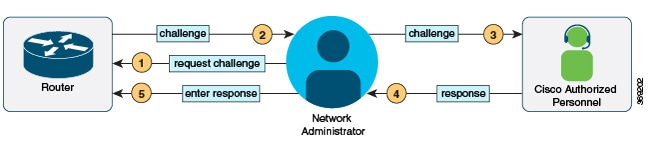
Restrictions for Consent Token
-
Consent Token is enabled by default and cannot be disabled.
-
After the challenge has been sent from the device, the response needs to be entered within 30 minutes. If it is not entered, the challenge expires and a new challenge must be requested.
-
A single response is valid only for one time for a corresponding challenge.
-
The maximum authorization timeout for root-shell access is seven days.
-
After a switchover event, all the existing Consent Token based authorizations would be treated as expired. You must then restart a fresh authentication sequence for service access.
-
Only Cisco authorized personnel have access to Consent Token response generation on Cisco's challenge signing server.
-
In System Shell access scenario, exiting the shell does not terminate authorization until the authorization timeout occurs or the shell authorization is explicitly terminated by the consent token terminate authorization command.
We recommend that you force terminate System Shell authorization by explicitly issuing the Consent Token terminate command once the purpose of System Shell access is complete.
 Feedback
Feedback