Use Case 1: Verify a Cisco Cloud OnRamp for SaaS Policy
Assume that you have a deployment that includes several branch sites. One of these sites, the SJC branch, with a site ID of 3, has two WAN links: an MPLS link, and a public internet link through which the Microsoft cloud can be accessed directly.
In addition, assume that a Cisco Catalyst SD-WAN Cloud OnRamp for SaaS policy, which is a part of an Application-Aware Routing (App-route) policy, has been created and enabled for Microsoft Office 365 applications.
In this use case, let's see how network-wide path insight can be used to determine whether the traffic from Microsoft Office 365 applications is following the expected network path, validate that the policy is programmed correctly and operates as intended, and view the configuration of the policy.
To begin, perform the following actions to start a trace in the SJC branch:
-
From the Cisco Catalyst SD-WAN menu, choose, .
-
Click New Trace.
-
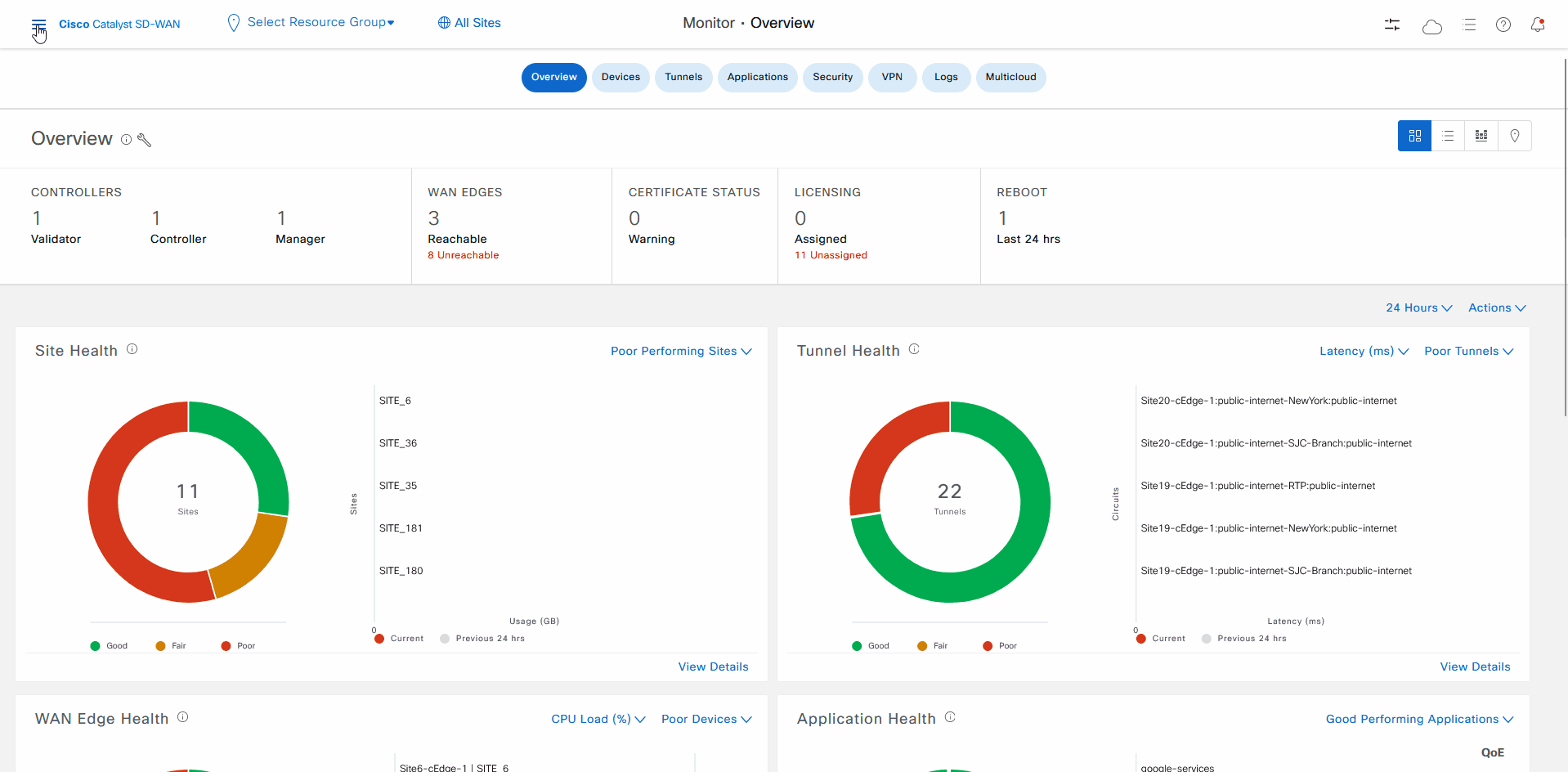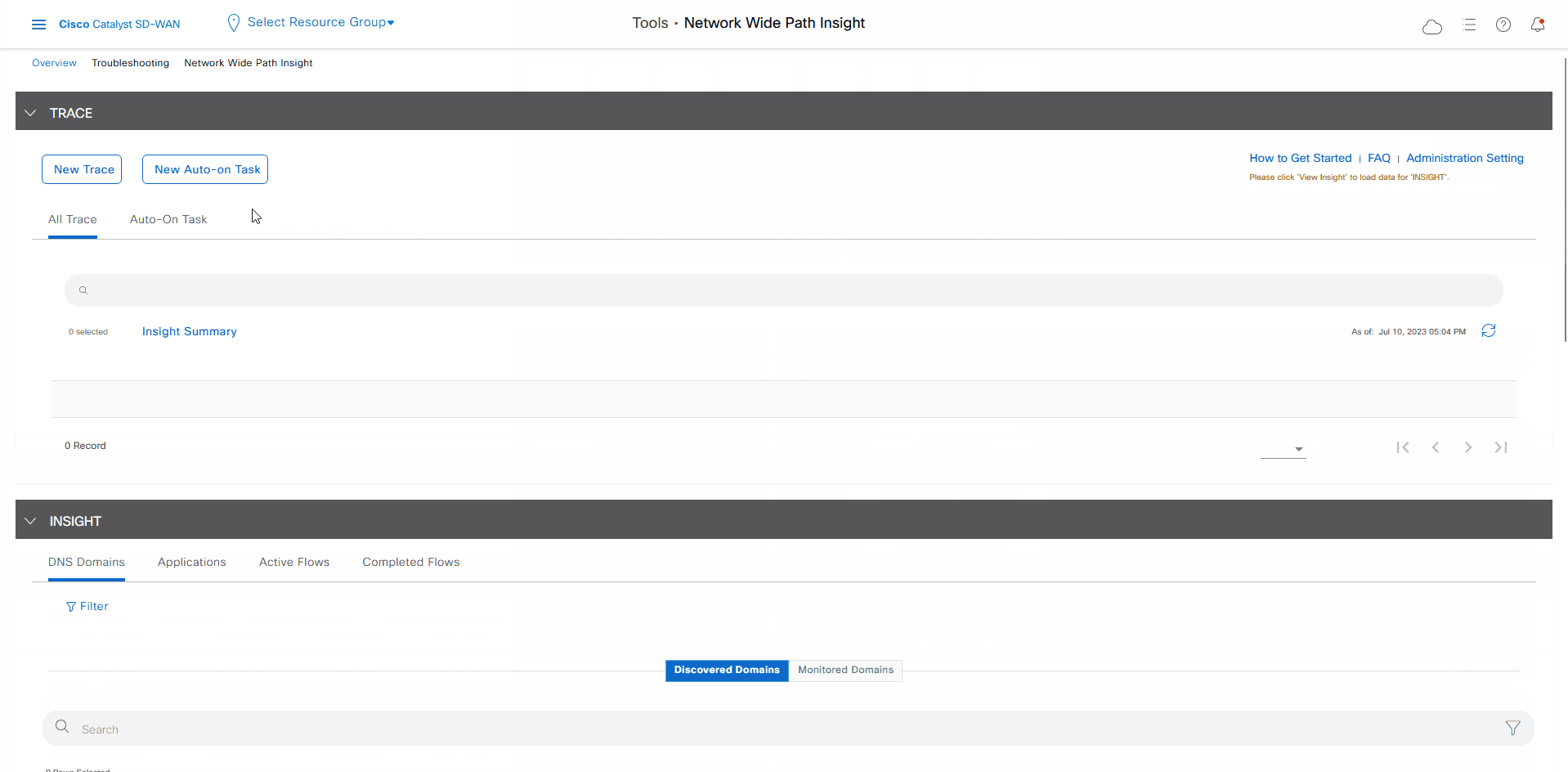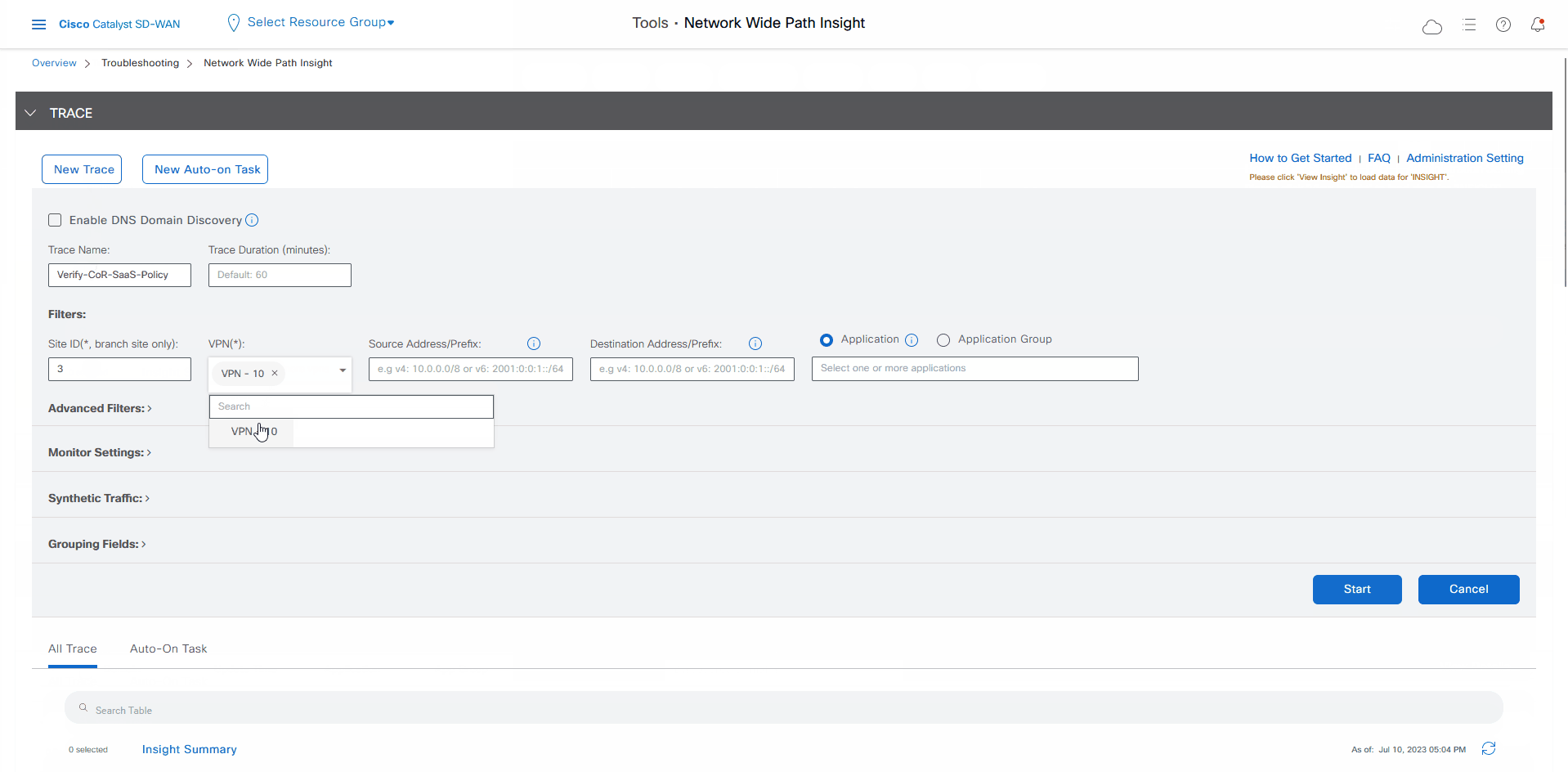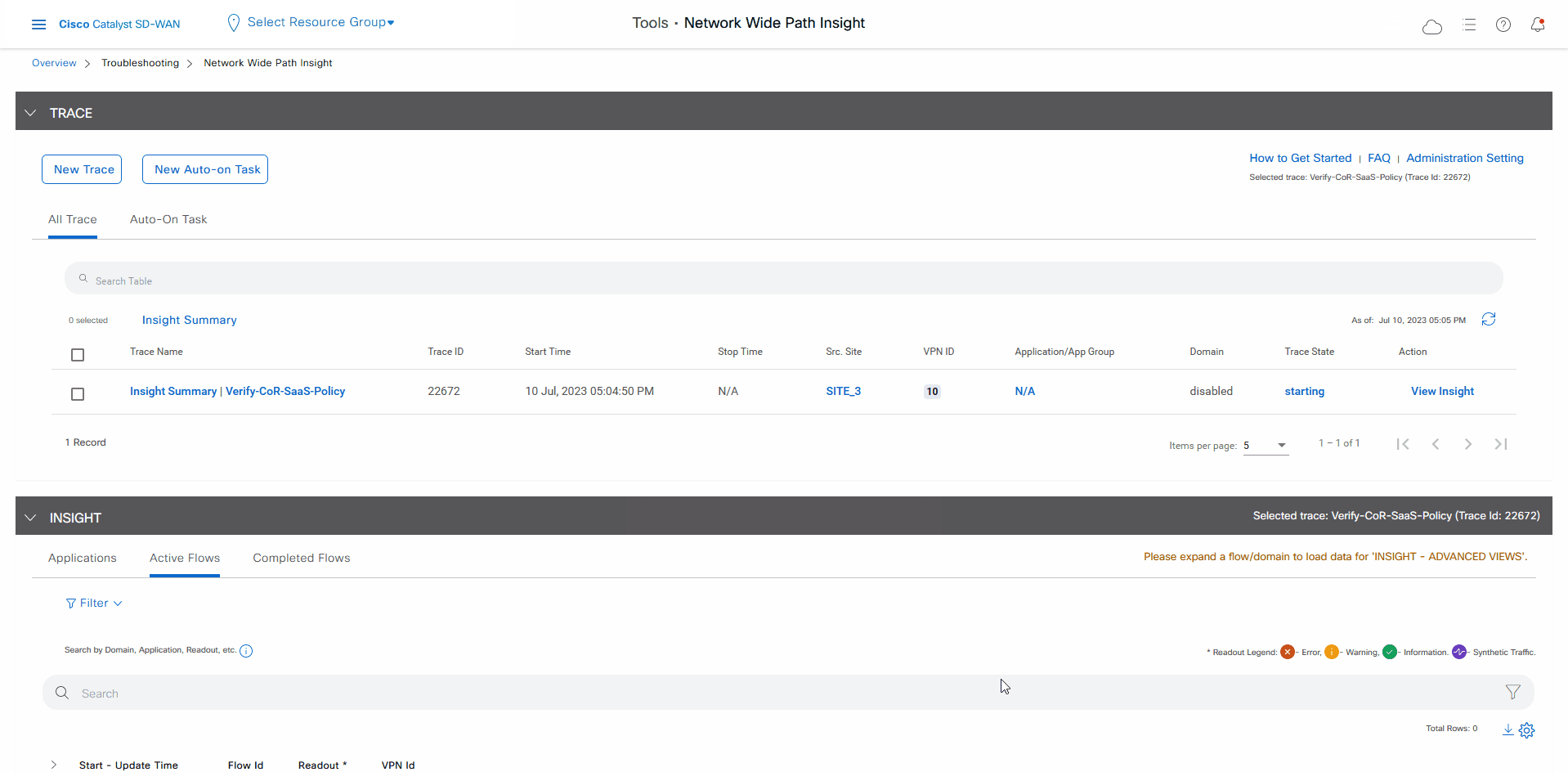
In the Trace Name field, enter a name for the trace.
In this use case, we use the name Verify-Cor-Saas-Policy.
-
From the VPN drop-down list, choose VPN - 10.
-
Click Start.
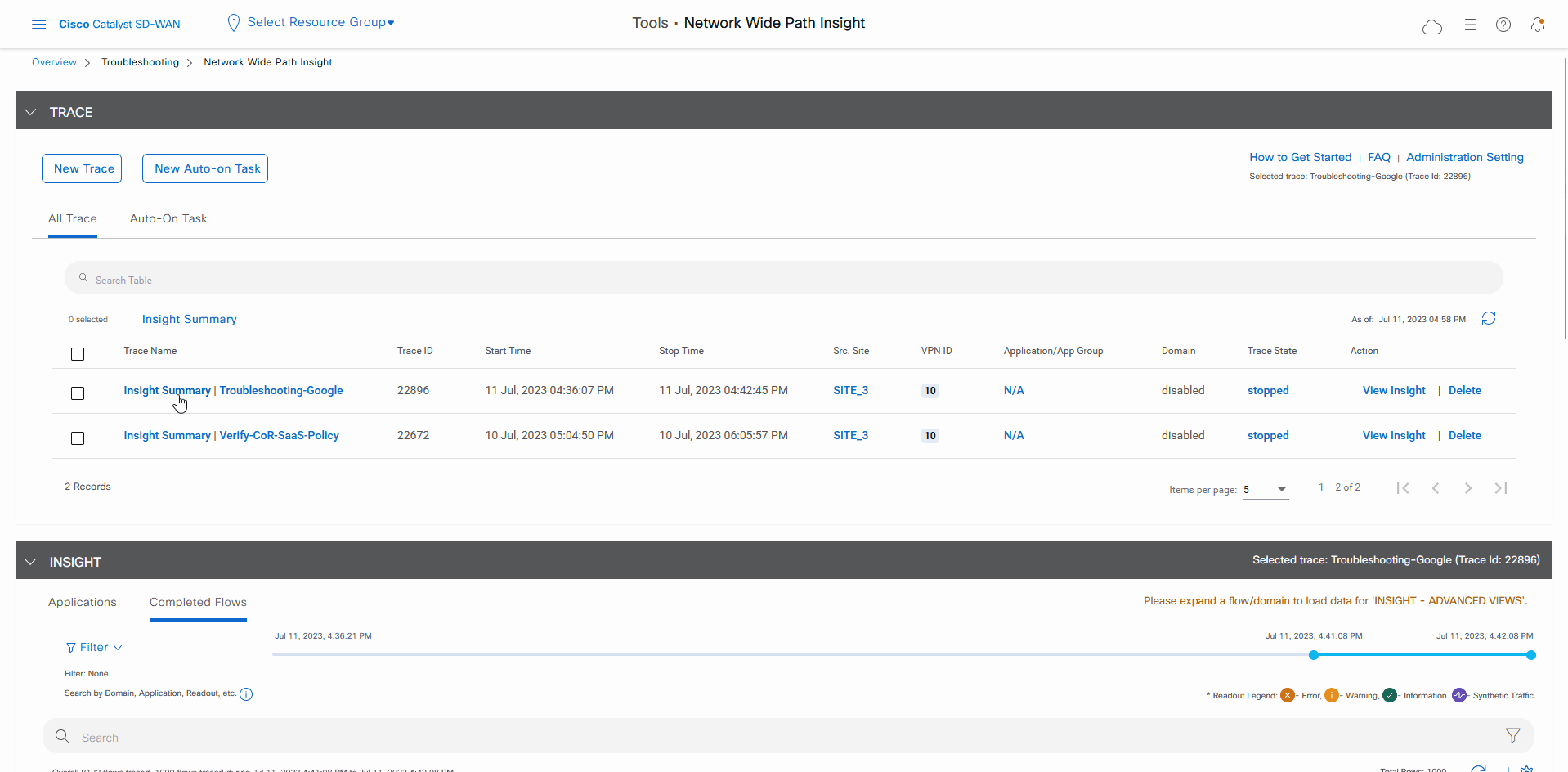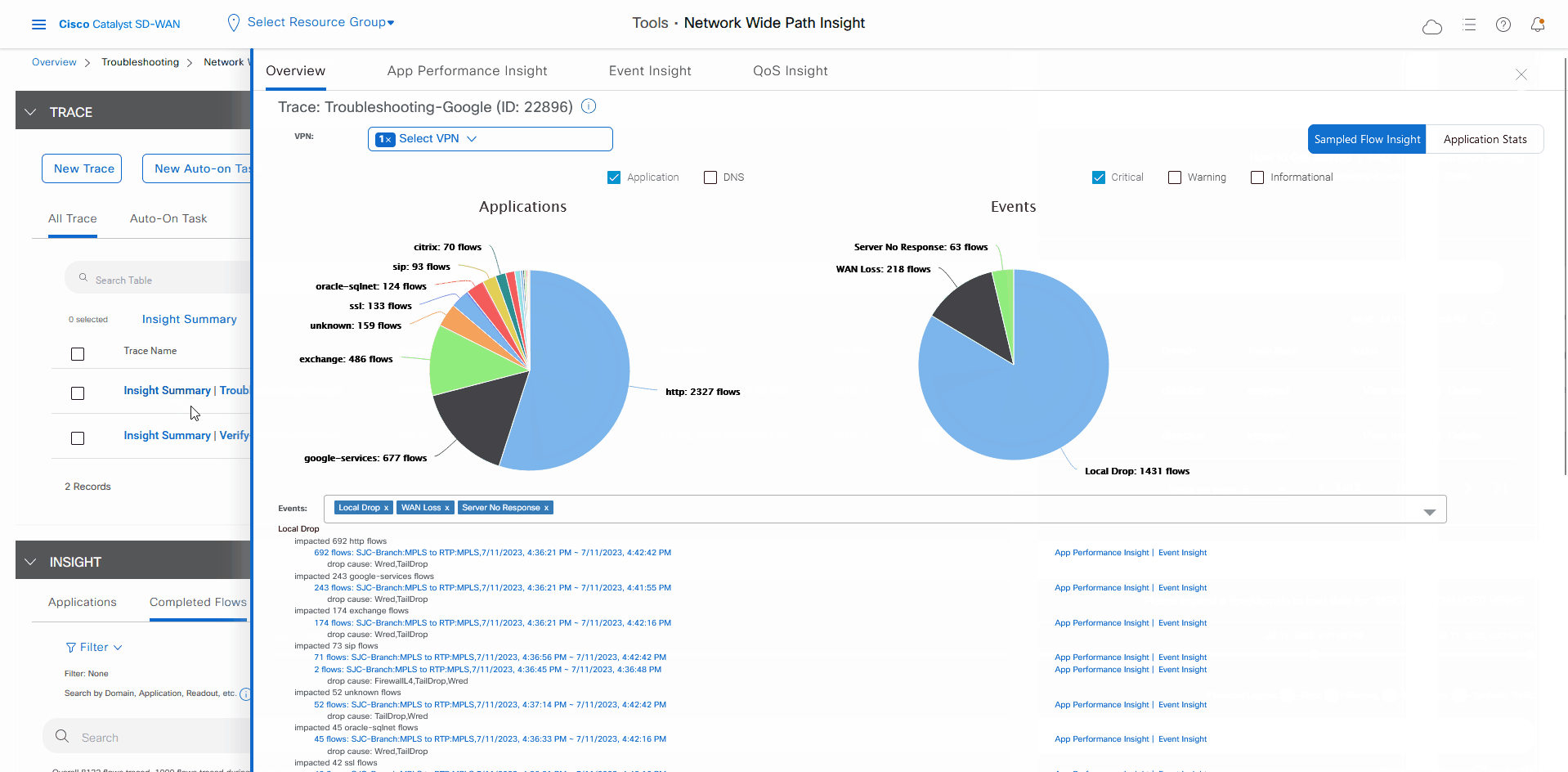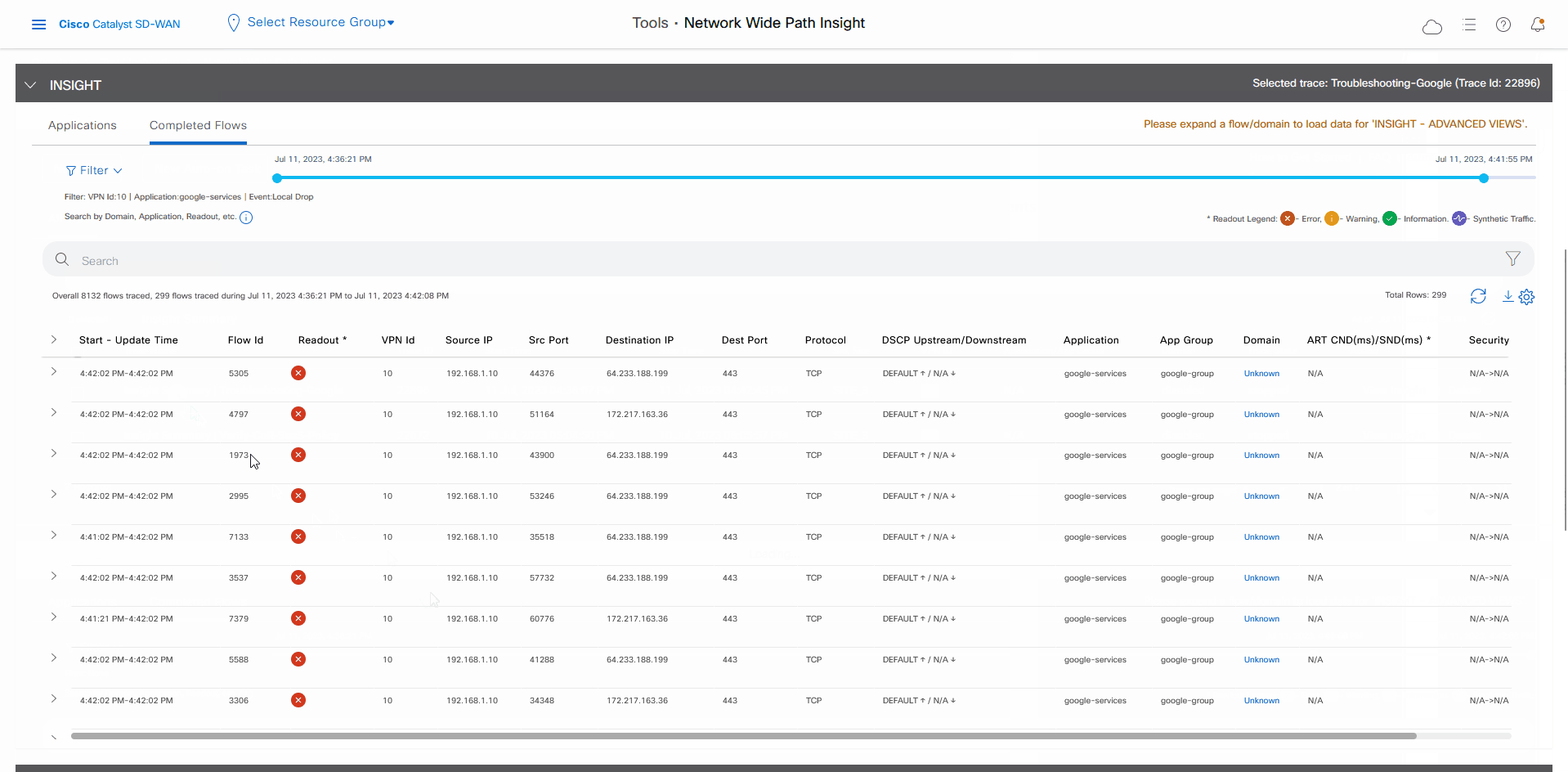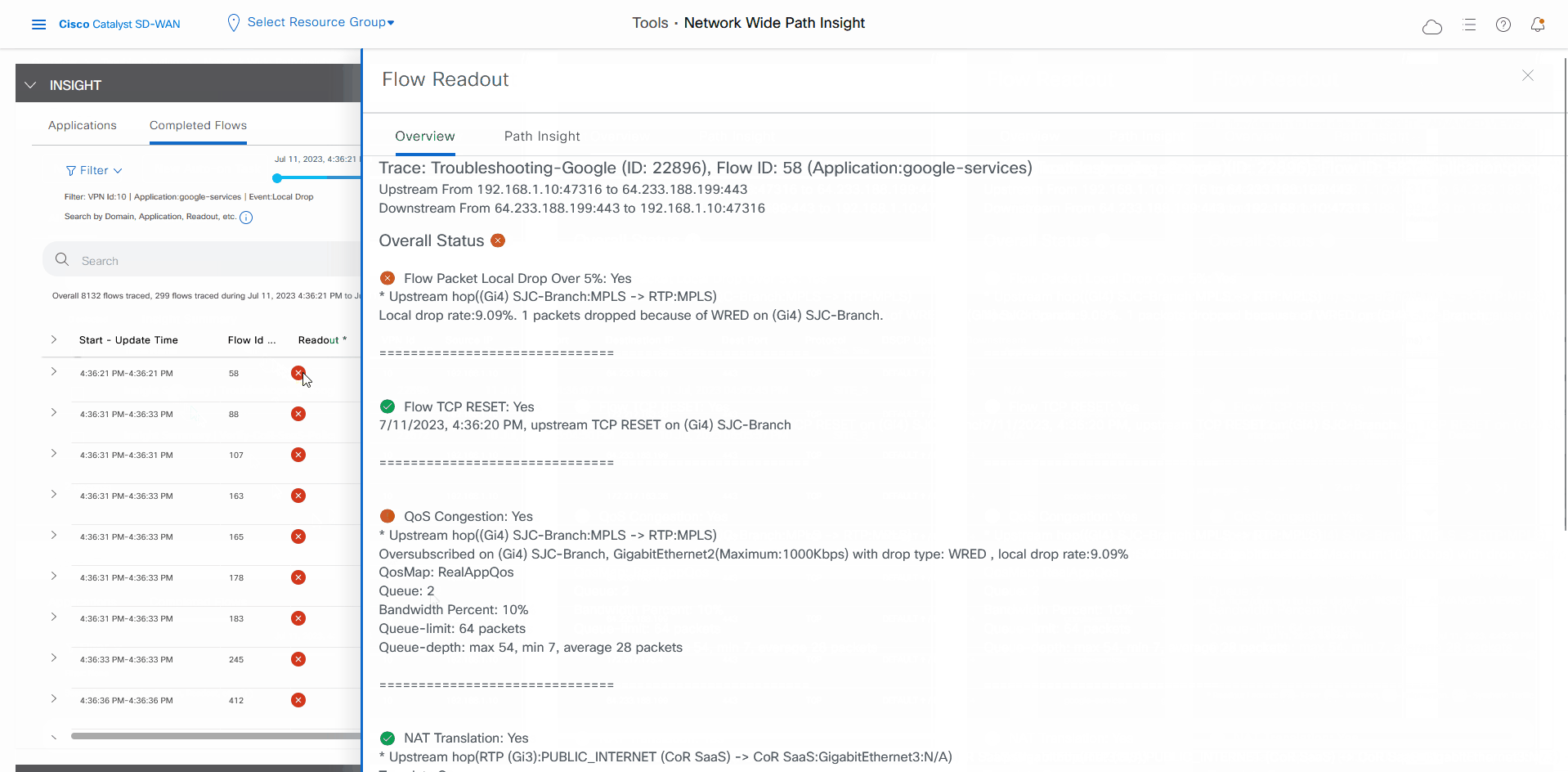
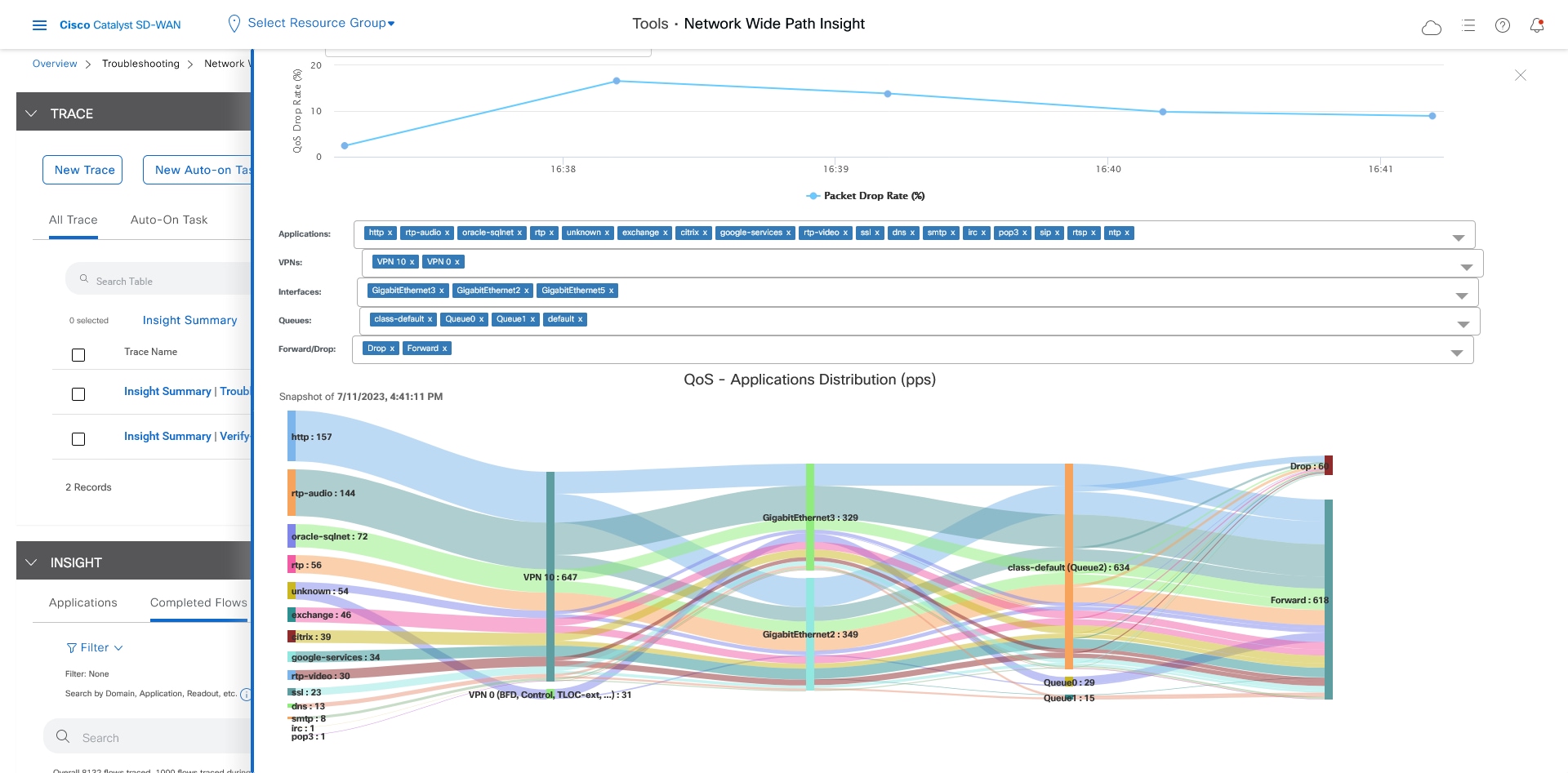
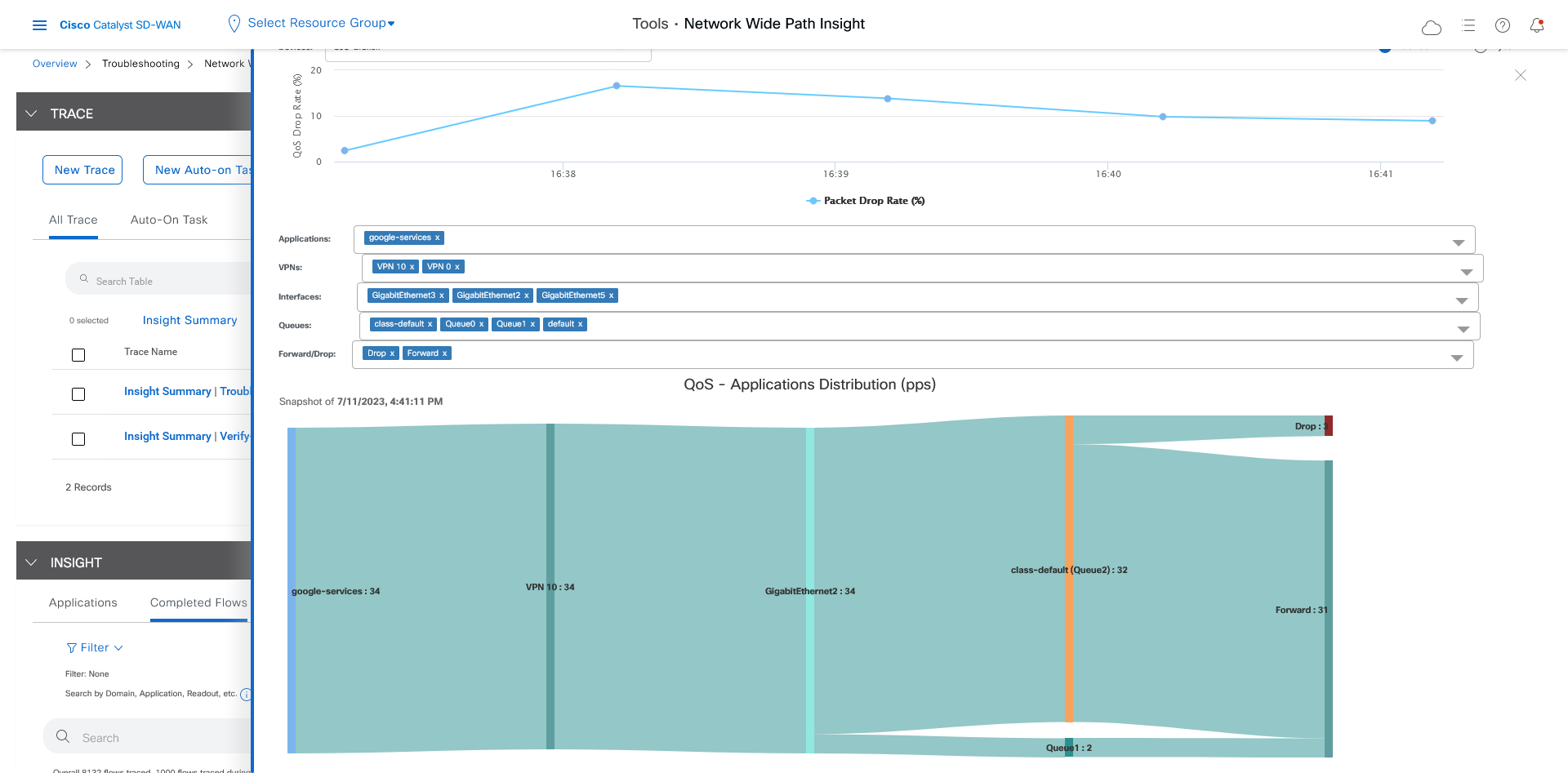
Let the trace run for approximately 5 minutes so that it can collect data, then perform the following actions to see a Sankey diagram that shows the network paths of Microsoft Office 365 applications traffic. This application-level information lets you see whether the traffic is taking the expected network path according to your Cisco Catalyst SD-WAN Cloud OnRamp for SaaS policy.
-
In the list of traces in the All Trace tab, click Insight Summary in the row that shows the Verify-Cor-Saas-Policy trace.
-
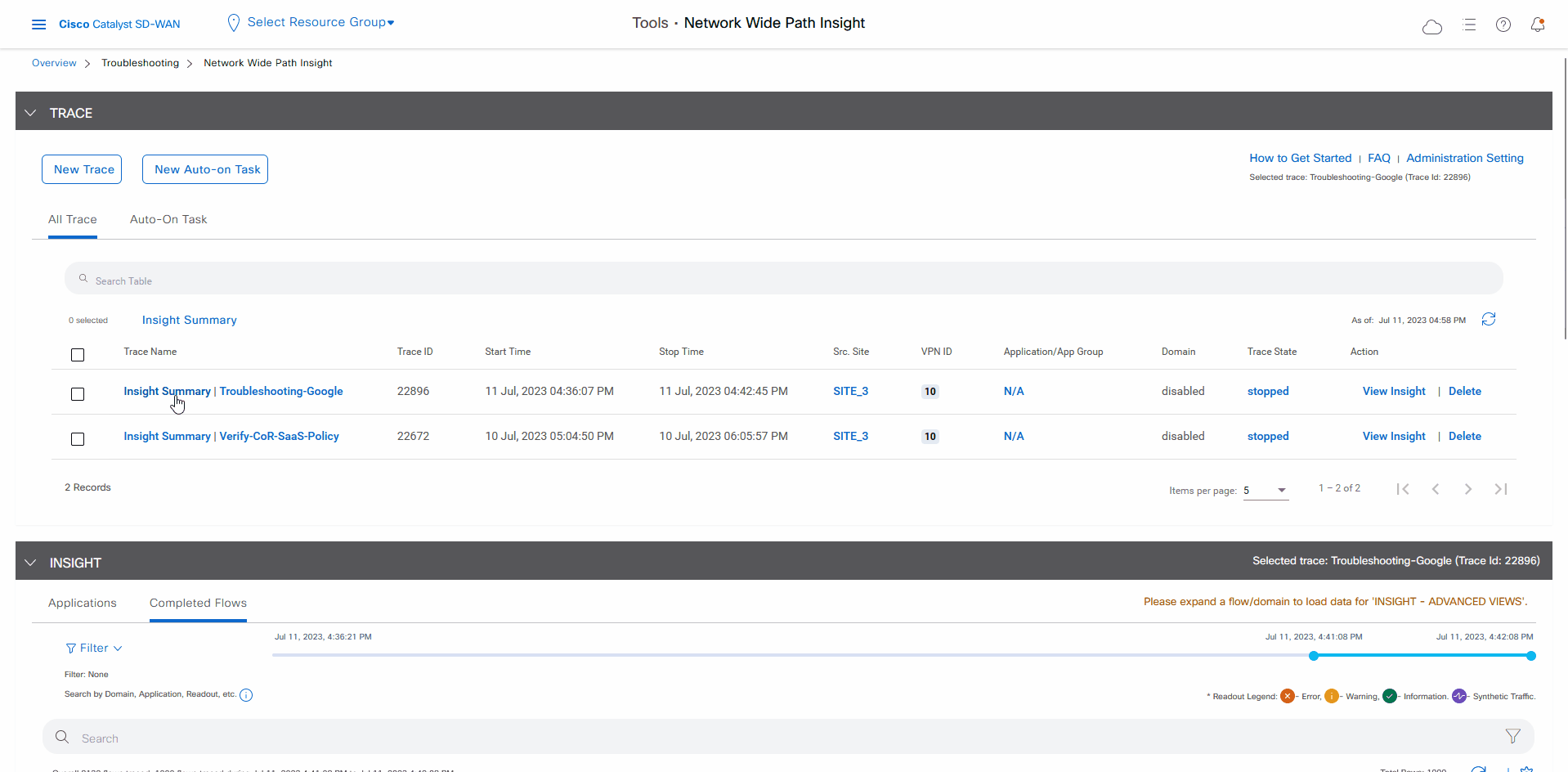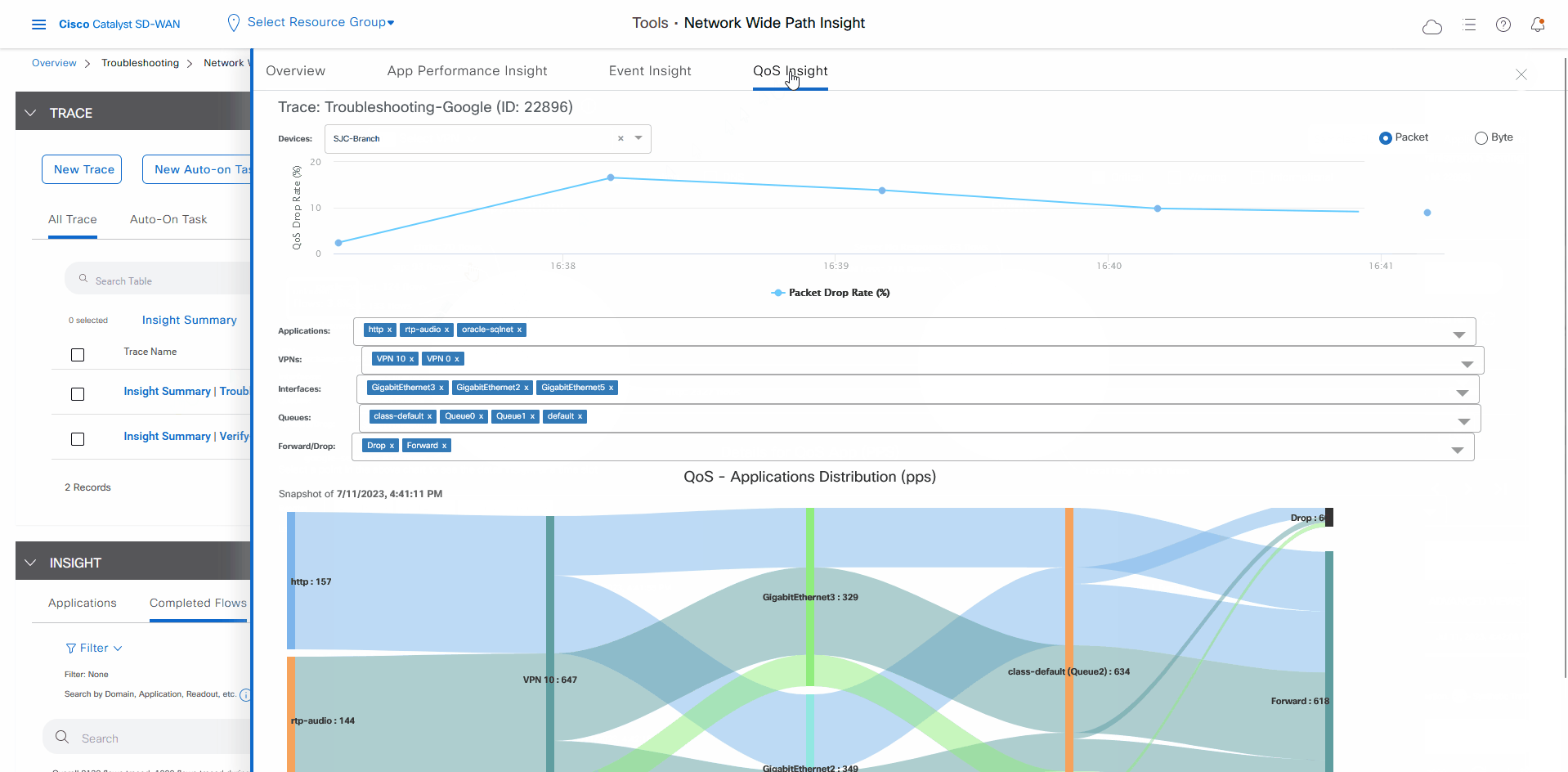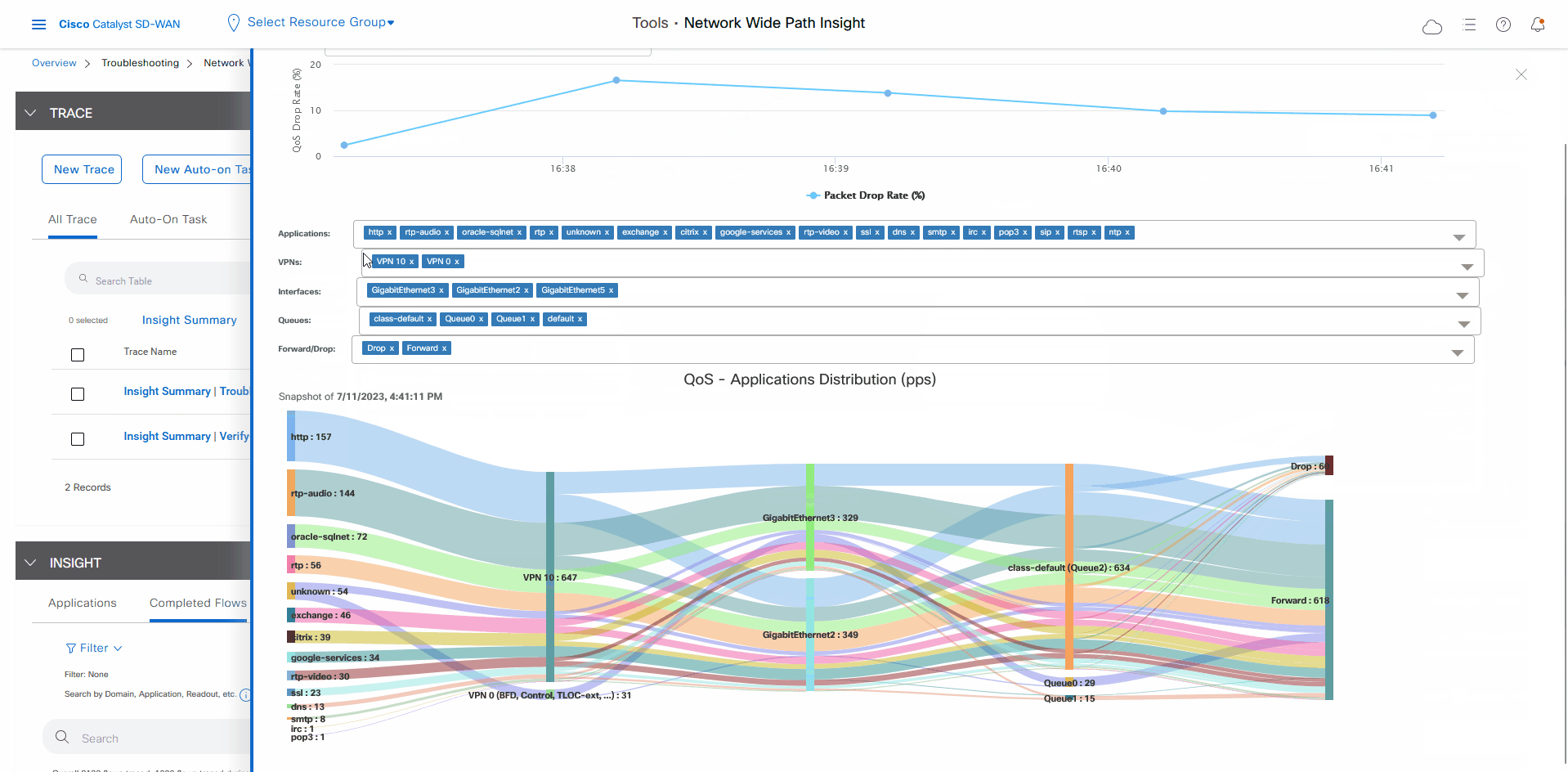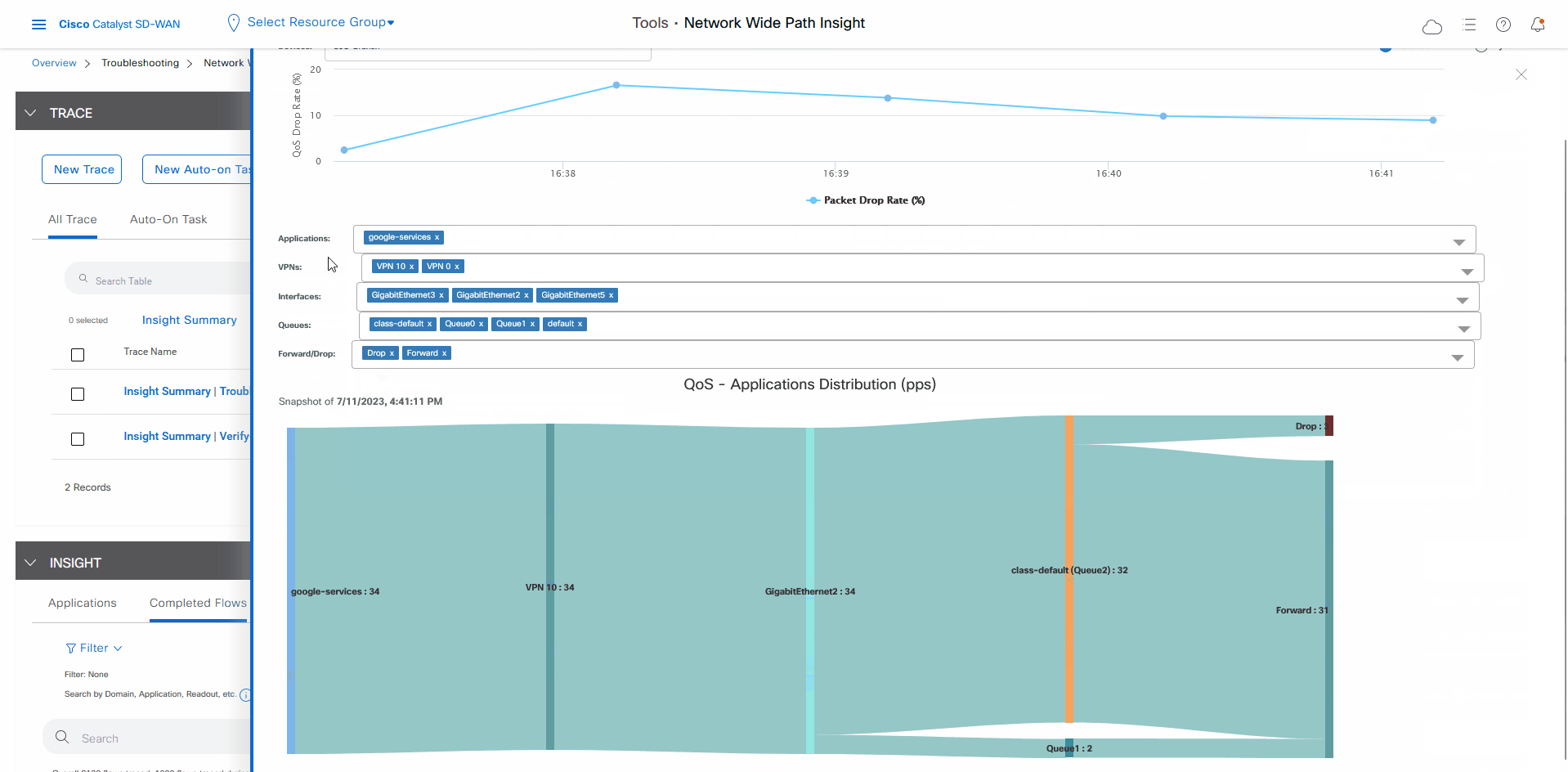
In the Insight Summary slide-in pane, choose the App Performance Insight tab and use the filters to see the Sankey chart that shows the network paths of Microsoft applications traffic.
The Sankey chart shows that this traffic flows directly from the SJC branch to the SaaS cloud-based host.
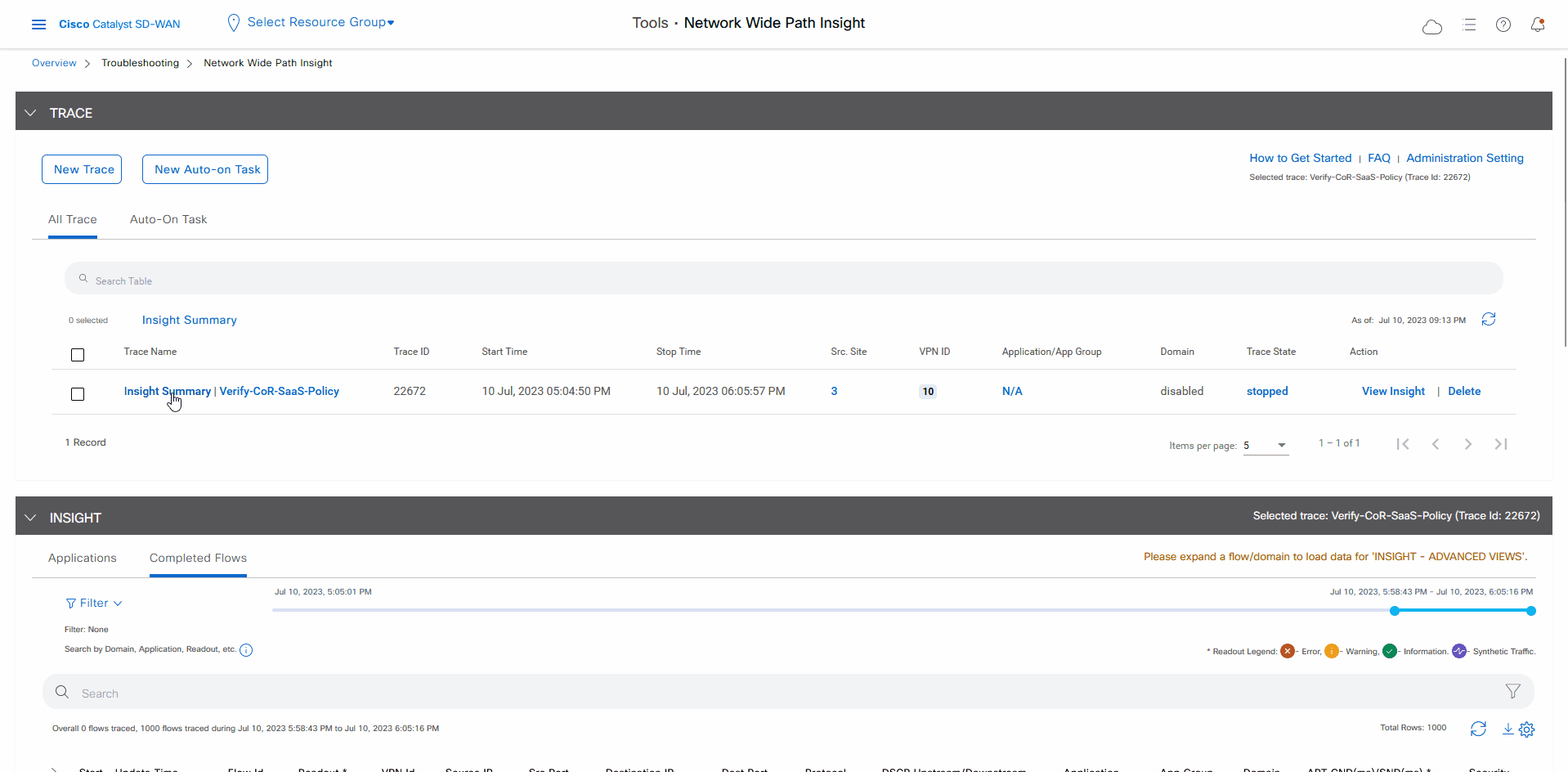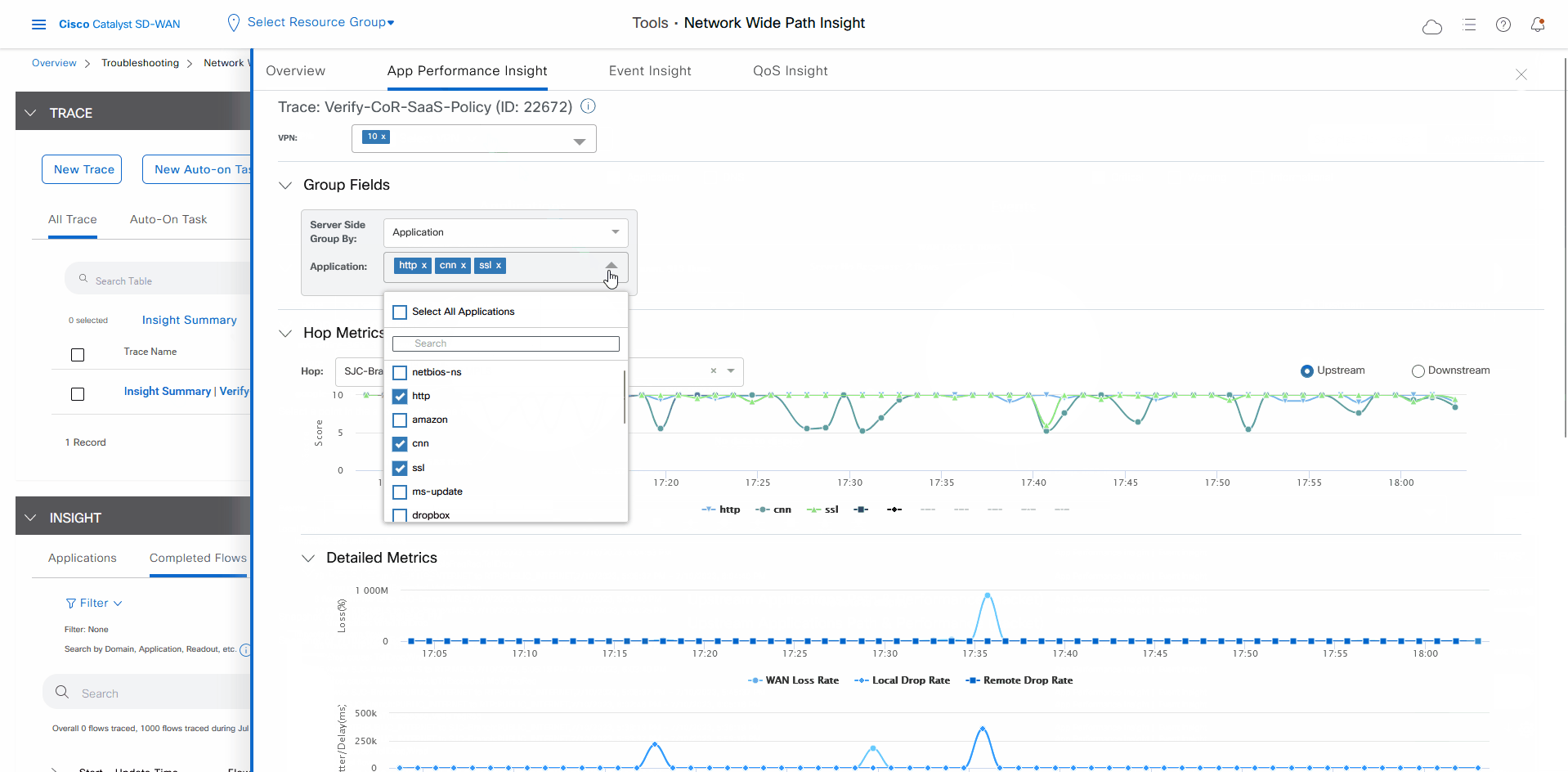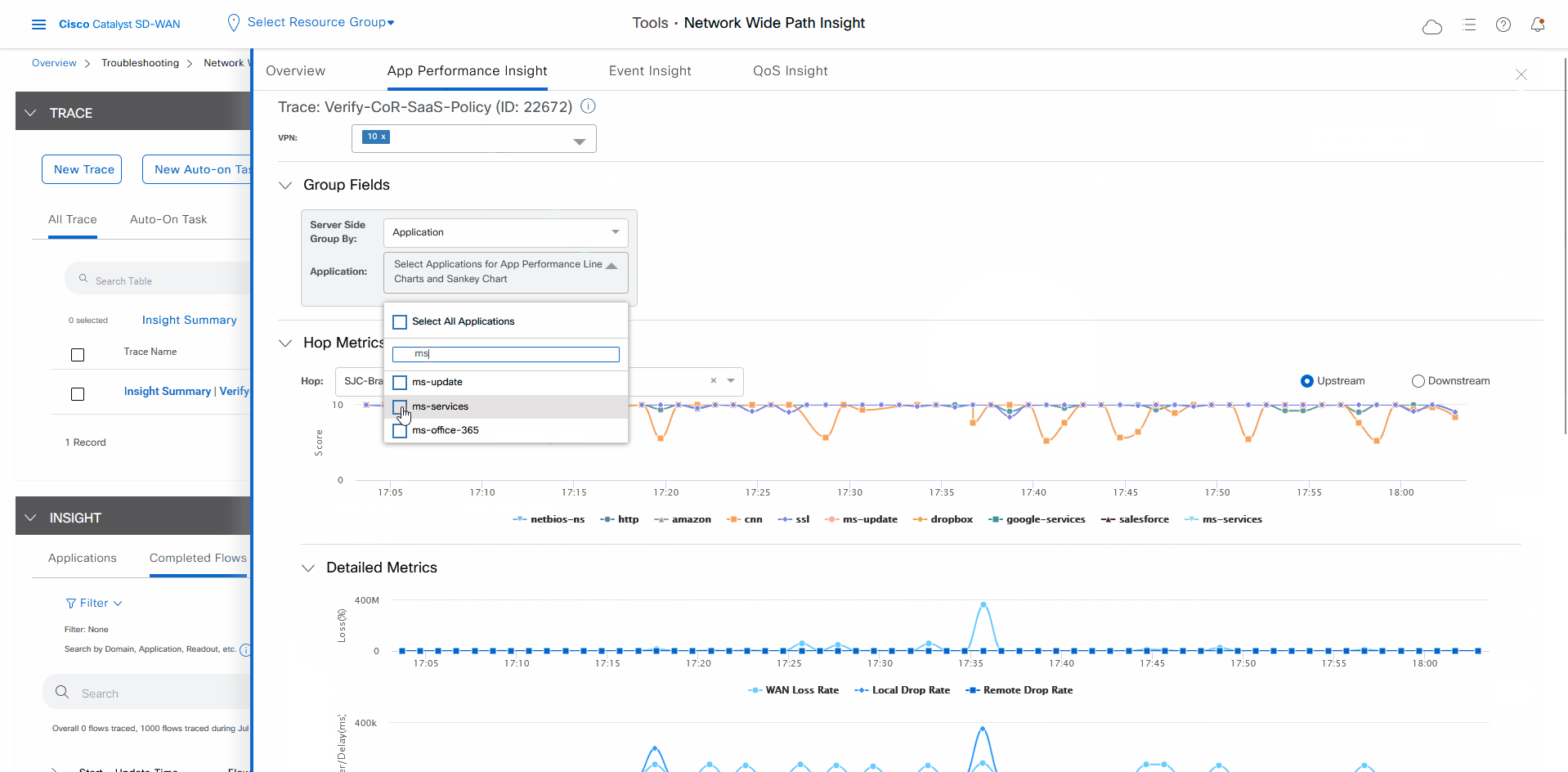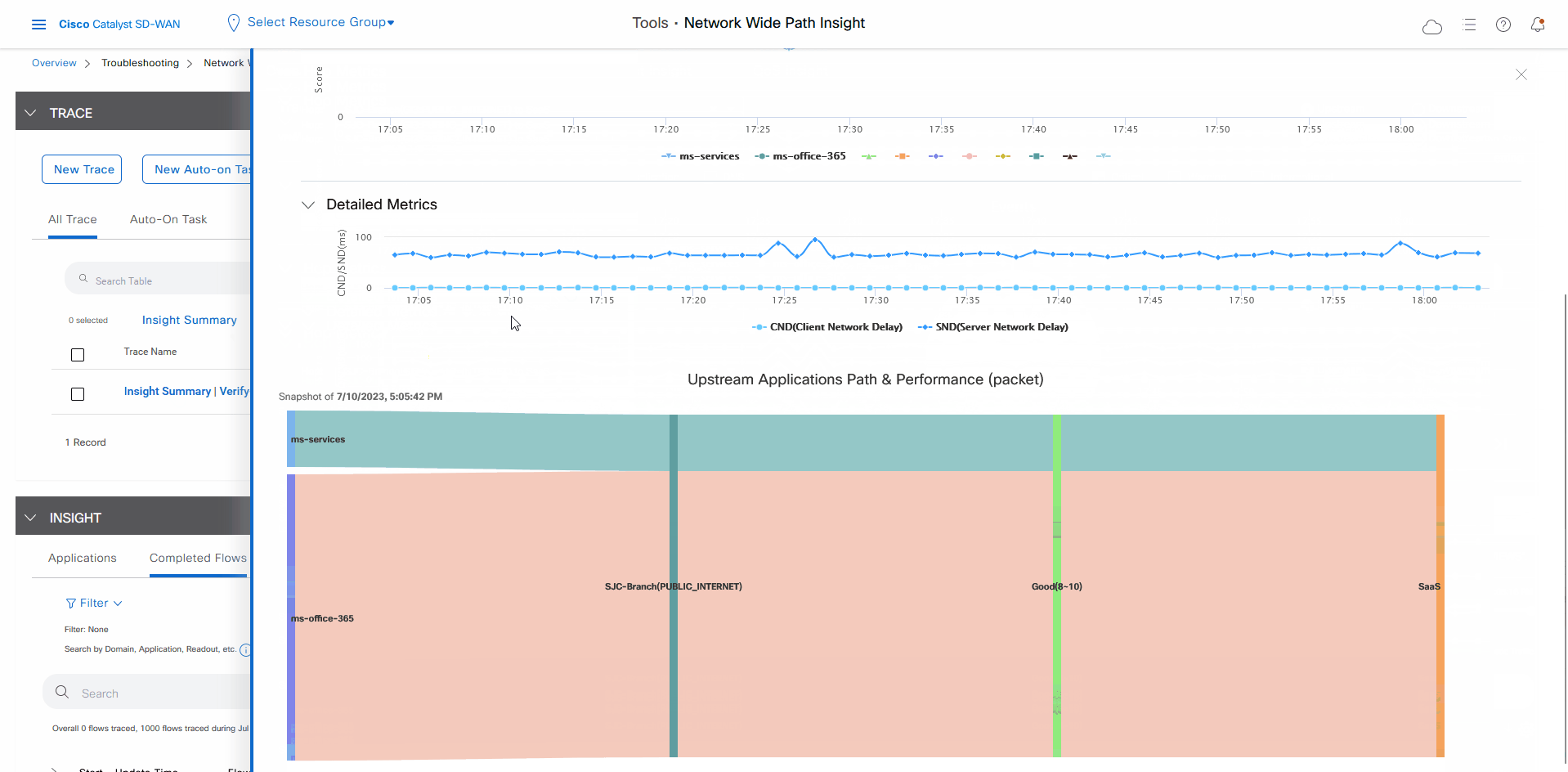
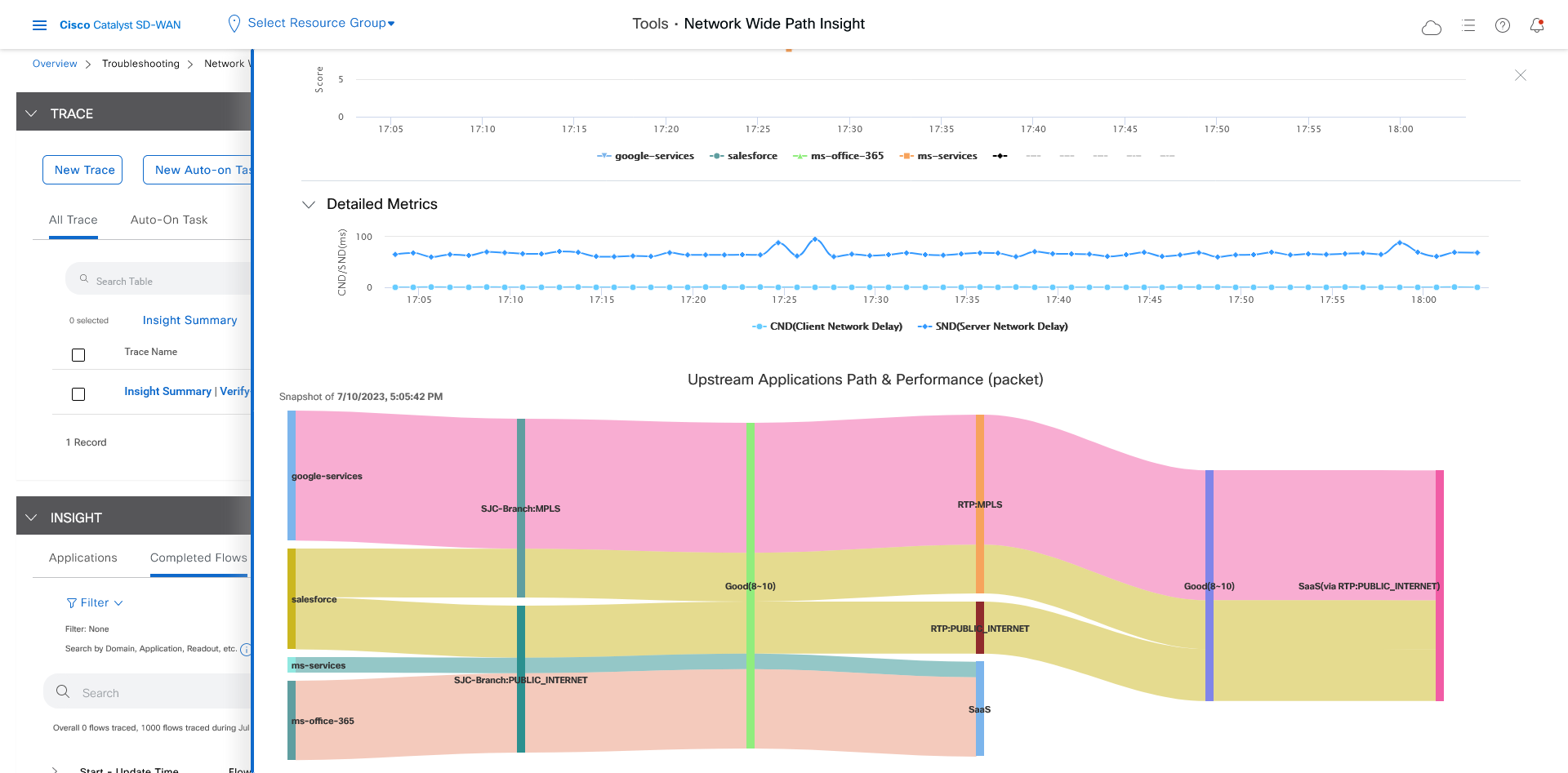
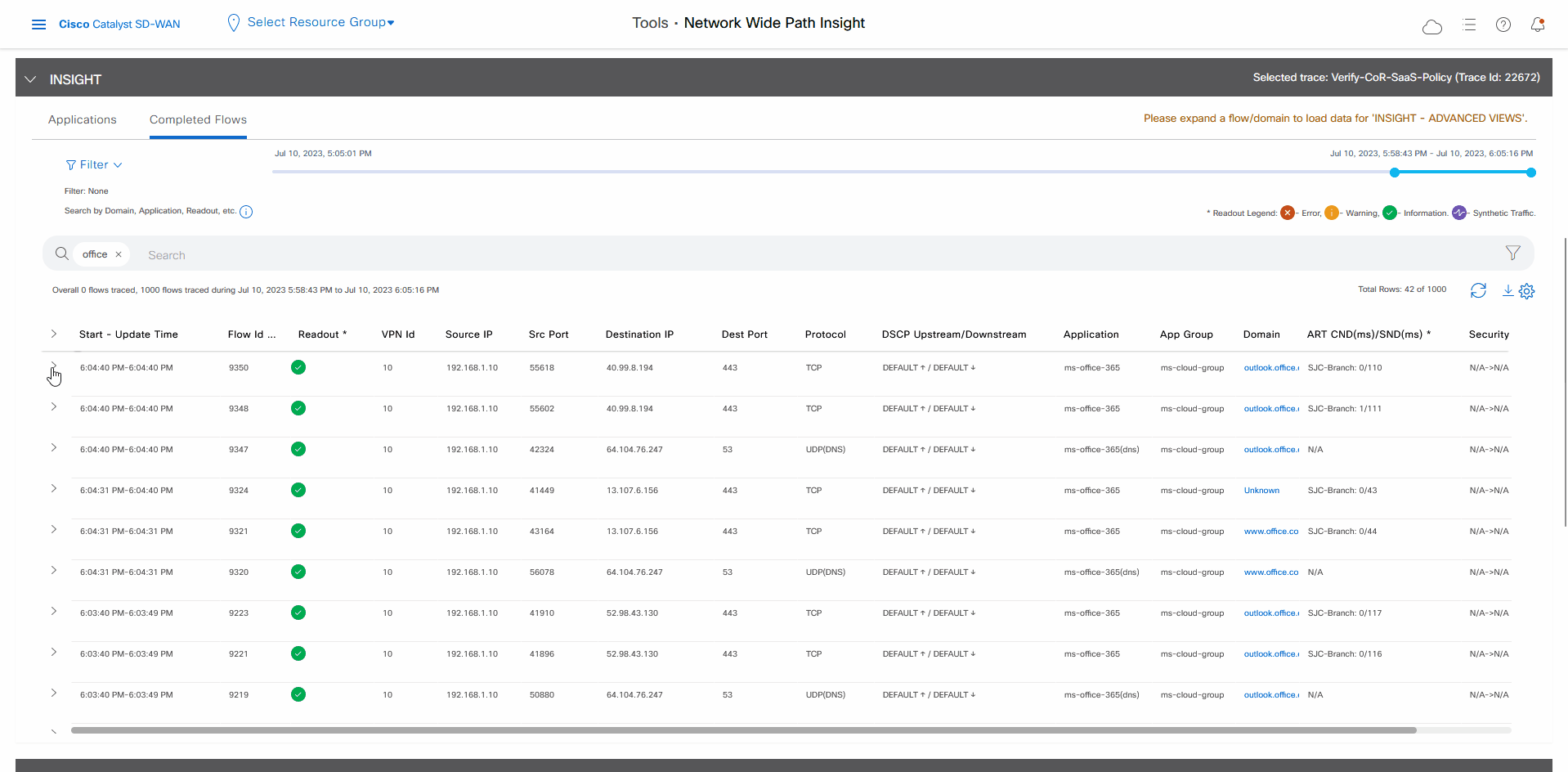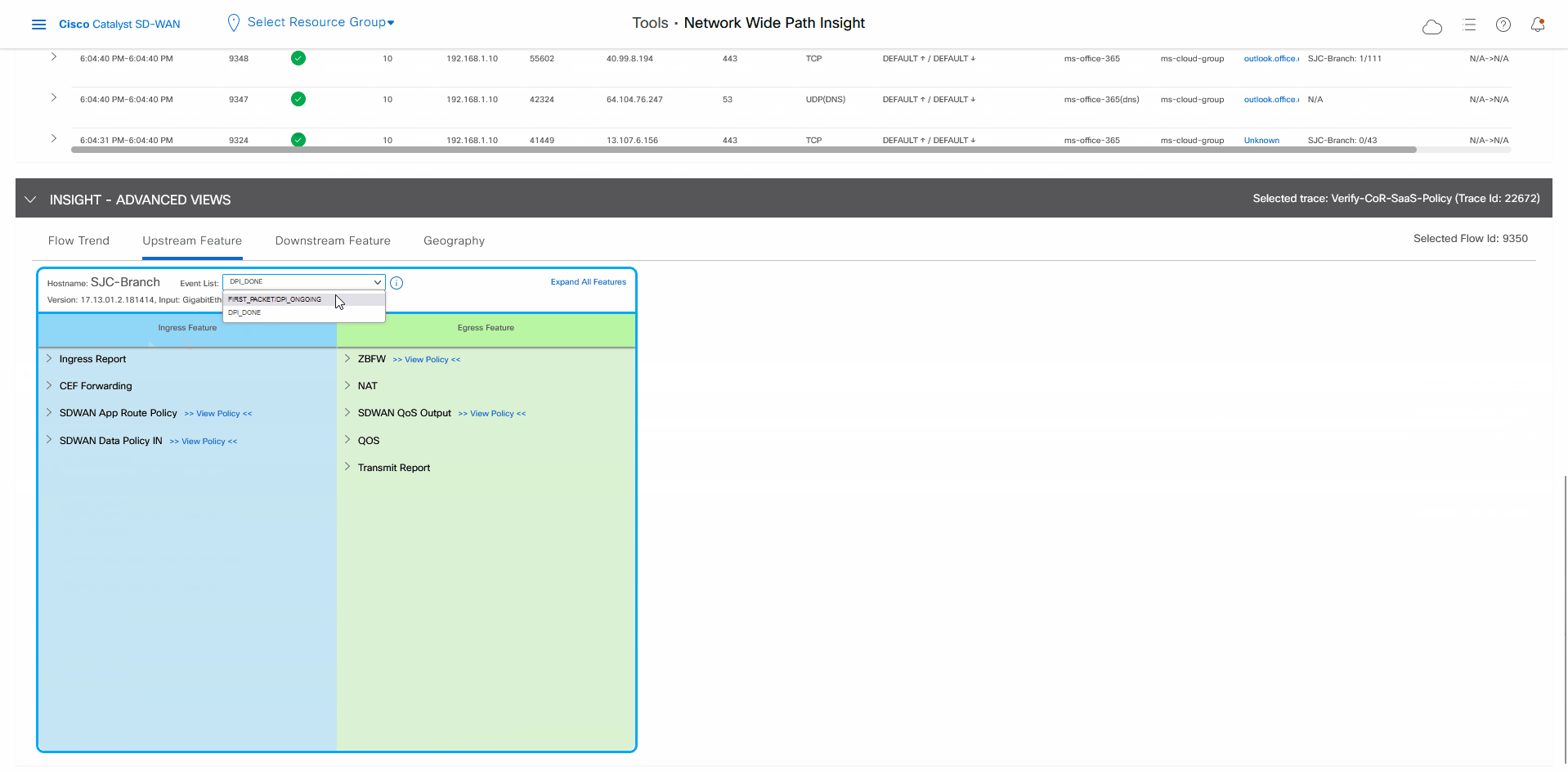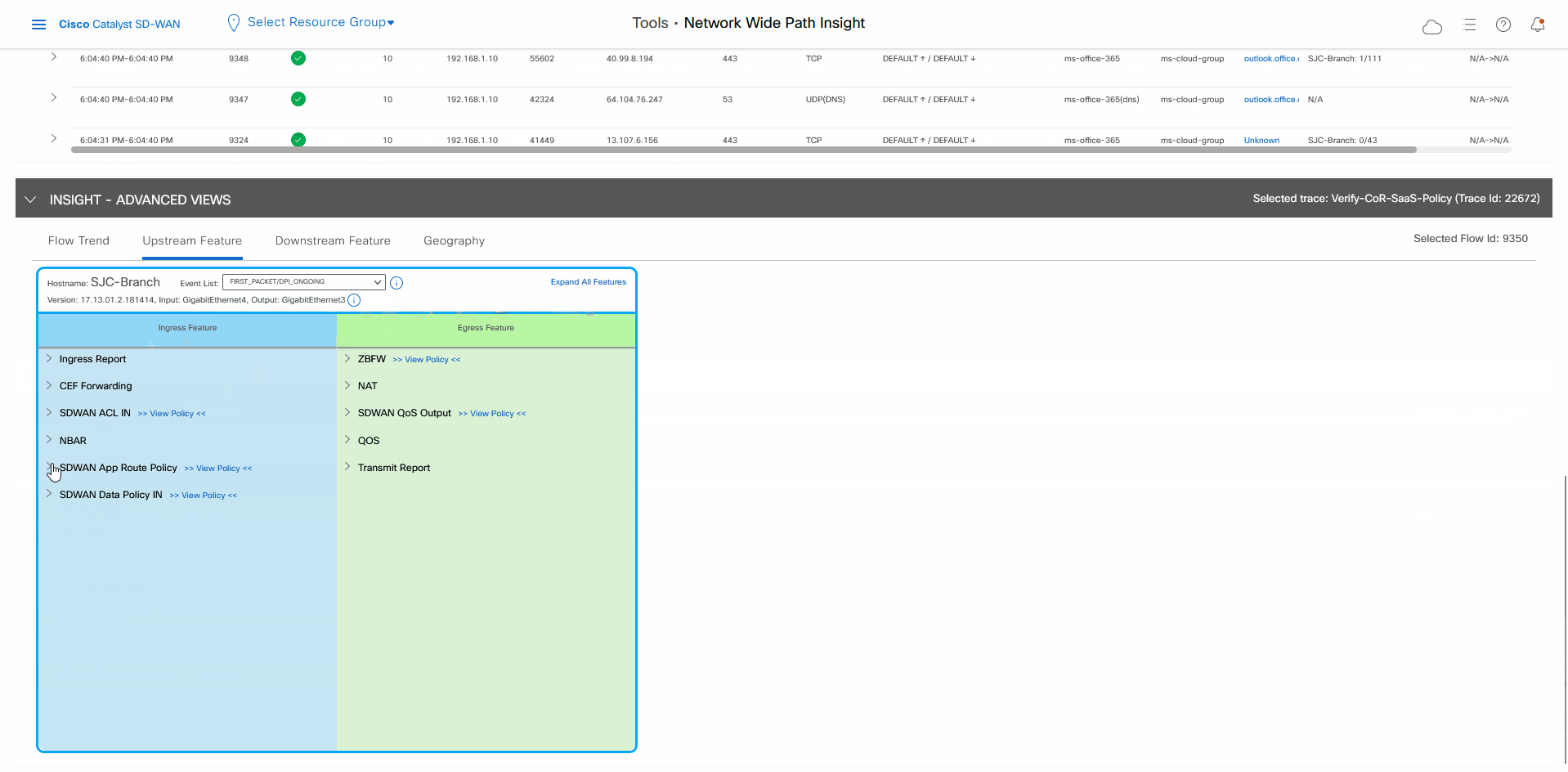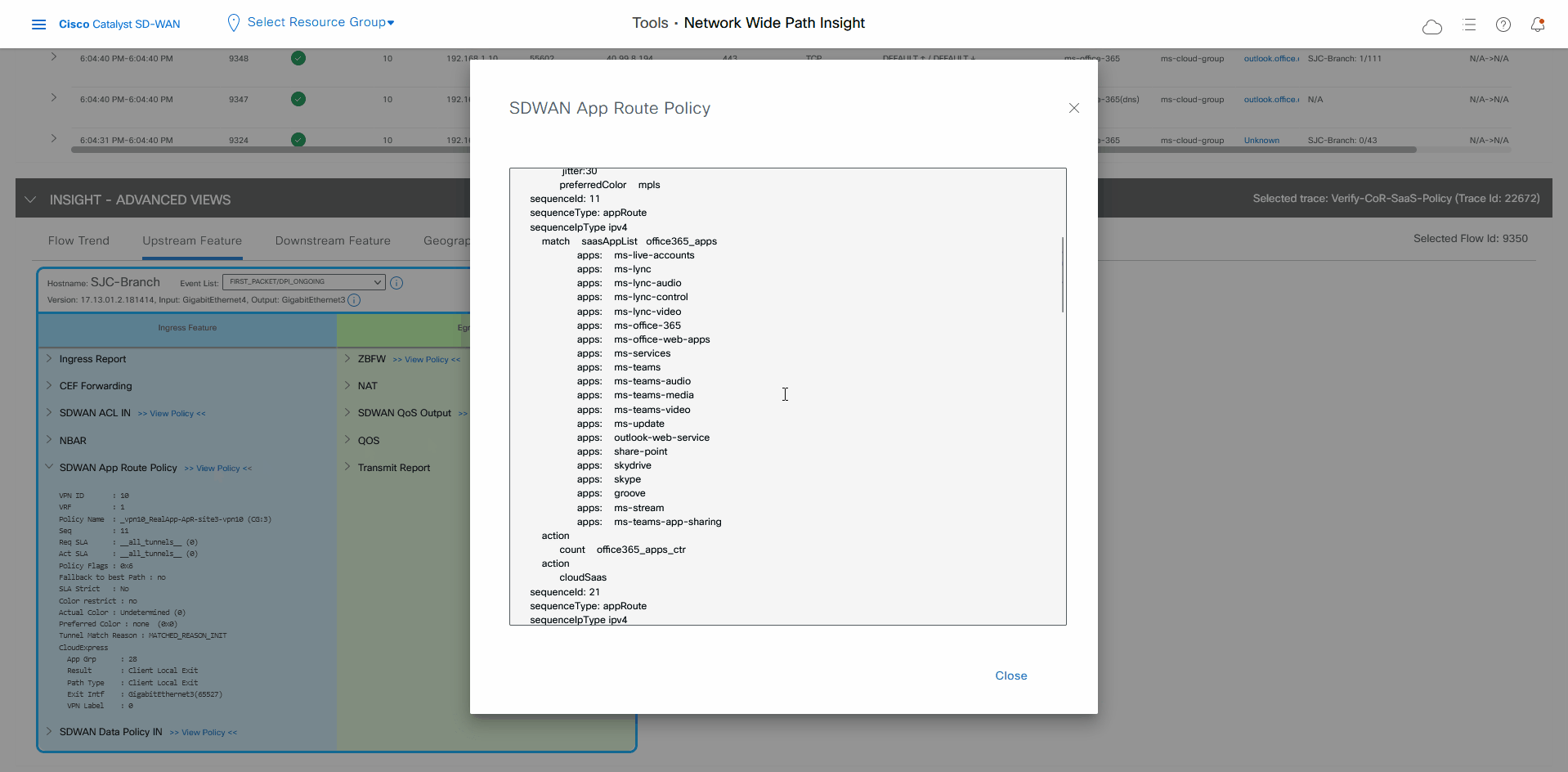
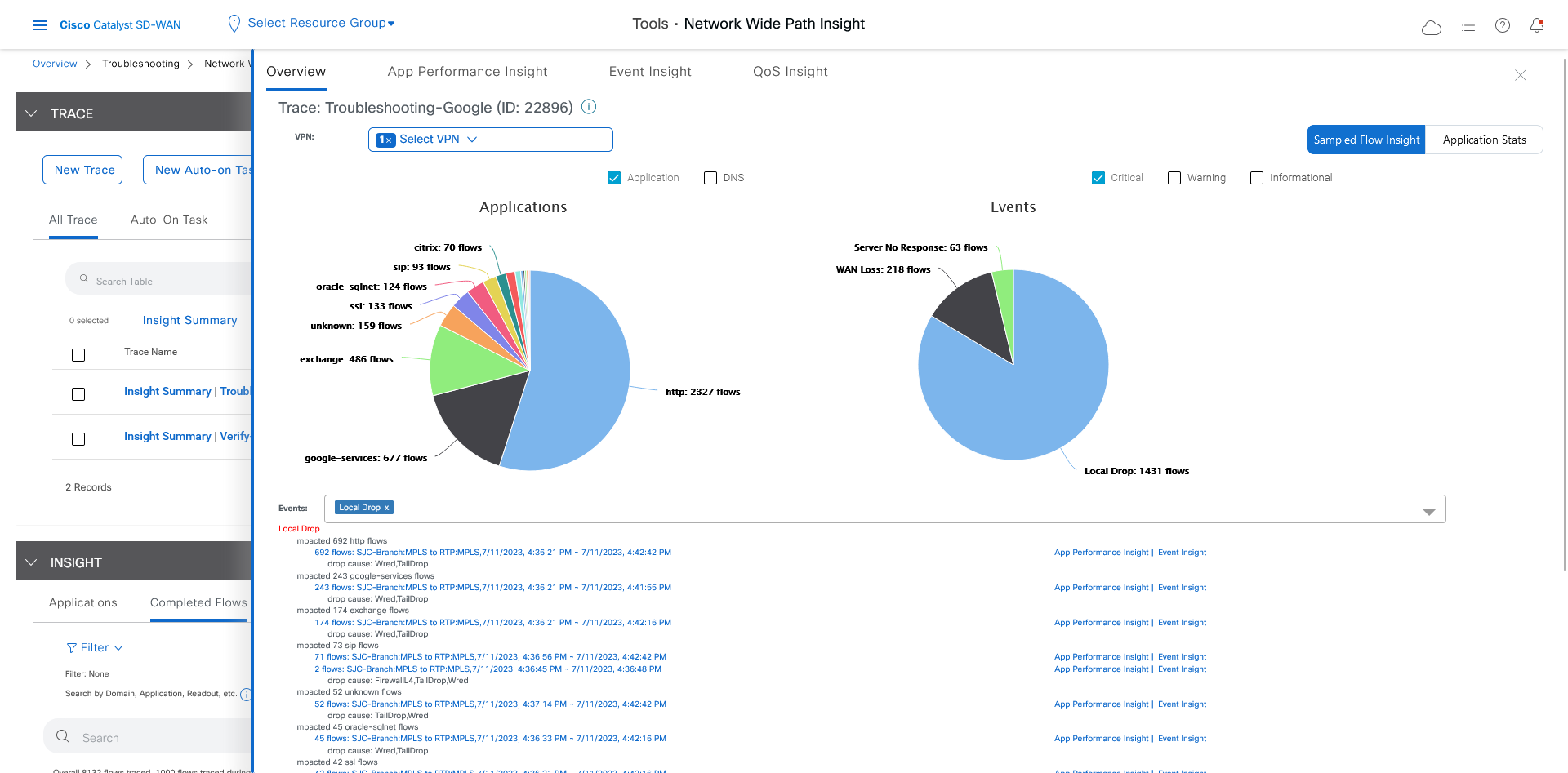
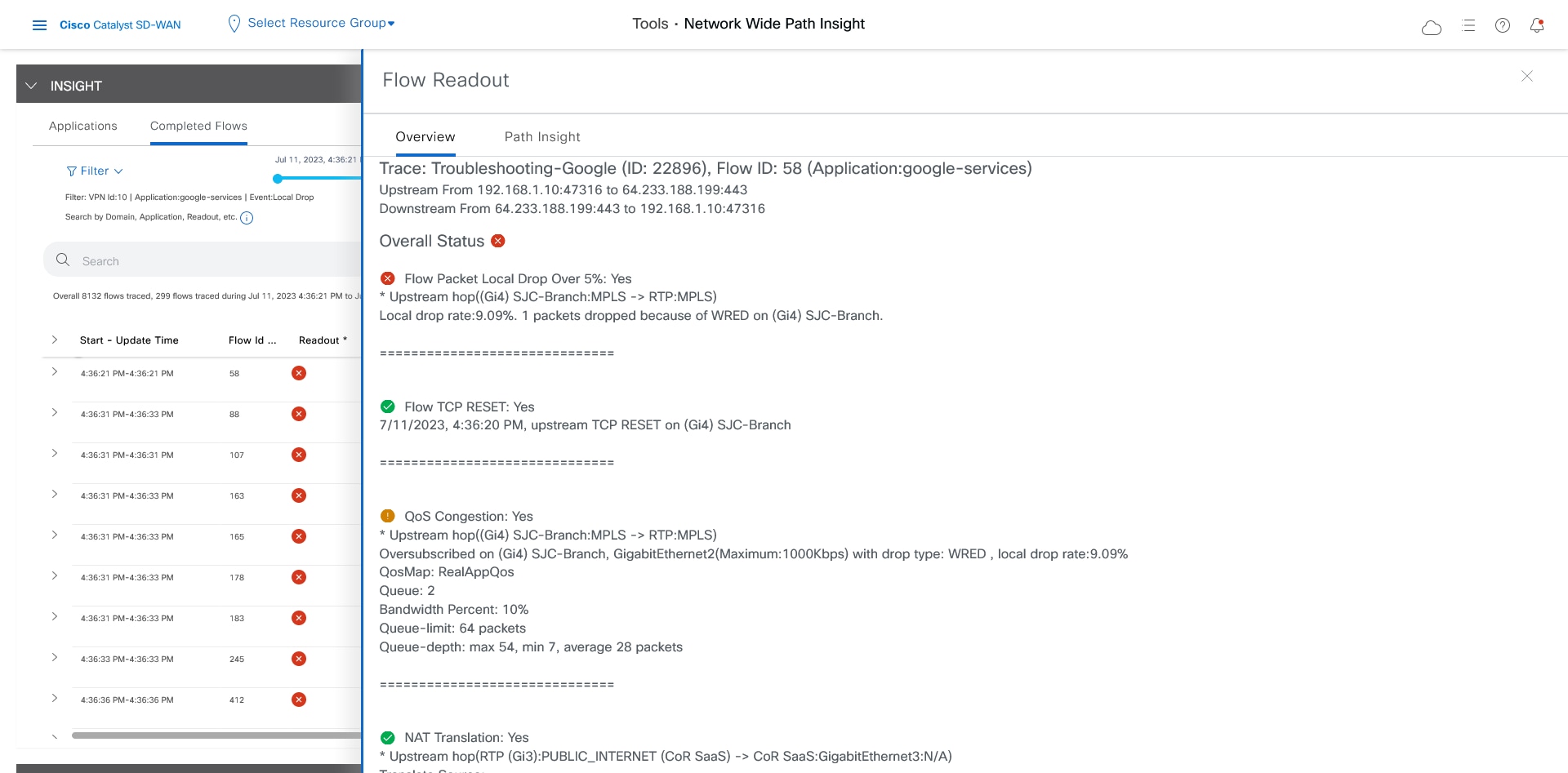
After reviewing application-level data, you can check whether your Cisco Catalyst SD-WAN Cloud OnRamp for SaaS policy took effect for Microsoft Office 365 applications traffic. To do so, look at flow-level information for this traffic:
-
In the All Trace tab, go to the Completed Flows tab in the Insight area.
-
Search for Office.
-
For any Microsoft Office 365 flow, click the green check mark in the Readout column to display the Flow Readout slide-in pane.
-
Click the Path Insight tab in the Flow Readout pane.
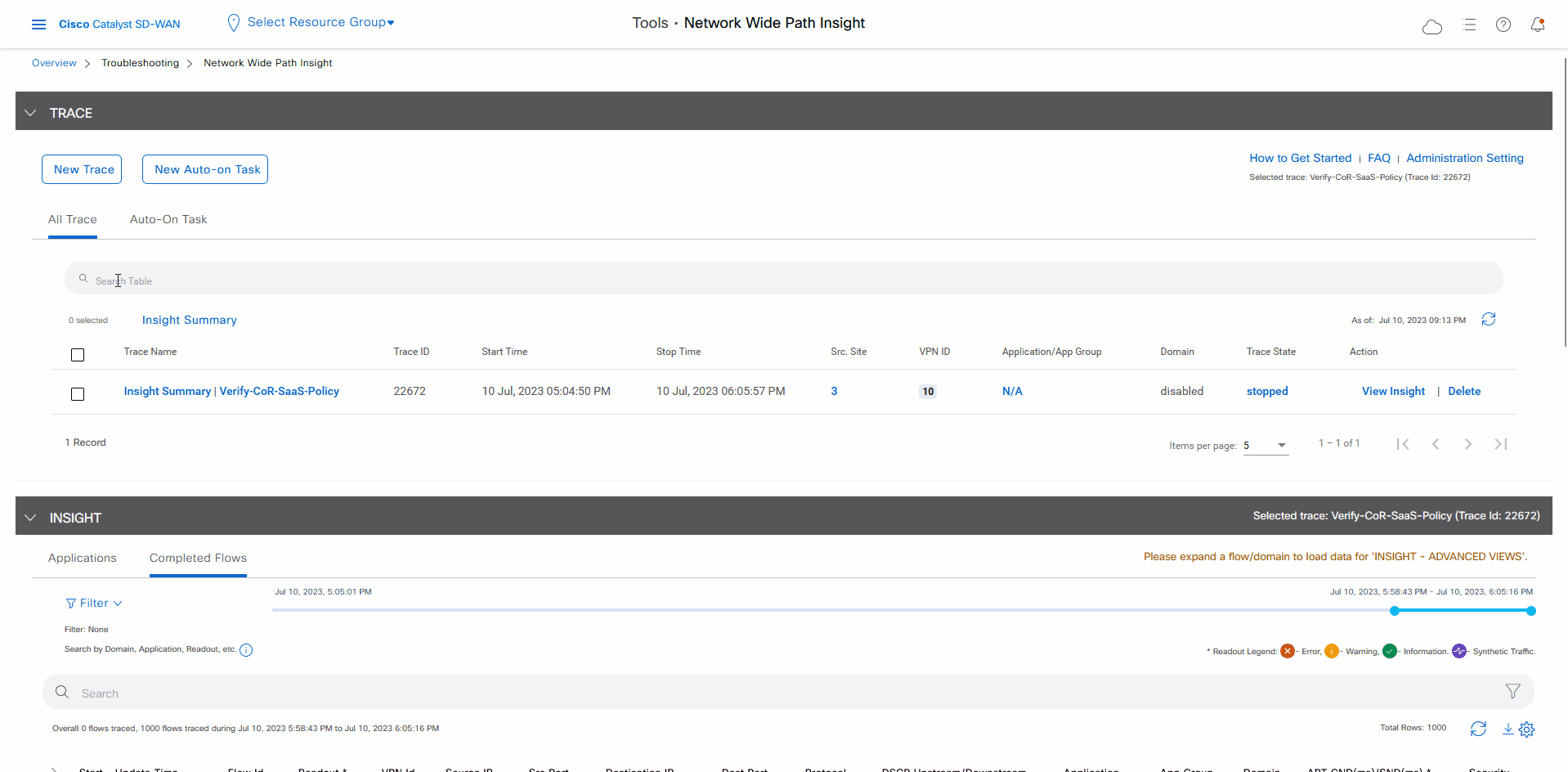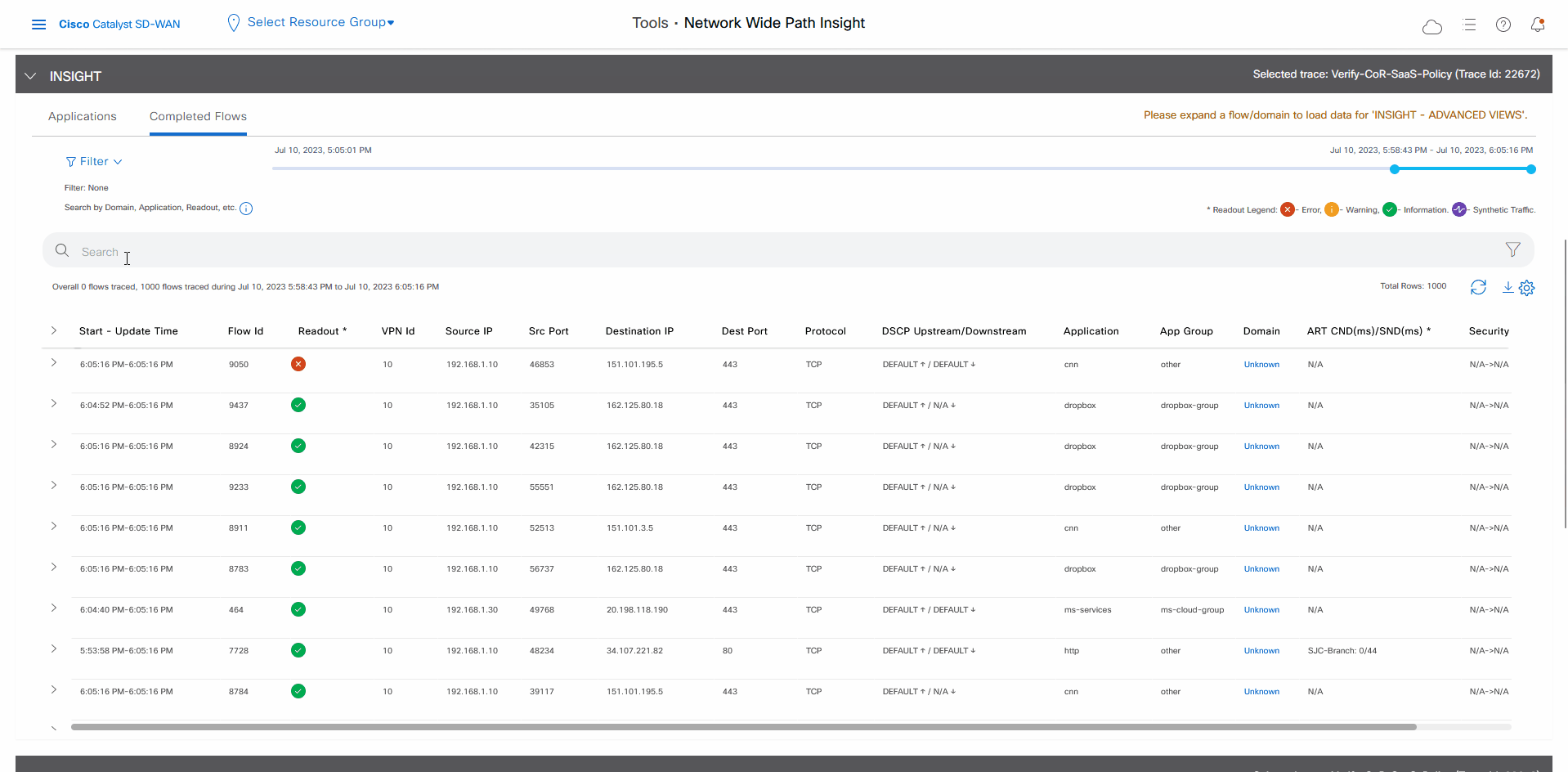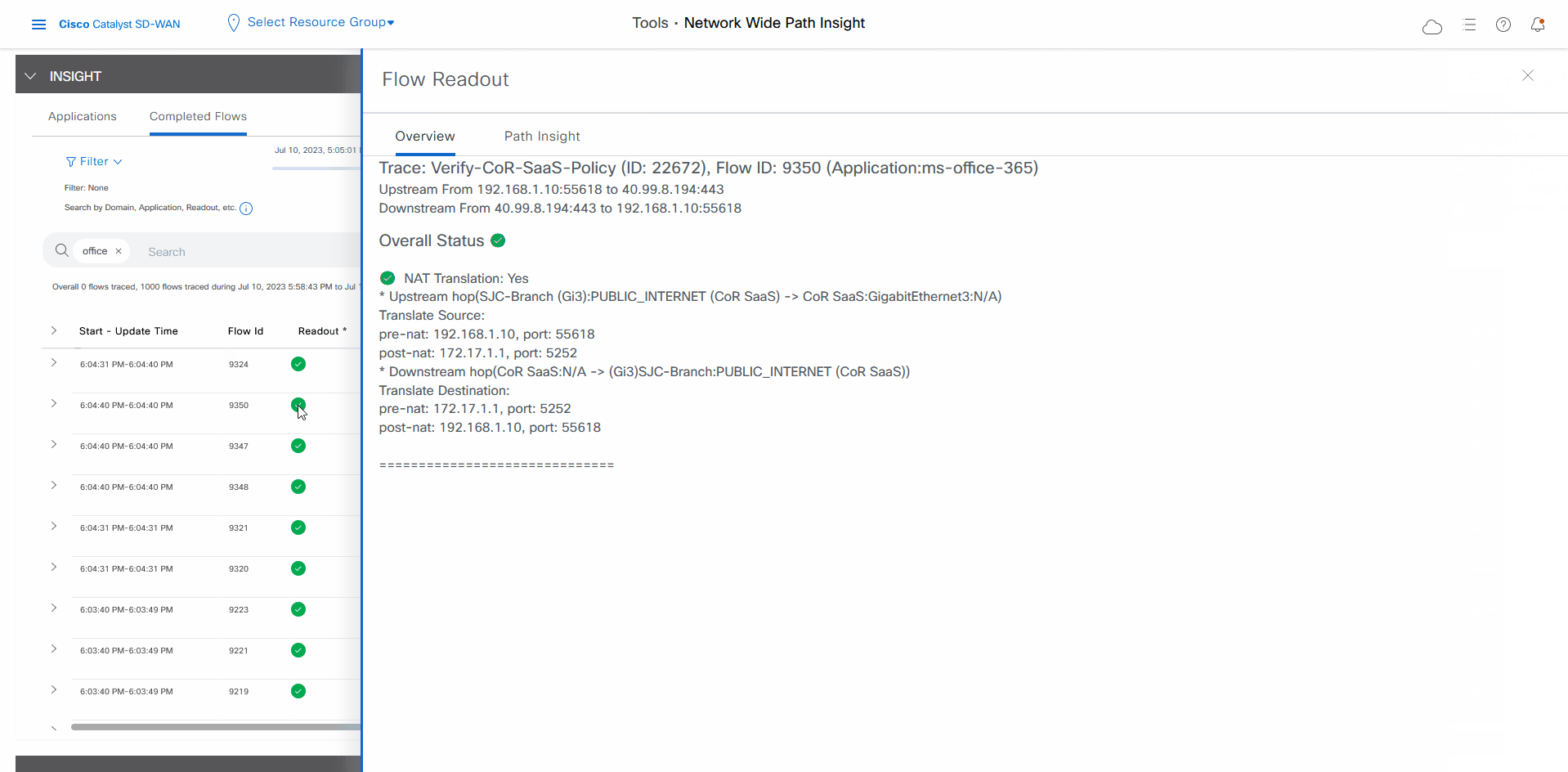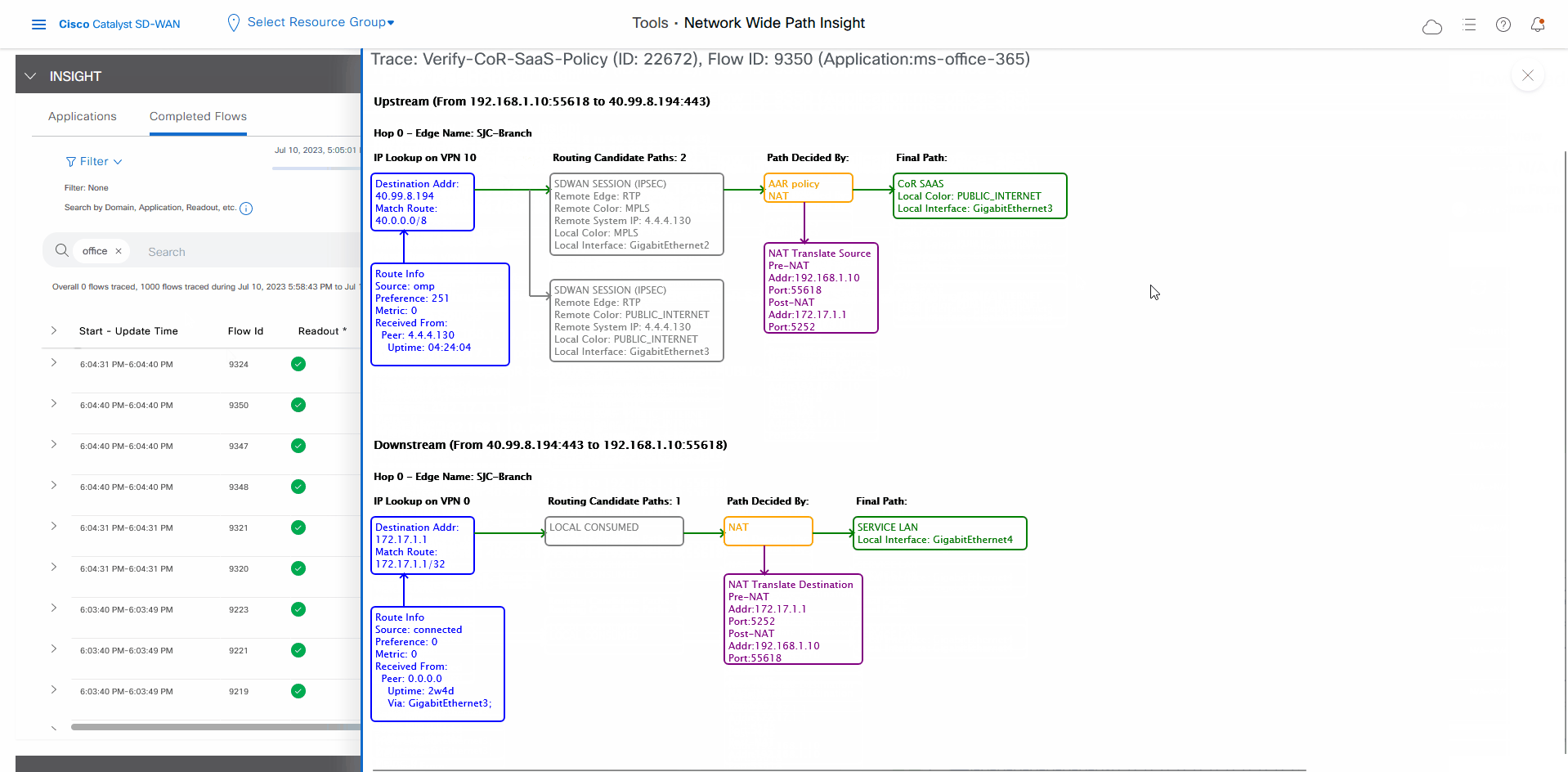
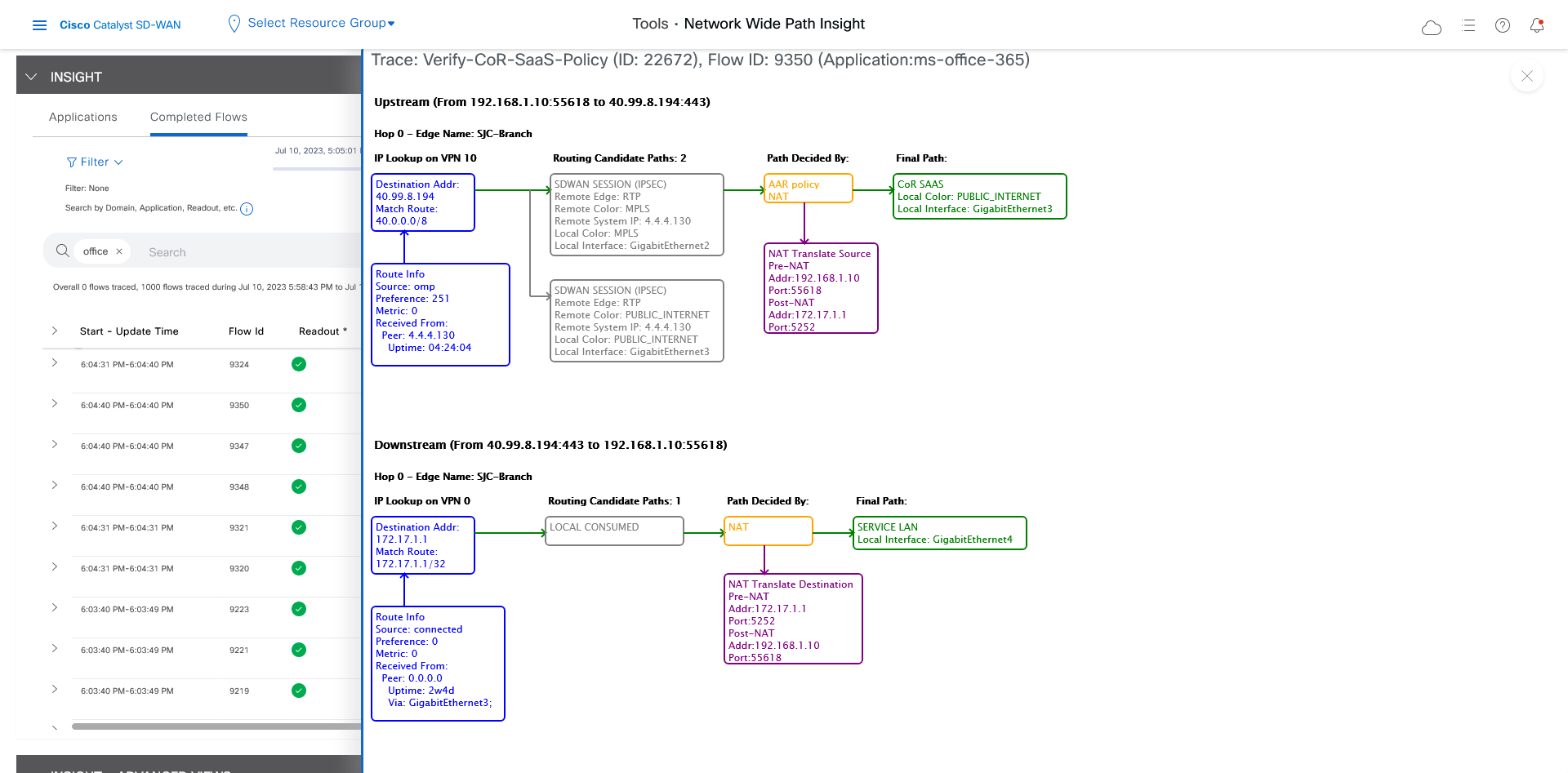
Finally, you can confirm how the App-route policy is programmed. This information lets you validate that Microsoft Office 365 applications traffic flows through the link that is intended according to your Cisco Catalyst SD-WAN Cloud OnRamp for SaaS policy, which is a part of the App-route policy.
-
In the All Trace tab, go to the Completed Flows tab in the Insight area.
-
Expand any Microsoft Office 365 flow by clicking the right-arrow icon at the beginning of the row.
-
Scroll down to the Insight – Advanced Views area.
-
In the Upstream Feature tab:
-
Choose an event from the Event List drop-down list.
-
Click Expand All Features to see detailed ingress and egress information about the features that are executed for the flow, then click Collapse All Features.
-
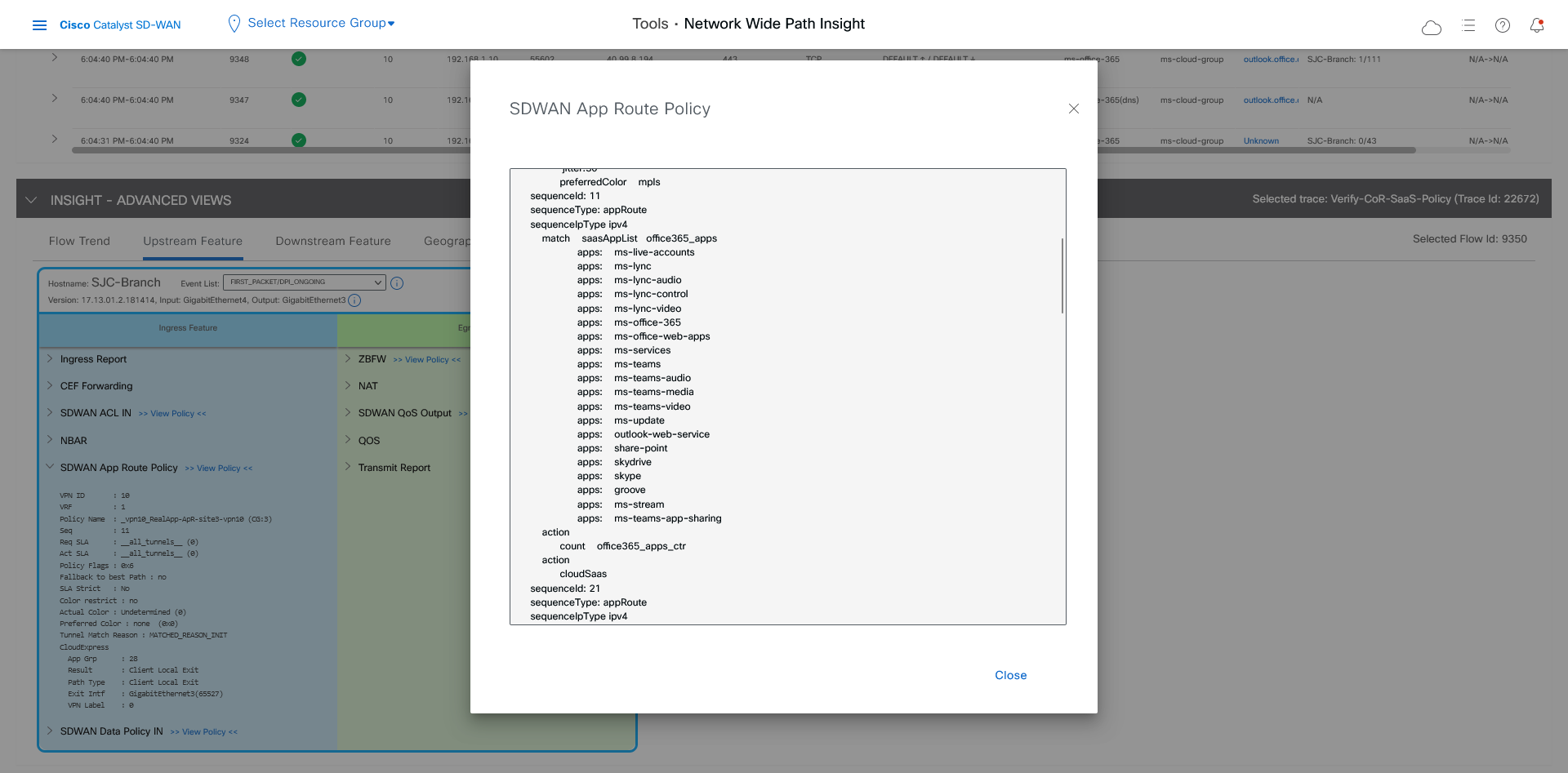
In the Ingress Feature area, expand SDWAN App Route Policy to see policy information.
-
Click View Policy next to SDWAN App Route Policy to see the policy programming.
-
 Feedback
Feedback