Configuring Devices using vManage
Use the Devices screen to add and delete devices, toggle the mode of a device between CLI and vManage, upload the WAN Edge Serial number file, export bootstrap configuration and, and perform other device-related tasks.


|
1 |
Menu |
|
2 |
CloudExpress |
|
3 |
Tasks |
|
4 |
Alarms |
|
5 |
Help |
|
6 |
User Profile |
Change Configuration Modes
A device can be in either of these configuration modes:
-
vManage mode–A template is attached to the device and you cannot change the configuration on the device by using the CLI.
-
CLI mode – No template is attached to the device and the device can be configured locally by using the CLI.
When you attach a template to a device from vManage, it puts the device in vManage mode. You can change the device back to CLI mode if needed to make local changes to its configuration.
To toggle a router from vManage mode to CLI mode:-
In WAN Edge List tab, select a device.
-
Click the Change Mode drop-down and select CLI mode.
An SSH window opens. To log in to the device, enter a username and password. You can then issue CLI commands to configure or monitor the device.
To toggle a controller device from vManage mode to CLI mode:
-
In the Controllers tab, select a device.
-
Click the Change Mode drop-down.
-
Select CLI mode and then select the device type. The Change Mode CLI window opens.
-
From the vManage mode pane, select the device and click the right arrow to move the device to the CLI mode pane.
-
Click Update to CLI Mode.
An SSH window opens. To log in to the device, enter a username and password. You can then issue CLI commands to configure or monitor the device.
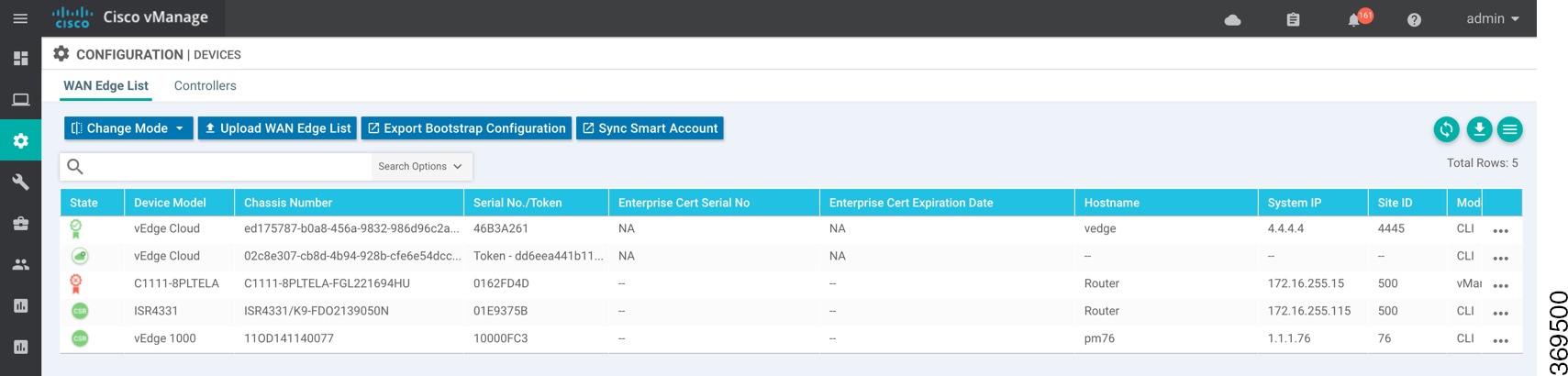
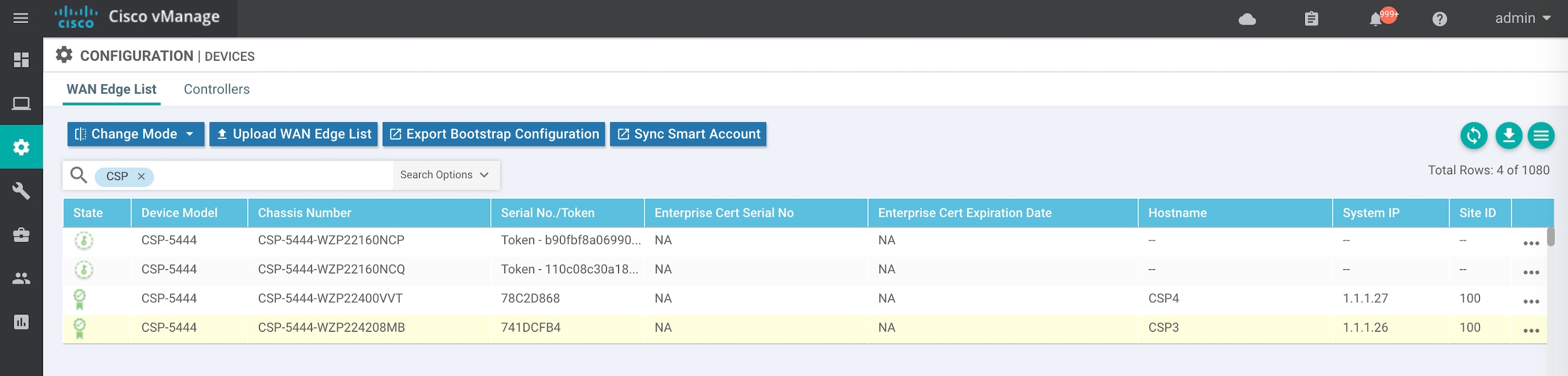
Upload WAN Edge Router Authorized Serial Number File
The WAN Edge router authorized serial number file contains the chassis and serial numbers of all valid Cisco vEdge deviceCisco IOS XE SD-WAN devices in the overlay network. You retrieve a serial number file from the Cisco Plug-and-Play (PnP) portal and upload it to the vManage NMS. Then, from the vManage NMS, you send it to the controllers in the network. This file is required to allow the Cisco SD-WAN overlay network components to validate and authenticate each other and thus to allow the overlay network to become operational.
To upload the WAN edge router authorized serial number file to the vManage NMS and then download it to all the controllers in the overlay network:
-
In the WAN Edge List tab, click Upload WAN Edge List.
-
In the Upload WAN Edge List window:
-
Click Choose File and select the WAN edge router authorized serial number file you received from Cisco SD-WAN.
-
To automatically validate the routers and send their chassis and serial numbers to the controllers, ensure that the checkbox Validate the Uploaded WAN Edge List and Send to Controllers is selected. (It is selected by default.) If you do not select this option, you must individually validate each router in Configuration ► Certificates ► WAN Edge List.
-
Click Upload.
-
A list of routers in the network is displayed in the router table, with details about each router.
Upload WAN Edge Router Serial Numbers from Cisco Smart Account
Chassis and serial numbers of all valid Cisco vEdge deviceCisco IOS XE SD-WAN devices in the overlay network are required to allow the Cisco SD-WAN overlay network components to validate and authenticate each other and thus to allow the overlay network to become operational.
To upload the WAN edge router authorized serial numbers from a Cisco Smart account to the vManage NMS and then download it to all the controllers in the overlay network:
-
In the WAN Edge List tab, click Sync Smart Account.
-
In the Sync Smart Account window:
-
Enter the username and password for your Smart account..
-
To automatically validate the routers and send their chassis and serial numbers to the controllers, ensure that the checkbox Validate the Uploaded WAN Edge List and Send to Controllers is selected. (It is selected by default.) If you do not select this option, you must individually validate each router in Configuration ► Certificates ► WAN Edge List.
-
Click Sync.
-
A list of routers in the network is displayed in the router table, with details about each router.
Generate Bootstrap Configuration for a vEdge Cloud Router
For vEdge Cloud routers, you need to generate a bootstrap configuration file that you use when you create vEdge cloud VM instances.
To generate and download a bootstrap configuration for one or more vEdge Cloud routers:
-
In the WAN Edge List tab, click the Export Bootstrap Configuration button.
-
In the Export Bootstrap Configuration window, in the Bootstrap Configuration field, click Cloud-Init or Encoded String, depending the Hypervisor you are using to bring up the vEdge Cloud router.
-
Select the devices to configure from the Available Devices pane, or click Select All to select all devices.
-
Click the right arrow to move the devices to the Selected Devices pane.
-
Click Generate Configuration. The configurations are downloaded to the vManage NMS.
-
Provision the vEdge Cloud router instance in AWS, KVM, or ESXi with the boostrap configuration. By default, ge0/0 is the device's tunnel interface and is a DHCP client. To use an interface other than ge0/0 as the tunnel interface or to use a static IP as the IP address, reconfigure the device through the CLI. For more information about configuring interfaces, see Configure Network Interfaces.
After you provision the vEdge Cloud router instance, vManage NMS installs a certificate on the device and the device's token changes to a serial number. After the device's control connections to vManage NMS come up, any templates attached to the device are automatically pushed to the device.
Export Device Data in CSV Format
In an overlay network, you might have multiple devices of the same type that have identical or effectively identical configurations. For example, in a network with redundant Cisco vSmart Controllers, each controller must be configured with identical policies. Another example is a network with Cisco vEdge deviceCisco IOS XE SD-WAN devices at multiple sites, where each Cisco vEdge deviceCisco IOS XE SD-WAN device is providing identical services at each site.
Because the configurations for these devices are essentially identical, you can create one set of feature templates, which you then consolidate into one device template that you use to configure all the devices. You can create an Excel file in CSV format that lists the variables and defines each device specific variable value for each device. Then you can load the file when you attach a device template to a device.
To export data for all devices to a file in CSV format, click the Export icon. This icon, which is a downward-pointing arrow, is located to the right of the filter criteria both in the WAN Edge List and in the Controllers tab.
vManage NMS downloads all data from the device table to an Excel file in CSV format.
View and Copy Device Configuration
View a Device's Running Configuration
Running configuration is configuration information that vManage obtains from the memory of a device. This information can be useful for troubleshooting.
To view a device's running configuration:
-
In the WAN Edge List or Controllers tab, select the device.
-
Click the More Actions icon to the right of the row and click Running Configuration.
View a Device's Local Configuration
Local configuration is configuration that vManage has stored for a device. This information can be useful for troubleshooting or for determining how to access a device if, for example, a device is not reachable from vManage.
To view a device's local configuration created using Configuration ► Templates:
-
In the WAN Edge List or Controllers tab, select the device.
-
Click the More Actions icon to the right of the row and click Local Configuration.
Copy Router Configuration
When you are replacing one router at a site with another router, you copy the old router's configuration to the new router. Then you remove the old router from the network and add the new one.
To copy the configuration from the old router to the new router:
-
In the Configuration ► Certificates screen, mark the new Cisco vEdge deviceCisco IOS XE SD-WAN device as invalid.
-
In the Configuration ► Devices screen, in the WAN Edge List tab, select the old router.
-
Click the More Actions icon to the right of the row and click Copy Configuration.
-
In the Copy Configuration window, select the new router.
-
Click Update to confirm the copy of the configuration.
After you have copied the configuration to the new router, you can add the new router to the network. First, delete the old router from the network, as described below. Then add the new router to the network:
-
In the Configuration ► Certificates screen, mark the new router as valid.
-
Click Send to Controller.
Delete a WAN Edge Router
Deleting a router removes its serial and chassis numbers from the WAN edge router serial number list and permanently removes the router's configuration from the vManage NMS. Delete a router if you need to remove it from your deployment.
-
In the Configuration ► Certificates screen, mark the WAN Edge router as invalid.
-
In the Configuration ► Devices screen, in the WAN Edge List tab, select the router.
-
Click the More Actions icon to the right of the row and click Delete WAN Edge.
-
Click OK to confirm deletion of the device.
-
In the Configuration ► Certificates screen, click Send to Controller.
Decommission a vEdge Cloud router
Decommissioning a vEdge Cloud router removes the device's serial number from vManage NMS and generates a new token for the device. To do so:
-
In the WAN Edge List tab, select a vEdge Cloud router.
-
Click the More Actions icon to the right of the row and click Decommission WAN Edge.
-
Click OK to confirm the decommissioning of the router.
View Template Log and Device Bringup
View Log of Template Activities
A log of template activities contains information that relates to creating, editing, and deleting configuration templates, and the status of attaching configuration templates to devices. This information can be useful for troubleshooting.
To view a log of template activities:
-
In the WAN Edge List or Controllers tab, select the device.
-
Click the More Actions icon to the right of the row and click Template Log.
View Status of Device Bringup
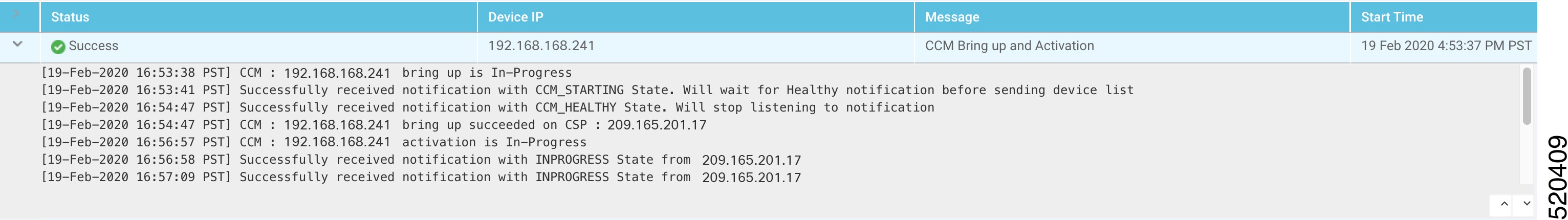
You can view the status of the operations involved in bringing a router or controller up in the overlay network. This information can help you monitor these operations.
To view the status of a device bringup:
-
In the WAN Edge List or Controllers tab, select the device.
-
Click the More Actions icon to the right of the row and click Device Bring Up.
Add a Cisco vBond Orchestrator
A Cisco vBond Orchestrator automatically orchestrates connectivity between Cisco vEdge deviceCisco IOS XE SD-WAN devices and vManage controllers. If any Cisco vEdge deviceCisco IOS XE SD-WAN device or Cisco vSmart Controller is behind a NAT, the Cisco vBond Orchestrator also serves as an initial NAT-traversal orchestrator. To add a Cisco vBond Orchestrator:
-
In the Controllers tab, click the Add Controller drop-down and select vBond.
-
In the Add vBond window:
-
Enter the management IP address of the vBond controller.
-
Enter the username and password to access the vBond orchestrator.
-
Select the Generate CSR checkbox to allow the certificate-generation process to occur automatically.
-
Click Add.
-
-
Repeat Steps 1 and 2 to add additional Cisco vBond Orchestrators.
The new Cisco vBond Orchestrator is added to the list of controllers in the Controllers screen.
Configure Cisco vSmart Controllers
Add a vSmart Controller
After the Cisco vBond Orchestrator authenticates Cisco vEdge deviceCisco IOS XE SD-WAN devices, the Cisco vBond Orchestrator provides Cisco vEdge deviceCisco IOS XE SD-WAN devices information that they need to connect to the Cisco vSmart Controller. A Cisco vSmart Controller controls the flow of data traffic throughout the network via data and app-route policies. To configure Cisco vSmart Controllers:
-
In the Controllers tab, click the Add Controller drop-down and select vSmart.
-
In the Add vSmart window:
-
Enter the system IP address of the Cisco vSmart Controller.
-
Enter the username and password to access the Cisco vSmart Controller.
-
Select the protocol to use for control-plane connections. The default is DTLS. The DTLS (Datagram Transport Layer Security) protocol is designed to provide security for UDP communications.
-
If you select TLS, enter the port number to use for TLS connections. The default is 23456.
The TLS (Transport Socket Layer) protocol that provides communications security over a network. -
Select the Generate CSR checkbox to allow the certificate-generation process to occur automatically.
-
Click Add.
-
-
Repeat Steps 1 and 2 to add additional Cisco vSmart Controllers. The vManage NMS can support up to 20 Cisco vSmart Controllers in the network.
The new Cisco vSmart Controller is added to the list of controllers in the Controllers screen.
Edit Controller Details
Editing controller details lets you update the IP address and login credentials of a controller device. To edit controller details:
-
In the Controllers tab, select the controller.
-
Click the More Actions icon to the right of the row and click Edit.
-
In the Edit window, edit the IP address and the login credentials.
-
Click Save.
Delete a Controller
Deleting a controller removes it from the overlay. Delete a controller it if you are replacing it or if you no longer need it in your network.
To delete a controller:
-
In the Controllers tab, select the controller.
-
Click the More Actions icon to the right of the row and click Invalidate.
-
Click OK to confirm the removal of the device and all its control connections.
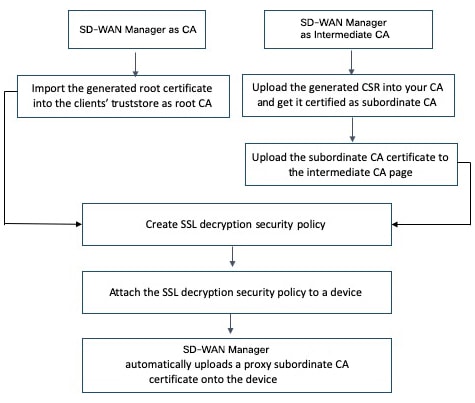
Configure Reverse Proxy on Controllers
To configure reverse proxy on an individual vManage NMS and Cisco vSmart Controller:
-
In the Controllers tab, select the device.
-
Click the More Actions icon to the right of the row, and click Add Reverse Proxy. The Add Reverse Proxy popup is displayed.
-
Click Add Reverse Proxy.
-
Configure the private IP address and port number for the device. The private IP address is the IP address of the transport interface in VPN 0. The default port number is 12346. This is the port used to establish the connections that handle control and traffic in the overlay network.
-
Configure the proxy IP address and port number for the device, to create the mapping between the private and public IP addresses and port numbers.
-
If the vManage NMS or Cisco vSmart Controller has multiple cores, repeat Steps 4 and 5 for each core.
-
Click Add.
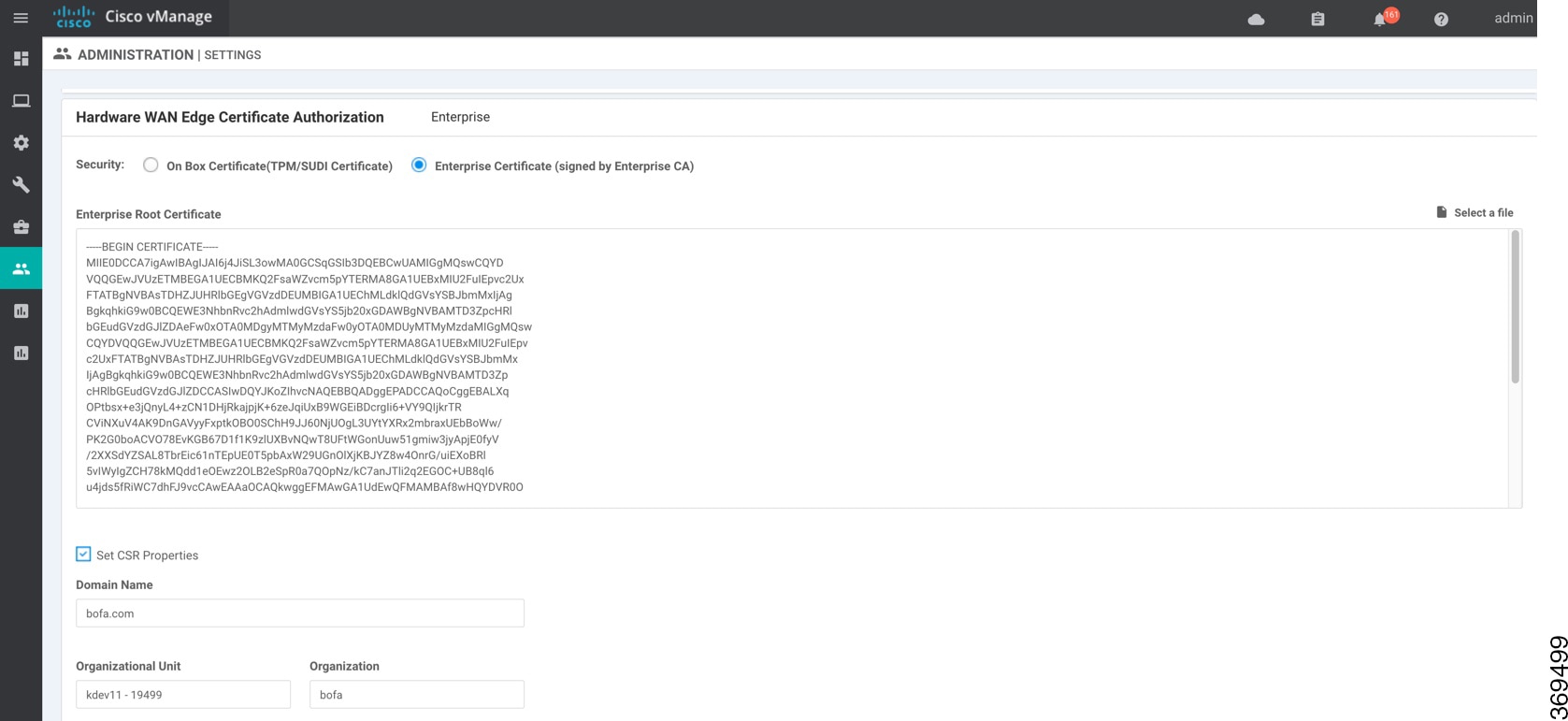
To enable reverse proxy in the overlay network, in vManage NMS select Administration ► Settings. Then click Edit to the right of the Reverse Proxy bar, click Enabled, and click Save.











 ), and the default setting or value is shown). To change the
default or to enter a value, click the scope drop-down to the left of the parameter
field and select one of the following:
), and the default setting or value is shown). To change the
default or to enter a value, click the scope drop-down to the left of the parameter
field and select one of the following:





































 .
.
 .
.



























 Feedback
Feedback