LPWA Interface Configuration
The P-LPWA-800 and P-LPWA-900 modules can be managed by command line interface (CLI), or the Cisco IOS XE Web User Interface (WebUI).
 Note |
GPS is mandatory for the Common Packet Forwarder (CPF) application to work. Please connect the Lora module GPS antenna, and check the GPS status using the below command before installing the CPF application. |
Router#show lorawan 0/1/0 gps
Recorded GNSS Info at 2022-09-13 19:20:50 UTC
GNSS Location:
Latitude: 37 Deg 25 Min 5.937 Sec North (37.418316)
Longitude: 121 Deg 55 Min 9.714 Sec West (-121.919365)
Height: 37.0m
Router#
The following is an example of GPS Configuration:
interface LORAWAN0/1/0
no ip address
common-packet-forwarder profile
country UNITEDSTATES
region-channel-plan US915
gateway-id 69
lns-ip 172.27.127.209
lns-port 6080
log-level xdebug lines 240
gps enable
cpf enable
arp timeout 0
no mop enabled
no mop sysid
end
To clear the GPS information use the following command:
Router#clear lorawan 0/1/0 cpf location-info
Router#Common Packet Forwarder Configuration Steps
Follow these steps to configure the interface.
Procedure
| Command or Action | Purpose | |||
|---|---|---|---|---|
|
Step 1 |
configure terminal Example: |
Enters global configuration mode. |
||
|
Step 2 |
int loraWAN interface Example: |
Enters LoraWan interface config mode. |
||
|
Step 3 |
common-packet-forwarder profile Example: |
Configures parameters for the CPF. |
||
|
Step 4 |
region-channel-plan <number> Example: |
Configures the regional channel plan code. |
||
|
Step 5 |
gateway-id <number> Example: |
Configures gateway id used for CPF. |
||
|
Step 6 |
lns-ip <ip-address> Example: |
Configures Lora network server IP address. |
||
|
Step 7 |
lns-port <port-number> Example: |
Configures Lora network server port number. |
||
|
Step 8 |
cpf enable Example: |
Starts the CPF.
|
||
|
Step 9 |
exit Example: |
Exits the CPF profile block and updates the configuration. |
||
|
Step 10 |
exit Example: |
Exits from interface config mode. |
||
|
Step 11 |
exit Example: |
Exits from config mode. |
Default Configuration
The following is an example of a default configuration for the lorawan interface.
Router#sh run int lorawan 0/3/0
Building configuration...
Current configuration : 192 bytes
!
interface LORAWAN0/3/0
no ip address
common-packet-forwarder profile
gateway-id 69
lns-ip 172.27.127.209
lns-port 6080
cpf enable
arp timeout 0
no mop enabled
no mop sysid
end
Router#
Configuring the Interface using the WebUI
Use the following steps to configure the Cisco lorawan interface through the WebUI.
Procedure
|
Step 1 |
After launching the WebUI, navigate to Configuration > LoRaWAN. 
For details about using the WebUI, see Web User Interface (WebUI) in the IR1101 Software Configuration Guide. |
|
Step 2 |
Double click on the LoRaWAN interface. 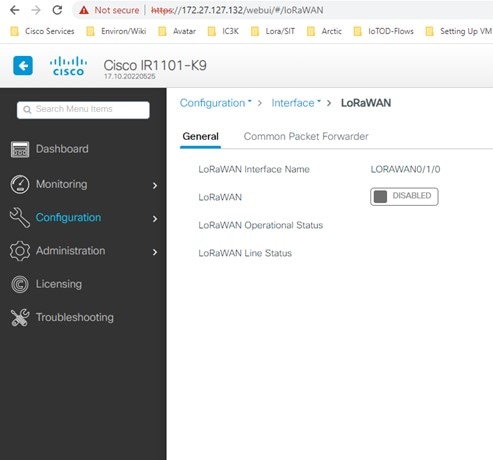
|
|
Step 3 |
Enable the Cisco lorawan interface. 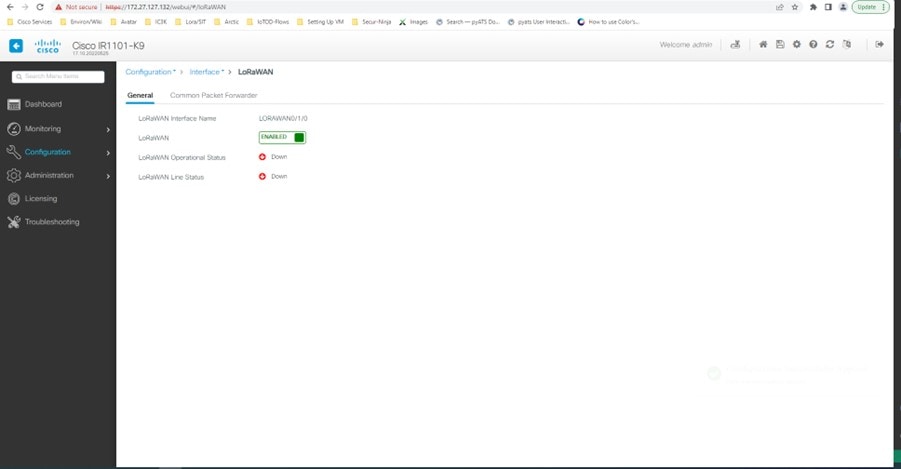
|
|
Step 4 |
Click on the Common Packet Forwarder tab to add the CPF configuration. 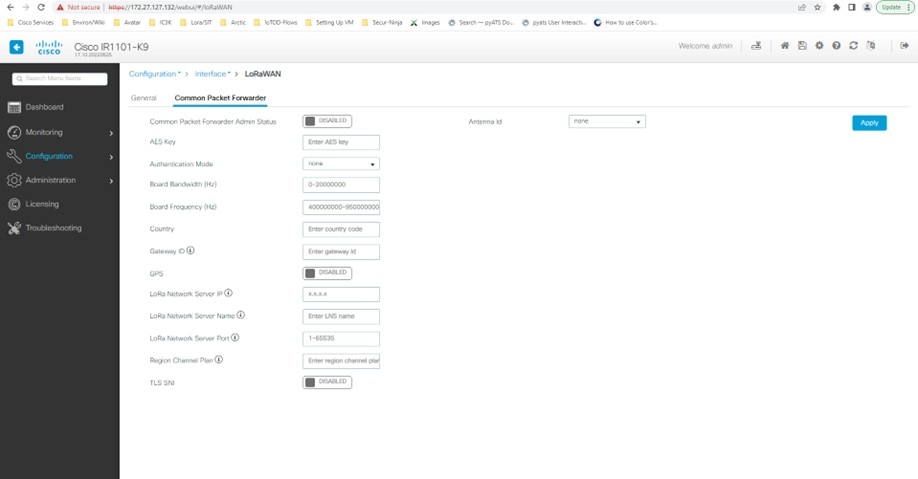
|
|
Step 5 |
Add the CPF configuration and set the Common Packet Forwarder Admin Status to ENABLED. 
|
What to do next
For the Application deployment process using the Local Manager, please refer to Cisco IOx Local Manager Workflows.
 Feedback
Feedback