Configuring Authentication, Authorization, and Accounting Functions
This chapter provides information about configuring authentication, authorization, and accounting (AAA) functions on the BNG router. BNG interacts with the RADIUS server to perform AAA functions. A group of RADIUS servers form a server group that is assigned specific AAA tasks. A method list defined on a server or server group lists methods by which authorization is performed. Some of the RADIUS features include creating specific AAA attribute formats, load balancing of RADIUS servers, throttling of RADIUS records, Change of Authorization (CoA), and Service Accounting for QoS.
|
Release |
Modification |
|---|---|
|
Release 4.2.0 |
Initial release |
|
Release 5.3.1 |
RADIUS over IPv6 was introduced. |
|
Release 5.3.2 |
Service accounting support was added for line card subscribers. |
|
Release 6.2.1 |
A new MAC address format was introduced for RADIUS User-name Attribute. |
|
Release 6.6.3 |
Dynamic Policy Download over RADIUS Interface for BNG Subscriber was introduced. |
|
Release 7.3.1 |
Addded BNG support on Cisco ASR 9000 5th Generation line cards. |
|
Release 7.3.2 |
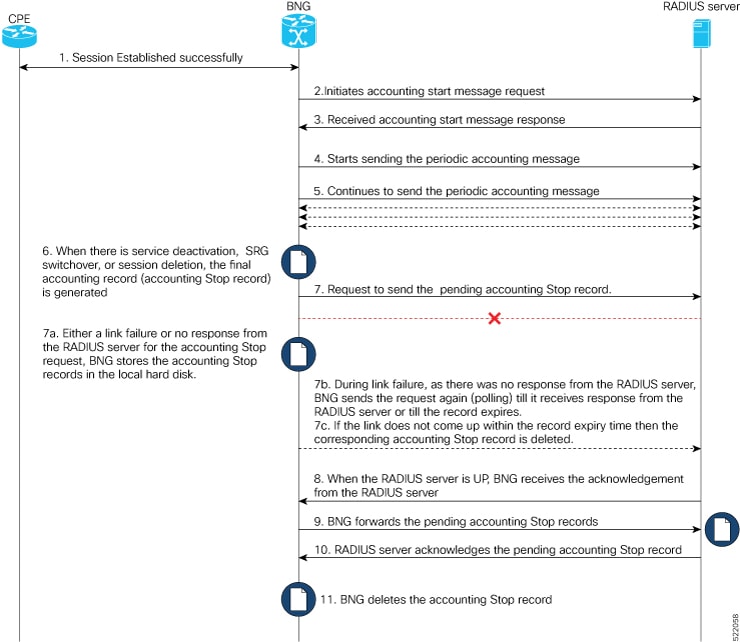
Store Accounting Stop Records was introduced. |
This chapter covers these topics:


 Feedback
Feedback