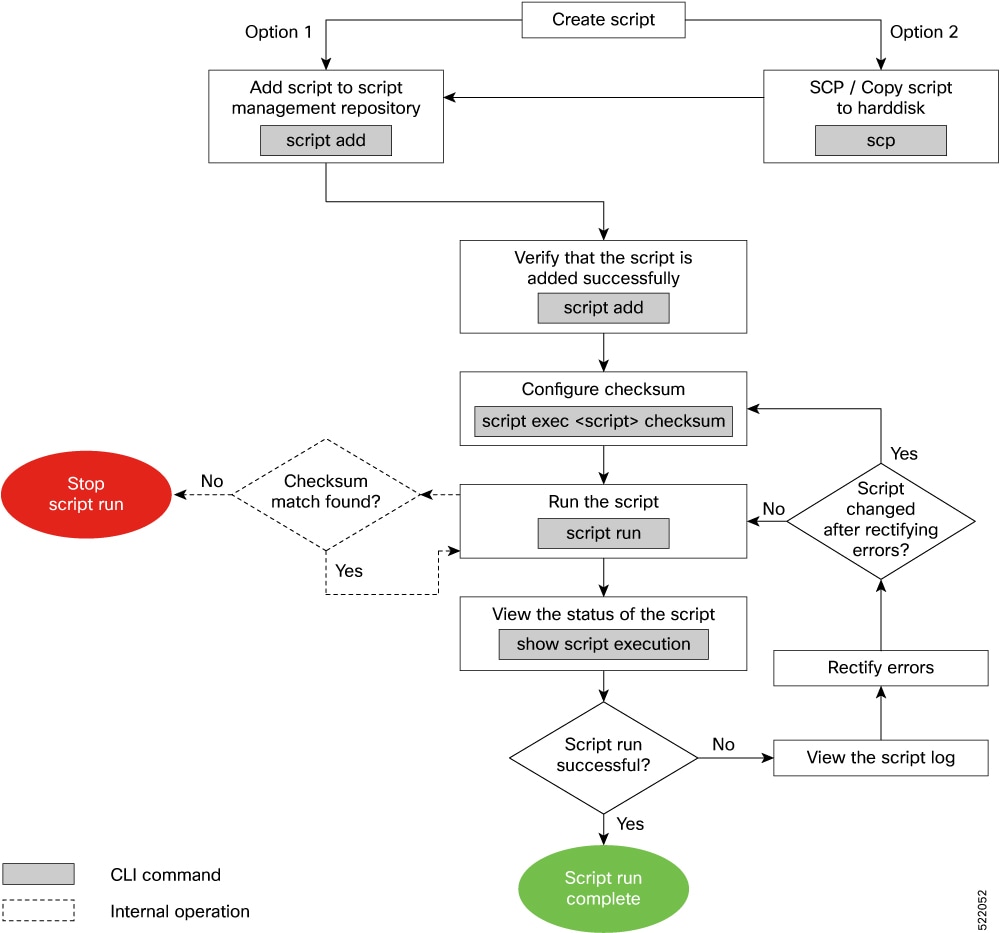
Workflow to Run an Exec Script
Complete the following tasks to provision exec scripts:
-
Download the script—Add the script to the appropriate exec script directory on the router. using the script add exec command.
-
Configure checksum—Check script integrity and authenticity using the script exec <script.py> checksum command.
-
Run the script—Trigger changes to the router configuration. Include arguments, set the maximum time for the script to run, setup log levels using the script run command.
-
View the script execution details—Validate the script and retrieve the operational data using the show script execution command.
The following image shows a workflow diagram representing the steps involved in using an exec script:
Download the Script to the Router
To manage the scripts, you must add the scripts to the script management repository on the router. A subdirectory is created for each script type. By default, this repository stores the downloaded scripts in the appropriate subdirectory based on script type.
| Script Type | Download Location |
|---|---|
|
config |
harddisk:/mirror/script-mgmt/config |
|
exec |
harddisk:/mirror/script-mgmt/exec |
|
process |
harddisk:/mirror/script-mgmt/process |
|
eem |
harddisk:/mirror/script-mgmt/eem |
-
Method 1: Add script from a server
-
Method 2: Copy script from external repository to harddisk using scp or copy command
In this section, you learn how to add exec-script.py script to the script management repository.
Procedure
|
Step 1 |
Add the script to the script management repository on the router using one of the two options:
|
||||
|
Step 2 |
Verify that the scripts are downloaded to the script management repository on the router. Example:exec-script.py is copied to harddisk:/mirror/script-mgmt/exec directory on the router.
|
Update Scripts from a Remote Server
|
Feature Name |
Release Information |
Description |
|---|---|---|
|
Update Automation Scripts from Remote Server |
Release 7.5.1 |
This feature lets you update automation scripts across routers by accessing the master script from a remote site. This eases script management, where you make changes to the master script and then copy it to routers where it is deployed. This feature introduces the auto-update keyword in the script exec command. |
You can maintain the latest copy of the scripts in a remote location, and configure the routers to automatically update the local copy with the latest copy on the server as required.
Procedure
|
You can update the script using one of the following options.
|
Invoke Scripts from a Remote Server
You can directly run the script using the URL to the remote server and provide the checksum value. The checksum is a mandatory
parameter. The format of the URL is [protocol]://[user:password@]server[:port]/directory/file_name.
Procedure
|
Run the script from the remote server. Example:The repository can be accessed remotely through FTP, HTTP, HTTPS, TFTP or SCP protocols. You can specify additional options to the command:
|
Configure Checksum for Exec Script
Every script is associated with a checksum value. The checksum ensures the integrity of the script that is downloaded from the server or external repository is intact, and that the script is not tampered. The checksum is a string of numbers and letters that act as a fingerprint for script. The checksum of the script is compared with the configured checksum. If the values do not match, the script is not run and a syslog warning message is displayed.
It is mandatory to configure the checksum to run the script.
 Note |
Exec scripts support SHA256 checksum. |
Before you begin
Procedure
|
Step 1 |
Retrieve the SHA256 checksum hash value for the script. Ideally this action would be performed on a trusted device, such as the system on which the script was created. This minimizes the possibility that the script is tampered with. Example:Make note of the checksum value. |
|
Step 2 |
View the status of the script. Example:The |
|
Step 3 |
Enter global configuration mode. Example: |
|
Step 4 |
Configure the checksum. Example: |
|
Step 5 |
Verify the status of the script. Example:The status |
Run the Exec Script
To run an exec script, use the script run command. After the script is run, a request ID is generated. Each script run is associated with a unique request ID.
Before you begin
Procedure
|
Run the exec script. Example:Scripts can be run with more options. The following table lists the various options that you can provide at run time:
The script run is complete. |
View the Script Execution Details
View the status of the script execution.
Before you begin
Procedure
|
Step 1 |
View the status of the script execution. Example:You can view detailed or filtered data for every script run. |
||||||||||||||
|
Step 2 |
Filter the script execution status to view the detailed output of a specific script run via request ID. Example:
|
 Feedback
Feedback