- 查看管理连接状态
-
在 管理中心 中,在 页面上检查管理连接状态。
在 威胁防御 CLI,输入 sftunnel-status-brief 命令以查看管理连接状态。您还可以使用 sftunnel-status 查看更完整的信息。
请参阅以下有关关闭连接的输出示例;没有显示“连接至“信息,也没有显示心跳信息:
> sftunnel-status-brief
PEER:10.10.17.202
Registration: Completed.
Connection to peer '10.10.17.202' Attempted at Mon Jun 15 09:21:57 2020 UTC
Last disconnect time : Mon Jun 15 09:19:09 2020 UTC
Last disconnect reason : Both control and event channel connections with peer went down
请参阅以下关于已建立连接的输出示例,其中显示了对等通道和心跳信息:
> sftunnel-status-brief
PEER:10.10.17.202
Peer channel Channel-A is valid type (CONTROL), using 'eth0', connected to '10.10.17.202' via '10.10.17.222'
Peer channel Channel-B is valid type (EVENT), using 'eth0', connected to '10.10.17.202' via '10.10.17.222'
Registration: Completed.
IPv4 Connection to peer '10.10.17.202' Start Time: Wed Jun 10 14:27:12 2020 UTC
Heartbeat Send Time: Mon Jun 15 09:02:08 2020 UTC
Heartbeat Received Time: Mon Jun 15 09:02:16 2020 UTC
- 查看 威胁防御 网络信息
-
在 威胁防御 CLI 上,查看管理和 管理中心 访问数据接口网络设置:
show network
> show network
===============[ System Information ]===============
Hostname : 5516X-4
DNS Servers : 208.67.220.220,208.67.222.222
Management port : 8305
IPv4 Default route
Gateway : data-interfaces
IPv6 Default route
Gateway : data-interfaces
======================[ br1 ]=======================
State : Enabled
Link : Up
Channels : Management & Events
Mode : Non-Autonegotiation
MDI/MDIX : Auto/MDIX
MTU : 1500
MAC Address : 28:6F:7F:D3:CB:8D
----------------------[ IPv4 ]----------------------
Configuration : Manual
Address : 10.99.10.4
Netmask : 255.255.255.0
Gateway : 10.99.10.1
----------------------[ IPv6 ]----------------------
Configuration : Disabled
===============[ Proxy Information ]================
State : Disabled
Authentication : Disabled
======[ System Information - Data Interfaces ]======
DNS Servers :
Interfaces : GigabitEthernet1/1
===============[ GigabitEthernet1/1 ]===============
State : Enabled
Link : Up
Name : outside
MTU : 1500
MAC Address : 28:6F:7F:D3:CB:8F
----------------------[ IPv4 ]----------------------
Configuration : Manual
Address : 10.89.5.29
Netmask : 255.255.255.192
Gateway : 10.89.5.1
----------------------[ IPv6 ]----------------------
Configuration : Disabled
- 检查向 管理中心注册 威胁防御
-
在 威胁防御 CLI 中,检查 管理中心 注册是否已完成。请注意,此命令不会显示管理连接的 当前 状态。
show managers
> show managers
Type : Manager
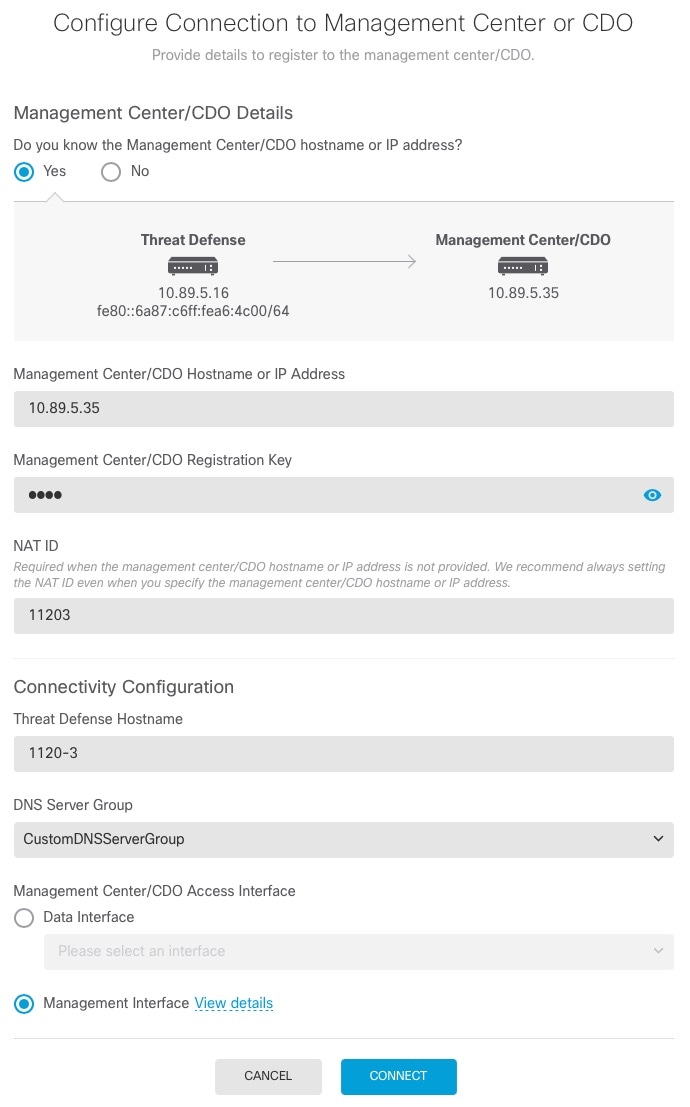
Host : 10.89.5.35
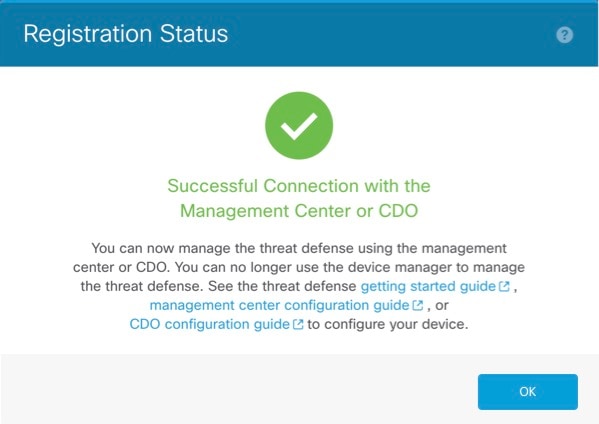
Registration : Completed
>
- Ping the 管理中心
-
在 威胁防御 CLI 上,使用以下命令从数据接口对 管理中心 执行 ping 操作:
ping fmc_ip
在 威胁防御 CLI 上,使用以下命令从管理接口对 管理中心 执行 ping 操作,该接口应通过背板路由到数据接口:
ping system fmc_ip
- 捕获 威胁防御 内部接口上的数据包
-
在 威胁防御 CLI 上,捕获内部背板接口 (nlp_int_tap) 上的数据包,以查看是否发送了管理数据包:
capture 名称 interface nlp_int_tap trace detail match ip any any
show capturename trace detail
- 检查内部接口状态,统计信息和数据包计数
-
在 威胁防御 CLI 上,查看有关内部背板接口 nlp_int_tap 的信息:
show interace detail
> show interface detail
[...]
Interface Internal-Data0/1 "nlp_int_tap", is up, line protocol is up
Hardware is en_vtun rev00, BW Unknown Speed-Capability, DLY 1000 usec
(Full-duplex), (1000 Mbps)
Input flow control is unsupported, output flow control is unsupported
MAC address 0000.0100.0001, MTU 1500
IP address 169.254.1.1, subnet mask 255.255.255.248
37 packets input, 2822 bytes, 0 no buffer
Received 0 broadcasts, 0 runts, 0 giants
0 input errors, 0 CRC, 0 frame, 0 overrun, 0 ignored, 0 abort
0 pause input, 0 resume input
0 L2 decode drops
5 packets output, 370 bytes, 0 underruns
0 pause output, 0 resume output
0 output errors, 0 collisions, 0 interface resets
0 late collisions, 0 deferred
0 input reset drops, 0 output reset drops
input queue (blocks free curr/low): hardware (0/0)
output queue (blocks free curr/low): hardware (0/0)
Traffic Statistics for "nlp_int_tap":
37 packets input, 2304 bytes
5 packets output, 300 bytes
37 packets dropped
1 minute input rate 0 pkts/sec, 0 bytes/sec
1 minute output rate 0 pkts/sec, 0 bytes/sec
1 minute drop rate, 0 pkts/sec
5 minute input rate 0 pkts/sec, 0 bytes/sec
5 minute output rate 0 pkts/sec, 0 bytes/sec
5 minute drop rate, 0 pkts/sec
Control Point Interface States:
Interface number is 14
Interface config status is active
Interface state is active
- 检查路由和 NAT
-
在 威胁防御 CLI 中,检查是否已添加默认路由 (S *),以及管理接口 (nlp_int_tap) 是否存在内部 NAT 规则。
show route
> show route
Codes: L - local, C - connected, S - static, R - RIP, M - mobile, B - BGP
D - EIGRP, EX - EIGRP external, O - OSPF, IA - OSPF inter area
N1 - OSPF NSSA external type 1, N2 - OSPF NSSA external type 2
E1 - OSPF external type 1, E2 - OSPF external type 2, V - VPN
i - IS-IS, su - IS-IS summary, L1 - IS-IS level-1, L2 - IS-IS level-2
ia - IS-IS inter area, * - candidate default, U - per-user static route
o - ODR, P - periodic downloaded static route, + - replicated route
SI - Static InterVRF
Gateway of last resort is 10.89.5.1 to network 0.0.0.0
S* 0.0.0.0 0.0.0.0 [1/0] via 10.89.5.1, outside
C 10.89.5.0 255.255.255.192 is directly connected, outside
L 10.89.5.29 255.255.255.255 is directly connected, outside
>
show nat
> show nat
Auto NAT Policies (Section 2)
1 (nlp_int_tap) to (outside) source static nlp_server_0_sftunnel_intf3 interface service tcp 8305 8305
translate_hits = 0, untranslate_hits = 6
2 (nlp_int_tap) to (outside) source static nlp_server_0_ssh_intf3 interface service tcp ssh ssh
translate_hits = 0, untranslate_hits = 73
3 (nlp_int_tap) to (outside) source static nlp_server_0_sftunnel_ipv6_intf3 interface ipv6 service tcp 8305 8305
translate_hits = 0, untranslate_hits = 0
4 (nlp_int_tap) to (outside) source dynamic nlp_client_0_intf3 interface
translate_hits = 174, untranslate_hits = 0
5 (nlp_int_tap) to (outside) source dynamic nlp_client_0_ipv6_intf3 interface ipv6
translate_hits = 0, untranslate_hits = 0
>
- 检查其他设置
-
请参阅以下命令以检查是否存在所有其他设置。您还可以在 管理中心 的 页面上看到许多这些命令。
show running-config sftunnel
> show running-config sftunnel
sftunnel interface outside
sftunnel port 8305
show running-config ip-client
> show running-config ip-client
ip-client outside
show conn address fmc_ip
> show conn address 10.89.5.35
5 in use, 16 most used
Inspect Snort:
preserve-connection: 0 enabled, 0 in effect, 0 most enabled, 0 most in effect
TCP nlp_int_tap 10.89.5.29(169.254.1.2):51231 outside 10.89.5.35:8305, idle 0:00:04, bytes 86684, flags UxIO
TCP nlp_int_tap 10.89.5.29(169.254.1.2):8305 outside 10.89.5.35:52019, idle 0:00:02, bytes 1630834, flags UIO
>
- 检查 DDNS 更新是否成功
-
在 威胁防御 CLI 中,检查 DDNS 更新是否成功:
debug ddns
> debug ddns
DDNS update request = /v3/update?hostname=domain.example.org&myip=209.165.200.225
Successfuly updated the DDNS sever with current IP addresses
DDNS: Another update completed, outstanding = 0
DDNS: IDB SB total = 0
如果更新失败,请使用 debug http 和 debug ssl 命令。对于证书验证失败,请检查是否已在设备上安装根证书:
show crypto ca certificates trustpoint_name
要检查 DDNS 操作,请执行以下操作:
show ddns update interface fmc_访问_ifc_name
> show ddns update interface outside
Dynamic DNS Update on outside:
Update Method Name Update Destination
RBD_DDNS not available
Last Update attempted on 04:11:58.083 UTC Thu Jun 11 2020
Status : Success
FQDN : domain.example.org
IP addresses : 209.165.200.225
- 检查 管理中心 日志文件
-
请参阅 https://cisco.com/go/fmc-reg-error。

 )
)


 )
)
 反馈
反馈