- Configuring LAN Interfaces
- Fast EtherChannel
- Configuring Serial Interfaces
- Lossless Compression R1 ATM Cell Switching and External BITS Clocking Source
- Network Analysis Module (NM-NAM)
- Minimal Disruptive Restart of VIP Cards
- Rate Based Satellite Control Protocol
- Configuring Virtual Interfaces
- Implementing Tunnels
- Dynamic Layer 3 VPNs with Multipoint GRE Tunnels
- MPLS VPN over mGRE
- IP Tunnel MIBs
- IF-MIBs
- Managing Dial Shelves
- Router-Shelf Redundancy for the Cisco AS5800
- Route-Switch-Controller Handover Redundancy on the Cisco AS5850
- Route Processor Redundancy Plus (RPR+)
- Synchronous Ethernet (SyncE) ESMC and SSM
- IPv6 GRE Tunnels in CLNS Networks
- ISATAP Tunnel Support for IPv6
- IP over IPv6 Tunnels
- IPv6 Automatic 6to4 Tunnels
- IPv6 over IPv4 GRE Tunnels
- IPv6 Automatic IPv4-Compatible Tunnels
- Manually Configured IPv6 over IPv4 Tunnels
Contents
- Network Analysis Module (NM-NAM)
- Finding Feature Information
- Prerequisites for the Network Analysis Module (NM-NAM)
- Restrictions for the Network Analysis Module (NM-NAM)
- Information About the Network Analysis Module (NM-NAM)
- NM-NAM Hardware
- NAM User Interface
- NAM Network Interfaces
- Analysis-Module Interface
- Internal NAM Interface
- External NAM Interface
- NM-NAM Operating Topologies and IP Address Assignments
- Management Traffic--Choose One of the NM-NAM Interfaces
- Monitored Traffic--Use One or Both of the NM-NAM Interfaces
- Sample Operating Topologies
- NAM Management Interface Is Internal and Analysis-Module Interface Is Assigned an IP Address
- NAM Management Interface Is Internal and Analysis-Module Interface Is IP Unnumbered
- NAM Management Interface Is External and Analysis-Module Interface Is IP Unnumbered
- NAM CLI
- NAM CLI Access
- NAM CLI Prompt
- Basic NAM CLI Commands
- NAM CLI Context-Sensitive Help
- How to Configure and Manage the Network Analysis Module (NM-NAM)
- Configuring the Analysis-Module Interface on the Router
- Examples
- What to Do Next
- Disabling AAA Login Authentication on the NAM Console Line
- What to Do Next
- Opening and Closing a NAM Console Session from the Router
- Examples
- Troubleshooting Tips
- What to Do Next
- Configuring the NM-NAM
- Examples
- What to Do Next
- Configuring a Static Route to the NAM Through the Analysis-Module Interface
- Examples
- What to Do Next
- Enabling NAM Packet Monitoring
- Example
- What to Do Next
- Enabling and Accessing the NAM Traffic Analyzer
- Examples
- What to Do Next
- Changing the NAM Root Password
- Examples
- Troubleshooting Tips
- Resetting the NAM Root Password to the Default Value
- Example
- Troubleshooting Tips
- What to Do Next
- Opening and Closing a Telnet or SSH Session to the NAM
- Examples
- Upgrading the NAM Software
- NAM Software Images
- Types of NAM Software Upgrades
- Prerequisites
- Upgrading the NAM Software--Patch
- Upgrading the NAM Software--Full Image
- Examples
- Troubleshooting Tips
- Configuration Examples for the Network Analysis Module (NM-NAM)
- NAM Management Interface Is Internal and Analysis-Module Interface Is Assigned an IP Address Example
- NAM Management Interface Is Internal and Analysis-Module Interface Is IP Unnumbered Example
- NAM Management Interface Is External and Analysis-Module Interface Is IP Unnumbered Example
- Additional References
- Command Reference
- Feature Information for Network Analysis Module (NM-NAM)
- Glossary
Network Analysis Module (NM-NAM)
The Network Analysis Module (NM-NAM) feature is a network module that monitors and analyzes network traffic for a system using extended Remote Monitoring (RMON) standards, RMON2, and other Management Information Bases (MIBs).
 Note | The Network Analysis Module (NAM) is available in multiple hardware forms for some Cisco routers and Catalyst switches. This document applies only to the NAM for branch routers, also known as modular access, multiservice, or integrated services routersNAM provides Layer 2 to Layer 7 visibility into network traffic for remote troubleshooting, real-time traffic analysis, application performance monitoring, capacity planning, and managing network-based services, including quality of service (QoS) and Voice over IP (VoIP). The NAM Traffic Analyzer is software that is embedded in the NM-NAM that gives you browser-based access to the RMON1, RMON2, DSMON, and voice monitoring features of the NAM. |
- Finding Feature Information
- Prerequisites for the Network Analysis Module (NM-NAM)
- Restrictions for the Network Analysis Module (NM-NAM)
- Information About the Network Analysis Module (NM-NAM)
- How to Configure and Manage the Network Analysis Module (NM-NAM)
- Configuration Examples for the Network Analysis Module (NM-NAM)
- Additional References
- Command Reference
- Feature Information for Network Analysis Module (NM-NAM)
- Glossary
Finding Feature Information
Your software release may not support all the features documented in this module. For the latest caveats and feature information, see Bug Search Tool and the release notes for your platform and software release. To find information about the features documented in this module, and to see a list of the releases in which each feature is supported, see the feature information table at the end of this module.
Use Cisco Feature Navigator to find information about platform support and Cisco software image support. To access Cisco Feature Navigator, go to www.cisco.com/go/cfn. An account on Cisco.com is not required.
Prerequisites for the Network Analysis Module (NM-NAM)
Install Cisco IOS Release 12.3(4)XD, Cisco IOS Release 12.3(7)T, or a later release.
Install the NM-NAM network module. Make sure that the network module is properly seated and that the EN (enable) and PWR (power) LEDs come on. Refer to the Cisco Network Modules Hardware Installation Guide.
For Cisco 2691, Cisco 3725, and Cisco 3745 routers only, make sure that the router runs ROM Monitor (ROMMON) Version 12.2(8r)T2 or a later version. This ROMMON version contains a fix that prevents the router from resetting all the network modules when it is reloaded. Refer to the ROM Monitor Download Procedures for Cisco 2691, Cisco, 3631, Cisco 3725, and Cisco 3745 Routers.
Restrictions for the Network Analysis Module (NM-NAM)
General Restrictions
Cisco IOS Release 12.3(4)XD, Cisco IOS Release 12.3(7)T, or a later release is required.
Network Analysis Module Release 3.2 or a later release is required.
Only one NM-NAM can be installed in the router at any time.
SNMPv3 is not supported.
Online insertion and removal (OIR), or hot swapping network modules, is supported on some platforms.
Traffic Monitoring Restrictions for the Internal NAM Interface
The following restrictions apply only to traffic that is monitored through the internal NAM interface:
Only IP traffic can be monitored.
The NAM Traffic Analyzer (web GUI) provides Layer 3 and higher layer information about the original packets. The Layer 2 header is modified by the router when it forwards the packets to the NAM, so the Layer 2 information that the NAM records is not applicable to the original packets.
When Network Address Translation (NAT) is used, the router forwards packets containing the NAT "inside" network addresses to the NAM.
When access control lists are used: The NAM does not monitor the following:
Information About the Network Analysis Module (NM-NAM)
 Note | For NM-NAM features and benefits, supported hardware and software, and other product information, refer to the Cisco Branch Router Network Analysis Module Data Sheet . |
- NM-NAM Hardware
- NAM User Interface
- NAM Network Interfaces
- NM-NAM Operating Topologies and IP Address Assignments
- NAM CLI
NM-NAM Hardware
For information on hardware installation and cable connections, refer to the Cisco Network Modules Hardware Installation Guide.
Specifications
|
Specification |
Description |
|---|---|
|
Processor |
500 Mhz Intel Mobile Pentium III |
|
SDRAM |
256 MB |
|
Internal disk storage |
NM-NAM 20 GB IDE |
|
Dimensions (H x W x D) |
1.55 x 7.10 x 7.2 in. (3.9 x 18.0 x 19.3 cm) |
|
Weight |
1.5 lb (0.7 kg) (maximum) |
|
Operating temperature |
3˚ to 104˚F (0˚ to 40˚C) |
|
Nonoperating temperature |
-40˚ to 185˚F (-40˚ to 85˚C) |
|
Humidity |
5 to 95% noncondensing |
|
Operating altitude |
0 to 10,000 ft (0 to 3,000 m) |
Faceplate and LEDs
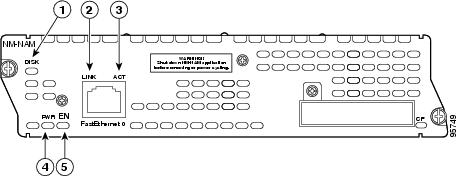
|
Callout |
LED |
Indicates |
|---|---|---|
|
1 |
DISK |
There is activity on the hard drive. |
|
2 |
LINK |
The Fast Ethernet connection is available to the network module. |
|
3 |
ACT |
There is activity on the Fast Ethernet connection. |
|
4 |
PWR |
Power is available to the network module. |
|
5 |
EN |
The module has passed self-test and is available to the router. |
NAM User Interface
The NAM has three interfaces;
Web GUI—The NAM Traffic Analyzer provides a browser-based GUI to configure and monitor the NAM.
CLI—A NAM-specific CLI is used to configure the NAM. It can be accessed through a NAM console session from the router or through Telnet or Secure Shell Protocol (SSH) over the network.
SNMP—The NAM supports SNMPv1 and SNMPv2 access to the SNMP agent in the router. The agents use different IP addresses and have independent communities.
NAM Network Interfaces
The NAM uses three interfaces for communication (see the figure below):
 Note | The NM-NAM does not have an external console port. To access the NAM console, open a NAM console session from the router or use Telnet or SSH over the network. The lack of an external console port on the NM-NAM means that the initial boot configuration is possible only through the router. |
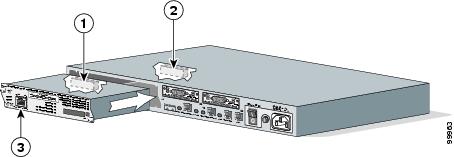
|
Callout |
Interface |
Location |
Configure and Manage From |
|---|---|---|---|
|
1 |
Internal NAM interface |
NM-NAM internal |
NAM CLI |
|
2 |
Analysis-Module interface |
Router internal |
Cisco IOS CLI |
|
3 |
External NAM interface |
NM-NAM faceplate |
NAM CLI |
Analysis-Module Interface
The Analysis-Module interface is used to access the NAM console for the initial configuration. After configuring the NAM IP parameters, the Analysis-Module interface is typically used only during NAM software upgrades and while troubleshooting if the NAM Traffic Analyzer is inaccessible.
Visible only to the Cisco IOS software on the router, the Analysis-Module interface is an internal Fast Ethernet interface on the router that connects to the internal NAM interface. The Analysis-Module interface is connected to the router’s Peripheral Component Interconnect (PCI) backplane, and all configuration and management of the Analysis-Module interface must be performed from the Cisco IOS CLI.
Internal NAM Interface
The internal NAM interface is used for monitoring traffic that passes through router interfaces. You can also select the internal NAM interface as the management interface for the NAM.
Visible only to the NAM software on the NM-NAM, the internal NAM interface is the Fast Ethernet interface on the NM-NAM that connects to the Analysis-Module interface on the router. The internal NAM interface is connected to the PCI bus on the NM-NAM, and all configuration and management of the internal NAM interface must be performed from the NAM software.
External NAM Interface
The external NAM interface can be used to monitor LAN traffic. You can also select the external NAM interface as the management interface for the NAM.
Visible only to the NAM software on the NM-NAM, the external NAM interface is the Fast Ethernet interface on the NM-NAM faceplate (see the first figure above). The external NAM interface supports data requests and data transfers from outside sources, and it provides direct connectivity to the LAN through an RJ-45 connector. All configuration and management of the external NAM interface must be performed from the NAM software.
NM-NAM Operating Topologies and IP Address Assignments
- Management Traffic--Choose One of the NM-NAM Interfaces
- Monitored Traffic--Use One or Both of the NM-NAM Interfaces
- Sample Operating Topologies
Management Traffic--Choose One of the NM-NAM Interfaces
Select either the internal or external NAM interface to handle management traffic such as IP, HTTP, SNMP, Telnet, and SSH. You cannot send management traffic through both NAM interfaces at the same time.
How you assign IP addresses on the NAM network interfaces depends on which NAM interface, internal or external, you use for management traffic. See the following sections:
Internal NAM Interface for Management Traffic--How to Assign IP Addresses
If you select the internal NAM interface to handle management traffic:
For the Analysis-Module interface (in Cisco IOS CLI), assign an IP address from a routable subnet. To conserve IP address space, you can configure the Analysis-Module as an IP unnumbered interface and borrow the IP address of another router interface, such as a Fast Ethernet or loopback interface. The borrowed IP address must come from a routable subnet.
For the NAM system (in NAM CLI), assign an IP address from the same subnet that is assigned to the Analysis-Module interface.
External NAM Interface for Management Traffic--How to Assign IP Addresses
If you select the external NAM interface to handle management traffic:
For the Analysis-Module interface (in Cisco IOS CLI), we recommend that you use the IP unnumbered interface configuration to borrow the IP address of another router interface. The subnet does not need to be routable.
For the NAM system (in NAM CLI), assign an IP address from the subnet that is connected to the external NAM interface.
Monitored Traffic--Use One or Both of the NM-NAM Interfaces
You can use either or both the internal and external NAM interfaces for monitoring traffic:
The same interface can be used for both management traffic and monitored traffic simultaneously.
Internal NAM Interface--Monitor LAN and WAN Traffic
When you monitor traffic through the internal NAM interface, you must enable NAM packet monitoring on each router interface that you want to monitor. NAM packet monitoring uses Cisco Express Forwarding (CEF) to send a copy of each packet that is received or sent out of the router interface to the NAM.
 Note | Some restrictions apply when monitoring traffic through the internal NAM interface. See the "Traffic Monitoring Restrictions for the Internal NAM Interface" section. |
Monitoring traffic through the internal NAM interface enables the NAM to see any encrypted traffic after it has already been decrypted by the router.
 Note | Traffic sent through the internal NAM interface--and the router’s Analysis-Module interface--uses router resources such as CPU, SDRAM bandwidth, and backplane PCI bandwidth. Therefore, we recommend that you use the internal NAM interface to monitor WAN interfaces, and use the external NAM interface to monitor LAN interfaces. |
External NAM Interface--Monitor LAN Traffic
Monitoring traffic through the external NAM interface does not impact router resources. Therefore, we recommend that you use the external NAM interface to monitor LAN traffic.
To monitor ports on Ethernet switching cards or modules (NM-16ESW-x , NMD-36ESW-x , HWIC-4ESW, or HWIC-D-9ESW), configure a Switched Port Analyzer (SPAN) session whose destination is the Ethernet switch port that connects to the external NAM interface. For more information about configuring SPAN for these cards and modules, refer to the following documents:
16- and 36-Port Ethernet Switch Module for Cisco 2600 Series, Cisco 3600 Series, and Cisco 3700 Series, Cisco IOS feature module
Cisco HWIC-4ESW and HWIC-D-9ESW EtherSwitch Interface Cards , Cisco IOS feature module
Sample Operating Topologies
In each of the following topologies, the router’s LAN interface is monitored through the external NAM interface, and the router’s WAN interface is monitored through the internal NAM interface:
To see sample configurations for the following topologies, see the Configuration Examples for the Network Analysis Module (NM-NAM).
- NAM Management Interface Is Internal and Analysis-Module Interface Is Assigned an IP Address
- NAM Management Interface Is Internal and Analysis-Module Interface Is IP Unnumbered
- NAM Management Interface Is External and Analysis-Module Interface Is IP Unnumbered
NAM Management Interface Is Internal and Analysis-Module Interface Is Assigned an IP Address
The figure below shows a sample topology, in which:
The internal NAM interface is used for management traffic.
IP addresses from the same routable subnet are assigned to the Analysis-Module interface and the NAM system.
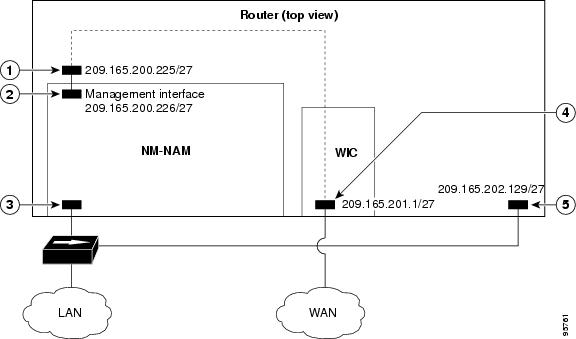
|
Callout |
Interface |
Location |
|---|---|---|
|
1 |
Analysis-Module interface |
Router internal |
|
2 |
Internal NAM interface (management) |
NM-NAM internal |
|
3 |
External NAM interface |
NM-NAM faceplate |
|
4 |
Serial interface |
WAN interface card (WIC) |
|
5 |
Fast Ethernet interface |
Router rear panel |
NAM Management Interface Is Internal and Analysis-Module Interface Is IP Unnumbered
The figure below shows a sample topology, in which:
The internal NAM interface is used for management traffic.
IP addresses from the same routable subnet are assigned to the Analysis-Module interface and the NAM system.
To conserve IP address space, the Analysis-Module interface is configured as IP unnumbered to borrow the IP address of the Fast Ethernet interface.
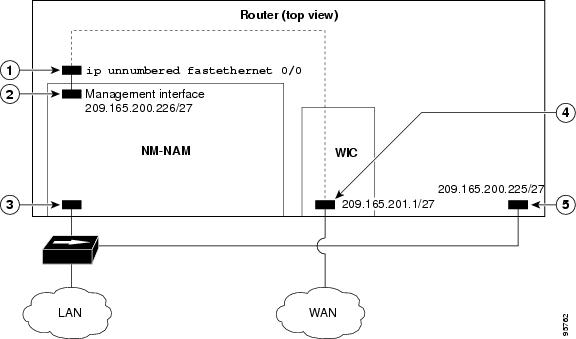
|
Callout |
Interface |
Location |
|---|---|---|
|
1 |
Analysis-Module interface |
Router internal |
|
2 |
Internal NAM interface (management) |
NM-NAM internal |
|
3 |
External NAM interface |
NM-NAM faceplate |
|
4 |
Serial interface |
WAN interface card (WIC) |
|
5 |
Fast Ethernet interface |
Router rear panel |
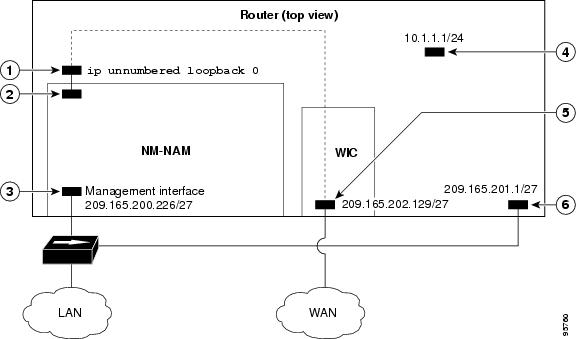
NAM Management Interface Is External and Analysis-Module Interface Is IP Unnumbered
The figure below shows a sample topology where:
The external NAM interface is used for management traffic.
The Analysis-Module interface is configured as IP unnumbered to borrow an IP address from the loopback interface.
The borrowed loopback interface IP address is not routable.
The NAM system is configured with an IP address from the LAN subnet that is connected to the external NAM interface.
|
Callout |
Interface |
Location |
|---|---|---|
|
1 |
Analysis-Module interface |
Router internal |
|
2 |
Internal NAM interface |
NM-NAM internal |
|
3 |
External NAM interface (management) |
NM-NAM faceplate |
|
4 |
Loopback interface |
Router internal |
|
5 |
Serial interface |
WAN interface card (WIC) |
|
6 |
Fast Ethernet interface |
Router rear panel |
NAM CLI
NAM CLI Access
There are three ways to access the NAM CLI:
Until you properly configure the NAM IP parameters, the only way to access the NAM CLI is by opening a NAM console session from the router.
NAM CLI Prompt
The NAM CLI prompt is root@nam-system-hostname# . For example, if the NAM system hostname is configured as "nam1," then the NAM CLI prompt appears as root@nam1# .
If the NAM system hostname has not yet been configured, the NAM CLI prompt is root@localhost# .
Basic NAM CLI Commands
The table below briefly describes the basic NAM CLI commands that are used for initial configuration and maintenance of the NM-NAM. For a complete description of all NAM CLI commands, refer to the Network Analysis Module Command Reference for your NAM software release.
 Note | Although NAM CLI commands appear similar to Cisco IOS commands, the commands described in the table below operate in the NAM CLI only. |
|
NAM CLI Command |
Purpose |
|---|---|
|
exsession on |
Enables outside logins (Telnet). |
|
exsession on ssh |
Enables outside logins (SSH). |
|
ip address |
Sets the system IP address. |
|
ip broadcast |
Sets the system broadcast address. |
|
ip domain |
Sets the system domain name. |
|
ip gateway |
Sets the system default gateway address. |
|
ip host |
Sets the system hostname. |
|
ip http secure server enable |
Enables the secure HTTP server. |
|
ip http server enable |
Enables the HTTP server. |
|
ip interface external |
Selects the external NAM interface for management traffic. |
|
ip interface internal |
Selects the internal NAM interface for management traffic. |
|
ip nameserver |
Sets the system name server address. |
|
password root |
Sets a new password to access the root (read/write) level of NAM. |
|
patch |
Downloads and installs a software patch. |
|
ping |
Checks connectivity to a network device. |
|
show ip |
Displays the NAM IP parameters. |
NAM CLI Context-Sensitive Help
The table below shows how to use the NAM CLI context-sensitive help.
|
NAM CLI Command |
Purpose |
|---|---|
(prompt
)# ?
or
(prompt
)# help
|
Displays a list of commands available for the command mode. |
(prompt
)# abbreviated-command-entry
<Tab>
|
Lists commands in the current mode that begin with a particular character string. |
(prompt
)# command?
|
Lists the available syntax options (arguments and keywords) for the command. |
(prompt
)# command
keyword ?
|
Lists the next available syntax option for the command. |
How to Configure and Manage the Network Analysis Module (NM-NAM)
- Configuring the Analysis-Module Interface on the Router
- Disabling AAA Login Authentication on the NAM Console Line
- Opening and Closing a NAM Console Session from the Router
- Configuring the NM-NAM
- Configuring a Static Route to the NAM Through the Analysis-Module Interface
- Enabling NAM Packet Monitoring
- Enabling and Accessing the NAM Traffic Analyzer
- Changing the NAM Root Password
- Resetting the NAM Root Password to the Default Value
- Opening and Closing a Telnet or SSH Session to the NAM
- Upgrading the NAM Software
Configuring the Analysis-Module Interface on the Router
This section describes how to configure the Analysis-Module interface on the router. For general information on the Analysis-Module interface, see the Analysis-Module Interface.
For information on assigning the IP address of the Analysis-Module interface, see the NM-NAM Operating Topologies and IP Address Assignments.
1.
enable
2.
configure
terminal
3.
interface
type
number
4.
ip
address
ip-address
mask
5.
interface
analysis-module
slot
/0
7.
no
shutdown
8.
end
DETAILED STEPS
To avoid losing your configuration at the next system reload or power cycle, save the running configuration to the startup configuration by entering the
copy
run
start command in privileged EXEC mode.

Tip
Examples
This section provides the following examples:
Configuring the Analysis-Module Interface--Routable Subnet: Example
In the following example, the Analysis-Module interface is configured with a routable IP address. The NM-NAM is installed in router slot 2.
Configuring the Analysis-Module Interface--IP Unnumbered with Routable Subnet: Example
In the following example, the Analysis-Module interface is IP unnumbered and borrows the IP address of the Fast Ethernet interface. The IP address is from a routable subnet, and the NM-NAM is installed in router slot 1.
! interface FastEthernet 0/0 ip address 209.165.202.129 255.255.255.224 no shutdown ! interface Analysis-Module 1/0 ip unnumbered FastEthernet 0/0 no shutdown !
Configuring the Analysis-Module Interface--IP Unnumbered with Subnet That Is Not Routable: Example
In the following example, the Analysis-Module interface is IP unnumbered and borrows a loopback interface IP address that is not routable. The NM-NAM is installed in router slot 3.
! interface loopback 0 ip address 10.20.30.40 255.255.255.0 ! interface Analysis-Module 3/0 ip unnumbered loopback 0 no shutdown !
Sample Output for the show ip interface brief Command
Router# show ip interface brief Interface IP-Address OK? Method Status Protocol FastEthernet0/0 172.20.105.213 YES NVRAM up up FastEthernet0/1 172.20.105.53 YES NVRAM up up Analysis-Module2/0 10.1.1.1 YES manual up up Router#
What to Do Next
If you configured authentication, authorization, and accounting (AAA) on your router, then proceed to the Disabling AAA Login Authentication on the NAM Console Line.
Otherwise, proceed to the Opening and Closing a NAM Console Session from the Router.
Disabling AAA Login Authentication on the NAM Console Line
If you configured authentication, authorization, and accounting (AAA) on your router, then you may have to log in twice to open a NAM console session from the router: first with your AAA username and password, and second with the NAM login and password.
If you do not want to log in twice to open a NAM console session from the router, then disable AAA login authentication on the router’s NAM console line by performing the steps in this section.
Note, however, that if your router contains both the NM-NAM and the NM-CIDS, the Cisco intrusion detection system network module, then AAA can be a useful tool for centrally controlling access to both network modules. For information about AAA, refer to the Cisco IOS Security Configuration Guide.
1.
enable
2.
configure
terminal
3.
aaa
authentication
login
list-name
none
4.
line
number
5.
login
authentication
list-name
6.
end
7.
show
running-config
DETAILED STEPS
What to Do Next
Proceed to the Opening and Closing a NAM Console Session from the Router.
Opening and Closing a NAM Console Session from the Router
This section describes how to open and close a NAM console session from the router.
1.
enable
2.
service-module
analysis-module
slot
/0
session
4. At the login prompt, enter root.
6. Perform the tasks that you need to perform in the NAM CLI. When you want to end the NAM console session and return to the Cisco IOS CLI, complete Step 7 through Step 10.
7.
exit
8. Hold Ctrl-Shift and press 6. Release all keys, and then press x.
9.
disconnect
10. Press Enter.
DETAILED STEPS
| Command or Action | Purpose | |
|---|---|---|
| Step 1 |
enable
Example: Router> enable |
Enables privileged EXEC mode. |
| Step 2 |
service-module
analysis-module
slot
/0
session
Example: Router# service-module analysis-module 1/0 session Example: Router# service-module analysis-module 1/0 session clear Example: [confirm] Example: [OK] Example: Router# service-module analysis-module 1/0 session |
Establishes a console session with the NAM. |
| Step 3 | Do one of the following:
Example: Trying 10.1.1.1, 2065 ... Open Example: <Press Return> Example: Example: Cisco Network Analysis Module (NM-NAM) Example: Example: nam1.cisco.com login: Example: Trying 10.1.1.1, 2065... Open Example: User Access Verification Example: Example: Username: myaaausername Example: Password: <myaaapassword> Example: Cisco Network Analysis Module (NM-NAM) Example: Example: nam1.cisco.com login: |
Activates the NAM console line. or Completes AAA login authentication and activates the NAM console line. |
| Step 4 | At the login prompt, enter
root.
Example: login: root |
Accesses the root (read/write) level of NAM. |
| Step 5 | Do one of the following:
Example: Password: <root> |
-- |
| Step 6 | Perform the tasks that you need to perform in the NAM CLI. When you want to end the NAM console session and return to the Cisco IOS CLI, complete Step 7 through Step 10. |
For initial configuration tasks, see the Configuring the NM-NAM. For help using NAM CLI commands, see the NAM CLI Context-Sensitive Help. |
| Step 7 |
exit
Example: root@localhost(sub-custom-filter-capture)# exit Example: root@localhost# exit Example: Example: login: |
Logs out of the NAM system or leaves a subcommand mode. |
| Step 8 | Hold
Ctrl-Shift and press
6. Release all keys, and then press
x.
Example: login: <suspend keystroke> Example: Router# |
Suspends and closes the Telnet session. |
| Step 9 |
disconnect
Example: Router# disconnect |
Disconnects a line. |
| Step 10 | Press
Enter.
Example: Closing connection to 10.20.30.40 [confirm] <Enter> |
Confirms that you want to disconnect the line. |
Examples
This section provides the following examples:
Opening and Closing a NAM Console Session When AAA Authentication Is Not Configured or Is Disabled on the NAM Console Line: Example
In the following example, a NAM console session is opened and closed from the router. The NM-NAM is installed in router slot 2.
Router# service-module analysis-module 2/0 session Trying 10.1.1.1, 2065 ... Open Cisco Network Analysis Module (NM-NAM) nam1.cisco.com login: root Password: <password> Terminal type: vt100 Cisco Network Analysis Module (NM-NAM) Console, 3.2 Copyright (c) 1999-2003 by cisco Systems, Inc. WARNING! Default password has not been changed! root@nam1.cisco.com# root@nam1.cisco.com# exit Cisco Network Analysis Module (NM-NAM) nam1.cisco.com login: <suspend keystroke> Router# disconnect Closing connection to 10.1.1.1 [confirm] <Enter> Deleting login session
Opening and Closing a NAM Console Session When AAA Authentication Is Configured and Enabled on the NAM Console Line: Example
In the following example, a NAM console session is opened and closed from the router. The NM-NAM is installed in router slot 2.
Router# service-module analysis-module 2/0 session Trying 10.1.1.1, 2065 ... Open User Access Verification Username: myaaausername Password: <myaaapassword> Cisco Network Analysis Module (NM-NAM) nam1.cisco.com login: root Password: <nampassword> Terminal type: vt100 Cisco Network Analysis Module (NM-NAM) Console, 3.2 Copyright (c) 1999-2003 by cisco Systems, Inc. WARNING! Default password has not been changed! root@nam1.cisco.com# root@nam1.cisco.com# exit Cisco Network Analysis Module (NM-NAM) nam1.cisco.com login: <suspend keystroke> Router# disconnect Closing connection to 10.1.1.1 [confirm] <Enter> Deleting login session
Troubleshooting Tips
Make sure that the NAM console line is clear by entering the service-module analysis-module slot /0 session clear command in privileged EXEC mode.
What to Do Next
Proceed to the Configuring the NM-NAM section.
Configuring the NM-NAM
This section describes how to configure the NM-NAM to establish network connectivity and configure IP parameters. This task must be performed from the NAM CLI. For more advanced NAM configuration, use the NAM Traffic Analyzer (web GUI) or refer to the Network Analysis Module Command Reference for your NAM software release.
For information on assigning IP addresses, see the NM-NAM Operating Topologies and IP Address Assignments.
Before performing this task, access the NAM console by performing Step 1 through Step 5 in the Opening and Closing a NAM Console Session from the Router.
1.
ip
interface
{internal |
external}
2.
ip
address
ip-address subnet-mask
3.
ip
broadcast
broadcast-address
4.
ip
gateway
ip-address
6.
ip
domain
name
7.
ip
host
name
8.
ip
nameserver
ip-address [ip-address ][ip-address ]
9.
ping
{host |
ip-address }
10.
show
ip
DETAILED STEPS
Examples
This section provides the following examples:
Configuring the NM-NAM: Example
In the following example, the external NAM interface is used for management traffic. The HTTP server and Telnet access are enabled. The resulting NAM CLI prompt is root@nam1.cisco.com# .
! ip address 172.20.105.215 255.255.255.192 ! ip host "nam1" ! ip domain "cisco.com" ! ip gateway 172.20.105.210 ! ip broadcast 10.255.255.255 ! ip nameserver 209.165.201.29 ! ip interface external ! ip http server enable ! exsession on !
Checking Network Connectivity with Ping: Example
root@nam1.cisco.com# ping 172.20.105.213 PING 172.20.105.213 (172.20.105.213) from 172.20.105.215 : 56(84) bytes of data. 64 bytes from 172.20.105.213: icmp_seq=0 ttl=255 time=353 usec 64 bytes from 172.20.105.213: icmp_seq=1 ttl=255 time=289 usec 64 bytes from 172.20.105.213: icmp_seq=2 ttl=255 time=284 usec 64 bytes from 172.20.105.213: icmp_seq=3 ttl=255 time=283 usec 64 bytes from 172.20.105.213: icmp_seq=4 ttl=255 time=297 usec --- 172.20.105.213 ping statistics --- 5 packets transmitted, 5 packets received, 0% packet loss round-trip min/avg/max/mdev = 0.283/0.301/0.353/0.028 ms root@nam1.cisco.com#
Sample Output for the show ip NAM CLI Command
root@nam1.cisco.com# show ip IP address: 172.20.105.215 Subnet mask: 255.255.255.192 IP Broadcast: 10.255.255.255 IP Interface: External DNS Name: nam1.cisco.com Default Gateway: 172.20.105.210 Nameserver(s): 209.165.201.29 HTTP server: Enabled HTTP secure server: Disabled HTTP port: 80 HTTP secure port: 443 TACACS+ configured: No Telnet: Enabled SSH: Disabled root@nam1.cisco.com#
What to Do Next
If you selected the internal NAM interface to handle management traffic in Step 1, then proceed to the Configuring a Static Route to the NAM Through the Analysis-Module Interface.
If you plan to monitor traffic through the internal NAM interface, then proceed to the Enabling NAM Packet Monitoring.
If you do not plan to monitor traffic through the internal NAM interface, then proceed to the Enabling and Accessing the NAM Traffic Analyzer.
Configuring a Static Route to the NAM Through the Analysis-Module Interface
This section describes how to ensure that the router can route packets to the NAM by configuring a static route through the Analysis-Module interface.
If you select the internal NAM interface to handle management traffic, then configuring a static route to the NAM through the Analysis-Module interface is:
Required when the Analysis-Module interface is IP unnumbered.
Recommended when the Analysis-Module interface is assigned a unique IP address.
If you select the external NAM interface to handle management traffic, then you do not need to perform this task. Proceed to the What to Do Next.
1.
enable
2.
configure
terminal
3.
ip
route
nam-ip-address
mask
analysis-module
slot
/
unit
4.
end
5.
ping
{nam-ip-address | nam-hostname}
DETAILED STEPS
| Command or Action | Purpose | |
|---|---|---|
| Step 1 |
enable
Example: Router> enable |
Enables privileged EXEC mode.
|
| Step 2 |
configure
terminal
Example: Router# configure terminal |
Enters global configuration mode. |
| Step 3 |
ip
route
nam-ip-address
mask
analysis-module
slot
/
unit
Example: Router(config)# ip route 172.20.105.215 255.255.255.192 analysis-module 1/0 |
Establishes a static route to the NAM. |
| Step 4 |
end
Example: Router(config-if)# end Example: Router# |
Returns to privileged EXEC mode. |
| Step 5 |
ping
{nam-ip-address | nam-hostname} Example: Router# ping 172.20.105.215 |
Verifies network connectivity to the NAM. |
Examples
This section provides the following examples:
Configuring a Static Route to the NAM Through the Analysis-Module Interface: Example
In the following example, a static route is configured to the NAM whose system IP address is 172.20.105.215. The NM-NAM is installed in router slot 1.
! ip route 172.20.105.215 255.255.255.192 analysis-module 1/0 ! interface FastEthernet 0/0 ip address 209.165.202.129 255.255.255.224 no shutdown ! interface Analysis-Module 1/0 ip unnumbered FastEthernet 0/0 no shutdown !
Verifying Network Connectivity with Ping: Example
In the following example, entering the ping command verifies network connectivity to the NAM with IP address 172.20.105.215.
Router# ping 172.20.105.215 Type escape sequence to abort. Sending 5, 100-byte ICMP Echos to 172.20.105.215, timeout is 2 seconds: !!!!! Success rate is 100 percent (5/5), round-trip min/avg/max = 1/1/1 ms Router#
What to Do Next
If you plan to monitor traffic through the internal NAM interface, then proceed to the Enabling NAM Packet Monitoring.
If you do not plan to monitor traffic through the internal NAM interface, then proceed to the Enabling and Accessing the NAM Traffic Analyzer.
Enabling NAM Packet Monitoring
This section describes how to enable NAM packet monitoring on router interfaces that you want to monitor through the internal NAM interface.
When you enable NAM packet monitoring on an interface, CEF sends an extra copy of each IP packet that is received or sent out on that interface to the NAM through the Analysis-Module interface on the router and the internal NAM interface.
1.
enable
2.
configure
terminal
3.
ip
cef
5.
analysis-module
monitoring
6. Repeat Step 4 and Step 5 for each interface that you want the NAM to monitor through the internal NAM interface.
7.
end
8.
show
running-config
DETAILED STEPS
| Command or Action | Purpose | |
|---|---|---|
| Step 1 |
enable
Example: Router> enable |
Enables privileged EXEC mode. |
| Step 2 |
configure
terminal
Example: Router# configure terminal |
Enters global configuration mode. |
| Step 3 |
ip
cef
Example: Router(config)# ip cef |
Enables the CEF switching path. |
| Step 4 | Do one of the following:
Example: Router(config)# interface serial 0/0 |
Selects an interface for configuration. |
| Step 5 |
analysis-module
monitoring
Example: Router(config-if)# analysis-module monitoring |
Enables NAM packet monitoring on the interface. |
| Step 6 | Repeat Step 4 and Step 5 for each interface that you want the NAM to monitor through the internal NAM interface. |
-- |
| Step 7 |
end
Example: Router(config-if)# end Example: Router# |
Returns to privileged EXEC mode. |
| Step 8 |
show
running-config
Example: Router# show running-config |
Displays the contents of the currently running configuration file. |
Example
This section provides the following example:
Enabling NAM Packet Monitoring: Example
In the following example, NAM packet monitoring is enabled on the serial interfaces:
interface Serial 0/0 ip address 172.20.105.213 255.255.255.240 ip route-cache flow speed auto full-duplex analysis-module monitoring no mop enabled ! interface Serial 0/1 ip address 172.20.105.53 255.255.255.252 ip route-cache flow duplex auto speed auto analysis-module monitoring ! interface Analysis-Module 2/0 ip address 10.1.1.1 255.255.255.0 hold-queue 60 out !
What to Do Next
This task must be repeated on the router on the other side of the satellite link. Substitute the sample IP addresses, hostnames, and other parameters for the appropriate values on the second router.
After the task is completed on the router on the other side of the satellite link, proceed to the Verifying RBSCP Tunnel Configuration and Operation.
Enabling and Accessing the NAM Traffic Analyzer
This section describes how to enable and access the NAM Traffic Analyzer (web GUI).
Make sure that your web browser supports your NAM software release. For a list of supported browsers, refer to the NAM software release notes.
If you plan to use the HTTP secure server (HTTPs), then you must first download and install the NAM software K9 crypto patch. Until you install the patch, the ip http secure commands are disabled. You can download the NAM software K9 crypto patch from Cisco.com.
 Note | You can use the HTTP server or the HTTP secure server, but you cannot use both simultaneously. |
- Open a NAM console session from the router. See the Opening and Closing a NAM Console Session from the Router.
- Open a Telnet or SSH session to the NAM. See the Opening and Closing a Telnet or SSH Session to the NAM.
- ip http server enable
- ip http secure server enable
- Enter a web username.
- Press Return to enter the default web username "admin".
1.
Do one of the following:
2.
Do one of the following:
3.
Do one of the following:
4. Enter a password.
5. Enter the password again.
6. On your PC, open a web browser.
7. In the web browser, enter the NAM system IP address or hostname as the URL.
DETAILED STEPS
| Command or Action | Purpose | |
|---|---|---|
| Step 1 | Do one of the following:
|
Accesses the NAM CLI. |
| Step 2 | Do one of the following:
Example: root@localhost# ip http server enable Example: root@localhost# ip http secure server enable |
Enables the HTTP server. or Enables the HTTP secure server (HTTPs). |
| Step 3 | Do one of the following:
Example: Please enter a web administrator user name [admin]: joeadmin Example: Please enter a web administrator user name [admin]: <cr> |
Configures a web username.
|
| Step 4 |
Enter a password. Example: New password: <adminpswd> |
Configures a password for the web username. |
| Step 5 |
Enter the password again. Example: Confirm password: <adminpswd> |
Confirms the password for the web username. |
| Step 6 | On your PC, open a web browser. |
-- |
| Step 7 |
In the web browser, enter the NAM system IP address or hostname as the URL. Example: http://172.20.105.215/ Example: https://172.20.105.215/ Example: http://nam1/ |
Opens the NAM Traffic Analyzer in your web browser.
|
Examples
This section provides the following examples:
Enabling the NAM Traffic Analyzer: Example
root@nam1# ip http server enable Enabling HTTP server... No web users are configured. Please enter a web administrator user name [admin]: <cr> New password: <pswd> Confirm password: <pswd> User admin added. Successfully enabled HTTP server. root@nam1#
Accessing the NAM Traffic Analyzer: Example
The figure below shows the NAM Traffic Analyzer login page that appears when you enter the NAM system IP address or hostname as the URL in a web browser.

What to Do Next
For information on the NAM Traffic Analyzer, refer to the User Guide for the Network Analysis Module Traffic Analyzer for your NAM software release. This document is available on Cisco.com and as online help within the NAM Traffic Analyzer application.
Changing the NAM Root Password
This section describes how to set a new password to access the root (read/write) level of NAM, where you can enter NAM CLI commands. The factory-set default root password is "root".
Before performing this task, access the NAM console by performing Step 1 through Step 5 in the Opening and Closing a NAM Console Session from the Router.
1.
password
root
2. Enter the new password.
3. Enter the new password again.
4.
exit
5. At the login prompt, enter root.
6. At the password prompt, enter your password.
DETAILED STEPS
| Command or Action | Purpose | |
|---|---|---|
| Step 1 |
password
root
Example: root@localhost.cisco.com# password root |
Starts the process of changing the NAM’s root (read/write) level password. |
| Step 2 | Enter the new password.
Example: New UNIX password: <password> |
Enters the new password. |
| Step 3 | Enter the new password again.
Example: Retype new UNIX password: <password> |
Confirms the new password. |
| Step 4 |
exit
Example: root@localhost# exit |
Logs out of the NAM system. |
| Step 5 | At the login prompt, enter
root.
Example: login: root |
Accesses the root (read/write) level of NAM. |
| Step 6 | At the password prompt, enter your password.
Example: Password: <password> |
Verifies that the new password is accepted. |
Examples
This section provides the following examples:
Changing the NAM Root Password: Example
root@nam1.cisco.com# password root Changing password for user root New UNIX password: <rtpswd> Retype new UNIX password: <rtpswd> passwd:all authentication tokens updated successfully root@nam1.cisco.com# root@nam1.cisco.com# exit
Verifying the NAM Root Password: Example
nam1.cisco.com login: root Password: <rtpswd> Terminal type: vt100 Cisco Network Analysis Module (NM-NAM) Console, 3.2 Copyright (c) 1999-2003 by cisco Systems, Inc. root@nam1.cisco.com# root@nam1.cisco.com# exit
Troubleshooting Tips
If you forget the NAM root password, see the Resetting the NAM Root Password to the Default Value.
Resetting the NAM Root Password to the Default Value
This section describes how to reset the NAM root password to the default value of "root". Use this procedure when you cannot remember the NAM root password but need to access the NAM CLI.
 Note | This procedure requires that you reload the NAM software. |
1.
enable
2.
service-module
analysis-module
slot
/0
reload
3.
y
4.
service-module
analysis-module
slot
/0
session
5. When prompted, enter *** to change the boot configuration.
6.
boot
flash
7. When prompted to select from the helper menu, enter 6.
8. When prompted to select from the helper menu, enter r.
9.
y
10. Hold Ctrl-Shift and press 6. Release all keys, and then press x.
11.
disconnect
12. Press Enter.
DETAILED STEPS
| Command or Action | Purpose | |
|---|---|---|
| Step 1 |
enable
Example: Router> enable |
Enables privileged EXEC mode. |
| Step 2 |
service-module
analysis-module
slot
/0
reload
Example: Router# service-module analysis-module 1/0 reload |
Reloads the software on the NM-NAM. |
| Step 3 |
y
Example: Do you want to proceed with reload?[confirm] y |
Confirms that you want to proceed with the NAM software reload. |
| Step 4 |
service-module
analysis-module
slot
/0
session
Example: Router# service-module analysis-module 1/0 session Example: Router# service-module analysis-module 1/0 session clear Example: [confirm] Example: [OK] Example: Router# service-module analysis-module 1/0 session |
Establishes a console session with the NAM. |
| Step 5 | When prompted, enter
*** to change the boot configuration.
Example: Please enter '***' to change boot configuration: *** |
Interrupts the boot loader. |
| Step 6 |
boot
flash
Example: ServicesEngine boot-loader> boot flash |
Loads the NAM helper image. |
| Step 7 | When prompted to select from the helper menu, enter
6.
Example: Selection [12345678rh]: 6 |
Selects the menu option to reset the root password to the default value of "root". |
| Step 8 | When prompted to select from the helper menu, enter
r.
Example: Selection [12345678rh]:r |
Selects the menu option to exit the helper and reset the NAM. |
| Step 9 |
y
Example: About to exit and reset Services Engine. Example: Are you sure? [y/N] y |
Confirms that you want to exit the helper and reset the NAM. |
| Step 10 | Hold
Ctrl-Shift and press
6. Release all keys, and then press
x.
Example: login: <suspend keystroke> Example: Router# |
Suspends and closes the Telnet session. |
| Step 11 |
disconnect
Example: Router# disconnect |
Disconnects a line. |
| Step 12 | Press
Enter.
Example: Closing connection to 10.20.30.40 [confirm] <Enter> |
Confirms that you want to disconnect the line. |
Example
This section provides the following example:
Resetting the NAM Root Password to the Default Value: Example
Router# service-module analysis-module 1/0 reload Do you want to proceed with reload?[confirm] y Trying to reload Service Module Analysis-Module1/0. Router# service-module analysis-module 1/0 session Trying 172.20.104.87, 2033 ... Open . <debug output omitted> . Booting from flash..., please wait. [BOOT-ASM] 7 Please enter '***' to change boot configuration: *** ServicesEngine Bootloader Version :1.0.6aN ServicesEngine boot-loader> boot flash . <debug output omitted> . ============================================================================== Cisco Systems, Inc. Services engine helper utility for NM-NAM Version 1.1(1) [200311111641] ----- Main menu 1 - Download application image and write to HDD 2 - Download application image and reformat HDD 3 - Download bootloader and write to flash 4 - Download helper and write to flash 5 - Display software versions 6 - Reset application image CLI passwords to default 7 - Change file transfer method (currently ftp/http) 8 - Show upgrade log 9 - Send Ping r - Exit and reset Services Engine h - Exit and shutdown Services Engine Selection [123456789rh]: 6 Restored default CLI passwords of application image. ============================================================================== Cisco Systems, Inc. Services engine helper utility for NM-NAM Version 1.1(1) [200311111641] ----- Main menu 1 - Download application image and write to HDD 2 - Download application image and reformat HDD 3 - Download bootloader and write to flash 4 - Download helper and write to flash 5 - Display software versions 6 - Reset application image CLI passwords to default 7 - Change file transfer method (currently ftp/http) 8 - Show upgrade log 9 - Send Ping r - Exit and reset Services Engine h - Exit and shutdown Services Engine Selection [123456789rh]: r About to exit and reset Services Engine. Are you sure? [y/N] y INITSending all processes the TERM signal... Sending all processes the KILL signal... Unmounting file systems: Please stand by while rebooting the system... Restarting system. . <debug output omitted> . Cisco Network Analysis Module (NM-NAM) nam1.cisco.com login: <suspend keystroke> Router# Router# disconnect Closing connection to 10.1.1.1 [confirm] <Enter> Deleting login session
Troubleshooting Tips
If you have trouble opening a NAM console session from the router, make sure that the NAM console line is clear by entering the service-module analysis-module slot /0 session clear command in privileged EXEC mode.
What to Do Next
Verify that the default root password of "root" is accepted by performing Step 1 through Step 5 in the Opening and Closing a NAM Console Session from the Router.
To change the NAM root password, see the Changing the NAM Root Password.
Opening and Closing a Telnet or SSH Session to the NAM
This section describes how to open and close a Telnet or SSH session to the NAM. This task is not commonly performed, because you would typically use the NAM Traffic Analyzer (web GUI) to monitor and maintain the NAM. If, however, you cannot access the NAM Traffic Analyzer, then you might want to use Telnet or SSH to troubleshoot from the NAM CLI.
If your NM-NAM is not properly configured for Telnet or SSH access (see the following Prerequisites section), then you can open a Telnet session to the router in which the NM-NAM is installed, and then open a NAM console session from the router. See the Opening and Closing a NAM Console Session from the Router.
Configure the NAM system IP address. Optionally, set the NAM system hostname. See the Configuring the NM-NAM.
Verify NAM network connectivity by performing one of the following ping tests:
Install the NAM software K9 crypto patch, which you can download from Cisco.com.
Enter the exsession on ssh NAM CLI command. See Step 5 of the Configuring the NM-NAM.
2. At the login prompt, enter root.
4. Perform the tasks that you need to perform in the NAM CLI. When you want to end the Telnet or SSH session to the NAM and return to the Cisco IOS CLI, complete Step 5 and Step 6 .
5.
exit
6.
logout
DETAILED STEPS
| Command or Action | Purpose | |
|---|---|---|
| Step 1 | Do one of the following:
Example: Router# telnet 10.20.30.40 Example: Router# ssh 10.20.30.40 |
Logs in to a host that supports Telnet. or Starts an encrypted session with a remote networking device. |
| Step 2 | At the login prompt, enter
root.
Example: login: root |
Accesses the root (read/write) level of NAM. |
| Step 3 | Do one of the following:
Example: Password: root |
-- |
| Step 4 | Perform the tasks that you need to perform in the NAM CLI. When you want to end the Telnet or SSH session to the NAM and return to the Cisco IOS CLI, complete Step 5 and Step 6 . |
For help using NAM CLI commands, see the NAM CLI Context-Sensitive Help. |
| Step 5 |
exit
Example: root@localhost(sub-custom-filter-capture)# exit Example: root@localhost# |
Leaves a subcommand mode. |
| Step 6 |
logout
Example: root@localhost# logout Example: Example: Connection closed by foreign host. |
Logs out of the NAM system. |
Examples
This section provides the following examples:
Opening and Closing a Telnet Session to the NAM Using the NAM System IP Address: Example
Router> telnet 172.20.105.215 Trying 172.20.105.215 ... Open Cisco Network Analysis Module (NM-NAM) login: root Password: <password> Terminal type: vt100 Cisco Network Analysis Module (NM-NAM) Console, 3.2 Copyright (c) 1999-2003 by cisco Systems, Inc. WARNING! Default password has not been changed! root@nam.cisco.com# root@nam.cisco.com# logout [Connection to 172.20.105.215 closed by foreign host] Router>
Opening and Closing an SSH Session to the NAM Using the NAM System Hostname: Example
host [/home/user] ssh -l root nmnam2 root@nmnam2’s password: <password> Terminal type: vt100 Cisco Network Analysis Module (NM-NAM) Console, 3.2 Copyright (c) 1999-2003 by cisco Systems, Inc. WARNING! Default password has not been changed! root@nmnam2.cisco.com# root@nmnam2.cisco.com# logout Connection to nmnam2 closed. host [/home/user]
Upgrading the NAM Software
This section describes how to upgrade the NAM software. This task is performed from the NAM CLI.
- NAM Software Images
- Types of NAM Software Upgrades
- Prerequisites
- Upgrading the NAM Software--Patch
- Upgrading the NAM Software--Full Image
- Examples
- Troubleshooting Tips
NAM Software Images
The NM-NAM contains three NAM software images:
NAM application image on the hard drive--Source of the NAM Traffic Analyzer and NAM CLI
Helper image in flash memory--Used to recover or upgrade NAM software images
Bootloader image in flash memory--Used to specify whether to boot the NAM application image or the helper image
Types of NAM Software Upgrades
NAM software upgrades are available in two forms:
Patches--Incremental updates to software releases that are installed with the patch NAM CLI command. Patches are available only for the NAM application image.
Images--Full image releases that are installed from the helper image. Full image upgrades are typically used to update the NAM application image, but if necessary and recommended by technical support, you can also use the helper image to upgrade the bootloader image or helper image.
Prerequisites
Download the NAM software image from Cisco.com, and copy the image to an FTP server.
Before performing this task, access the NAM console by completing Step 1 through Step 5 in the Opening and Closing a NAM Console Session from the Router.
Perform one of the following tasks in this section, depending on whether you are adding a patch to your NAM application or are performing a full software image upgrade:
Upgrading the NAM Software--Patch
Perform this task to add a patch to your NAM application image. This task is performed from the NAM CLI.
- patch ftp://user:password@host/full-path/filename
- patch ftp://user@host/full-path/filename
1.
Do one of the following:
2.
show
patches
DETAILED STEPS
| Command or Action | Purpose | |
|---|---|---|
| Step 1 | Do one of the following:
Example: root@nam1.cisco.com# patch ftp://person:mypwd@examplehost/dir/subdir/nam-app.3-2.cryptoK9.patch.1-0.bin Example: root@nam1.cisco.com# patch ftp://person@examplehost/dir/subdir/nam-app.3-2.cryptoK9.patch.1-0.bin Example: Example: Proceeding with installation. Please do not interrupt. Example: If installation is interrupted, please try again. Example: Example: Downloading nam-app.3-2.cryptoK9.patch.1-0.bin. Please wait... Example: Password for person@examplehost: <mypwd> |
Downloads and installs a software patch.
|
| Step 2 |
show
patches
Example: root@nam1.cisco.com# show patches |
Displays all installed patches.
|
Upgrading the NAM Software--Full Image
Perform this task to upgrade one of your NAM software images to a new release. This task is performed from the NAM CLI.
1.
reboot
2.
y
3. When prompted, enter *** to change the boot configuration.
4.
boot
flash
5. When prompted to select from the helper menu, enter 1or 2.
6.
ftp://
ip-address/path/nam-image-file
7.
y
8.
r
9.
y
DETAILED STEPS
| Command or Action | Purpose | |
|---|---|---|
| Step 1 |
reboot
Example: root@nam1.cisco.com# reboot |
Shuts down and restarts the NAM. |
| Step 2 |
y
Example: Reboot the NAM? (Y/N) [N]: y |
Confirms that you want to reboot the NAM. |
| Step 3 | When prompted, enter
*** to change the boot configuration.
Example: Please enter '***' to change boot configuration: *** |
Interrupts the boot loader. |
| Step 4 |
boot
flash
Example: ServicesEngine boot-loader> boot flash |
Loads the NAM helper image. |
| Step 5 | When prompted to select from the helper menu, enter
1or
2.
Example: Selection [12345678rh]: 1 Example: Selection [12345678rh]: 2 |
Selects the menu option to download the NAM software image onto the NM-NAM internal memory.
|
| Step 6 |
ftp://
ip-address/path/nam-image-file
Example: Download NAM application image via ftp and write to HDD Example: URL of application image []: ftp://172.20.98.136/dir1/dir2/nam-image.bin.gz |
Specifies the FTP location and filename of the NAM software image. |
| Step 7 |
y
Example: Do you want to proceed installing it? [y/N] y |
Confirms that you want to install the specified NAM software image. |
| Step 8 |
r
Example: Selection [12345678rh]:r |
Selects the menu option to exit the helper and reset the NAM. |
| Step 9 |
y
Example: About to exit and reset Services Engine. Example: Are you sure? [y/N] y |
Confirms that you want to exit the helper and reset the NAM. |
Examples
This section provides the following examples:
Upgrading the NAM Software--Patch: Example
Router> enable Password: <password> Router# Router# service-module analysis-Module 1/0 session Trying 172.20.104.86, 2033 ... Open Cisco Network Analysis Module (NM-NAM) nam1.cisco.com login: root Password: <password> Terminal type:vt100 Cisco Network Analysis Module (NM-NAM) Console, 3.2(0.10) Copyright (c) 1999-2003 by cisco Systems, Inc. WARNING! Default password has not been changed! root@nam1.cisco.com# patch ftp://person@examplehost/dir/subdir/nam-app.3-2.cryptoK9.patch.1-0.bin Proceeding with installation. Please do not interrupt. If installation is interrupted, please try again. Downloading nam-app.3-2.cryptoK9.patch.1-0.bin. Please wait... Password for person@examplehost: <mypwd> ftp://person@examplehost/dir/subdir/nam-app.3-2.cryptoK9.patch.1-0.bin (1K) /usr/local/nam/patch/wor [########################] 1K | 104.43K/s 1894 bytes transferred in 0.02 sec (102.35k/sec) Verifying nam-app.3-2.cryptoK9.patch.1-0.bin. Please wait... Patch nam-app.3-2.cryptoK9.patch.1-0.bin verified. Applying /usr/local/nam/patch/workdir/nam-app.3-2.cryptoK9.patch.1-0.bin. Please wait... ########################################### [100%] ########################################### [100%] Patch applied successfully. root@nam1.cisco.com# show patches Tue Aug 31 21:04:28 2004 Patch:nam-app.3-2.strong-crypto-patchK9-1-0 Description:Strong Crypto Patch for NAM. root@nam1.cisco.com#
Upgrading the NAM Software--Full Image: Example
Router> enable Password: <password> Router# Router# service-module analysis-Module 1/0 session Trying 172.20.104.86, 2033 ... Open Cisco Network Analysis Module (NM-NAM) nam1.cisco.com login: root Password: <password> Terminal type:vt100 Cisco Network Analysis Module (NM-NAM) Console, 3.2(0.10) Copyright (c) 1999-2003 by cisco Systems, Inc. WARNING! Default password has not been changed! root@nam1.cisco.com# root@nam1.cisco.com# reboot Reboot the NAM? (Y/N) [N]: y System reboot in process... . <debug output omitted> . Booting from flash..., please wait. [BOOT-ASM] 7 Please enter '***' to change boot configuration: *** ServicesEngine Bootloader Version :1.0.6-NAM ServicesEngine boot-loader> ServicesEngine boot-loader> boot flash . <debug output omitted> . ============================================================================== Cisco Systems, Inc. Services engine helper utility for NM-NAM Version 1.1(1) [200311111641] ----- Main menu 1 - Download application image and write to HDD 2 - Download application image and reformat HDD 3 - Download bootloader and write to flash 4 - Download helper and write to flash 5 - Display software versions 6 - Reset application image CLI passwords to default 7 - Change file transfer method (currently ftp/http) 8 - Show upgrade log 9 - Send Ping r - Exit and reset Services Engine h - Exit and shutdown Services Engine Selection [123456789rh]: 1 ----- Download NAM application image via ftp and write to HDD URL of application image []: ftp://172.20.98.136/dir1/dir2/nam-image.bin.gz Getting c6svc-nam.mainline-DAILY_20030825.bin.gz from 171.69.17.19 via ftp. ftp://172.20.98.136/dir1/dir2/nam-image.bin.gz (46389K) - [########################] 46389K | 7421.38K/s 47502347 bytes transferred in 6.25 sec (7421.14k/sec) upgrade.bin size:48241545 File transfer successful. Checking upgrade.bin Do you want to proceed installing it? [y/N] y . <debug output omitted> . Application image upgrade complete. You can boot the image now. ============================================================================== Cisco Systems, Inc. Services engine helper utility for NM-NAM Version 1.1(1) [200311111641] ----- Main menu 1 - Download application image and write to HDD 2 - Download application image and reformat HDD 3 - Download bootloader and write to flash 4 - Download helper and write to flash 5 - Display software versions 6 - Reset application image CLI passwords to default 7 - Change file transfer method (currently ftp/http) 8 - Show upgrade log 9 - Send Ping r - Exit and reset Services Engine h - Exit and shutdown Services Engine Selection [123456789rh]: r About to exit and reset Services Engine. Are you sure? [y/N] y
Troubleshooting Tips
If you have trouble opening a NAM console session from the router, make sure that the NAM console line is clear by entering the service-module analysis-module slot /0 session clear command in privileged EXEC mode.
Configuration Examples for the Network Analysis Module (NM-NAM)
- NAM Management Interface Is Internal and Analysis-Module Interface Is Assigned an IP Address Example
- NAM Management Interface Is Internal and Analysis-Module Interface Is IP Unnumbered Example
- NAM Management Interface Is External and Analysis-Module Interface Is IP Unnumbered Example
NAM Management Interface Is Internal and Analysis-Module Interface Is Assigned an IP Address Example
In this configuration example:
The internal NAM interface is used for management traffic.
IP addresses from the same routable subnet are assigned to the Analysis-Module interface and the NAM system.
A static route to the NAM through the Analysis-Module interface is configured.
The internal NAM interface is used to monitor WAN traffic on interface Serial 0/0, and the external NAM interface is used to monitor LAN traffic on interface Fast Ethernet 0/0.
The NM-NAM is installed in router slot 2.
The figure below shows the topology used in the example, and the following sections show the router and NAM configurations:

|
Callout |
Interface |
Location |
|---|---|---|
|
1 |
Analysis-Module interface |
Router internal |
|
2 |
Internal NAM interface (management) |
NM-NAM internal |
|
3 |
External NAM interface |
NM-NAM faceplate |
|
4 |
Serial interface |
WAN interface card (WIC) |
|
5 |
Fast Ethernet interface |
Router rear panel |
Router Configuration (Cisco IOS Software)
! ip cef ! ip route 209.165.200.226 255.255.255.224 analysis-module 2/0 ! interface FastEthernet0/0 ip address 209.165.202.129 255.255.255.224 ip route-cache flow speed auto full-duplex no mop enabled no shutdown ! interface Serial 0/0 encapsulation ppp ip address 209.165.201.1 255.255.255.224 analysis-module monitoring no shutdown ! interface analysis-module 2/0 ip address 209.165.200.225 255.255.255.224 hold-queue 60 out no shutdown !
NAM Configuration (NAM Software)
! ip address 209.165.200.226 255.255.255.224 ! ip host "nam1" ! ip domain "cisco.com" ! ip gateway 209.165.200.225 ! ip broadcast 10.255.255.255 ! ip nameserver 172.16.201.29 ! ip interface internal ! ip http server enable ! exsession on !
NAM Management Interface Is Internal and Analysis-Module Interface Is IP Unnumbered Example
In this configuration example:
The internal NAM interface is used for management traffic.
IP addresses from the same routable subnet are assigned to the Analysis-Module interface and the NAM system.
To conserve IP address space, the Analysis-Module interface is configured as IP unnumbered to borrow the IP address of the Fast Ethernet interface.
A static route to the NAM through the Analysis-Module interface is configured.
The internal NAM interface is used to monitor WAN traffic on interface Serial 0/0, and the external NAM interface is used to monitor LAN traffic on interface Fast Ethernet 0/0.
The NM-NAM is installed in router slot 2.
The figure below shows the topology used in the example, and the following sections show the router and NAM configurations:

|
Callout |
Interface |
Location |
|---|---|---|
|
1 |
Analysis-Module interface |
Router internal |
|
2 |
Internal NAM interface (management) |
NM-NAM internal |
|
3 |
External NAM interface |
NM-NAM faceplate |
|
4 |
Serial interface |
WAN interface card (WIC) |
|
5 |
Fast Ethernet interface |
Router rear panel |
Router Configuration (Cisco IOS Software)
! ip cef ! ip route 209.165.200.226 255.255.255.224 analysis-module 2/0 ! interface FastEthernet0/0 ip address 209.165.200.225 255.255.255.224 ip route-cache flow speed auto full-duplex no mop enabled no shutdown ! interface Serial 0/0 encapsulation ppp ip address 209.165.201.1 255.255.255.224 analysis-module monitoring no shutdown ! interface analysis-module 2/0 ip unnumbered FastEthernet0/0 no shutdown hold-queue 60 out !
NAM Configuration (NAM Software)
! ip address 209.165.200.226 255.255.255.224 ! ip host "nam1" ! ip domain "cisco.com" ! ip gateway 209.165.200.225 ! ip broadcast 10.255.255.255 ! ip nameserver 172.16.201.29 ! ip interface internal ! ip http server enable ! exsession on !
NAM Management Interface Is External and Analysis-Module Interface Is IP Unnumbered Example
In this configuration example:
The external NAM interface is used for management traffic.
The Analysis-Module interface is configured as IP unnumbered to borrow the IP address of the loopback interface.
The borrowed loopback interface IP address is not routable.
The NAM system is configured with an IP address from the LAN subnet that is connected to the external NAM interface.
The internal NAM interface is used to monitor WAN traffic on interface Serial 0/0, and the external NAM interface is used to monitor LAN traffic on interface Fast Ethernet 0/0.
The NM-NAM is installed in router slot 3.
The figure below shows the topology used in the example, and the following sections show the router and NAM configurations:

|
Callout |
Interface |
Location |
|---|---|---|
|
1 |
Analysis-Module interface |
Router internal |
|
2 |
Internal NAM interface |
NM-NAM internal |
|
3 |
External NAM interface (management) |
NM-NAM faceplate |
|
4 |
Loopback interface |
Router internal |
|
5 |
Serial interface |
WAN interface card (WIC) |
|
6 |
Fast Ethernet interface |
Router rear panel |
Router Configuration (Cisco IOS Software)
! ip cef ! interface loopback 0 ip address 10.1.1.1 255.255.255.0 ! interface FastEthernet0/0 ip address 209.165.201.1 255.255.255.224 ip route-cache flow speed auto full-duplex no mop enabled no shutdown ! interface Serial 0/0 encapsulation ppp ip address 209.165.202.129 255.255.255.224 analysis-module monitoring no shutdown ! interface analysis-module 3/0 ip unnumbered loopback 0 hold-queue 60 out no shutdown !
NAM Configuration (NAM software)
! ip address 209.165.201.2 255.255.255.224 ! ip host "nam1" ! ip domain "cisco.com" ! ip gateway 209.165.201.1 ! ip broadcast 10.255.255.255 ! ip nameserver 209.165.201.29 ! ip interface external ! ip http server enable ! exsession on !
Additional References
Related Documents
Related Topic |
Document Title |
|---|---|
|
IPv6 addressing and connectivity |
IPv6 Configuration Guide |
|
Cisco IOS commands |
|
|
IPv6 commands |
|
|
Cisco IOS IPv6 features |
Standards and RFCs
Standard/RFC |
Title |
|---|---|
|
RFCs for IPv6 |
IPv6 RFCs |
MIBs
|
MIB |
MIBs Link |
|---|---|
|
|
To locate and download MIBs for selected platforms, Cisco IOS releases, and feature sets, use Cisco MIB Locator found at the following URL: |
Technical Assistance
Description |
Link |
|---|---|
|
The Cisco Support and Documentation website provides online resources to download documentation, software, and tools. Use these resources to install and configure the software and to troubleshoot and resolve technical issues with Cisco products and technologies. Access to most tools on the Cisco Support and Documentation website requires a Cisco.com user ID and password. |
Command Reference
The following new commands are pertinent to this feature. To see the command pages for these commands and other commands used with this feature, go to the Cisco IOS Master Commands List , Release 12.4, at http://www.cisco.com/univercd/cc/td/doc/product/software/ios124/124mindx/ 124index.htm.
analysis-module monitoring
interface analysis-module
service-module analysis-module reload
service-module analysis-module reset
service-module analysis-module session
service-module analysis-module shutdown
service-module analysis-module status
show controllers analysis-module
show interfaces analysis-module
Feature Information for Network Analysis Module (NM-NAM)
The following table provides release information about the feature or features described in this module. This table lists only the software release that introduced support for a given feature in a given software release train. Unless noted otherwise, subsequent releases of that software release train also support that feature.
Use Cisco Feature Navigator to find information about platform support and Cisco software image support. To access Cisco Feature Navigator, go to www.cisco.com/go/cfn. An account on Cisco.com is not required.
|
Feature Name |
Releases |
Feature Information |
|---|---|---|
|
Network Analysis Module (NM-NAM) |
12.3(4)XD |
This feature was introduced on the following platforms: Cisco 2600XM series, Cisco 2691, Cisco 3660, Cisco 3725, and Cisco 3745. |
|
Network Analysis Module (NM-NAM) |
12.3(7)T |
This feature was integrated into Cisco IOS Release 12.3(7)T. |
|
|
12.3(8)T4 |
This feature was implemented on the following platforms: Cisco 2811, Cisco 2821, and Cisco 2851. |
|
|
12.3(11)T |
This feature was implemented on the Cisco 3800 series. |
Glossary
AAA --authentication, authorization, and accounting. Pronounced "triple a."
access list --A list kept by routers to control access to or from the router for a number of services (for example, to prevent packets with a certain IP address from leaving a particular interface on the router).
CEF --Cisco Express Forwarding.
DSMON --Differentiated Services Monitoring.
flooding --Traffic passing technique used by switches and bridges in which traffic received on an interface is sent out all the interfaces of that device except the interface on which the information was received originally.
GRE --generic routing encapsulation. Tunneling protocol developed by Cisco that can encapsulate a wide variety of protocol packet types inside IP tunnels, creating a virtual point-to-point link to Cisco routers at remote points over an IP internetwork. By connecting multiprotocol subnetworks in a single-protocol backbone environment, IP tunneling using GRE allows network expansion across a single-protocol backbone environment.
GUI --graphical user interface. A user environment that uses pictorial as well as textual representations of the input and the output of applications and the hierarchical or other data structure in which information is stored. Such conventions as buttons, icons, and windows are typical, and many actions are performed using a pointing device (such as a mouse). Microsoft Windows and the Apple Macintosh are prominent examples of platforms using a GUI.
IP multicast --Routing technique that allows IP traffic to be propagated from one source to a number of destinations or from many sources to many destinations. Rather than sending one packet to each destination, one packet is sent to a multicast group identified by a single IP destination group address.
MIB --Management Information Base. Database of network management information that is used and maintained by a network management protocol, such as SNMP or Common Management Information Protocol (CMIP). The value of a MIB object can be changed or retrieved using SNMP or CMIP commands, usually through a GUI network management system. MIB objects are organized in a tree structure that includes public (standard) and private (proprietary) branches.
NAT --Network Address Translation. Mechanism for reducing the need for globally unique IP addresses. NAT allows an organization with addresses that are not globally unique to connect to the Internet by translating those addresses into globally routable address space. Also known as Network Address Translator .
NetFlow --A feature of some routers that allows them to categorize incoming packets into flows. Because packets in a flow often can be treated in the same way, this classification can be used to bypass some of the work of the router and accelerate its switching operation.
PCI --Peripheral Component Interconnect. An industry local bus standard.
QoS --quality of service. Cisco IOS QoS technology lets complex networks control and predictably service a variety of networked applications and traffic types.
RMON --remote monitoring. MIB agent specification described in RFC 1271 that defines functions for the remote monitoring of networked devices. The RMON specification provides numerous monitoring, problem detection, and reporting capabilities.
SNMP --Simple Network Management Protocol. Network management protocol used almost exclusively in TCP/IP networks. SNMP provides a means to monitor and control network devices, and to manage configurations, statistics collection, performance, and security. SNMPv2c supports centralized and distributed network management strategies and includes improvements in the Structure of Management Information (SMI), protocol operations, management architecture, and security. SNMPv3 provides secure access to devices by a combination of authenticating and encrypting packets over the network.
SSH --Secure Shell Protocol. A protocol that provides a secure remote connection to a router through a Transmission Control Protocol (TCP) application.
UDP --User Datagram Protocol. Connectionless transport layer protocol in the TCP/IP protocol stack. UDP is a simple protocol that exchanges datagrams without acknowledgments or guaranteed delivery, requiring that error processing and retransmission be handled by other protocols. UDP is defined in RFC 768.
VoIP --Voice over IP. The capability to carry normal telephony-style voice over an IP-based Internet with POTS-like functionality, reliability, and voice quality. VoIP enables a router to carry voice traffic (for example, telephone calls and faxes) over an IP network. In VoIP, the digital signal processor (DSP) segments the voice signal into frames, which then are coupled in groups of two and stored in voice packets. These voice packets are transported using IP in compliance with ITU-T specification H.323.
 Note | Refer to Internetworking Terms and Acronyms for terms not included in this glossary. |