- Index
- Preface
- Overview
- Using the Command-Line Interface
- Getting Started with CMS
- Assigning the Switch IP Address and Default Gateway
- Managing Switch Stacks
- Clustering Switches
- Administering the Switch
- Configuring SDM Templates
- Configuring Switch-Based Authentication
- Configuring 802.1X Port-Based Authentication
- Configuring Interface Characteristics
- Configuring SmartPort Macros
- Configuring VLANs
- Configuring VTP
- Configuring Voice VLAN
- Configuring STP
- Configuring MSTP
- Configuring Optional Spanning-Tree Features
- Configuring DHCP Features
- Configuring IGMP Snooping and MVR
- Configuring Port-Based Traffic Control
- Configuring CDP
- Configuring UDLD
- Configuring SPAN and RSPAN
- Configuring RMON
- Configuring System Message Logging
- Configuring SNMP
- Configuring Network Security with ACLs
- Configuring QoS
- Configuring EtherChannels
- Configuring IP Unicast Routing
- Configuring HSRP
- Configuring IP Multicast Routing
- Configuring MSDP
- Configuring Fallback Bridging
- Troubleshooting
- Supported MIBs
- Working with the Cisco IOS File System, Configuration Files, and Software Images
- Unsupported Commands in Cisco IOS Release 12.1(19)EA1
Configuring DHCP Features
This chapter describes how to configure Dynamic Host Configuration Protocol (DHCP) snooping and the option-82 data insertion features on the Catalyst 3750 switch. Unless otherwise noted, the term switch refers to a standalone switch and to a switch stack.

Note ![]() For complete syntax and usage information for the commands used in this chapter, see the command reference for this release, and refer to the "IP Addressing and Services" section in the Cisco IOS IP and IP Routing Command Reference for Release 12.1.
For complete syntax and usage information for the commands used in this chapter, see the command reference for this release, and refer to the "IP Addressing and Services" section in the Cisco IOS IP and IP Routing Command Reference for Release 12.1.
This chapter consists of these sections:
Understanding DHCP Features
DHCP is widely used in LAN environments to dynamically assign host IP addresses from a centralized server, which significantly reduces the overhead of administration of IP addresses. DHCP also helps conserve the limited IP address space because IP addresses no longer need to be permanently assigned to hosts; only those hosts that are connected to the network consume IP addresses.
DHCP Snooping
DHCP snooping is a DHCP security feature that provides network security by filtering untrusted DHCP messages and by building and maintaining a DHCP snooping binding table. An untrusted message is a message that is received from outside the network or firewall that can cause traffic attacks within your network.
The DHCP snooping binding table contains the MAC address, IP address, lease time, binding type, VLAN number, and interface information that corresponds to the local untrusted interfaces of a switch; it does not contain information regarding hosts interconnected with a trusted interface. An untrusted interface is an interface that is configured to receive messages from outside the network or firewall. A trusted interface is an interface that is configured to receive only messages from within the network.
DHCP snooping acts like a firewall between untrusted hosts and DHCP servers. It also gives you a way to differentiate between untrusted interfaces connected to the end user and trusted interfaces connected to the DHCP server or another switch.
Option-82 Data Insertion
In residential, metropolitan Ethernet-access environments, DHCP can centrally manage the IP address assignments for a large number of subscribers. When the DHCP option-82 feature is enabled on the switch, a subscriber is identified by the switch port through which it connects to the network (in addition to its MAC address). Multiple hosts on the subscriber LAN can be connected to the same port on the access switch and are uniquely identified.
Figure 19-1 is an example of a metropolitan Ethernet network in which a centralized DHCP server assigns IP addresses to subscribers connected to the switch at the access layer. Because the DHCP clients and their associated DHCP server do not reside on the same IP network or subnet, a DHCP relay agent (the Catalyst switch) is configured with a helper address to enable broadcast forwarding and to transfer DHCP messages between the clients and the server.
Figure 19-1 DHCP Relay Agent in a Metropolitan Ethernet Network
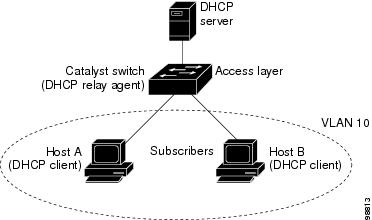
When you enable the DHCP snooping information option 82 on the switch, this sequence of events occurs:
•![]() The host (DHCP client) generates a DHCP request and broadcasts it on the network.
The host (DHCP client) generates a DHCP request and broadcasts it on the network.
•![]() When the switch receives the DHCP request, it adds the option-82 information in the packet. The option-82 information contains the switch MAC address (the remote ID suboption) and the port identifier, vlan-mod-port, from which the packet is received (the circuit ID suboption).
When the switch receives the DHCP request, it adds the option-82 information in the packet. The option-82 information contains the switch MAC address (the remote ID suboption) and the port identifier, vlan-mod-port, from which the packet is received (the circuit ID suboption).
•![]() The switch forwards the DHCP request that includes the option-82 field to the DHCP server.
The switch forwards the DHCP request that includes the option-82 field to the DHCP server.
•![]() The DHCP server receives the packet. If the server is option-82-capable, it can use the remote ID, the circuit ID, or both to assign IP addresses and implement policies, such as restricting the number of IP addresses that can be assigned to a single remote ID or a circuit ID. Then the DHCP server echoes the option-82 field in the DHCP reply.
The DHCP server receives the packet. If the server is option-82-capable, it can use the remote ID, the circuit ID, or both to assign IP addresses and implement policies, such as restricting the number of IP addresses that can be assigned to a single remote ID or a circuit ID. Then the DHCP server echoes the option-82 field in the DHCP reply.
•![]() The DHCP server unicasts the reply to the switch if the request was relayed to the server by the switch. The switch verifies that it originally inserted the option-82 data by inspecting the remote ID and possibly the circuit ID fields. The switch removes the option-82 field and forwards the packet to the switch port that connects to the DHCP client that sent the DHCP request.
The DHCP server unicasts the reply to the switch if the request was relayed to the server by the switch. The switch verifies that it originally inserted the option-82 data by inspecting the remote ID and possibly the circuit ID fields. The switch removes the option-82 field and forwards the packet to the switch port that connects to the DHCP client that sent the DHCP request.
DHCP Snooping and Switch Stacks
DHCP snooping is managed on the stack master. When a new switch joins the stack, the switch receives DHCP snooping configuration from the stack master. When a member leaves the stack, all DHCP snooping bindings associated with the switch age out.
When a stack merge occurs, all DHCP snooping bindings in the stack master are lost if it is no longer the stack master. With a stack partition, the existing stack master is unchanged, and the bindings belonging to the partitioned switches age out. The new master of the partitioned stack begins processing the new incoming DHCP packets. For more information about switch stacks, see "Managing Switch Stacks."
Configuring DHCP Features
These sections describe how to configure DHCP snooping and option 82 on your switch:
•![]() DHCP Snooping Configuration Guidelines
DHCP Snooping Configuration Guidelines
•![]() Enabling DHCP Snooping and Option 82
Enabling DHCP Snooping and Option 82
Default DHCP Configuration
Table 19-1 shows the default DHCP configuration.
DHCP Snooping Configuration Guidelines
These are the configuration guidelines for DHCP snooping.
•![]() You must globally enable DHCP snooping on the switch.
You must globally enable DHCP snooping on the switch.
•![]() DHCP snooping is not active until DHCP snooping is enabled on a VLAN.
DHCP snooping is not active until DHCP snooping is enabled on a VLAN.
•![]() When you globally enable DHCP snooping on the switch, these Cisco IOS commands are not available until snooping is disabled. If you enter these commands, the switch returns an error message, and the configuration is not applied.
When you globally enable DHCP snooping on the switch, these Cisco IOS commands are not available until snooping is disabled. If you enter these commands, the switch returns an error message, and the configuration is not applied.
–![]() ip dhcp relay information check global configuration command
ip dhcp relay information check global configuration command
–![]() ip dhcp relay information policy global configuration command
ip dhcp relay information policy global configuration command
–![]() ip dhcp relay information trust-all global configuration command
ip dhcp relay information trust-all global configuration command
–![]() ip dhcp relay information trusted interface configuration command
ip dhcp relay information trusted interface configuration command
•![]() Before configuring the DHCP information option on your switch, make sure to configure the device that is acting as the DHCP server. For example, you must specify the IP addresses that the DHCP server can assign or exclude or configure DHCP options for devices.
Before configuring the DHCP information option on your switch, make sure to configure the device that is acting as the DHCP server. For example, you must specify the IP addresses that the DHCP server can assign or exclude or configure DHCP options for devices.
–![]() If your switch is the DHCP server, see the "Configuring the DHCP Server" section section for more information.
If your switch is the DHCP server, see the "Configuring the DHCP Server" section section for more information.
–![]() If your DHCP server is a Cisco device, refer to the "IP Addressing and Services" section in the "Configuring DHCP" chapter of the Cisco IOS IP and IP Routing Configuration Guide for Release 12.1. Otherwise, refer to the documentation that shipped with the server.
If your DHCP server is a Cisco device, refer to the "IP Addressing and Services" section in the "Configuring DHCP" chapter of the Cisco IOS IP and IP Routing Configuration Guide for Release 12.1. Otherwise, refer to the documentation that shipped with the server.
Enabling DHCP Snooping and Option 82
Beginning in privileged EXEC mode, follow these steps to enable DHCP snooping on the switch.
To disable DHCP snooping, use the no ip dhcp snooping global configuration command. To disable DHCP snooping on a VLAN or range of VLANs, use the no ip dhcp snooping vlan vlan-id global configuration command. To disable the insertion and removal of the option-82 field, use the no ip dhcp snooping information option global configuration command.
This example shows how to enable DHCP snooping globally and on VLAN 10 and to configure a rate limit of 100 packets per second on a port:
Switch(config)# ip dhcp snooping
Switch(config)# ip dhcp snooping vlan 10
Switch(config)# ip dhcp snooping information option
Switch(config)# interface gigabitethernet2/0/1
Switch(config-if)# ip dhcp snooping limit rate 100
Displaying DHCP Information
You can display a DHCP snooping binding table and configuration information for all interfaces on a switch.
Displaying a Binding Table
The DHCP snooping binding table for each switch has binding entries that correspond to untrusted ports. The table does not have information about hosts interconnected with a trusted port because each interconnected switch has its own DHCP snooping binding table.
This example shows how to display the DHCP snooping binding entries for a switch.
Switch# show ip dhcp snooping binding
MacAddress IpAddress Lease(sec) Type VLAN Interface
------------------ --------------- ---------- ------- ---- --------------------
00:30:94:C2:EF:35 41.0.0.51 286 dynamic 41 gigabitethernet2/0/1
00:D0:B7:1B:35:DE 41.0.0.52 237 dynamic 41 gigabitethernet2/0/1
00:00:00:00:00:01 40.0.0.46 286 dynamic 40 gigabitethernet1/0/2
00:00:00:00:00:03 42.0.0.33 286 dynamic 42 gigabitethernet3/0/2
00:00:00:00:00:02 41.0.0.53 286 dynamic 41 gigabitethernet2/0/2
Table 19-2 describes the fields in the show ip dhcp snooping binding command output.
Displaying the DHCP Snooping Configuration
This example shows how to display the DHCP snooping configuration for a switch.
Switch# show ip dhcp snooping
Switch DHCP snooping is enabled
DHCP snooping is configured on following VLANs:
40-42
Insertion of option 82 is enabled
Interface Trusted Rate limit (pps)
------------------------ ------- ----------------
gigabitethernet1/0/1 yes unlimited
gigabitethernet2/0/2 no 5000
gigabitethernet2/0/3 yes unlimited
gigabitethernet2/0/4 yes unlimited
 Feedback
Feedback