Pseudowire over MPLS
|
Feature Name |
Release Information |
Feature Description |
|
Pseudowire over MPLS |
Release 7.3.15 |
This feature allows you to tunnel two L2VPN Provider Edge (PE) devices to transport L2VPN traffic over an MPLS core network. MPLS labels are used to transport data over the pseudowire. |
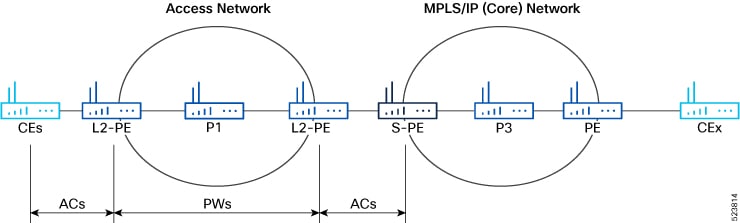
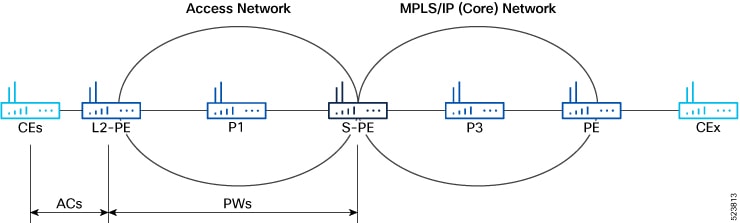
A pseudowire (PW) is a point-to-point connection between two provider edge (PE) devices which connects two attachment circuits (ACs). The two ACs connected at each PE are linked by a PW over the MPLS network, which is the MPLS PW.
PWs provide a common intermediate format to transport multiple types of network services over a Packet Switched Network (PSN) – a network that forwards packets – IPv4, IPv6, MPLS, Ethernet.
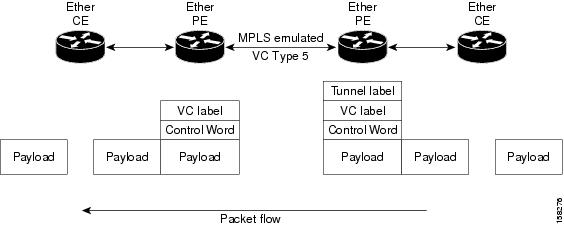
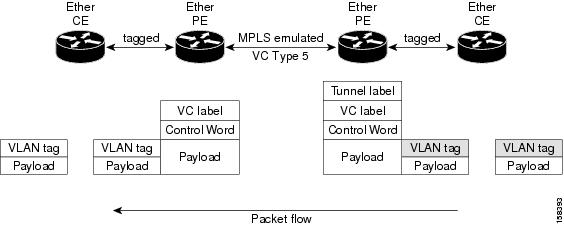
Pseudowire over MPLS or Ethernet-over-MPLS (EoMPLS) provides a tunneling mechanism for Ethernet traffic through an MPLS-enabled Layer 3 core network. PW over MPLS encapsulates Ethernet protocol data units (PDUs) using MPLS labels to forward them across the MPLS network.
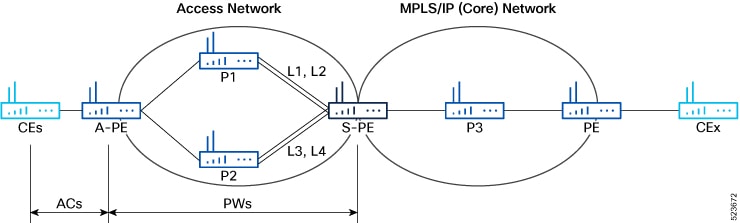
Topology
Here is an example that showcases how the L2VPN traffic is transported using the PW over MPLS network.

-
CEs are connected to PEs using the attachment circuit (AC).
-
PW is configured on the PE devices to connect two PEs over an MPLS core network.
Consider a traffic flow from Router 1 to Router 4. Router 1 sends the traffic to Router 2 through the AC. Router 2 adds the MPLS PW label and sends it to Router 3 through the PW. Each PE needs to have an MPLS label in order to reach the loopback of the remote PE. This label, usually called the Interior Gateway Protocol (IGP) label, can be learned through the MPLS Label Distribution Protocol (LDP) or MPLS Traffic Engineering (TE).
One PE advertises the MPLS label to the other PE for PW identification. Router 3 identifies traffic with MPLS label and sends it to the AC connected to Router 4 after removing the MPLS label.
You can configure static or dynamic point-to-point connections.
Configure Static Point-to-Point Connections Using Cross-Connect Circuits
This section describes how you can configure static point-to-point cross connects in a Layer 2 VPN.
Requirements and Limitations
Before you can configure a cross-connect circuit in a Layer 2 VPN, ensure that the following requirements are met:
-
The CE and PE routers are configured to operate in a network.
-
The name of a cross-connect circuit is configured to identify a pair of PE routers and must be unique within the cross-connect group.
-
A segment (an attachment circuit or pseudowire) is unique and can belong only to a single cross-connect circuit.
-
A static virtual circuit local label is globally unique and can be used in only one pseudowire.
 Note |
Static pseudowire connections do not use LDP for signaling. |
Topology
The following topology is used to configure static cross-connect circuits in a Layer 2 VPN.

Configuration
/* Configure PE1 */
Router# configure
Router(config)# l2vpn
Router(config-l2vpn)# xconnect group XCON1
Router(config-l2vpn-xc)# p2p xc1
Router(config-l2vpn-xc-p2p)# interface HundredGigEt0/1/0/0.1
Router(config-l2vpn-xc-p2p)# neighbor 10.0.0.3 pw-id 100
Router(config-l2vpn-xc-p2p-pw)# mpls static label local 50 remote 40
Router(config-l2vpn-xc-p2p-pw)# commit/*Configure PE2 */
Router# configure
Router(config)# l2vpn
Router(config-l2vpn)# xconnect group XCON1
Router(config-l2vpn-xc)# p2p xc1
Router(config-l2vpn-xc-p2p)# interface HundredGigE0/2/0/0.4
Router(config-l2vpn-xc-p2p)# neighbor 10.0.0.4 pw-id 100
Router(config-l2vpn-xc-p2p-pw)# mpls static label local 40 remote 50
Router(config-l2vpn-xc-p2p-pw)# commitRunning Configuration
/* On PE1 */
!
l2vpn
xconnect group XCON1
p2p xc1
interface HundredGigE0/1/0/0.1
neighbor ipv4 10.0.0.3 pw-id 100
mpls static label local 50 remote 40
!
/* On PE2 */
!
l2vpn
xconnect group XCON2
p2p xc1
interface HundredGigE0/2/0/0.4
neighbor ipv4 10.0.0.4 pw-id 100
mpls static label local 40 remote 50
!
Verification
/* Verify the static cross connect on PE1 */
Router# show l2vpn xconnect
Tue Apr 12 20:18:02.971 IST
Legend: ST = State, UP = Up, DN = Down, AD = Admin Down, UR = Unresolved,
SB = Standby, SR = Standby Ready, (PP) = Partially Programmed
XConnect Segment 1 Segment 2
Group Name ST Description ST Description ST
------------------------ ----------------------------- -----------------------------
XCON1 xc1 UP Hu0/1/0/0.1 UP 10.0.0.3 100 UP
----------------------------------------------------------------------------------------
/* Verify the static cross connect on PE2 */
Router# show l2vpn xconnect
Tue Apr 12 20:18:02.971 IST
Legend: ST = State, UP = Up, DN = Down, AD = Admin Down, UR = Unresolved,
SB = Standby, SR = Standby Ready, (PP) = Partially Programmed
XConnect Segment 1 Segment 2
Group Name ST Description ST Description ST
------------------------ ----------------------------- -----------------------------
XCON2 xc1 UP Hu0/2/0/0.4 UP 10.0.0.4 100 UP
----------------------------------------------------------------------------------------Configure Dynamic Point-to-point Cross-Connects
Perform this task to configure dynamic point-to-point cross-connects.
 Note |
For dynamic cross-connects, LDP must be up and running. |
Configuration
Router# configure
Router(config)# l2vpn
Router(config-l2vpn)# xconnect group vlan_grp_1
Router(config-l2vpn-xc)# p2p vlan1
Router(config-l2vpn-xc-p2p)# interface HunGigE 0/0/0/0.1
Router(config-l2vpn-xc-p2p)# neighbor 10.0.0.1 pw-id 1
Router(config-l2vpn-xc-p2p-pw)# commitRunning Configuration
configure
l2vpn
xconnect group vlan_grp_1
p2p vlan1
interface HunGigE 0/0/0/0.1
neighbor 10.0.0.1 pw-id 1
!





 Feedback
Feedback