About Smart Software Licensing
Cisco Smart Licensing is a flexible licensing model that provides you with an easier, faster, and more consistent way to purchase and manage software across the Cisco portfolio and across your organization. And it’s secure—you control what users can access. With Smart Licensing you get:
-
Easy Activation: Smart Licensing establishes a pool of software licenses that can be used across the entire organization—no more PAKs (Product Activation Keys).
-
Unified Management: My Cisco Entitlements (MCE) provides a complete view into all of your Cisco products and services in an easy-to-use portal, so you always know what you have and what you are using.
-
License Flexibility: Your software is not node-locked to your hardware, so you can easily use and transfer licenses as needed.
To use Smart Licensing, you must first set up a Smart Account on Cisco Software Central (software.cisco.com).
For a more detailed overview on Cisco Licensing, go to cisco.com/go/licensingguide
Smart Software Licensing for the ASA on the Firepower 4100/9300 Chassis
For the ASA on the Firepower 4100/9300 chassis, Smart Software Licensing configuration is split between the Firepower 4100/9300 chassis supervisor and the ASA.
-
Firepower 4100/9300 chassis—Configure all Smart Software Licensing infrastructure on the chassis, including parameters for communicating with the Smart Software Manager. The Firepower 4100/9300 chassis itself does not require any licenses to operate.

Note
Inter-chassis clustering requires that you enable the same Smart Licensing method on each chassis in the cluster.
-
ASA Application—Configure all license entitlements in the ASA.
Smart Software Manager and Accounts
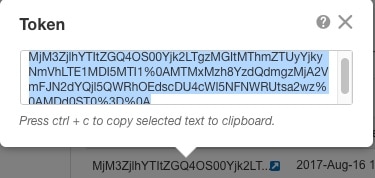
When you purchase 1 or more licenses for the device, you manage them in the Cisco Smart Software Manager:
https://software.cisco.com/#module/SmartLicensing
The Smart Software Manager lets you create a master account for your organization.
 Note |
If you do not yet have an account, click the link to set up a new account. The Smart Software Manager lets you create a master account for your organization. |
By default, your licenses are assigned to the Default Virtual Account under your master account. As the account administrator, you can optionally create additional virtual accounts; for example, you can create accounts for regions, departments, or subsidiaries. Multiple virtual accounts let you more easily manage large numbers of licenses and devices.
Offline Management
If your devices do not have internet access, and cannot register with the Smart Software Manager, you must configure offline licensing.
Permanent License Reservation
If your devices cannot access the internet for security reasons, you can optionally request permanent licenses for each ASA. Permanent licenses do not require periodic access to the Smart Software Manager. As with PAK licenses, you can purchase a license and install the license key for the ASA. Unlike a PAK license, you can obtain and manage the licenses with the Smart Software Manager. You can easily switch between regular smart licensing mode and permanent license reservation mode.
 Note |
ASA does not support Specific License Reservation (SLR). In SLR, specific feature entitlements are enabled permanently. ASA supports only PLR, where all the features are enabled permanently. |
ASA Virtual Permanent License Reservation
 Note |
Permanent license reservation is supported only on VMware and KVM. |
You can obtain a model-specific license that enables all of the following features:
-
Maximum throughput for your model
-
Essentials tier
-
Strong Encryption (3DES/AES) license, if you have enabled it in your Smart Licensing account
-
Secure Client capabilities enabled for the platform
Use of Secure Client features is contingent on your purchase of the Secure Client license that enables the right to use Secure Client (see Secure Client Advantage, Secure Client Premier, and Secure Client VPN Only Licenses).
When you deploy ASA virtual, the vCPU and memory that you choose determines the model license required. Unlike regular smart licensing with flexible vCPU and memory and throughput combinations, permanent license reservation is still tied to the vCPU/memory you use when you deploy ASA virtual.
vCPU and memory-to-license relationships are as follows:
-
2 GB, 1 vCPU—ASAv5 (100 M) (You must run the license smart set_plr5 command; otherwise, the ASAv10 license is assigned to allow 1-G throughput.)

Note
In Version 9.13, the ASAv5 RAM requirements were increased to 2 GB. Because of this increase, the ASAv5 permanent license no longer worked because the ASA checked the memory assigned and determined that 2 GB of RAM was actually an ASAv10, not an ASAv5. To allow the ASAv5 permanent license to work, you must configure the ASA to recognize the extra memory for the model.
-
2 GB, 1 vCPU—ASAv10 (1G)
-
8 GB, 4 vCPUs —ASAv30 (2G)
-
16 GB, 8 vCPUs—ASAv50 (10G)
-
32 GB, 16 vCPUs—ASAv100 (20G)
-
64 GB, 32 vCPU—ASAvU
-
128 GB, 64 vCPU—ASAvU
Later, if you want to change the model level of a unit, you will have to return the current license and request a new license at the correct model level. To change the model of an already deployed ASA virtual, from the hypervisor you can change the vCPUs and DRAM settings to match the new model requirements. See the ASA virtual Virtual Getting Started Guide for these values.
If you stop using a license, you must return the license by generating a return code on ASA virtual and then enter that code into the Smart Software Manager. Make sure you follow the return process correctly to ensure that you do not pay for unused licenses.
Firepower 1010 Permanent License Reservation
You can obtain a license that enables all features:
-
Essentials tier
-
Security Plus
-
Strong Encryption (3DES/AES) license if your account qualifies
-
Secure Client capabilities enabled to the platform maximum.
Use of Secure Client features is contingent on your purchase of the Secure Client license that enables the right to use Secure Client (see Secure Client Advantage, Secure Client Premier, and Secure Client VPN Only Licenses).
 Note |
You also need to request the entitlements in the ASA configuration so that the ASA allows their use. |
If you stop using a license, you must return the license by generating a return code on the ASA, and then entering that code into the Smart Software Manager. Make sure you follow the return process correctly so you do not pay for unused licenses.
Firepower 1100 Permanent License Reservation
You can obtain a license that enables all features:
-
Essentials tier
-
Maximum Security Contexts
-
Strong Encryption (3DES/AES) license if your account qualifies
-
Secure Client capabilities enabled to the platform maximum.
Use of Secure Client features is contingent on your purchase of the Secure Client license that enables the right to use Secure Client (see Secure Client Advantage, Secure Client Premier, and Secure Client VPN Only Licenses).
 Note |
You also need to request the entitlements in the ASA configuration so that the ASA allows their use. |
If you stop using a license, you must return the license by generating a return code on the ASA, and then entering that code into the Smart Software Manager. Make sure you follow the return process correctly so you do not pay for unused licenses.
Secure Firewall 1210/1220 Permanent License Reservation
You can obtain a license that enables all features:
-
Essentials tier
-
Strong Encryption (3DES/AES) license if your account qualifies
-
Secure Client capabilities enabled to the platform maximum.
Use of Secure Client features is contingent on your purchase of the Secure Client license that enables the right to use Secure Client (see Secure Client Advantage, Secure Client Premier, and Secure Client VPN Only Licenses).
 Note |
You also need to request the entitlements in the ASA configuration so that the ASA allows their use. |
If you stop using a license, you must return the license by generating a return code on the ASA, and then entering that code into the Smart Software Manager. Make sure you follow the return process correctly so you do not pay for unused licenses.
Secure Firewall 3100/4200 Permanent License Reservation
You can obtain a license that enables all features:
-
Essentials tier
-
Maximum Security Contexts
-
Carrier license
-
Strong Encryption (3DES/AES) license if your account qualifies
-
Secure Client capabilities enabled to the platform maximum.
Use of Secure Client features is contingent on your purchase of the Secure Client license that enables the right to use Secure Client (see Secure Client Advantage, Secure Client Premier, and Secure Client VPN Only Licenses).
 Note |
You also need to request the entitlements in the ASA configuration so that the ASA allows their use. |
If you stop using a license, you must return the license by generating a return code on the ASA, and then entering that code into the Smart Software Manager. Make sure you follow the return process correctly so you do not pay for unused licenses.
Firepower 4100/9300 Chassis Permanent License Reservation
You can obtain a license that enables all features:
-
Essentials tier.
-
Maximum Security Contexts
-
Carrier license
-
Strong Encryption (3DES/AES) license if your account qualifies
-
Secure Client capabilities enabled to the platform maximum.
Use of Secure Client features is contingent on your purchase of the Secure Client license that enables the right to use Secure Client (see Secure Client Advantage, Secure Client Premier, and Secure Client VPN Only Licenses).
 Note |
The license is managed on the Firepower 4100/9300 chassis, but you also need to request the entitlements in the ASA configuration so that the ASA allows their use. |
If you stop using a license, you must return the license by generating a return code on the Firepower 4100/9300 chassis, and then entering that code into the Smart Software Manager. Make sure you follow the return process correctly so you don't pay for unused licenses.
 Note |
When you reverse upgrade ASA Virtual version 9.20 to an earlier unlicensed version, the PLR token that is generated during the registration of ASA Virtual version 9.20 is returned to the smart license server. This PLR token is not compatible with the license installation of the unlicensed ASA Virtual (post upgrade). |
Smart Software Manager On-Prem
If your devices cannot access the internet for security reasons, you can optionally install a local Smart Software Manager On-Prem (formerly known as "Smart Software Satellite Server") server as a virtual machine (VM). The Smart Software Manager On-Prem provides a subset of Smart Software Manager functionality, and allows you to provide essential licensing services for all your local devices. Only the Smart Software Manager On-Prem needs to connect periodically to the main Smart Software Manager to sync your license usage. You can sync on a schedule or you can sync manually.
You can perform the following functions on the Smart Software Manager On-Prem:
-
Activate or register a license
-
View your company's licenses
-
Transfer licenses between company entities
For more information, see Cisco Smart Software Manager On-Prem Data Sheet.
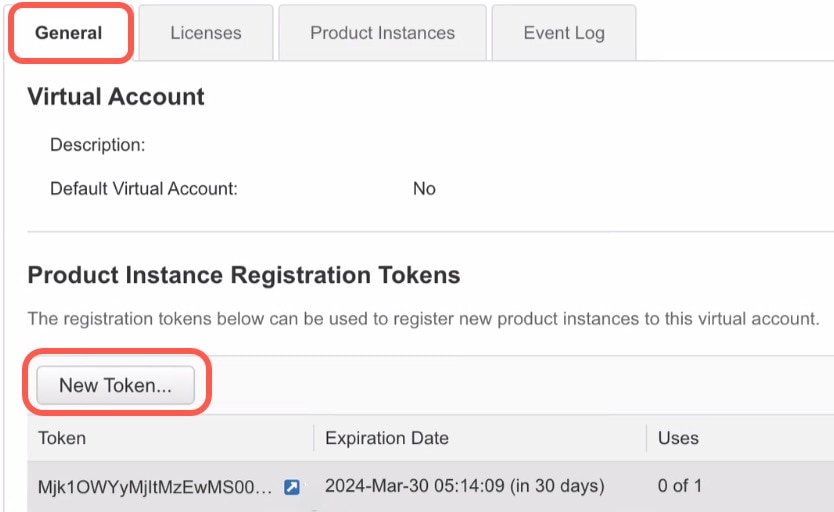
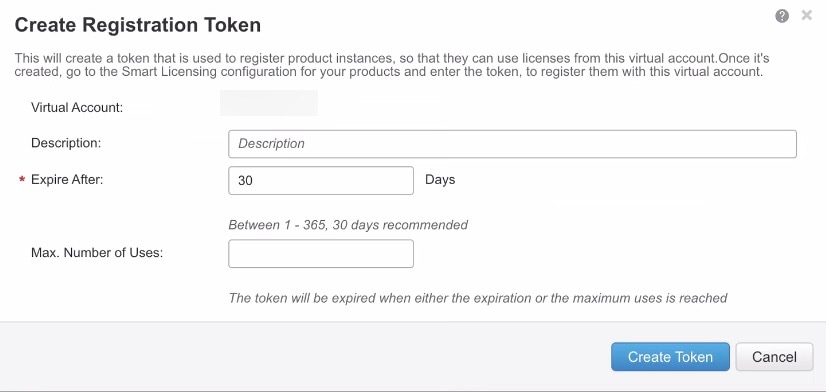
Licenses and Devices Managed per Virtual Account
Licenses and devices are managed per virtual account: only that virtual account’s devices can use the licenses assigned to the account. If you need additional licenses, you can transfer an unused license from another virtual account. You can also transfer devices between virtual accounts.
For the ASA on the Firepower 4100/9300 chassis—Only the chassis registers as a device, while the ASA applications in the chassis request their own licenses. For example, for a Firepower 9300 chassis with 3 security modules, the chassis counts as one device, but the modules use 3 separate licenses.
Evaluation License
ASA Virtual
The ASA virtual does not support an evaluation mode. Before the ASA virtual registers with the Smart Software Manager, it operates in a severely rate-limited state.
Firepower 1000
Before the Firepower 1000 registers with the Smart Software Manager, it operates for 90 days (total usage) in evaluation mode. Only default entitlements are enabled. When this period ends, the Firepower 1000 becomes out-of-compliance.
 Note |
You cannot receive an evaluation license for Strong Encryption (3DES/AES); you must register with the Smart Software Manager to receive the export-compliance token that enables the Strong Encryption (3DES/AES) license. |
Firepower 2100
Before the Firepower 2100 registers with the Smart Software Manager, it operates for 90 days (total usage) in evaluation mode. Only default entitlements are enabled. When this period ends, the Firepower 2100 becomes out-of-compliance.
 Note |
You cannot receive an evaluation license for Strong Encryption (3DES/AES); you must register with the Smart Software Manager to receive the export-compliance token that enables the Strong Encryption (3DES/AES) license. |
Secure Firewall 3100/4200
Before the Secure Firewall 3100/4200 registers with the Smart Software Manager, it operates for 90 days (total usage) in evaluation mode. Only default entitlements are enabled. When this period ends, the Secure Firewall 3100/4200 becomes out-of-compliance.
 Note |
You cannot receive an evaluation license for Strong Encryption (3DES/AES); you must register with the Smart Software Manager to receive the export-compliance token that enables the Strong Encryption (3DES/AES) license. |
Firepower 4100/9300 Chassis
The Firepower 4100/9300 chassis supports two types of evaluation license:
-
Chassis-level evaluation mode—Before the Firepower 4100/9300 chassis registers with the Smart Software Manager, it operates for 90 days (total usage) in evaluation mode. The ASA cannot request specific entitlements in this mode; only default entitlements are enabled. When this period ends, the Firepower 4100/9300 chassis becomes out-of-compliance.
-
Entitlement-based evaluation mode—After the Firepower 4100/9300 chassis registers with the Smart Software Manager, you can obtain time-based evaluation licenses that can be assigned to the ASA. In the ASA, you request entitlements as usual. When the time-based license expires, you need to either renew the time-based license or obtain a permanent license.
 Note |
You cannot receive an evaluation license for Strong Encryption (3DES/AES); you must register with the Smart Software Manager and obtain a permanent license to receive the export-compliance token that enables the Strong Encryption (3DES/AES) license. |
About Licenses by Type
The following sections include additional information about licenses by type.
Secure Client Advantage, Secure Client Premier, and Secure Client VPN Only Licenses
Secure Client licenses are not applied directly to the ASA. However, you need to purchase licenses and add them to your Smart Account to guarantee the right to use the ASA as the Secure Client headend.
-
For the Secure Client Advantage and Secure Client Premier licenses, add up the number of peers you intend to use across all the ASAs in your Smart Account and purchase license(s) for that many peers.
-
For the Secure Client VPN Only, purchase one license per ASA. Unlike the other licenses that provide a pool of peers that can be shared by multiple ASAs, the Secure Client VPN Only license is per headend.
For more information, see:
Other VPN Peers
Other VPN peers include the following VPN types:
-
IPsec remote access VPN using IKEv1
-
IPsec site-to-site VPN using IKEv1
-
IPsec site-to-site VPN using IKEv2
This license is included in the Base license.
Total VPN Peers Combined, All Types
-
The Total VPN Peers is the maximum VPN peers allowed of both Secure Client and Other VPN peers combined. For example, if the total is 1000, you can allow 500 Secure Client and 500 Other VPN peers simultaneously; or 700 Secure Client and 300 Other VPN; or use all 1000 for Secure Client. If you exceed the total VPN peers, you can overload the ASA, so be sure to size your network appropriately.
Encryption License
Strong Encryption: ASA Virtual
Strong Encryption (3DES/AES) is available for management connections before you connect to the Smart Software Manager or Smart Software Manager On-Prem server, so you can launch ASDM and connect to the Smart Software Manager. For through-the-box traffic that requires strong encryption (such as VPN), throughput is severely limited until you connect to the Smart Software Manager and obtain the Strong Encryption license.
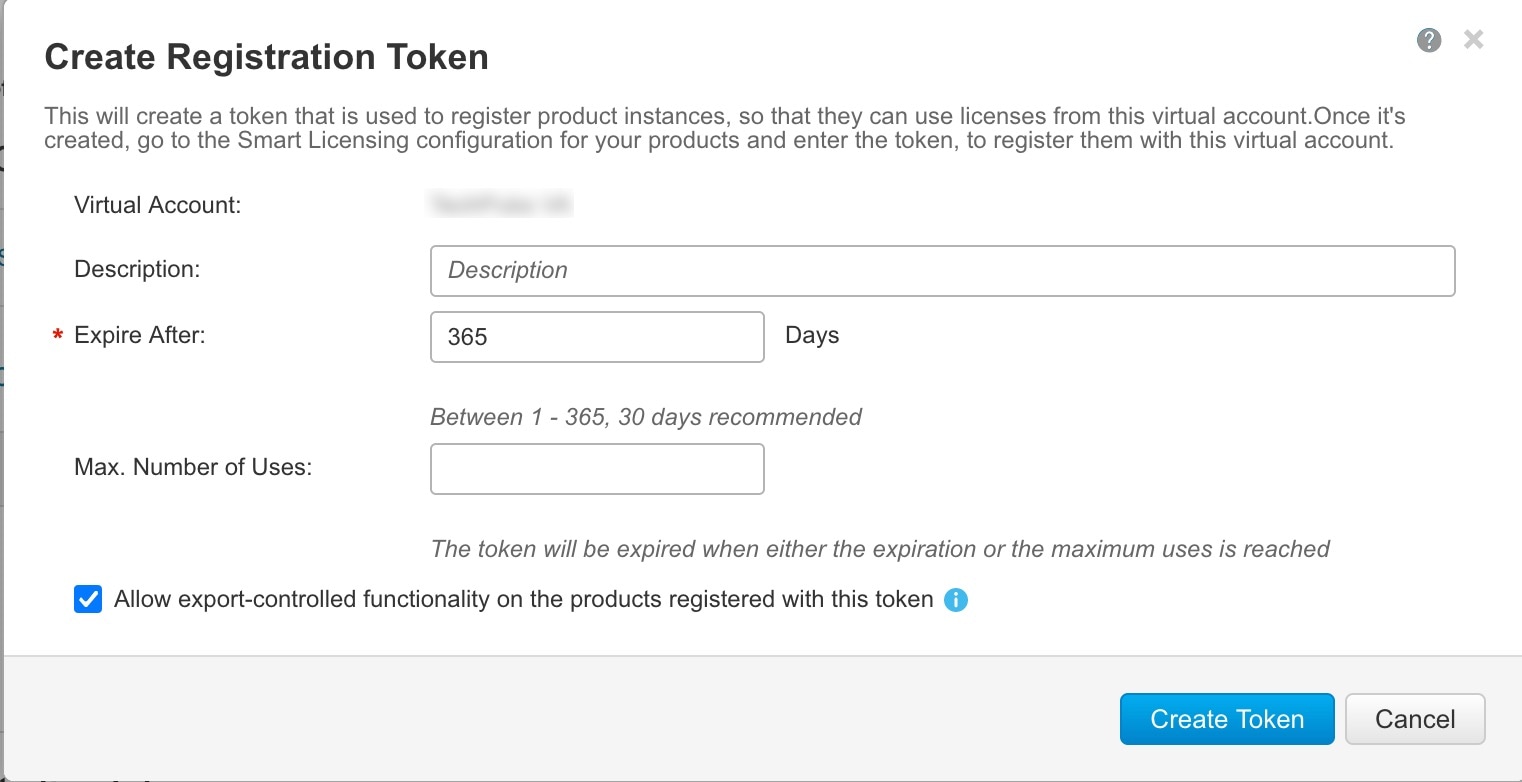
When you request the registration token for the ASA virtual from your Smart Software Licensing account, check the Allow export-controlled functionality on the products registered with this token check box so that the Strong Encryption (3DES/AES) license is applied (your account must be qualified for its use). If the ASA virtual becomes out-of-compliance later, as long as the export compliance token was successfully applied, the ASA virtual will retain the license and not revert to the rate-limited state. The license is removed if you re-register the ASA virtual, and export compliance is disabled, or if you restore the ASA virtual to factory default settings.
If you initially register the ASA virtual without strong encryption and later add strong encryption, then you must reload the ASA virtual for the new license to take effect.
For permanent license reservation licenses, the Strong Encryption (3DES/AES) license is enabled if your account qualifies for its use.
If your Smart Account is not authorized for strong encryption, but Cisco has determined that you are allowed to use strong encryption, you can manually add a strong encryption license to your account.
Strong Encryption: Firepower 1000, Secure Firewall 1200/3100/4200
The ASA includes 3DES capability by default for management access only, so you can connect to the Smart Software Manager and also use ASDM immediately. You can also use SSH and SCP if you later configure SSH access on the ASA. Other features that require strong encryption (such as VPN) must have Strong Encryption enabled, which requires you to first register to the Smart Software Manager.
 Note |
If you attempt to configure any features that can use strong encryption before you register—even if you only configure weak encryption—then your HTTPS connection will be dropped on that interface, and you cannot reconnect. The exception to this rule is if you are connected to a management-only interface, such as Management 1/1. SSH is not affected. If you lose your HTTPS connection, you can connect to the console port to reconfigure the ASA, connect to a management-only interface, or connect to an interface not configured for a strong encryption feature. |
When you request the registration token for the ASA from your Smart Software Licensing account, check the Allow export-controlled functionality on the products registered with this token check box so that the Strong Encryption (3DES/AES) license is applied (your account must be qualified for its use). If the ASA becomes out-of-compliance later, as long as the export compliance token was successfully applied, the ASA will continue to allow through the box traffic. Even if you re-register the ASA, and export compliance is disabled, the license remains enabled. The license is removed if you restore the ASA to factory default settings.
If you initially register the ASA without strong encryption and later add strong encryption, then you must reload the ASA for the new license to take effect.
For permanent license reservation licenses, the Strong Encryption (3DES/AES) license is enabled if your account qualifies for its use.
If your Smart Account is not authorized for strong encryption, but Cisco has determined that you are allowed to use strong encryption, you can manually add a strong encryption license to your account.
Strong Encryption: Firepower 4100/9300 Chassis
When the ASA is deployed as a logical device, you can launch ASDM immediately. Through the box traffic that requires strong encryption (such as VPN) is not allowed until you connect and obtain the Strong Encryption license.
When you request the registration token for the chassis from your Smart Software Licensing account, check the Allow export-controlled functionality on the products registered with this token check box so that the Strong Encryption (3DES/AES) license is applied (your account must be qualified for its use).
If the ASA becomes out-of-compliance later, as long as the export compliance token was successfully applied, the ASA will continue to allow through the box traffic. The license is removed if you re-register the chassis, and export compliance is disabled, or if you restore the chassis to factory default settings.
If you initially register the chassis without strong encryption and later add strong encryption, then you must reload the ASA application for the new license to take effect.
For permanent license reservation licenses, the Strong Encryption (3DES/AES) license is enabled if your account qualifies for its use.
If your Smart Account is not authorized for strong encryption, but Cisco has determined that you are allowed to use strong encryption, you can manually add a strong encryption license to your account.
DES: All Models
The DES license cannot be disabled. If you have the 3DES license installed, DES is still available. To prevent the use of DES when you want to only use strong encryption, be sure to configure any relevant commands to use only strong encryption.
Carrier License
The Carrier license enables the following inspection features:
-
Diameter—Diameter is an Authentication, Authorization, and Accounting (AAA) protocol used in next-generation mobile and fixed telecom networks such as EPS (Evolved Packet System) for LTE (Long Term Evolution) and IMS (IP Multimedia Subsystem). It replaces RADIUS and TACACS in these networks.
-
GTP/GPRS—GPRS Tunneling Protocol is used in GSM, UMTS and LTE networks for general packet radio service (GPRS) traffic. GTP provides a tunnel control and management protocol to provide GPRS network access for a mobile station by creating, modifying, and deleting tunnels. GTP also uses a tunneling mechanism for carrying user data packets.
-
M3UA—MTP3 User Adaptation (M3UA) is a client/server protocol that provides a gateway to the SS7 network for IP-based applications that interface with the SS7 Message Transfer Part 3 (MTP3) layer. M3UA makes it possible to run the SS7 User Parts (such as ISUP) over an IP network. M3UA is defined in RFC 4666.
-
SCTP—SCTP (Stream Control Transmission Protocol) is described in RFC 4960. The protocol supports the telephony signaling protocol SS7 over IP and is also a transport protocol for several interfaces in the 4G LTE mobile network architecture.
Total TLS Proxy Sessions
Each TLS proxy session for Encrypted Voice Inspection is counted against the TLS license limit.
Other applications that use TLS proxy sessions do not count toward the TLS limit, for example, Mobility Advantage Proxy (which does not require a license).
Some applications might use multiple sessions for a connection. For example, if you configure a phone with a primary and backup Cisco Unified Communications Manager, there are 2 TLS proxy connections.
You independently set the TLS proxy limit using the tls-proxy maximum-sessions command or in ASDM, using the Configuration > Firewall > Unified Communications > TLS Proxy pane. To view the limits of your model, enter the tls-proxy maximum-sessions ? command. When you apply a TLS proxy license that is higher than the default TLS proxy limit, the ASA automatically sets the TLS proxy limit to match the license. The TLS proxy limit takes precedence over the license limit; if you set the TLS proxy limit to be less than the license, then you cannot use all of the sessions in your license.
 Note |
For license part numbers ending in “K8” (for example, licenses under 250 users), TLS proxy sessions are limited to 1000. For license part numbers ending in “K9” (for example, licenses 250 users or larger), the TLS proxy limit depends on the configuration, up to the model limit. K8 and K9 refer to whether the license is restricted for export: K8 is unrestricted, and K9 is restricted. If you clear the configuration (using the clear configure all command, for example), then the TLS proxy limit is set to the default for your model; if this default is lower than the license limit, then you see an error message to use the tls-proxy maximum-sessions command to raise the limit again (in ASDM, use the TLS Proxy pane). If you use failover and enter the write standby command or in ASDM, use File > Save Running Configuration to Standby Unit on the primary unit to force a configuration synchronization, the clear configure all command is generated on the secondary unit automatically, so you may see the warning message on the secondary unit. Because the configuration synchronization restores the TLS proxy limit set on the primary unit, you can ignore the warning. |
You might also use SRTP encryption sessions for your connections:
-
For K8 licenses, SRTP sessions are limited to 250.
-
For K9 licenses, there is no limit.
 Note |
Only calls that require encryption/decryption for media are counted toward the SRTP limit; if passthrough is set for the call, even if both legs are SRTP, they do not count toward the limit. |
VLANs, Maximum
For an interface to count against the VLAN limit, you must assign a VLAN to it. For example:
interface gigabitethernet 0/0.100
vlan 100
Botnet Traffic Filter License
Requires a Strong Encryption (3DES/AES) License to download the dynamic database.
Failover or ASA Cluster Licenses
Failover Licenses for the ASAv
The standby unit requires the same model license as the primary unit.
Failover Licenses for the Firepower 1010
Smart Software Manager Regular and On-Prem
Both Firepower 1010 units must be registered with the Smart Software Manager or Smart Software Manager On-Prem server. Both units require you to enable the Essentials license and the Security Plus license before you can configure failover.
Typically, you do not also need to enable the Strong Encryption (3DES/AES) feature license in the ASA, because both units should have obtained the Strong Encryption token when you registered the units. When using the registration token, both units must have the same encryption level.
If your Smart Account is not authorized for strong encryption, but Cisco has determined that you are allowed to use strong encryption, you can manually add a strong encryption license to your account. In this case, enable it on the active unit after you enable failover. The configuration is replicated to the standby unit, but the standby unit does not use the configuration; it remains in a cached state. Only the active unit requests the license from the server. The license is aggregated into a single failover license that is shared by the failover pair, and this aggregated license is also cached on the standby unit to be used if it becomes the active unit in the future. After a failover, the new active unit continues to use the aggregated license. It uses the cached license configuration to re-request the entitlement from the server. When the old active unit rejoins the pair as a standby unit, it releases the license entitlement. Before the standby unit releases the entitlement, the new active unit's license might be in a non-compliant state if there are no available licenses in the account. The failover pair can use the aggregated license for 30 days, but if it is still non-compliant after the grace period, and you are not using the Strong Encryption token, then you will not be able to make configuration changes to features requiring the Strong Encryption (3DES/AES) feature license; operation is otherwise unaffected. The new active unit sends an entitlement authorization renewal request every 35 seconds until the license is compliant. If you disband the failover pair, then the active unit releases the entitlements, and both units retain the licensing configuration in a cached state. To re-activate licensing, you need to clear the configuration on each unit, and re-configure it.
Permanent License Reservation
For permanent license reservation, you must purchase separate licenses for each chassis and enable the licenses before you configure failover.
Failover Licenses for the Firepower 1100
Smart Software Manager Regular and On-Prem
Only the active unit requests licenses from the server. Licenses are aggregated into a single failover license that is shared by the failover pair. There is no extra cost for secondary units.
After you enable failover for Active/Standby failover, you can only configure smart licensing on the active unit. For Active/Active failover, you can only configure smart licensing on the unit with failover group 1 as active. The configuration is replicated to the standby unit, but the standby unit does not use the configuration; it remains in a cached state. The aggregated license is also cached on the standby unit to be used if it becomes the active unit in the future.
 Note |
Each ASA must have the same encryption license when forming a failover pair. When you register an ASA to the smart licensing server, the Strong Encryption license is automatically enabled for qualified customers when you apply the registration token. Because of this requirement, you have two choices for licensing when you use the Strong Encryption token with failover:
|
Each add-on license type is managed as follows:
-
Essentials—Although only the active unit requests this license from the server, the standby unit has the Essentials license enabled by default; it does not need to register with the server to use it.
-
Context—Only the active unit requests this license. However, the Essentials license includes 2 contexts by default and is present on both units. The value from each unit’s Essentials license plus the value of the Context license on the active unit are combined up to the platform limit. For example:
-
Active/Standby: The Essentials license includes 2 contexts; for two Firepower 1120 units, these licenses add up to 4 contexts. You configure a 3-Context license on the active unit in an Active/Standby pair. Therefore, the aggregated failover license includes 7 contexts. However, because the platform limit for one unit is 5, the combined license allows a maximum of 5 contexts only. In this case, you might only configure the active Context license to be 1 context.
-
Active/Active: The Essentials license includes 2 contexts; for two Firepower 1140 units, these licenses add up to 4 contexts. You configure a 4-Context license on the primary unit in an Active/Active pair. Therefore, the aggregated failover license includes 8 contexts. One unit can use 5 contexts and the other unit can use 3 contexts, for example; but during a failure, one unit will use all 8. Because the platform limit for one unit is 10, the combined license allows a maximum of 10 contexts; the 8 contexts are within the limit.
-
-
Strong Encryption (3DES/AES)—If your Smart Account is not authorized for strong encryption, but Cisco has determined that you are allowed to use strong encryption, you can manually add a strong encryption license to your account. Only the active unit requests this license, and both units can use it due to license aggregation.
After a failover, the new active unit continues to use the aggregated license. It uses the cached license configuration to re-request the entitlement from the server. When the old active unit rejoins the pair as a standby unit, it releases the license entitlement. Before the standby unit releases the entitlement, the new active unit's license might be in a non-compliant state if there are no available licenses in the account. The failover pair can use the aggregated license for 30 days, but if it is still non-compliant after the grace period, you will not be able to make configuration changes to features requiring special licenses (i.e. add an extra context); operation is otherwise unaffected. The new active unit sends an entitlement authorization renewal request every 35 seconds until the license is compliant. If you disband the failover pair, then the active unit releases the entitlements, and both units retain the licensing configuration in a cached state. To re-activate licensing, you need to clear the configuration on each unit, and re-configure it.
Permanent License Reservation
For permanent license reservation, you must purchase separate licenses for each chassis and enable the licenses before you configure failover.
Failover Licenses for the Secure Firewall 1210/1220
Smart Software Manager Regular and On-Prem
Each unit requires the Essentials license (enabled by default) and the same encryption license. We recommend licensing each unit with the licensing server before you enable failover to avoid licensing mismatch issues, and when using the Strong Encryption license, issues with failover link encryption.
The Strong Encryption license is automatically enabled for qualified customers when you apply the registration token. For the optional Strong Encryption (3DES/AES) feature license enabled in the ASA configuration, see below.
In the ASA license configuration, the Essentials license is always enabled by default on both units. After you enable failover for Active/Standby failover, you can only configure smart licensing on the active unit. For Active/Active failover, you can only configure smart licensing on the unit with failover group 1 as active. The configuration is replicated to the standby unit, but the standby unit does not use the configuration; it remains in a cached state. The aggregated license is also cached on the standby unit to be used if it becomes the active unit in the future.
Each add-on license type is managed as follows:
-
Essentials—Each unit requests a Essentials license from the server.
-
Strong Encryption (3DES/AES)—If your Smart Account is not authorized for strong encryption, but Cisco has determined that you are allowed to use strong encryption, you can manually add a strong encryption license to your account. Only the active unit requests this license, and both units can use it due to license aggregation.
After a failover, the new active unit continues to use the aggregated license. It uses the cached license configuration to re-request the entitlement from the server. When the old active unit rejoins the pair as a standby unit, it releases the license entitlement. Before the standby unit releases the entitlement, the new active unit's license might be in a non-compliant state if there are no available licenses in the account. The failover pair can use the aggregated license for 30 days, but if it is still non-compliant after the grace period, you will not be able to make configuration changes to features requiring special licenses; operation is otherwise unaffected. The new active unit sends an entitlement authorization renewal request every 35 seconds until the license is compliant. If you disband the failover pair, then the active unit releases the entitlements, and both units retain the licensing configuration in a cached state. To re-activate licensing, you need to clear the configuration on each unit, and re-configure it.
Permanent License Reservation
For permanent license reservation, you must purchase separate licenses for each chassis and enable the licenses before you configure failover.
Failover Licenses for the Secure Firewall 3100
Smart Software Manager Regular and On-Prem
Each unit requires the Essentials license (enabled by default) and the same encryption license. We recommend licensing each unit with the licensing server before you enable failover to avoid licensing mismatch issues, and when using the Strong Encryption license, issues with failover link encryption.
The failover feature itself does not require any licenses. There is no extra cost for the Context license on data units.
The Strong Encryption license is automatically enabled for qualified customers when you apply the registration token. For the optional Strong Encryption (3DES/AES) feature license enabled in the ASA configuration, see below.
In the ASA license configuration, the Essentials license is always enabled by default on both units. After you enable failover for Active/Standby failover, you can only configure smart licensing on the active unit. For Active/Active failover, you can only configure smart licensing on the unit with failover group 1 as active. The configuration is replicated to the standby unit, but the standby unit does not use the configuration; it remains in a cached state. The aggregated license is also cached on the standby unit to be used if it becomes the active unit in the future.
Each add-on license type is managed as follows:
-
Essentials—Each unit requests a Essentials license from the server.
-
Context—Only the active unit requests this license. However, the Essentials license includes 2 contexts by default and is present on both units. The value from each unit’s Essentials license plus the value of the Context license on the active unit are combined up to the platform limit. For example:
-
Active/Standby: The Essentials license includes 2 contexts; for two Secure Firewall 3130 units, these licenses add up to 4 contexts. You configure a 100-Context license on the active unit in an Active/Standby pair. Therefore, the aggregated failover license includes 104 contexts. However, because the platform limit for one unit is 100, the combined license allows a maximum of 100 contexts only. In this case, you might only configure the active Context license to be 95 contexts.
-
Active/Active: The Essentials license includes 2 contexts; for two Secure Firewall 3130 units, these licenses add up to 4 contexts. You configure a 10-Context license on the primary unit in an Active/Active pair. Therefore, the aggregated failover license includes 14 contexts. One unit can use 9 contexts and the other unit can use 5 contexts, for example; but during a failure, one unit will use all 14. Because the platform limit for one unit is 100, the combined license allows a maximum of 100 contexts; the 14 contexts are within the limit.
-
-
Strong Encryption (3DES/AES)—If your Smart Account is not authorized for strong encryption, but Cisco has determined that you are allowed to use strong encryption, you can manually add a strong encryption license to your account. Only the active unit requests this license, and both units can use it due to license aggregation.
After a failover, the new active unit continues to use the aggregated license. It uses the cached license configuration to re-request the entitlement from the server. When the old active unit rejoins the pair as a standby unit, it releases the license entitlement. Before the standby unit releases the entitlement, the new active unit's license might be in a non-compliant state if there are no available licenses in the account. The failover pair can use the aggregated license for 30 days, but if it is still non-compliant after the grace period, you will not be able to make configuration changes to features requiring special licenses (i.e. add an extra context); operation is otherwise unaffected. The new active unit sends an entitlement authorization renewal request every 35 seconds until the license is compliant. If you disband the failover pair, then the active unit releases the entitlements, and both units retain the licensing configuration in a cached state. To re-activate licensing, you need to clear the configuration on each unit, and re-configure it.
Permanent License Reservation
For permanent license reservation, you must purchase separate licenses for each chassis and enable the licenses before you configure failover.
Failover Licenses for the Secure Firewall 4200
Smart Software Manager Regular and On-Prem
Each unit requires the Essentials license (enabled by default) and the same encryption license. We recommend licensing each unit with the licensing server before you enable failover to avoid licensing mismatch issues, and when using the Strong Encryption license, issues with failover link encryption.
The failover feature itself does not require any licenses. There is no extra cost for the Context license on data units.
The Strong Encryption license is automatically enabled for qualified customers when you apply the registration token. For the optional Strong Encryption (3DES/AES) feature license enabled in the ASA configuration, see below.
In the ASA license configuration, the Essentials license is always enabled by default on both units. After you enable failover for Active/Standby failover, you can only configure smart licensing on the active unit. For Active/Active failover, you can only configure smart licensing on the unit with failover group 1 as active. The configuration is replicated to the standby unit, but the standby unit does not use the configuration; it remains in a cached state. The aggregated license is also cached on the standby unit to be used if it becomes the active unit in the future.
Each add-on license type is managed as follows:
-
Essentials—Each unit requests a StEssentialsandard license from the server.
-
Context—Only the active unit requests this license. However, the Essentials license includes 2 contexts by default and is present on both units. The value from each unit’s Essentials license plus the value of the Context license on the active unit are combined up to the platform limit. For example:
-
Active/Standby: The Essentials license includes 2 contexts; for two Secure Firewall 4215 units, these licenses add up to 4 contexts. You configure a 250-Context license on the active unit in an Active/Standby pair. Therefore, the aggregated failover license includes 254 contexts. However, because the platform limit for one unit is 250, the combined license allows a maximum of 250 contexts only. In this case, you might only configure the active Context license to be 246 contexts.
-
Active/Active: The Essentials license includes 2 contexts; for two Secure Firewall 4215 units, these licenses add up to 4 contexts. You configure a 10-Context license on the primary unit in an Active/Active pair. Therefore, the aggregated failover license includes 14 contexts. One unit can use 9 contexts and the other unit can use 5 contexts, for example; but during a failure, one unit will use all 14. Because the platform limit for one unit is 250, the combined license allows a maximum of 250 contexts; the 14 contexts are within the limit.
-
-
Strong Encryption (3DES/AES)—If your Smart Account is not authorized for strong encryption, but Cisco has determined that you are allowed to use strong encryption, you can manually add a strong encryption license to your account. Only the active unit requests this license, and both units can use it due to license aggregation.
After a failover, the new active unit continues to use the aggregated license. It uses the cached license configuration to re-request the entitlement from the server. When the old active unit rejoins the pair as a standby unit, it releases the license entitlement. Before the standby unit releases the entitlement, the new active unit's license might be in a non-compliant state if there are no available licenses in the account. The failover pair can use the aggregated license for 30 days, but if it is still non-compliant after the grace period, you will not be able to make configuration changes to features requiring special licenses (i.e. add an extra context); operation is otherwise unaffected. The new active unit sends an entitlement authorization renewal request every 35 seconds until the license is compliant. If you disband the failover pair, then the active unit releases the entitlements, and both units retain the licensing configuration in a cached state. To re-activate licensing, you need to clear the configuration on each unit, and re-configure it.
Permanent License Reservation
For permanent license reservation, you must purchase separate licenses for each chassis and enable the licenses before you configure failover.
Failover Licenses for the Firepower 4100/9300
Smart Software Manager Regular and On-Prem
Both Firepower 4100/9300 must be registered with the Smart Software Manager or Smart Software Manager On-Prem server before you configure failover. There is no extra cost for secondary units.
The Strong Encryption license is automatically enabled for qualified customers when you apply the registration token. When using the token, each chassis must have the same encryption license. For the optional Strong Encryption (3DES/AES) feature license enabled in the ASA configuration, see below.
After you enable failover, for the ASA license configuration for Active/Standby failover, you can only configure smart licensing on the active unit. For Active/Active failover, you can only configure smart licensing on the unit with failover group 1 as active. The configuration is replicated to the standby unit, but the standby unit does not use the configuration; it remains in a cached state. Only the active unit requests the licenses from the server. The licenses are aggregated into a single failover license that is shared by the failover pair, and this aggregated license is also cached on the standby unit to be used if it becomes the active unit in the future. Each license type is managed as follows:
-
Essentials—Although only the active unit requests this license from the server, the standby unit has the Essentials license enabled by default; it does not need to register with the server to use it.
-
Context—Only the active unit requests this license. However, the Essentials license includes 10 contexts by default and is present on both units. The value from each unit’s Essentials license plus the value of the Context license on the active unit are combined up to the platform limit. For example:
-
Active/Standby: The Essentials license includes 10 contexts; for 2 units, these licenses add up to 20 contexts. You configure a 250-Context license on the active unit in an Active/Standby pair. Therefore, the aggregated failover license includes 270 contexts. However, because the platform limit for one unit is 250, the combined license allows a maximum of 250 contexts only. In this case, you should only configure the active Context license to be 230 contexts.
-
Active/Active: The Essentials license includes 10 contexts; for 2 units, these licenses add up to 20 contexts. You configure a 10-Context license on the primary unit in an Active/Active pair. Therefore, the aggregated failover license includes 30 contexts. One unit can use 17 contexts and the other unit can use 13 contexts, for example; but during a failure, one unit will use all 30. Because the platform limit for one unit is 250, the combined license allows a maximum of 250 contexts; the 30 contexts are within the limit.
-
-
Carrier—Only the active requests this license, and both units can use it due to license aggregation.
-
Strong Encryption (3DES)—If your Smart Account is not authorized for strong encryption, but Cisco has determined that you are allowed to use strong encryption, you can manually add a strong encryption license to your account. Only the active unit requests this license, and both units can use it due to license aggregation.
After a failover, the new active unit continues to use the aggregated license. It uses the cached license configuration to re-request the entitlement from the server. When the old active unit rejoins the pair as a standby unit, it releases the license entitlement. Before the standby unit releases the entitlement, the new active unit's license might be in a non-compliant state if there are no available licenses in the account. The failover pair can use the aggregated license for 30 days, but if it is still non-compliant after the grace period, you will not be able to make configuration changes to features requiring special licenses; operation is otherwise unaffected. The new active unit sends an entitlement authorization renewal request every 35 seconds until the license is compliant. If you disband the failover pair, then the active unit releases the entitlements, and both units retain the licensing configuration in a cached state. To re-activate licensing, you need to clear the configuration on each unit, and re-configure it.
Permanent License Reservation
For permanent license reservation, you must purchase separate licenses for each chassis and enable the licenses before you configure failover.
ASA Cluster Licenses for the Secure Firewall 3100
Smart Software Manager Regular and On-Prem
Each unit requires the Essentials license (enabled by default) and the same encryption license. We recommend licensing each unit with the licensing server before you enable clustering to avoid licensing mismatch issues, and when using the Strong Encryption license, issues with cluster control link encryption.
The clustering feature itself does not require any licenses. There is no extra cost for the Context license on data units.
The Strong Encryption license is automatically enabled for qualified customers when you apply the registration token. For the optional Strong Encryption (3DES/AES) feature license enabled in the ASA configuration, see below.
In the ASA license configuration, the Essentials license is always enabled by default on all units. You can only configure smart licensing on the control unit. The configuration is replicated to the data units, but for some licenses, they do not use the configuration; it remains in a cached state, and only the control unit requests the license. The licenses are aggregated into a single cluster license that is shared by the cluster units, and this aggregated license is also cached on the data units to be used if one of them becomes the control unit in the future. Each license type is managed as follows:
-
Essentials—Each unit requests a Essentials license from the server.
-
Context—Only the control unit requests the Context license from the server. The Essentials license includes 2 contexts by default and is present on all cluster members. The value from each unit’s Essentials license plus the value of the Context license on the control unit are combined up to the platform limit in an aggregated cluster license. For example:
-
You have 6 Secure Firewall 3100s in the cluster. The Essentials license includes 2 contexts; for 6 units, these licenses add up to 12 contexts. You configure an additional 20-Context license on the control unit. Therefore, the aggregated cluster license includes 32 contexts. Because the platform limit for one chassis is 100, the combined license allows a maximum of 100 contexts; the 32 contexts are within the limit. Therefore, you can configure up to 32 contexts on the control unit; each data unit will also have 32 contexts through configuration replication.
-
You have 3 Secure Firewall 3100s in the cluster. The Essentials license includes 2 contexts; for 3 units, these licenses add up to 6 contexts. You configure an additional 100-Context license on the control unit. Therefore, the aggregated cluster license includes 106 contexts. Because the platform limit for one unit is 100, the combined license allows a maximum of 100 contexts; the 106 contexts are over the limit. Therefore, you can only configure up to 100 contexts on the control unit; each data unit will also have 100 contexts through configuration replication. In this case, you should only configure the control unit Context license to be 94 contexts.
-
-
Strong Encryption (3DES)—If your Smart Account is not authorized for strong encryption, but Cisco has determined that you are allowed to use strong encryption, you can manually add a strong encryption license to your account. Only the control unit requests this license, and all units can use it due to license aggregation.
If a new control unit is elected, the new control unit continues to use the aggregated license. It also uses the cached license configuration to re-request the control unit license. When the old control unit rejoins the cluster as a data unit, it releases the control unit license entitlement. Before the data unit releases the license, the control unit's license might be in a non-compliant state if there are no available licenses in the account. The retained license is valid for 30 days, but if it is still non-compliant after the grace period, you will not be able to make configuration changes to features requiring special licenses; operation is otherwise unaffected. The new active unit sends an entitlement authorization renewal request every 35 seconds until the license is compliant. You should refrain from making configuration changes until the license requests are completely processed. If a unit leaves the cluster, the cached control configuration is removed, while the per-unit entitlements are retained. In particular, you would need to re-request the Context license on non-cluster units.
Permanent License Reservation
For permanent license reservation, you must purchase separate licenses for each chassis and enable the licenses before you configure clustering.
ASA Cluster Licenses for the Secure Firewall 4200
Smart Software Manager Regular and On-Prem
Each unit requires the Essentials license (enabled by default) and the same encryption license. We recommend licensing each unit with the licensing server before you enable clustering to avoid licensing mismatch issues, and when using the Strong Encryption license, issues with cluster control link encryption.
The clustering feature itself does not require any licenses. There is no extra cost for the Context license on data units.
The Strong Encryption license is automatically enabled for qualified customers when you apply the registration token. For the optional Strong Encryption (3DES/AES) feature license enabled in the ASA configuration, see below.
In the ASA license configuration, the Essentials license is always enabled by default on all units. You can only configure smart licensing on the control unit. The configuration is replicated to the data units, but for some licenses, they do not use the configuration; it remains in a cached state, and only the control unit requests the license. The licenses are aggregated into a single cluster license that is shared by the cluster units, and this aggregated license is also cached on the data units to be used if one of them becomes the control unit in the future. Each license type is managed as follows:
-
Essentials—Each unit requests a Essentials license from the server.
-
Context—Only the control unit requests the Context license from the server. The Essentials license includes 2 contexts by default and is present on all cluster members. The value from each unit’s Essentials license plus the value of the Context license on the control unit are combined up to the platform limit in an aggregated cluster license. For example:
-
You have 6 Secure Firewall 4200s in the cluster. The Essentials license includes 2 contexts; for 6 units, these licenses add up to 12 contexts. You configure an additional 20-Context license on the control unit. Therefore, the aggregated cluster license includes 32 contexts. Because the platform limit for one chassis is 250, the combined license allows a maximum of 250 contexts; the 32 contexts are within the limit. Therefore, you can configure up to 32 contexts on the control unit; each data unit will also have 32 contexts through configuration replication.
-
You have 3 Secure Firewall 4200s in the cluster. The Essentials license includes 2 contexts; for 3 units, these licenses add up to 6 contexts. You configure an additional 250-Context license on the control unit. Therefore, the aggregated cluster license includes 256 contexts. Because the platform limit for one unit is 250, the combined license allows a maximum of 250 contexts; the 256 contexts are over the limit. Therefore, you can only configure up to 250 contexts on the control unit; each data unit will also have 250 contexts through configuration replication. In this case, you should only configure the control unit Context license to be 244 contexts.
-
-
Strong Encryption (3DES)—If your Smart Account is not authorized for strong encryption, but Cisco has determined that you are allowed to use strong encryption, you can manually add a strong encryption license to your account. Only the control unit requests this license, and all units can use it due to license aggregation.
If a new control unit is elected, the new control unit continues to use the aggregated license. It also uses the cached license configuration to re-request the control unit license. When the old control unit rejoins the cluster as a data unit, it releases the control unit license entitlement. Before the data unit releases the license, the control unit's license might be in a non-compliant state if there are no available licenses in the account. The retained license is valid for 30 days, but if it is still non-compliant after the grace period, you will not be able to make configuration changes to features requiring special licenses; operation is otherwise unaffected. The new active unit sends an entitlement authorization renewal request every 35 seconds until the license is compliant. You should refrain from making configuration changes until the license requests are completely processed. If a unit leaves the cluster, the cached control configuration is removed, while the per-unit entitlements are retained. In particular, you would need to re-request the Context license on non-cluster units.
Permanent License Reservation
For permanent license reservation, you must purchase separate licenses for each chassis and enable the licenses before you configure clustering.
ASA Cluster Licenses for the ASAv
Smart Software Manager Regular and On-Prem
Each unit requires the same Throughput license and the same encryption license. We recommend licensing each unit with the licensing server before you enable clustering to avoid licensing mismatch issues, and when using the Strong Encryption license, issues with cluster control link encryption.
The clustering feature itself does not require any licenses.
The Strong Encryption license is automatically enabled for qualified customers when you apply the registration token. For the optional Strong Encryption (3DES/AES) feature license enabled in the ASA configuration, see below.
In the ASA license configuration, you can only configure smart licensing on the control unit. The configuration is replicated to the data units, but for some licenses, they do not use the configuration; it remains in a cached state, and only the control unit requests the license. The licenses are aggregated into a single cluster license that is shared by the cluster units, and this aggregated license is also cached on the data units to be used if one of them becomes the control unit in the future. Each license type is managed as follows:
-
Essentials—Only the control unit requests the Essentials license from the server, and all units can use it due to license aggregation.
-
Throughput—Each unit requests its own Throughput license from the server.
-
Strong Encryption (3DES)—If your Smart Account is not authorized for strong encryption, but Cisco has determined that you are allowed to use strong encryption, you can manually add a strong encryption license to your account. Only the control unit requests this license, and all units can use it due to license aggregation.
Permanent License Reservation
For permanent license reservation, you must purchase separate licenses for each unit and enable the licenses before you configure clustering.
ASA Cluster Licenses for the Firepower 4100/9300
Smart Software Manager Regular and On-Prem
The clustering feature itself does not require any licenses. To use Strong Encryption and other optional licenses, each Firepower 4100/9300 chassis must be registered with the License Authority or Smart Software Manager Regular and On-Prem server. There is no extra cost for data units.
The Strong Encryption license is automatically enabled for qualified customers when you apply the registration token. When using the token, each chassis must have the same encryption license. For the optional Strong Encryption (3DES/AES) feature license enabled in the ASA configuration, see below.
In the ASA license configuration, you can only configure smart licensing on the control unit. The configuration is replicated to the data units, but for some licenses, they do not use the configuration; it remains in a cached state, and only the control unit requests the license. The licenses are aggregated into a single cluster license that is shared by the cluster units, and this aggregated license is also cached on the data units to be used if one of them becomes the control unit in the future. Each license type is managed as follows:
-
Essentials—Only the control unit requests the Essentials license from the server, and both units can use it due to license aggregation.
-
Context—Only the control unit requests the Context license from the server. The Essentials license includes 10 contexts by default and is present on all cluster members. The value from each unit’s Essentials license plus the value of the Context license on the control unit are combined up to the platform limit in an aggregated cluster license. For example:
-
You have 6 Firepower 9300 modules in the cluster. The Essentials license includes 10 contexts; for 6 units, these licenses add up to 60 contexts. You configure an additional 20-Context license on the control unit. Therefore, the aggregated cluster license includes 80 contexts. Because the platform limit for one module is 250, the combined license allows a maximum of 250 contexts; the 80 contexts are within the limit. Therefore, you can configure up to 80 contexts on the control unit; each data unit will also have 80 contexts through configuration replication.
-
You have 3 Firepower 4112 units in the cluster. The Essentials license includes 10 contexts; for 3 units, these licenses add up to 30 contexts. You configure an additional 250-Context license on the control unit. Therefore, the aggregated cluster license includes 280 contexts. Because the platform limit for one unit is 250, the combined license allows a maximum of 250 contexts; the 280 contexts are over the limit. Therefore, you can only configure up to 250 contexts on the control unit; each data unit will also have 250 contexts through configuration replication. In this case, you should only configure the control unit Context license to be 220 contexts.
-
-
Carrier—Required for Distributed S2S VPN. This license is a per-unit entitlement, and each unit requests its own license from the server.
-
Strong Encryption (3DES)—For pre-2.3.0 Cisco Smart Software Manager On-Prem deployment; or if your Smart Account is not authorized for strong encryption, but Cisco has determined that you are allowed to use strong encryption, you can manually add a strong encryption license to your account. This license is a per-unit entitlement, and each unit requests its own license from the server.
If a new control unit is elected, the new control unit continues to use the aggregated license. It also uses the cached license configuration to re-request the control unit license. When the old control unit rejoins the cluster as a data unit, it releases the control unit license entitlement. Before the data unit releases the license, the control unit's license might be in a non-compliant state if there are no available licenses in the account. The retained license is valid for 30 days, but if it is still non-compliant after the grace period, you will not be able to make configuration changes to features requiring special licenses; operation is otherwise unaffected. The new active unit sends an entitlement authorization renewal request every 12 hours until the license is compliant. You should refrain from making configuration changes until the license requests are completely processed. If a unit leaves the cluster, the cached control configuration is removed, while the per-unit entitlements are retained. In particular, you would need to re-request the Context license on non-cluster units.
Permanent License Reservation
For permanent license reservation, you must purchase separate licenses for each chassis and enable the licenses before you configure clustering.
 Feedback
Feedback