AWS Service VPC
For the Centralized (hub) mode deployment using AWS Transit Gateway, the Multicloud Defense Gateway is deployed in a new VPC. This VPC is called a Service VPC. The Service VPC and the application (Spoke) VPCs are connected to the AWS Transit Gateway in a Hub-Spoke model as shown below:
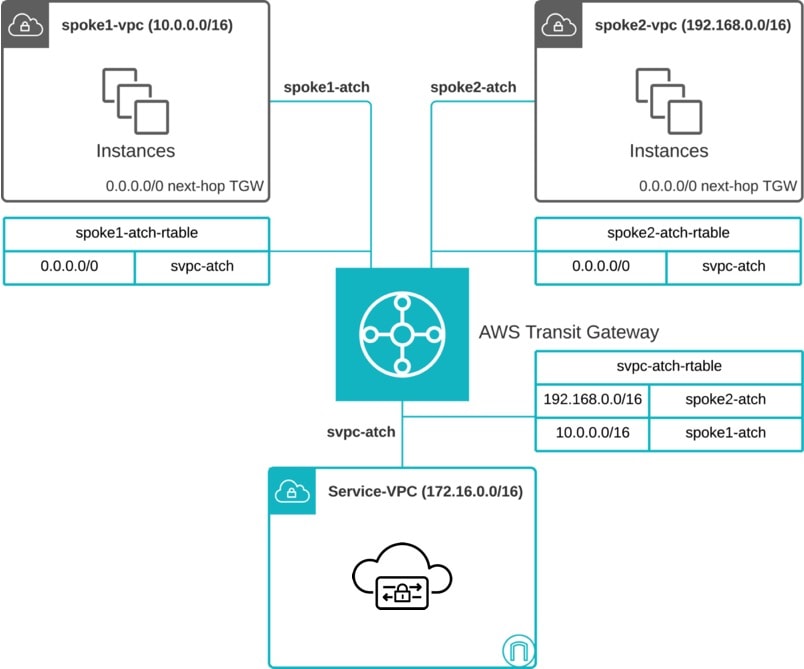
Multicloud Defense orchestrates creating the Service VPC, creating (or reusing) the AWS Transit Gateway (TGW), and attaching the Spoke VPCs and the Service VPC to the TGW. It updates the routing between the Service VPC and Spoke VPCs. Customers need to change the route tables associated with subnets in the Spoke VPCs to add a default route and set the destination to the TGW.
 Note |
If the TGW is created using the AWS Terraform Provider, the attributes default_route_table_association and default_route_table_propagation MUST be set to "disable". If the TGW is created using the AWS Console, the attributes Default association route table and Default propagation route table MUST be set to Disable. If the TGW is created using the Multicloud Defense Service VPC orchestration, the attributes are set appropriately. If these values are not set properly, traffic will bypass the Service VPC and will not be protected by Multicloud Defense. |
Create an AWS Service VPC
Procedure
|
Step 1 |
Click . |
||
|
Step 2 |
Click Create VPC/VNet. |
||
|
Step 3 |
Provide a name for the service VPC (an example is multicloud defense-service-vpc1). |
||
|
Step 4 |
Select the AWS account. |
||
|
Step 5 |
Select the Region where the service VPC needs to be created (an example isus-east-1). |
||
|
Step 6 |
Provide a CIDR block with mask minimum of /25 and maximum of /16. Make sure this does not overlap with any of the spoke VPC CIDRs that you plan to attach to the Transit Gateway (an example is 172.16.0.0/16). |
||
|
Step 7 |
Select the Availability Zones. It's recommended to select at least two (2) AZs for HA purposes (an example is us- east-1a and us-east-1b). |
||
|
Step 8 |
Select a Transit Gateway. Alternatively, create a new one. You can reuse an existing transit gateway for all kinds of security types. |
||
|
Step 9 |
Select the Auto accept shared attachments, if you are planning to use the transit gateway shared across multiple AWS accounts. |
||
|
Step 10 |
Click Save to create the service VPC.
|
 Feedback
Feedback