APN and APN Profile-Based User Plane Selection
Revision History
 Note |
Revision history details are not provided for features introduced before release 21.24. |
|
Revision Details |
Release |
|---|---|
|
First introduced. |
Pre 21.24 |
Feature Description
In the CUPS architecture, SAEGW-C selects a user plane by using an algorithm that selects the least connected user plane. It also selects the user plane from a flat list of user planes.
This feature enables the operator to select a user plane from a specific UP group associated with an APN or APN Profile.
In S-GW, UP groups are associated with an Access Point Name (APN) profile. An APN profile groups a set of APN-specific parameters that are applicable to one or more APNs. A single APN profile can be associated with multiple operator policies.
How It Works
Cisco CUPS solution supports static UP selection. This is based on static selection of active and available SAEGW-U. The static UP selection uses the UP Group concept. UP group is a group of UP SAEGW-Us. Each APN is then associated with one UP group. APN is served by the UP groups associated with it. UPs are selected using an algorithm that selects the least connected UP available in that particular group.
UP Group
A UP can be part of only one UP group. In a UP Group, all UPs must be of the same capacity and capability. Different type of UPs must be part of different UP groups.
CUPS supports the following types of UP groups:
-
Specific UP Group—It is a set of explicitly configured UPs. The specific group gives the flexibility to group certain specific types of UPs together. This helps in reserving specific set of UPs for a specific purpose. There can be multiple specific groups that can be configured.
-
Default UP Group—This is a default group that groups all UPs that are registered and are not explicitly configured as part of any specific UP group. The default group has advantage of registering UPs in a zero touch manner without configuring a UP on the CP explicitly. This type of group is suited for collocated CUPS cases where all UPs with the same capacity and capability are in the same data center. The default group optimizes the UP configuration on CP.
An APN can be associated with UP group. If no group is associated with an APN, then default UP group is used to serve that APN. Similarly, for selecting UP for Pure-S calls, UP group can be associated to an APN profile. If there is no APN Profile/Operator-Policy defined or no group is associated with APN Profile, then SAEGW-C uses the "default" UP group for selection.
An operator can reserve certain UPs for certain applications. For example, IMS, Internet, and IOT can have different UP groups.
With this feature:
-
SAEGW-C always has one user plane group with the name "default".
-
SAEGW-C supports a maximum number of 100 user planes.
-
The user planes can be organized in different groups.
-
Currently, 100 user-plane-groups can be configured, and a single group can have a maximum number of 100 user planes.
-
One user plane can be part of only one user plane group.
-
Multiple user planes can be configured in specific user-plane-groups and default group.
-
The user planes associated with SAEGW-C but not defined in any user plane group are added in the default group.
-
An operator can associate a User Plane Group to APN and APN Profile.
-
If there is no User Plane group associated to an APN for Pure-P and Collapsed calls, SAEGW-C uses the default group to select user plane for that session.
-
If there is no user plane group associated to APN Profile or no APN Profile is defined, then SAEGW-C uses the "default" user plane group for Pure-S calls.
-
For multi-PDN call with same APN, the same user plane is selected. For multi-PDN call with different APN, a different user plane from a different user plane group is selected.
-
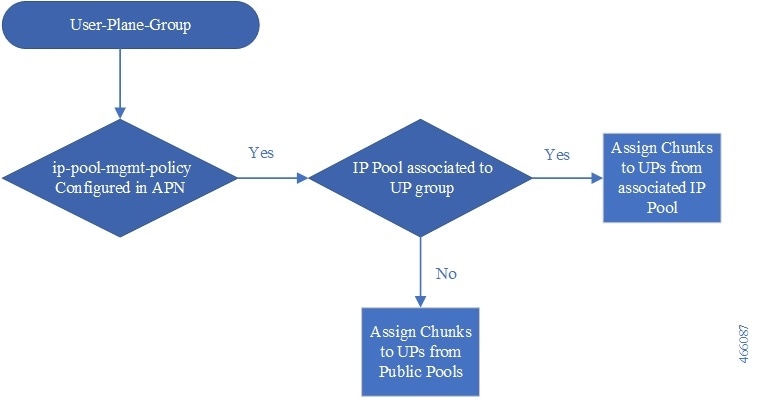
User Plane group associated with APN is also used while sending IP Pool chunks to User Plane. IP Pool associated with APN is broken down to chunks and are available for distribution to all UPs from group associated with APN.
-
For user-plane-groups that are not associated with any APN, SAEGW-C does not send any IP pool chunks to UPs belonging to these groups. This is also applicable to the default group.
-
Sessions with static IP address (IPv4 or IPv6) are supported. The user plane selection of static session is fixed as per chunk allocation to user plane from user plane group associated to an APN.
-
If the same static IP address range is used across multiple APNs, it is recommended to use the same user plane group in those APNs.
Architecture
The following figure depicts a high-level architecture of this feature.

Session Recovery and ICSR
Sx-Demux Recovery, ICSR and Sessmgr and VPNmgr recovery is supported
Limitations
In CUPS architecture, this feature has the following known limitations:
-
SAEGW-C does not support IPv4v6 PDN type call with static address received from UE, even if one of the IP address (either IPv4 or IPv6, or both) is static address.
-
SAEGW-C does not support “allow-static” type pool configuration.
-
Multi-PDN call with static IP address allocation is not supported.
Licensing
This feature is license-controlled. Contact your Cisco Account representative for license related details.
Configuring APN-Based UP Grouping
This section provides information about configurations available in support of this feature.
Prerequisites:
-
Same IP context should be present at Control-Plane as well as in User-Plane.
-
IP context name which is specified in APN configuration should be same at Control-Plane and User-Plane.
Configuring User Plane Group in Control Plane
New user-plane-group is defined at the global configuration mode which lists User Plane endpoints
-
User Plane Group name “default” is created by default. Operator can add and remove peer-node-id in default group. Operator cannot delete user-plane-group “default
-
If Sx Association Setup Request is received for any User plane node-id which is not part of any defined User Plane Group, it will be part of Default User Plane Group.
Configuring User Plane Group
Use the following CLI commands to configure User Plane endpoint group in Control Plane.
configure
[ no ] user-plane-groupgroup_name
end Notes:
-
Removal of user-plane-group will trigger Sx-Association release from Control Plane of individual peer id from that group.
Configuring Peer Node ID and User Plane Node IP Address
Use the following configuration commands to configure time-based PCC rule.
configure
user-plane-group group_name
[ no ] peer-node-id { ipv4-address | ipv6-address }
end Notes:
-
Removal of peer-node-id will trigger Sx-Association Release from Control Plane for that peer id.
Verifying the User Plane Group
Use the following CLI command for verification.
show user-plane-group { all | name group_name } Associating User Plane Group with APN
It is desired that calls to a particular APN be connected to a certain group of user-planes based on some predefined selection criteria. Operator can associate User Plane Group to APN Configuration.
User Plane group configured to APN is also used while sending IP Pool chunks to User Plane. If there is IP Pool associated with APN, only then the chunks from that pool will be sent to all User Planes in this group.
User Plane Group configuration in APN is used to select User Plane for P-GW Pure-P and Collapsed Call.
If there is no specific group is configured in APN then “default” group will be used.
Configuring User Plane Group in APN
Use the following CLI commands to configure User Plane group in APN.
configure
context context_name
apn apn_name
[ no ] user-plane-group group_name
end NOTE: In this EFT release, removal or change of user-plane-group from APN is not supported.
Verifying the User Plane Group in APN
Use the following CLI command for verification.
show apn name apn_name } Associating User Plane Group with APN Profile
To select User Plane for S-GW Pure-S calls, SAEGW-C uses user-plane-group associated with APN Profile under Operator Policy. When APN profile do not have any user-plane-group associated or no APN profile was used, then SAEGW-C will select User Plane from default user-plane-group.
Configuring User Plane Group in APN Profile
Use the following CLI commands to configure User Plane group in APN.
configure
apn-profile profile_name
[ no ] user-plane-group group_name
end Method of Procedure (MOP) to Remove or Change User Plane Group from APN
When explicit user-plane-group is configured, or implicit default group is used, the SAEGW-C sends IP Pool chunks from the pool that is configured (or global pool when there is no explicit pool configuration in APN) to the user planes in the group.
If you want to change or remove user-plane-group associated to a APN, then it is recommended to follow this MOP because, currently, there is no support of run time config change of user-plane-group in APN after User Plane is associated with SAEGW-C.
Before changing user-plane-group in APN it is recommended to use the following CLI command to first gracefully clear all existing calls belonging to user-plane-group associated with APN.
clear subscribers saegw-only user-plane-group group_name no-select-up
Executing this CLI command releases all sessions from User Plane belonging to the mentioned user-plane-group gracefully, and marks that User Plane as "Not Available for Session Selection". This User Plane continues to be in Associated state, but it will not be available for Session selection.
 Note |
When the clear subscribers command is executed on UP, CP will not be informed and CP will consider the sessions as running. |
After clearing the session, execute either of the following CLI command on User Plane to remove its association from Control Plane, and make required changes after UP association is released.
no user-plane-service service_name
Or:
no peer-node-id { ipv4-address ipv4_address | ipv6-address ipv6_address}
Monitoring and Troubleshooting APN-Based UP Grouping
This feature supports the following CLI commands:
-
show sx peers
-
Group Name Column in the output of this command displays the name of the user-plane-group under which the peer is configured at Control Plane.
-
Peer, which is not part of any group, will be added under "default" user-plane-group
-
For a user-plane-group that is not associated with any "apn", SAEGW-C will not send any IP pools to user planes from this group. Hence, in the output of this command, for the Group Name that is not associated with "apn", the IP Pool status will be "N – Not Applicable". Also, for user planes in this group, when show sx peers is executed on UP, it displays Peer ID as "0".
-
-
show ip user-plane
-
show ip pool-chunks up-id up_id user-plane-group name up_group_name







 Feedback
Feedback