Understanding uRPF
|
Feature Name |
Release Information |
|
|---|---|---|
|
uRPF in Loose Mode |
Release 24.4.1 |
Introduced in this release on: Fixed Systems (8700) (select variants only*) uRPF in Loose Mode is now supported on Cisco 8712-MOD-M routers. |
|
uRPF in Loose Mode |
Release 7.3.15 |
When the source IP address of an incoming packet is not present in the Forwarding Information Base (FIB), the router considers it as an invalid packet and drops it. Use the allow-default keyword of ipv4/ipv6 verify unicast source reachable-via command and configure the default route for the interface so that the router does not drop a packet even when the source IP address is not present in the FIB. The command ipv4/ipv6 verify unicast source reachable-via is introduced. |
It has become commonplace practice for hackers planning a Denial of Service (DoS) attack to use forged IP addresses (the practice is known as IP address spoofing). Hackers constantly change the source IP address to avoid detection by service providers. DoS uses more than one forged IP address from thousands of hosts that are infected with malware to flood a device. Therefore, it is complicated to identify and defeat the malware attack.
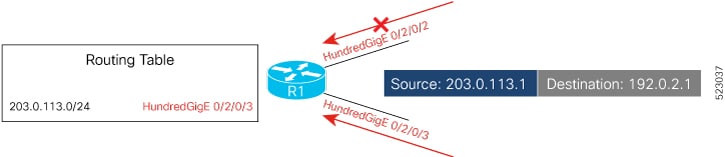
The uRPF is a mechanism for validating the source IP address of packets that are received on a router. A router that is configured with uRPF performs a reverse path lookup in the FIB table to validate the presence of the source IP address. If the FIB table lists the source IP address, then it indicates that the source is reachable and valid. If the FIB table does not list the source IP address, the router treats the packet as malicious and drops it.
The router supports uRPF in two modes:
-
uRPF in Loose Mode: In uRPF loose mode, the router checks if it has a matching entry for the source IP address in the FIB and does not drop the legitimate regardless of interfaces the source address is learned on
-
uRPF in Strict Mode: In uRPF strict mode, the router check if the interface receiving traffic packets is the same as the interface to reach the incoming packet's source address, the router considers such traffic packets legitimate and processes them. If not, the router drops it. The router supports uRPF in Strict Mode since IOS XR Release 7.9.1


 Feedback
Feedback