Recover from Hosts File Errors When Using Application Access
To prevent hosts file errors that can interfere with Application Access, close the Application Access window properly when you finish using Application Access. To do so, click the close icon.
When Application Access terminates abnormally, the hosts file remains in a Clientless SSL VPN-customized state. Clientless SSL VPN checks the state the next time you start Application
Access by searching for a hosts.webvpn file. If it finds one, a Backup HOSTS File Found error message appears, and Application Access is temporarily switched off.
If Application Access is stopped improperly, you leave the remote access client/server applications in limbo. If you try to start these applications without using Clientless SSL VPN, they may malfunction. You may find that hosts that you normally connect to are unavailable. This situation could commonly occur if you run applications remotely from home, fail to quit the Application Access window before shutting down the computer, then try to run the applications later from the office.
The following errors can occur if you do not close the Application Access window properly:
-
The next time you try to start Application Access, it may be switched off; you receive a
Backup HOSTS File Founderror message. -
The applications themselves may be switched off or malfunction, even when you are running them locally.
These errors can result from terminating the Application Access window in any improper way. For example:
-
Your browser crashes while you are using Application Access.
-
A power outage or system shutdown occurs while you are using Application Access.
-
You minimize the Application Access window while you are working, then shut down your computer with the window active (but minimized).
Understanding the Hosts File
The hosts file on your local system maps IP addresses to hostnames. When you start Application Access, Clientless SSL VPN modifies the hosts file, adding Clientless SSL VPN-specific entries. Stopping Application Access by properly closing the Application Access window returns the file to its original state.
|
Before invoking Application Access... |
hosts file is in original state. |
|
When Application Access starts.... |
|
|
When Application Access stops... |
|
|
After finishing Application Access... |
hosts file is in original state. |
 Note |
Microsoft anti-spyware software blocks changes that the port forwarding Java applet makes to the hosts file. See www.microsoft.com for information on how to allow hosts file changes when using anti-spyware software. |
Reconfigure a Host’s File Automatically Using Clientless SSL VPN
If you are able to connect to your remote access server, follow these steps to reconfigure the host’s file and re-enable both Application Access and the applications.
Procedure
| Step 1 |
Start Clientless SSL VPN and log in. Click the Applications Access link. 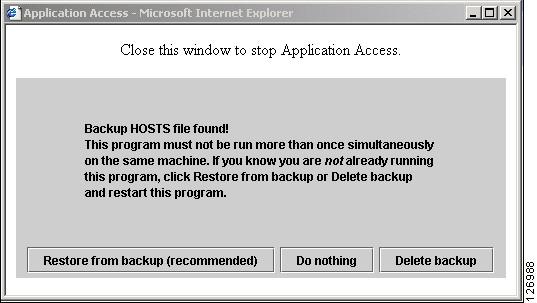 |
| Step 2 |
Choose one of the following options:
|
Reconfigure Hosts File Manually
If you are not able to connect to your remote access server from your current location, or if you have customized the hosts file and do not want to lose your edits, follow these steps to reconfigure the hosts file and reenable both Application Access and the applications.
Procedure
| Step 1 |
Locate and edit your hosts file. The most common location is c:\windows\sysem32\drivers\etc\hosts. |
| Step 2 |
Check to see if any lines contain the string: |
| Step 3 |
Delete the lines that contain the string: |
| Step 4 |
Save and close the file. |
| Step 5 |
Start Clientless SSL VPN and log in. |
| Step 6 |
Click the Application Access link. |
 Feedback
Feedback