Information About FlexConnect Groups
To organize and manage your FlexConnect access points, you can create FlexConnect Groups and assign specific access points to them.
All of the FlexConnect APs in a group can share the same backup RADIUS server, fast secure roaming, local authentication configuration, and WLAN-VLAN mapping information. We recommend this feature if you have multiple FlexConnect APs in a remote office or on the floor of a building and you want to configure them all at once. For example, you can configure a backup RADIUS server for a FlexConnect group rather than having to configure the same server on each AP. A maximum of 100 APs is supported per FlexConnect group (other than the default FlexConnect group, which is limited only by the maximum APs supported by the controller).
FlexConnect Groups and VLAN Support
You can configure VLAN Support and VLAN ID on a per FlexConnect group basis. This allows all APs in a FlexConnect group to inherit the VLAN configuration from the FlexConnect group including VLAN support, Native VLAN, and WLAN-VLAN mappings.
Deployment Considerations
-
When the override flag is set at the FlexConnect Group, modification of VLAN Support, Native VLAN ID, WLAN-VLAN mappings, and Inheritance-Level at the AP is not allowed.
-
An Inheritance-Level configuration is available at the FlexConnect AP. You have to set this to “Make VLAN AP Specific” to configure any AP-Specific VLAN Support, Native VLAN ID and VLAN-WLAN mappings on the AP. Note that you can modify this only when the override flag at the group is disabled.
To achieve this on the controller GUI, choose , click on the AP name. In the FlexConnect tab, select Make VLAN AP Specific from the drop-down list.
IP-MAC Context Distribution for FlexConnect Local Switching Clients
Using this feature, you can prevent IP theft and ARP spoofing within the same FlexConnect group. The controller distributes the client IP:MAC context to all the APs in the same FlexConnect group. When the client roams to a new AP in the same FlexConnect group, the AP uses the IP:MAC context to validate the client data.
The Client IP-MAC context consists of the following parameter values:
-
Source AP MAC Address to which a client is associated with
-
Client’s MAC Address
-
Client’s IPv4 Address
-
Client’s IPv6 address count
-
List of IPv6 addresses based on count
This section contains the following subsections:
Guidelines and Restrictions for IP-MAC Context Distribution for FlexConnect Local Switching Clients
-
A maximum of 2000 client IP-MAC entries are supported in an AP.
-
IP-MAC entries are deleted when the AP is rebooted.
-
Clients behind NAT/PAT-enabled WLANs cannot use this IP:MAC binding as the controller reports and de-authenticates clients with duplicated IP address.
-
AP evaluates IP-MAC context only for clients with IPv4 addresses, although distribution is done for both IPv4 and IPv6 addresses.
-
This feature is not applicable to the default Flex Group.
-
This feature does not support centrally switched clients as IP-Source guard is done at the controller data path.
Configuring IP-MAC Context Distribution For FlexConnect Local Switching Clients (GUI)
Procedure
|
Step 1 |
Choose to open the WLANs page. |
|
Step 2 |
Click the WLAN id you want to configure. |
|
Step 3 |
Click the Advanced tab |
|
Step 4 |
Under the DHCP section, check the DHCP Addr. Assignment check box. |
|
Step 5 |
Under the FlexConnect section, check the FlexConnect Local Switching check box. |
|
Step 6 |
Save the configuration. |
Configuring IP-MAC Context Distribution For FlexConnect Local Switching Clients (CLI)
Procedure
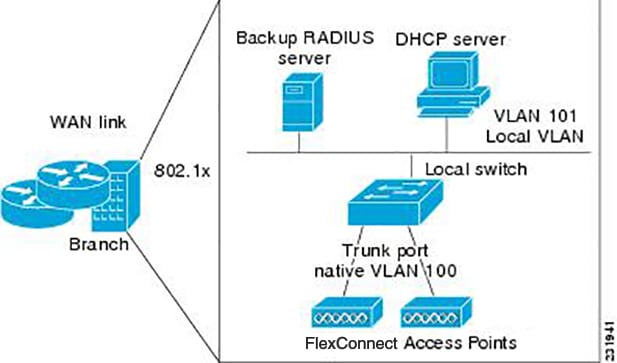
FlexConnect Groups and Backup RADIUS Servers
You can configure the controller to allow a FlexConnect access point in standalone mode to perform full 802.1X authentication to a backup RADIUS server. You can configure a primary backup RADIUS server or both a primary and secondary backup RADIUS server. These servers can be used when the FlexConnect access point is in of these two modes: standalone or connected.
FlexConnect Groups and Fast Secure Roaming
Fast secure roaming among FlexConnect APs is supported only if the APs are in non-default FlexConnect groups. For OKC, fast roaming is supported between APs in different FlexConnect groups (because key caching is handled by the controller). For 802.11r and CCKM, fast roaming is supported only among APs in the same FlexConnect group. Sticky key caching is not supported with FlexConnect APs.
 Note |
Fast roaming among FlexConnect and non-FlexConnect APs is not supported. |
 Note |
FlexConnect Groups is needed for fast roaming to work. Flex group needs to be created for fast roaming, 11r, and OKC , only then the caching can happen on an AP. The group name must be same between APs for a fast roaming to happen for 11r/fast roaming. The group can be different for OKC as final check is done at the controller. |
FlexConnect Groups and Local Authentication Server
You can configure the controller to allow a Cisco Wave 1 (IOS-based) FlexConnect AP in standalone mode to perform LEAP, EAP-FAST, PEAP, or EAP-TLS authentication for up to 100 statically configured users. The controller sends the static list of usernames and passwords to each FlexConnect access point when it joins the controller. Each access point in the group authenticates only its own associated clients.
 Note |
This feature is not supported on Wave 2 and 802.11ax APs. |
 Note |
If you want to enable FlexConnect local authentication, you have to enable FlexConnect AP Local Authentication in the Local Authentication tab. If the FlexConnect APs act as an 802.11X authenticator (RADIUS client), then configure the RADIUS servers in the General tab. |
This feature is ideal for customers who are migrating from an autonomous access point network to a lightweight FlexConnect access point network and are not interested in maintaining a large user database or adding another hardware device to replace the RADIUS server functionality available in the autonomous access point.
 Note |
|
You have to provision a certificate to the AP because the AP has to send the certificate to the client. You must download the Vendor Device Certificate and the Vendor Certification Authority Certificate to the controller. The controller then pushes these certificates to the AP. If you do not configure a Vendor Device Certificate and the Vendor CA Certificate on the controller, the APs associating with the FlexConnect group download the self-signed certificate of the controller, which may not be recognized by many wireless clients.
With EAP-TLS, AP does not recognize and accept client certificate if the client root CA is different from the AP root CA. When you use Enterprise public key infrastructures (PKI), you must download a Vendor Device Certificate and Vendor CA Certificate to the controller so that the controller can push the certificates to the AP in the FlexConnect group. Without a common client and AP root CA, EAP-TLS fails on the local AP. The AP cannot check an external CA and relies on its own CA chain for client certificate validation.
The space on the AP for the local certificate and the CA certificate is around 7 Kb, which means that only short chains are adapted. Longer chains or multiple chains are not supported.
 Note |
This feature can be used with the FlexConnect backup RADIUS server feature. If a FlexConnect is configured with both a backup RADIUS server and local authentication, the FlexConnect access point always attempts to authenticate clients using the primary backup RADIUS server first, followed by the secondary backup RADIUS server (if the primary is not reachable), and finally the FlexConnect access point itself (if the primary and secondary are not reachable). |
For information about the number of FlexConnect groups and access point support for a controller model, see the data sheet of the respective controller model.
Default FlexGroup
Default FlexGroup is a container where FlexConnect access points (APs), which are not a part of an administrator-configured FlexConnect group, are added automatically when they join the Cisco Wireless Controller. The Default FlexGroup is created and stored when the controller comes up (after upgrading from an earlier release. Note that a reload of the 8.3 will not create the group again. It will only restore the existing Default FlexGroup configuration.) This group cannot be deleted or added manually. Also, you cannot manually add or delete APs to the Default FlexGroup. The APs in the Default FlexGroup inherit the common configuration of the group. Any change in the group configuration is propagated to all the APs in the group.
When a group created by an admin is deleted, all the APs from that group are moved to the Default FlexGroup and inherit the configuration of this group. Similarly, APs that are removed manually from other groups are also added to the Default FlexGroup.
When an AP from the Default FlexGroup is added to a customized group, the existing configuration (from the Default FlexGroup) is deleted and the configuration from the customized group is pushed to the AP. If there is a standby controller, the Default FlexGroup and its configuration are also synchronized to it.
The AP provides FlexConnect group name during the join process. The AP could have received this group name either through cloud provisioning or through controller configuration. There are various scenarios involved in deciding the final FlexConnect group, when an AP joins and they are listed in the table below:
|
FlexConnect Group Received from AP |
Status in Controller |
Final Group Information/Configuration Setn to AP |
Type of Entry (Based on Priority) |
|---|---|---|---|
|
Group1 |
Group1 not present; AP entry not present in any group |
Default FlexGroup |
Admin |
|
Group1 |
Group1 present but maximum entries reached; AP entry not present in any group |
Default FlexGroup |
Admin |
|
Group1 |
Group1 present, but AP entry not present in any group |
Group1 |
Cloud |
|
Group1 |
Group1 present, but AP entry present as part of a different group, Group2 (added by admin) |
Group2 |
Admin |
|
Group1 |
Group1 present, but AP entry exists in a different group, Group2 learnt earlier through cloud |
Group1 |
Cloud |
|
No Group/Default Group |
AP entry exists as part of Group2 (either through admin configuration or learnt via cloud) |
Group2 |
Admin/Cloud |
Whenever the final type of entry is cloud, the AP entry gets added to the corresponding FlexConnect group. Also, when the FlexConnect group received from AP is different from the resultant group, a trap is raised to inform the admin about the conflict. The show flexconnect group detail group-name aps command displays the conflict value.
The following features are not supported in default Flex Group:
-
Efficient image upgrade
-
PMK cache distribution
-
Fast Roaming
The following features are supported in default Flex Group:
-
VLAN support (native VLAN, WLAN-VLAN mapping)
-
VLAN ACL mapping
-
WebAuth, web policy, local split mapping
-
Local authentication users
-
RADIUS authentication
-
Central DHCP or NAT-PAT
-
Flex AVC
-
VLAN name ID mapping
-
Multicast override
Restrictions
-
You cannot use the following CLIs to add or delete a Defaut FlexGroup or AP to a group:
-
config flexconnect group default-flexgroup{ add | delete}
-
config flexconnect group default-flexgroup ap{ add | delete}
-
-
The Defaut FlexGroup does not have a default configuration.
-
When you delete an AP from the customized flex group, the VLAN support is also deleted from that AP.

 Feedback
Feedback