- Index
- Preface
- Product Overview
- Command-Line Interfaces
- Configuring the Switch for the First Time
- Configuring a Supervisor Engine 32 PISA
- Configuring NSF with SSO Supervisor Engine Redundancy
- Configuring RPR Supervisor Engine Redundancy
- Configuring Interfaces
- Configuring Layer 2 Ethernet Interfaces
- Configuring Flex Links
- Configuring Layer 3 and Layer 2 EtherChannel
- Configuring VLAN Trunking Protocol (VTP)
- Configuring VLANs
- Configuring Private VLANs (PVLANs)
- Configuring Cisco IP Phone Support
- Configuring IEEE 802.1Q Tunneling
- Configuring Layer 2 Protocol Tunneling (L2PT)
- Configuring STP and MST
- Configuring STP Features
- Configuring Layer 3 Interfaces
- Configuring UDE and UDLR
- Configuring PFC3BXL and PFC3B Multiprotocol Label Switching (MPLS)
- Configuring IPv4 Multicast VPN Support
- Configuring IP Unicast Layer 3 Switching
- Configuring IPv6 Multicast Layer 3 Switching
- Configuring IPv4 Multicast Layer 3 Switching
- Configuring MLDv2 Snooping
- Configuring IGMP Snooping
- Configuring PIM Snooping
- Configuring Router-Port Group Management Protocol (RGMP)
- Configuring Network Security
- Understanding Cisco IOS ACL Support
- Configuring VLAN ACLs (VACLs)
- Configuring Denial of Service (DoS) Protection
- Configuring DHCP Snooping
- Configuring Dynamic ARP Inspection (DAI)
- Configuring Traffic-Storm Control
- Configuring Unknown Unicast and Multicast Flood Blocking
- Configuring PFC QoS
- Configuring PFC3BXL or PFC3B Mode MPLS QoS
- Configuring PFC QoS Statistics Data Export
- Configuring Network Admission Control (NAC)
- Configuring 802.1X Port-Based Authentication
- Configuring Port Security
- Configuring Cisco Discovery Protocol (CDP)
- Configuring UniDirectional Link Detection (UDLD)
- Configuring the NetFlow Table
- Configuring NetFlow Data Export (NDE)
- Configuring Local SPAN, Remote SPAN (RSPAN), and Encapsulated RSPAN
- Configuring SNMP IfIndex Persistence
- Power Management and Environmental Monitoring
- Configuring Online Diagnostics
- Configuring Top N Utility Reports
- Using the Layer 2 Traceroute Utility
- Online Diagnostic Tests
- Acronyms
Configuring UDLD
This chapter describes how to configure the UniDirectional Link Detection (UDLD) protocol on the Catalyst 6500 series switches.

Note ![]() For complete syntax and usage information for the commands used in this chapter, refer to the Catalyst Supervisor Engine 32 PISA Cisco IOS Command Reference, Release 12.2ZY, at this URL:
For complete syntax and usage information for the commands used in this chapter, refer to the Catalyst Supervisor Engine 32 PISA Cisco IOS Command Reference, Release 12.2ZY, at this URL:
http://www.cisco.com/en/US/docs/switches/lan/catalyst6500/ios/12.2ZY/command/reference/cmdref.html
This chapter consists of these sections:
Understanding How UDLD Works
These sections describe how UDLD works:
UDLD Overview
The Cisco-proprietary UDLD protocol allows devices connected through fiber-optic or copper (for example, Category 5 cabling) Ethernet cables connected to LAN ports to monitor the physical configuration of the cables and detect when a unidirectional link exists. When a unidirectional link is detected, UDLD shuts down the affected LAN port and alerts the user. Unidirectional links can cause a variety of problems, including spanning tree topology loops.
UDLD is a Layer 2 protocol that works with the Layer 1 protocols to determine the physical status of a link. At Layer 1, autonegotiation takes care of physical signaling and fault detection. UDLD performs tasks that autonegotiation cannot perform, such as detecting the identities of neighbors and shutting down misconnected LAN ports. When you enable both autonegotiation and UDLD, Layer 1 and Layer 2 detections work together to prevent physical and logical unidirectional connections and the malfunctioning of other protocols.
A unidirectional link occurs whenever traffic transmitted by the local device over a link is received by the neighbor but traffic transmitted from the neighbor is not received by the local device. If one of the fiber strands in a pair is disconnected, as long as autonegotiation is active, the link does not stay up. In this case, the logical link is undetermined, and UDLD does not take any action. If both fibers are working normally at Layer 1, then UDLD at Layer 2 determines whether those fibers are connected correctly and whether traffic is flowing bidirectionally between the correct neighbors. This check cannot be performed by autonegotiation, because autonegotiation operates at Layer 1.
The Catalyst 6500 series switch periodically transmits UDLD packets to neighbor devices on LAN ports with UDLD enabled. If the packets are echoed back within a specific time frame and they are lacking a specific acknowledgment (echo), the link is flagged as unidirectional and the LAN port is shut down. Devices on both ends of the link must support UDLD in order for the protocol to successfully identify and disable unidirectional links.

Note ![]() By default, UDLD is locally disabled on copper LAN ports to avoid sending unnecessary control traffic on this type of media since it is often used for access ports.
By default, UDLD is locally disabled on copper LAN ports to avoid sending unnecessary control traffic on this type of media since it is often used for access ports.
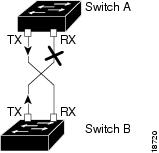
Figure 45-1 shows an example of a unidirectional link condition. Switch B successfully receives traffic from Switch A on the port. However, Switch A does not receive traffic from Switch B on the same port. UDLD detects the problem and disables the port.
Figure 45-1 Unidirectional Link
UDLD Aggressive Mode
UDLD aggressive mode is disabled by default. Configure UDLD aggressive mode only on point-to-point links between network devices that support UDLD aggressive mode. With UDLD aggressive mode enabled, when a port on a bidirectional link that has a UDLD neighbor relationship established stops receiving UDLD packets, UDLD tries to reestablish the connection with the neighbor. After eight failed retries, the port is disabled.
To prevent spanning tree loops, nonaggressive UDLD with the default interval of 15 seconds is fast enough to shut down a unidirectional link before a blocking port transitions to the forwarding state (with default spanning tree parameters).
When you enable UDLD aggressive mode, you receive additional benefits in the following situations:
•![]() One side of a link has a port stuck (both Tx and Rx)
One side of a link has a port stuck (both Tx and Rx)
•![]() One side of a link remains up while the other side of the link has gone down
One side of a link remains up while the other side of the link has gone down
In these cases, UDLD aggressive mode disables one of the ports on the link, which prevents traffic from being discarding.

Note ![]() In UDLD normal mode, when a unidirectional error is detected, the port is not disabled. In UDLD aggressive mode, when a unidirectional error is detected, the port is disabled.
In UDLD normal mode, when a unidirectional error is detected, the port is not disabled. In UDLD aggressive mode, when a unidirectional error is detected, the port is disabled.
Default UDLD Configuration
Table 45-1 shows the default UDLD configuration.
Configuring UDLD
These sections describe how to configure UDLD:
•![]() Enabling UDLD on Individual LAN Interfaces
Enabling UDLD on Individual LAN Interfaces
•![]() Disabling UDLD on Fiber-Optic LAN Interfaces
Disabling UDLD on Fiber-Optic LAN Interfaces
•![]() Configuring the UDLD Probe Message Interval
Configuring the UDLD Probe Message Interval
•![]() Resetting Disabled LAN Interfaces
Resetting Disabled LAN Interfaces
Enabling UDLD Globally
To enable UDLD globally on all fiber-optic LAN ports, perform this task:
Enabling UDLD on Individual LAN Interfaces
To enable UDLD on individual LAN ports, perform this task:
|
|
|
|
|---|---|---|
Step 1 |
Router(config)# interface type1 slot/port |
Selects the LAN port to configure. |
Step 2 |
Router(config-if)# udld port [aggressive] |
Enables UDLD on a specific LAN port. Enter the aggressive keyword to enable aggressive mode. On a fiber-optic LAN port, this command overrides the udld enable global configuration command setting. |
Router(config-if)# no udld port [aggressive] |
Disables UDLD on a nonfiber-optic LAN port. Note |
|
Step 3 |
Router# show udld type1 slot/number |
Verifies the configuration. |
1 type = ethernet, fastethernet, gigabitethernet, or tengigabitethernet |
Disabling UDLD on Fiber-Optic LAN Interfaces
To disable UDLD on individual fiber-optic LAN ports, perform this task:
|
|
|
|
|---|---|---|
Step 1 |
Router(config)# interface type1 slot/port |
Selects the LAN port to configure. |
Step 2 |
Router(config-if)# udld port disable |
Disables UDLD on a fiber-optic LAN port. |
Router(config-if)# no udld port disable |
Reverts to the udld enable global configuration command setting. Note |
|
Step 3 |
Router# show udld type1 slot/number |
Verifies the configuration. |
1 type = ethernet, fastethernet, gigabitethernet, or tengigabitethernet |
Configuring the UDLD Probe Message Interval
To configure the time between UDLD probe messages on ports that are in advertisement mode and are currently determined to be bidirectional, perform this task:
|
|
|
|
|---|---|---|
Step 1 |
Router(config)# udld message time interval |
Configures the time between UDLD probe messages on ports that are in advertisement mode and are currently determined to be bidirectional; valid values are from 7 to 90 seconds. |
Router(config)# no udld message |
Returns to the default value (60 seconds). |
|
Step 2 |
Router# show udld type1 slot/number |
Verifies the configuration. |
1 type = ethernet, fastethernet, gigabitethernet, or tengigabitethernet |
Resetting Disabled LAN Interfaces
To reset all LAN ports that have been shut down by UDLD, perform this task:
|
|
|
|---|---|
Router# udld reset |
Resets all LAN ports that have been shut down by UDLD. |
 Feedback
Feedback