Feature Information for Cisco Unified Communications Manager Line-Side Support
The following table provides release information about the feature or features described in this module. This table lists only the software release that introduced support for a given feature in a given software release train. Unless noted otherwise, subsequent releases of that software release train also support that feature.
Use Cisco Feature Navigator to find information about platform support and Cisco software image support. To access Cisco Feature Navigator, go to https://cfnng.cisco.com/. An account on Cisco.com is not required.|
Feature Name |
Releases |
Feature Information |
|---|---|---|
|
Cisco Unified Communications Manager Line-Side Support |
15.5(2)T |
The Cisco Unified Communications Manager (CUCM) Line-Side Support feature was supported until the release 15.4(2)T. This feature has been deprecated from 15.5(2)T release onwards. |
|
Simplified Line-Side Support of CUCM on CUBE |
15.4(2)T Cisco IOS XE Release 3.12S |
The Simplified Line-Side Support of CUCM on CUBE feature simplifies the complex CUBE configurations required for registering IP Phones on a CUCM through CUBE using a single CLI that automatically applies all the necessary configurations. The following commands were modified by this feature: extension cucm and voice-class sip extension cucm . |
|
Cisco Unified Communications Manager Line-Side Support |
15.3(3)M Cisco IOS XE Release 3.10S |
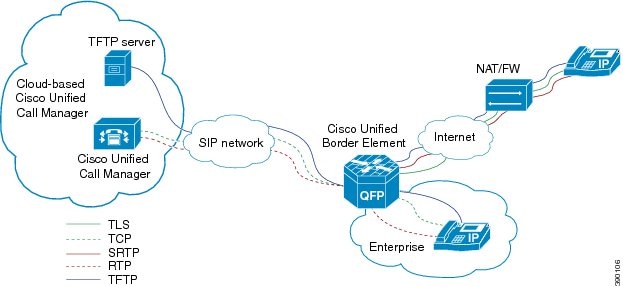
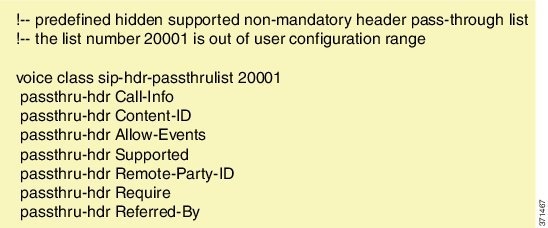
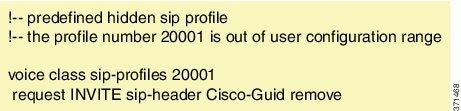
The Cisco Unified Communications Manager Line-Side Support feature provides line-side support for Cisco Unified Communications Manager and IP phones deployed on different logical networks, in both cloud-based and premise-based deployments. The following commands were introduced or modified: access-secure , capf-address , clear voice phone-proxy all-sessions , complete (ctl file) , ctl-file (phone proxy) , debug voice phone-proxy , description (ctl file) , description (phone proxy) , disable service-settings , max-concurrent-sessions , phone-proxy (dial peer) , port-range , record-entry , show voice class ctl-file , show voice class phone-proxy , service-map , session-timeout , tftp-server address , voice-ctl-file , voice-phone-proxy . |

 Feedback
Feedback