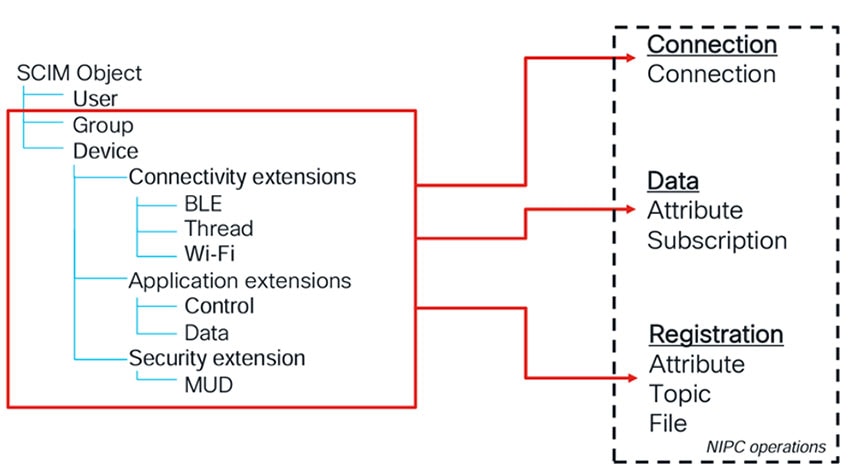
Overview of Cisco Spaces Connect for IoT Services
Enterprise customers need easy ways to onboard, authorize, and control IoT devices onto a single unified infrastructure. The Cisco Spaces Connect addresses this by providing a set of interfaces to:
-
Onboard devices into the infrastructure.
-
Control and receive events from the devices.
To accomplish this, the Cisco Spaces Connect leverages the following interfaces between the network and applications:
-
Onboarding Interface: This interface is used to onboard a device to a network.
-
Control Interface: This interface is used for bi-directional communication with a non-IP device.
-
Telemetry Interface: This interface is used for streaming telemetry from a non-IP device.



 Feedback
Feedback