Feature Information for Layer 2 Tunneling Protocol Version 3
The following table provides release information about the feature or features described in this module. This table lists only the software release that introduced support for a given feature in a given software release train. Unless noted otherwise, subsequent releases of that software release train also support that feature.
Use Cisco Feature Navigator to find information about platform support and Cisco software image support. To access Cisco Feature Navigator, go to www.cisco.com/go/cfn. An account on Cisco.com is not required.|
Feature Name |
Releases |
Feature Information |
|---|---|---|
|
Layer 2 TPv3 on Switched Virtual Interface |
Cisco IOS XE Amsterdam 17.2.1r |
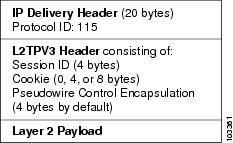
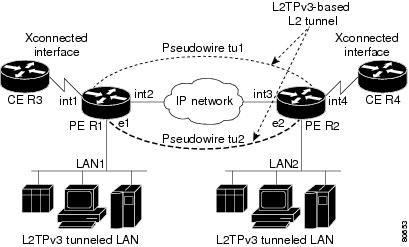
The Layer 2 Tunneling Protocol Version 3 (L2TPv3) feature expands Cisco's support of Layer 2 VPNs on Switched Virtual Interface. For L2TPv3 enabled on SVI interfaces that have xconnect deployed on the devices, the ports are configured to function as LAN switching ports. There are no commands introduced or modified for this feature. |
|
Layer 2Tunneling Protocol Version 3 |
XE 2.6 XE 2.6.2 XE 3.3S XE 3.11S |
The Layer 2 Tunneling Protocol Version 3 (L2TPv3) feature expands Cisco's support of Layer 2 VPNs. In Cisco IOS XE Release 2.6, the following features were added:
In Cisco IOS XE Release 2.6.2, support was added for the ip pmtu command. In Cisco IOS XE Release 3.3S, support for HDLC over L2TPv3 was added. The following commands were introduced or modified: clear l2tun , debug vpdn , ip pmtu , l2tp cookie local , l2tp cookie remote l2tp hello , l2tp id , and xconnect . |



 Feedback
Feedback