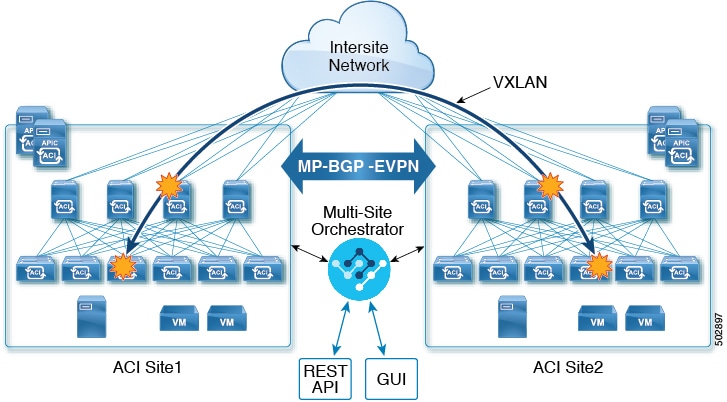
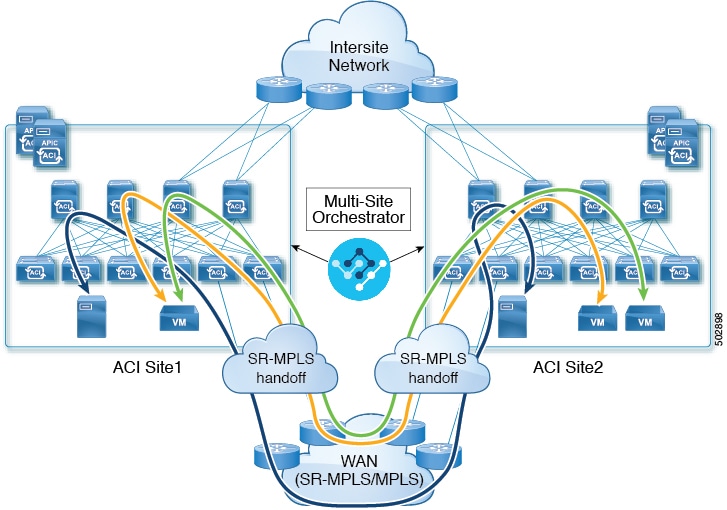
Configuring Infra Prerequisites and Guidelines
The following sections describe the steps necessary to configure the general as well as site-specific fabric Infra settings.
Before you proceed with Infra configuration, you must have configured and added the sites as described in previous sections, which includes:
-
Configuring each site's fabric access policies.
-
Configuring direct communication and routable subnets for sites with remote leaf switches.
In addition, keep in mind the following:
-
Any infrastructure changes such as adding and removing spine switches or spine node ID changes require a Multi-Site fabric connectivity information refresh described in the Refreshing Site Connectivity Information as part of the general Infra configuration procedures.
-
The Overlay Unicast TEP, Overlay Multicast TEP, and BGP-EVPN Router-IDs IP addresses assigned on the Orchestrator should not be taken from the address space of the original fabric's
InfraTEP pool or from the0.x.x.xrange.
 Feedback
Feedback