|
+ Create VA Pod button disabled
|
Hover your cursor over the disabled button to learn more about why it's disabled.
The following are likely reasons why you can't create a new VA pod:
-
You have reached the limit of VPC service quota: For every region, a limit is set by your AWS administrator for how many VPCs can be created. Typically, there are 5 VPCs per region, and each VPC can have only one VA
pod. However, you may want to contact your AWS administrator for the exact number.
Note that any VPC used for resources outside of Cisco Global Launchpad contributes to this limit. For example, if your AWS account has a limit of five VPCs and two are in use, you can only create three more VA pods in the selected region.
To create new VA pods, ask your AWS administrator to change the limit or delete some of your existing VA pods or VPCs on your AWS account. For more information, see the AWS
Creating a service quota increase topic in the AWS Support User Guide on the AWS website.
-
Pod deletion in progress: The deletion of the last VA pod in the region is in progress. Wait a few minutes, and then retry creating a new VA pod.
|
|
AMI ID for this region is not available for your account.
|
When you click + Create a new VA pod, Cisco Global Launchpad validates the AMI ID for your selected region.
If you encounter this error, the validation failed and you can't create a new pod in this region. Contact Cisco TAC to help
you resolve the issue.
|
|
Your VPN configuration is invalid. At this step you cannot update it so please delete the instance and create a new one.
|
When configuring a VA pod, the following VPN vendors are not supported:
-
Barracuda
-
Sophos
-
Vyatta
-
Zyxel
If you are using an unsupported VPN vendor, the following error message is displayed on the Configure the on-premises tunnel endpoint window:
Your VPN configuration is invalid. At this step, you cannot update it,
so please delete the instance and create a new one.
|
|
CustomerGateway with type "ipsec.1", ip-address "xx.xx.xx.xx", and bgp-asn "65000" already exists (RequestToken: f78ad45d-b4f8-d02b-9040-f29e5f5f86cf,
HandlerErrorCode: AlreadyExists)
|
You may encounter this error if you try to create more than one VA pod at a time.
To resolve this error, delete the failed VA pod and recreate it. Ensure that you create only one VA pod at a time.
|
|
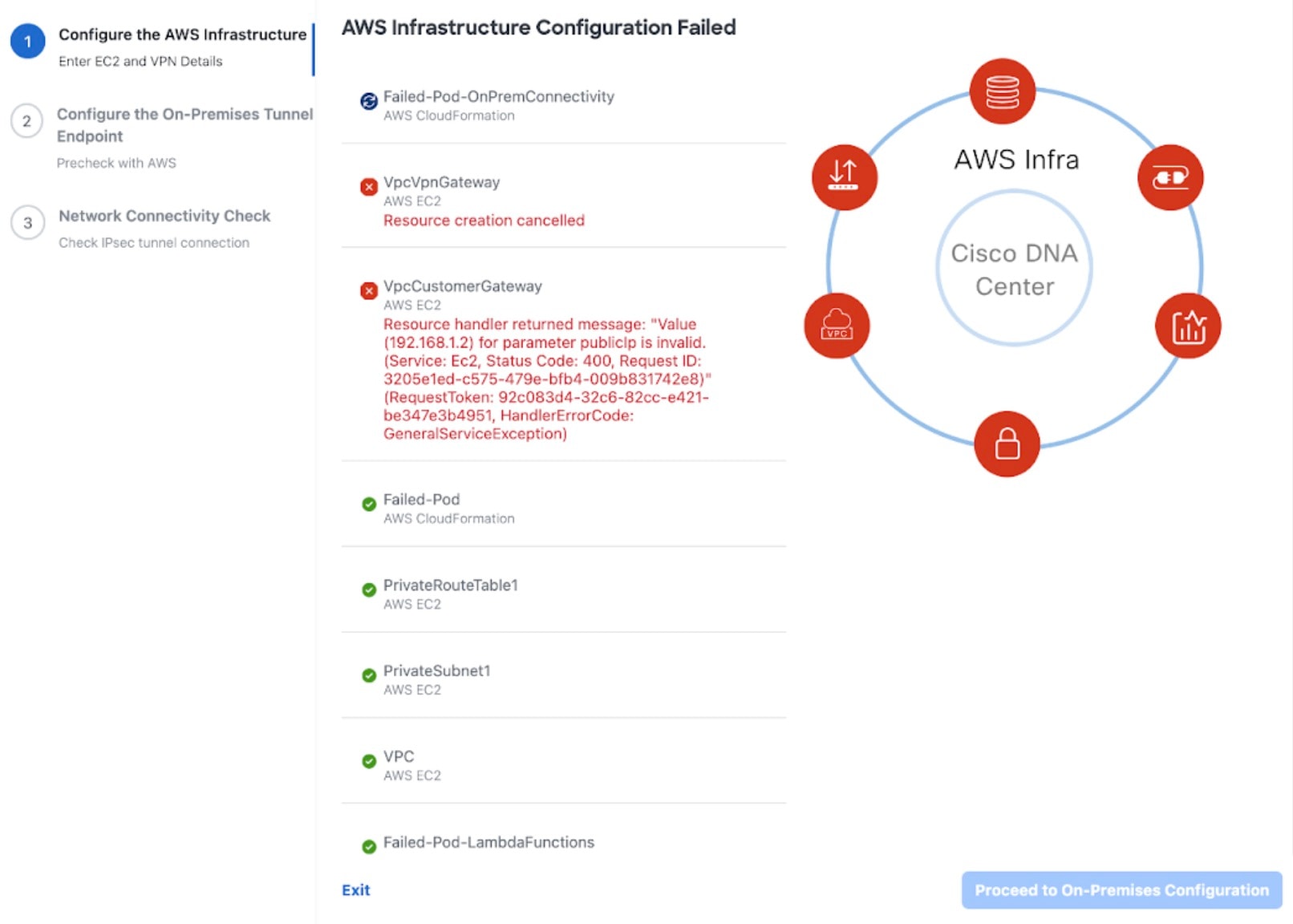
AWS infrastructure failed.
|
If the AWS configuration fails, return to the Dashboard pane and create a new VA pod. For more information, see Create a New VA Pod.
|
Note
|
You can delete the VA pod that failed to configure.
|
|
|
AWS configuration fails when editing a VA Pod
|
Make sure that any manual process on the AWS console completed successfully, and try this step again. If the problem persists, contact Cisco TAC.
|
Note
|
To avoid such conflicts, we recommend that you do not make any manual changes to the VA pods. Instead, use Cisco Global Launchpad for all actions.
|
|
|
Deleting VA Pod has failed
|
Make sure that any manual process on the AWS console completed successfully, and try this step again. If the problem persists, contact Cisco TAC.
|
Note
|
To avoid such conflicts, we recommend that you do not make any manual changes to the VA pods. Instead, use Cisco Global Launchpad for all actions.
|
|
|
The resource you are trying to delete has been modified recently. Please refresh the page to get the latest changes and try
again.
|
If you encounter this error while deleting a VA pod, contact Cisco TAC.
|














 Feedback
Feedback