Audit Logs
Audit logs contain details of actions performed by Users. This includes, but is not limited to, actions such as login/logout activity, creating, deleting, updating, enabling, and disabling of Profiles, Rules, Gateways, or any user activity that relates to the configuration and operation of the Multicloud Defense solution. Multicloud Defense supports log forwarding to AWS S3.
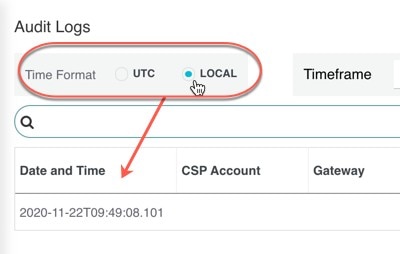
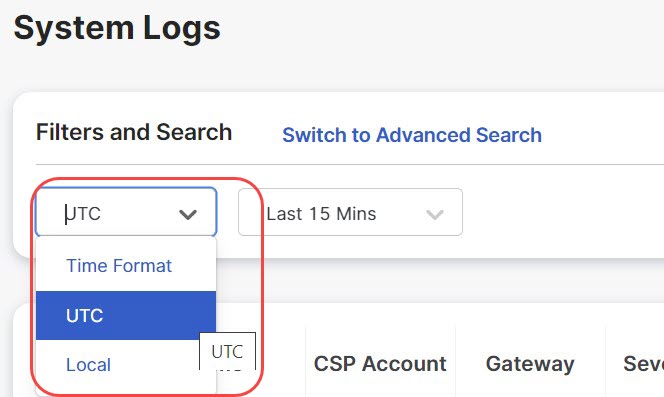
Time Format
Logs can be displayed in UTC (Coordinated Universal Time) or Local time format. Local means the time zone of the user as configured
e.g. USA/Pacific. Date and Time of logs will be displayed in ISO 8601 format (complete date plus hours, minutes, seconds and
a decimal fraction of a second - YYYY-MM-DD T HH:MM:SS:S). Example: 2020-11-22T10:58:46.820
To select, or switch between, different Time Formats, click the radio button as shown:
Timeframe
Logs can be displayed in increment options from 15 minutes to 30 days, or Custom timeframes. To select, or switch between, timeframes, click the drop-down menu and select a timeframe as shown:

For Custom timeframes, select Custom, the Start and the End date or time by clicking the calendar objects followed by Save.
Search Filter
Logs can be filtered using the Search function and audit log fields. The audit log fields are Action
Type, Source IP, User, Gateway, CSP Account, Role.
To filter audit logs on one, or multiple, fields:
Procedure
|
Step 1 |
Left mouse-click in the Search field to access the pull down menu. 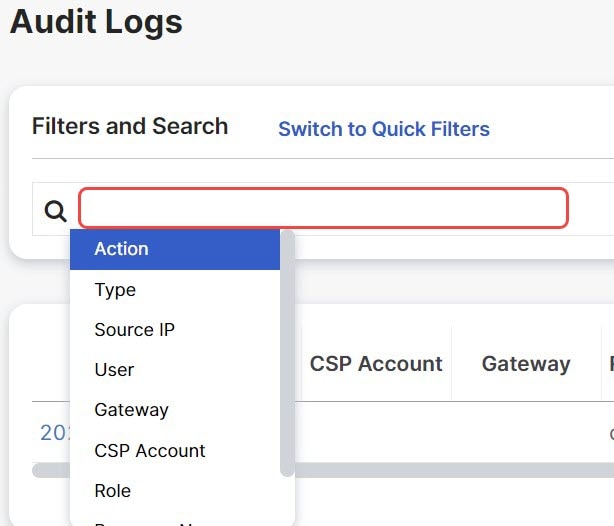
|
|
Step 2 |
Select a field. |
|
Step 3 |
Type a desired search string. |
|
Step 4 |
Add additional fields to the search criteria as required. Example: Filter for Actions = "DELETE" and performed by user with string containing "steve" would appear in the filter criteria and results. |


 Feedback
Feedback