Information About Cisco Unified Border Element
Cisco Unified Border Element (CUBE) can terminate and originate signaling (H.323 and Session Initiation Protocol [SIP]) and media streams (Real-Time Transport Protocol [RTP] and RTP Control Protocol [RTCP]).
CUBE extends the functionality provided by conventional session border controllers (SBCs) in terms of protocol interworking, especially on the enterprise side. As shown in the chart below, the CUBE provides the following additional features:
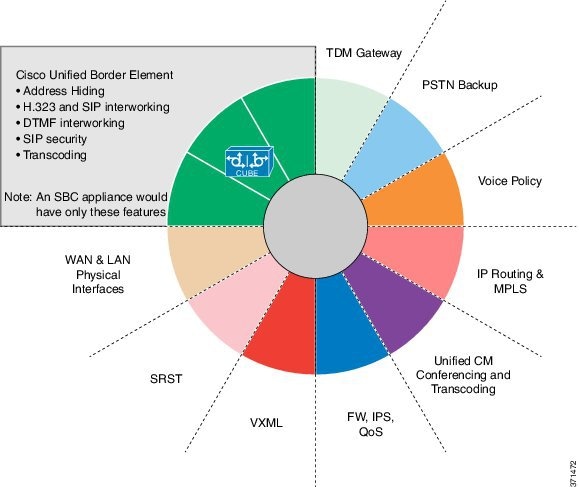
The CUBE provides a network-to-network interface point for:
-
Signaling interworking—H.323 and SIP.
-
Media interworking—dual-tone multifrequency (DTMF), fax, modem, and codec transcoding.
-
Address and port translations—privacy and topology hiding.
-
Billing and call detail record (CDR) normalization.
-
Quality-of-service (QoS) and bandwidth management—QoS marking using differentiated services code point (DSCP) or type of service (ToS), bandwidth enforcement using Resource Reservation Protocol (RSVP), and codec filtering.
CUBE functionality is implemented on devices using a special IOS feature set, which allows CUBE to route a call from one VoIP dial peer to another.
Protocol interworking is possible for the following combinations:
-
H.323-to-SIP interworking
-
H.323-to-H.323 interworking
-
SIP-to-SIP interworking
The CUBE provides a network-to-network demarcation interface for signaling interworking, media interworking, address and port translations, billing, security, quality of service, call admission control, and bandwidth management.
The CUBE is used by enterprise and small and medium-sized organizations to interconnect SIP PSTN access with SIP and H.323 enterprise unified communications networks.
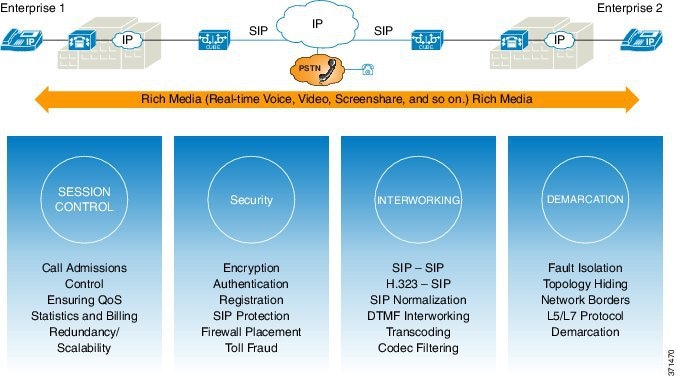
A CUBE interoperates with several different network elements including voice gateways, IP phones, and call-control servers in many different application environments, from advanced enterprise voice and/or video services with Cisco Unified Communications Manager or Cisco Unified Communications Manager Express, as well as simpler toll bypass and voice over IP (VoIP) transport applications. The CUBE provides organizations with all the border controller functions integrated into the network layer to interconnect unified communications voice and video enterprise-to-service-provider architectures.
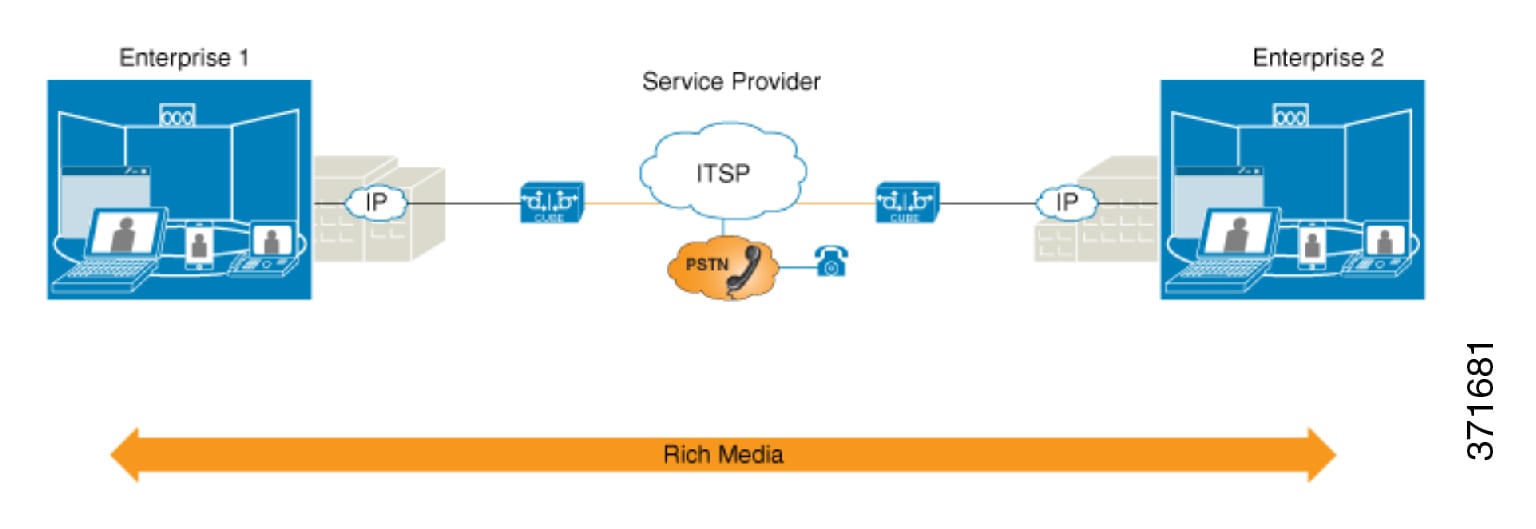
If an enterprise subscribes to VoIP services offered by an ITSP, connecting the enterprise CUCM through a CUBE provides network demarcation capabilities, such as security, topology hiding, transcoding, call admission control, protocol normalization and SIP registration, none of which is possible if CUCM connects directly to the ITSP. Another use case involves mergers or acquisitions in an enterprise and the need to integrate voice equipment, such as CUCMs, IP PBXs, VM servers, and so on. If the networks in the two organizations have overlapping IP addresses, CUBE can be used to connect the two distinct networks until the acquired organization can be migrated into the enterprise addressing plan.
SIP/H.323 Trunking
 Note |
H.323 protocol is no longer supported from Cisco IOS XE Bengaluru 17.6.1a onwards. Consider using SIP for multimedia applications. |
The Session Initiation Protocol (SIP) is a signaling communications protocol, widely used for controlling multimedia communication sessions such as voice and video calls over IP networks. SIP (or H.323) trunking is the use of VoIP to facilitate the connection of PBX to other VoIP endpoints across the Internet. To use SIP trunking, an enterprise must have a PBX (internal VoIP system) that connects to all internal end users, an Internet telephony service provider (ITSP), and a gateway that serves as the interface between the PBX and the ITSP. One of the most significant advantages of SIP and H.323 trunking is the ability to combine data, voice, and video in a single line, eliminating the need for separate physical media for each mode.

SIP trunking overcomes TDM barriers, in that it:
-
Improves efficiency of interconnection between networks
-
Simplifies PSTN interconnection with IP end-to-end
-
Enables rich media services to employees, customers, and partners
-
Carries converged voice, video, and data traffic

 Note |
For Cisco IOS XE Gibraltar 16.11.1a and later releases, the SIP processes are initiated only when either of the following CLIs is configured:
In the releases before Cisco IOS XE Gibraltar 16.11.1a, the following commands initiated the SIP processes:
|
Typical Deployment Scenarios for CUBE
CUBE in an enterprise environment serves two main purposes:
- External Connections—CUBE is the demarcation point within a unified communications network and provides interconnectivity with external networks. This includes H.323 and SIP voice and video connections.
- Internal Connections—When used within a VoIP network, CUBE increases flexibility and interoperability between devices.


 Feedback
Feedback