Feature Information for SRTP-RTP Interworking
The following table provides release information about the feature or features described in this module. This table lists only the software release that introduced support for a given feature in a given software release train. Unless noted otherwise, subsequent releases of that software release train also support that feature.
Use Cisco Feature Navigator to find information about platform support and Cisco software image support. To access Cisco Feature Navigator, go to https://cfnng.cisco.com/. An account on Cisco.com is not required.|
Feature Name |
Releases |
Feature Information |
|---|---|---|
|
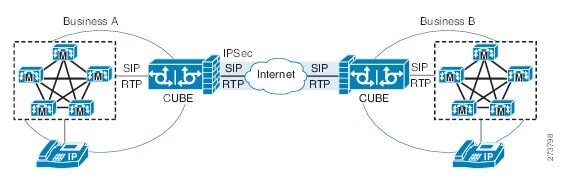
Cisco Unified Border Element Support for SRTP-RTP Interworking |
12.4(22)YB , 15.0(1)M Cisco IOS XE 3.1S |
This feature allows secure to non-secure enterprise calls. Support for SRTP-RTP interworking between one or multiple Cisco Unified Border Elements is enabled for SIP-SIP audio calls. |
|
Supplementary Services Support on CUBE for SRTP-RTP Calls |
Cisco IOS 15.2(1)T Cisco IOS XE 3.7S |
The SRTP-RTP Interworking feature was enhanced to support supplementary services for SRTP-RTP calls. |
|
Support for AEAD_AES_GCM_256 and AEAD_AES_GCM_128 crypto-suites |
Cisco IOS XE Everest 16.5.1b |
AEAD_AES_GCM_256 and AEAD_AES_GCM_128 crypto suites were added to support SRTP-RTP interworking. |




 Feedback
Feedback