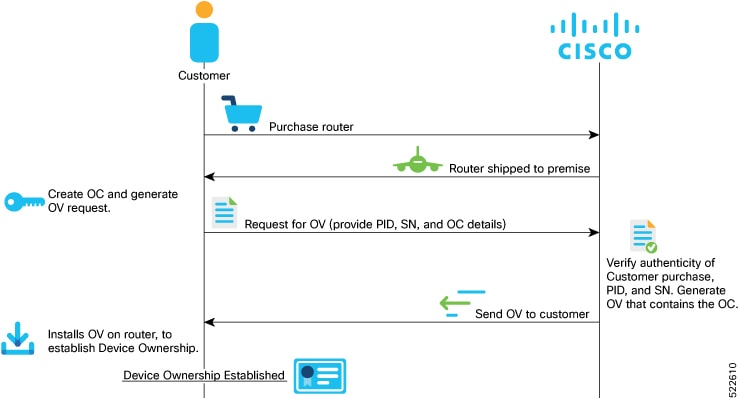
Establish Device Ownership
Device ownership is a process by which a device establishes its first trusted connection with the device management service (network) and vice versa.
Device Ownership Establishment (DOE) is required to allow the network to validate the router, and for the router to validate the network. DOE also helps to validate the signature of third-party applications before being installed on the router.
DOE is also required to perform some tasks securely and without Cisco’s intervention, such as:
-
Enable or disable Reimage Protection mechanism
-
Install and enable customer key-package – a feature that provides a conduit to verify and onboard third party applications on Cisco IOS XR routers.
-
Create the ownership certificate using OpenSSL commands.
The router verifies that the OC has a chain of trust leading to the trust certificate (pinned-domain-cert [PDC]) that is included in the OV.
-
Create request for ownership voucher (OV). For more information, see the Interacting with the MASA Server section in the Manufacturer Authorized Signing Authority (MASA) chapter.

Note
Reference scripts to create OCs are available on Github at https://github.com/ios-xr/key-package-scripts.
-
Send the OV request to Cisco along with the following artifacts:
-
Router’s Product Identifier (PID)
-
Router’s Serial Number
-
Owner Certificate (OC) for the router for which the OV is required
Cisco verifies the authenticity of the artifacts and generates the OVs.
-
-
Install the OVs on the router by running the platform security device-owership command in EXEC mode.
RP/0/RP0/CPU0:router# platform security device-ownership /disk0:/testing2/deliverable/bulk_ovs.tar.gz /disk0:/testing2/oc-single.cms Mon Jun 14 16:05:15.008 UTC
Note
-
This command requires you to provide a tar ball of OVs, with each OV representing a route processor (RP) on the router. You can choose to include an OV for the chassis in the tar ball. You can also choose to maintain a single tar ball of OVs of all the route processors you have purchased that you can then provide as input to the command.
-
The OC must have its trust chain leading to the PDC in the OV.
-
The command accepts only the latest OV. The installation fails if you install a version of the OV that is older than the version of the currently-installed OV.
The router verifies that the OC has a chain of trust leading to the trust certificate (pinned-domain-cert [PDC]) that is included in the OV.
The router adds the PDC and OC to a special trust point as a CA certificate. This trust point configuration appears by default in the router configuration and can be used by any third-party application to establish trust.
If a PDC or OC has expired or has been revoked, re-run the platform security device-ownership command with new certificates.
-
-
Run the following command to verify device ownership is established:
RP/0/RP0/CPU0:ios# show platform security device-ownership Performing operation on all nodes.. ========================= Location : 0/RP0/CPU0 ========================= Trustpoint : device_ownership ================================================== CA certificate Certificate: Data: Version: 3 (0x2) Serial Number: f6:20:61:bd:db:22:30:74 ...truncated...Run the show logging command to verify.
RP/0/RP0/CPU0:router# show logging RP/0/RP1/CPU0:Oct 13 13:10:26.086 UTC: ownership_app[66652]: %SECURITY-OWNERSHIP-6-INFO : Device ownership established.
For information on establishing device ownership through Secure Zero touch provisioning (SZTP), see the chapter Securely Provision Your Network Devices in the System Setup and Software Installation Guide for Cisco NCS 540 Series Routers.
To clear device ownership:
RP/0/RP0/CPU0:router# clear device-ownership
Do you want to clear the device ownership [Y/N]? Y
RP/0/RP0/CPU0:router# show platform security device-ownership
No platform ownership information found. Note |
When you clear device ownership all applications that depend on the OC will fail to function. |









 Feedback
Feedback