toolkit, is designed to improve the effectiveness in network risk management and device troubleshooting. The BST allows partners and customers to search for software bugs based on product, release, and keyword, and aggregates key data, such as bug details, product, and version. The tool has a provision to filter bugs based on credentials to provide external and internal bug views for the search input.
To view the details of a caveat whose ID you do not have, perform the following procedure:
1. http://www.cisco.com/c/dam/en/us/td/i/templates/blank.gif Access the BST using your Cisco user ID and password at: https://tools.cisco.com/bugsearch/ .
2. In the Bug Search window that is displayed, enter the necessary information in the corresponding fields.
For more information about how to use the Cisco Bug Search Tool effectively, including how to set email alerts for bugs and to save bugs and searches, see the Bug Search Tool Help & FAQ page.
Resolved Caveats in Cisco IOS XE Release 3.7.5E
Use the BST to view the details of a caveat listed in this section. For more information about the Cisco BST, see the “Cisco Bug Search Tool” section
Resolved Caveats in Cisco IOS XE Release 3.7.4E
Use the BST to view the details of a caveat listed in this section. For more information about the Cisco BST, see the “Cisco Bug Search Tool” section
Resolved Caveats in Cisco IOS XE Release 3.7.3E
Use the BST to view the details of a caveat listed in this section. For more information about the Cisco BST, see the “Cisco Bug Search Tool” section.
Resolved Caveats in Cisco IOS XE Release 3.7.2E
Use the BST to view the details of a caveat listed in this section. For more information about the Cisco BST, see the “Cisco Bug Search Tool” section.
Resolved Caveats in Cisco IOS XE Release 3.7.1E
Use the BST to view the details of a caveat listed in this section. For more information about the Cisco BST, see the “Cisco Bug Search Tool” section.
Resolved Caveats in Cisco IOS XE Release 3.7.0E
Use the BST to view the details of a caveat listed in this section. For more information about the BST, see the “Cisco Bug Search Tool” section.
Troubleshooting
For the most up-to-date, detailed troubleshooting information, see the Cisco TAC website at this URL:
http://www.cisco.com/en/US/support/index.html
Choose Product Support > Wireless. Then choose your product and click Troubleshoot and Alerts to find information for the problem that you are experiencing.
Related Documentation
http://www.cisco.com/c/en/us/support/ios-nx-os-software/ios-xe-3e/tsd-products-support-series-home.html
http://www.cisco.com/en/US/products/ps12598/tsd_products_support_series_home.html
http://www.cisco.com/go/designzone
https://www.cisco.com/cgi-bin/Support/Errordecoder/index.cgi
Obtaining Documentation and Submitting a Service Request
For information on obtaining documentation, submitting a service request, and gathering additional information, see the monthly What’s New in Cisco Product Documentation , which also lists all new and revised Cisco technical documentation, at:
http://www.cisco.com/c/en/us/td/docs/general/whatsnew/whatsnew.html
Subscribe to the What’s New in Cisco Product Documentation , which lists all new and revised Cisco Technical documentation, as an RSS feed and deliver content directly to your desktop using a read application. The RSS feeds are a free service.
Cisco and the Cisco logo are trademarks or registered trademarks of Cisco and/or its affiliates in the U.S. and other countries. To view a list of Cisco trademarks, go to this URL: www.cisco.com/go/trademarks . Third-party trademarks mentioned are the property of their respective owners. The use of the word partner does not imply a partnership relationship between Cisco and any other company. (1110R)
Any Internet Protocol (IP) addresses and phone numbers used in this document are not intended to be actual addresses and phone numbers. Any examples, command display output, network topology diagrams, and other figures included in the document are shown for illustrative purposes only. Any use of actual IP addresses or phone numbers in illustrative content is unintentional and coincidental.
Contact Cisco
- Open a Support Case

- (Requires a Cisco Service Contract)
 Feedback
Feedback